Key Challenges in IOT Security | Digitdefence
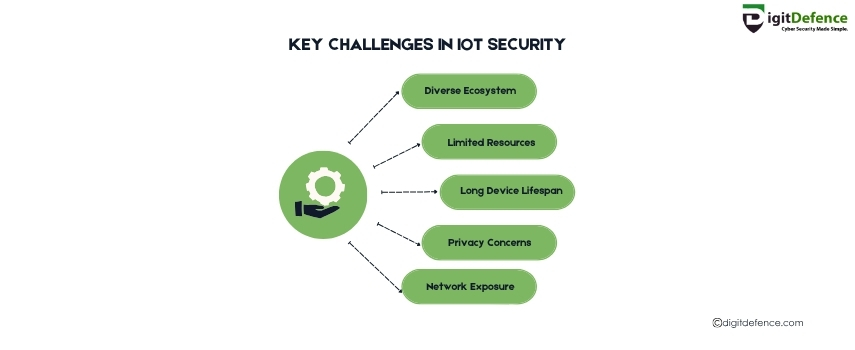
Key challenges in IoT security include the lack of standardized security protocols and the increased attack surface due to the vast number of connected devices. As IoT devices proliferate, ensuring robust security measures against data breaches, unauthorized access, and device vulnerabilities becomes increasingly complex
#IoTSecurity #CyberSecurity #DataProtection #ConnectedDevices #IoTChallenges #Vulnerabilities #SecurityProtocols #CyberThreats #dataprivacy #TechSecurity
Key challenges in IoT security include the lack of standardized security protocols and the increased attack surface due to the vast number of connected devices. As IoT devices proliferate, ensuring robust security measures against data breaches, unauthorized access, and device vulnerabilities becomes increasingly complex
#IoTSecurity #CyberSecurity #DataProtection #ConnectedDevices #IoTChallenges #Vulnerabilities #SecurityProtocols #CyberThreats #dataprivacy #TechSecurity
09:51 AM - Jun 11, 2025 (UTC)
Common Cloud Security Threats | Digitdefence
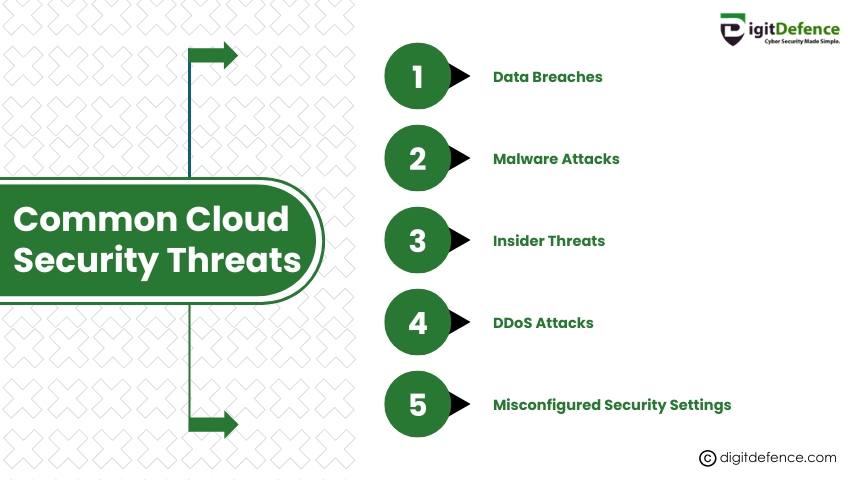
Common cloud security threats include data breaches, misconfigured settings, and insecure APIs. Understanding them is key to building a secure cloud environment.
#cloudsecurity #CyberThreats #DataBreach #cloudcomputing #infosec #CloudProtection #CloudRisk #SecurityAwareness #cloudinfrastructure #SecureCloud
Common cloud security threats include data breaches, misconfigured settings, and insecure APIs. Understanding them is key to building a secure cloud environment.
#cloudsecurity #CyberThreats #DataBreach #cloudcomputing #infosec #CloudProtection #CloudRisk #SecurityAwareness #cloudinfrastructure #SecureCloud
10:16 AM - Jun 06, 2025 (UTC)
Why is Endpoint Protection Vital For CyberSecurity | Digitdefence
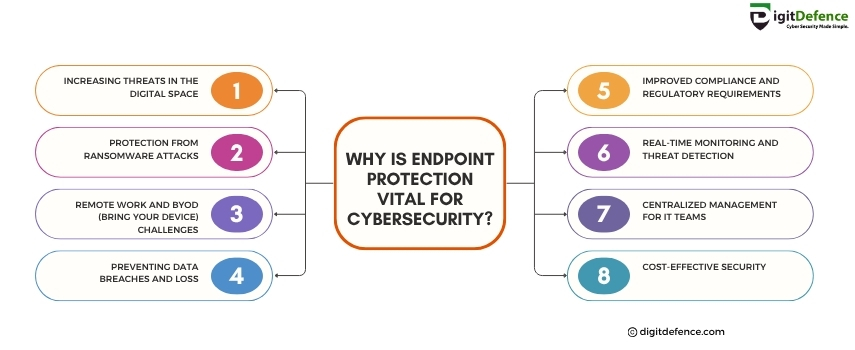
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
06:44 AM - Jun 13, 2025 (UTC)
The Importance of Securing Endpoint Devices | Digitdefence
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
09:51 AM - Jun 10, 2025 (UTC)
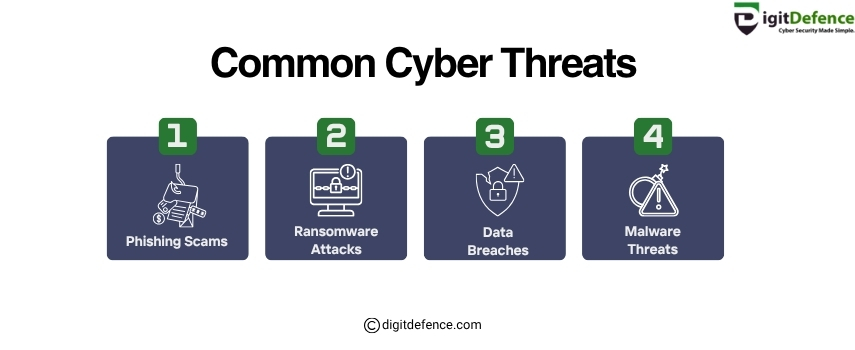
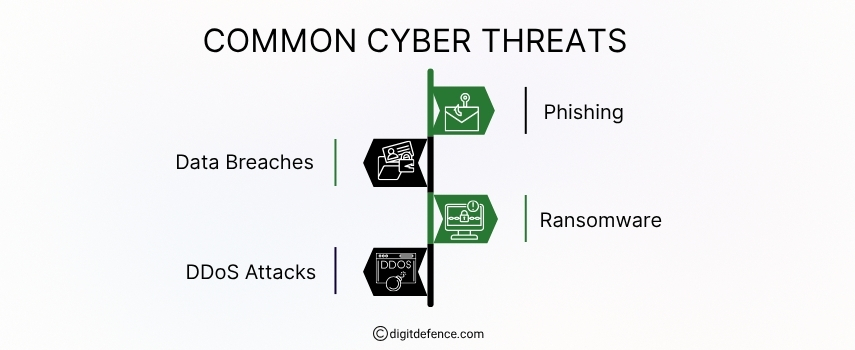
Common Cyber Threats | Digitdefence
Common cyber threats include malware, phishing attacks, ransomware, and data breaches. These threats can compromise sensitive information and disrupt business operations if not properly managed.
#CyberThreats #Malware #Phishing #Ransomware #DataBreach #CyberSecurityAwareness #OnlineSafety #infosec #ThreatPrevention #DigitalSecurity
Common cyber threats include malware, phishing attacks, ransomware, and data breaches. These threats can compromise sensitive information and disrupt business operations if not properly managed.
#CyberThreats #Malware #Phishing #Ransomware #DataBreach #CyberSecurityAwareness #OnlineSafety #infosec #ThreatPrevention #DigitalSecurity
06:44 AM - Jun 25, 2025 (UTC)
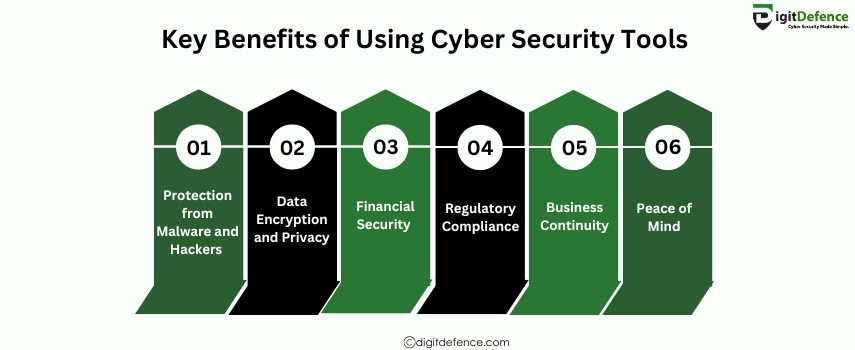
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:28 AM - Jun 13, 2025 (UTC)
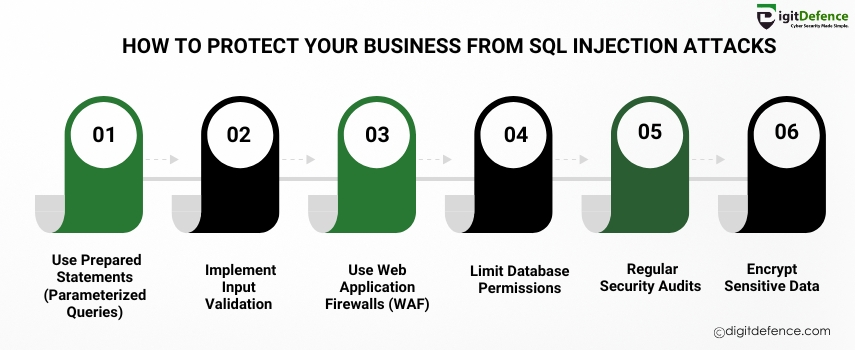
How to Protect Your Business From SQL Injection Attacks| Digitdefence
Protecting your business from SQL injection attacks requires implementing secure coding practices, such as using prepared statements and parameterized queries. Regularly updating your systems and conducting security audits can further reduce the risk of these attacks.
#SQLInjection #CyberSecurity #DataProtection #WebSecurity #SecureCoding #TechSecurity #HackingPrevention #VulnerabilityManagement #BusinessSecurity #CyberThreats
Protecting your business from SQL injection attacks requires implementing secure coding practices, such as using prepared statements and parameterized queries. Regularly updating your systems and conducting security audits can further reduce the risk of these attacks.
#SQLInjection #CyberSecurity #DataProtection #WebSecurity #SecureCoding #TechSecurity #HackingPrevention #VulnerabilityManagement #BusinessSecurity #CyberThreats
10:38 AM - Jun 12, 2025 (UTC)
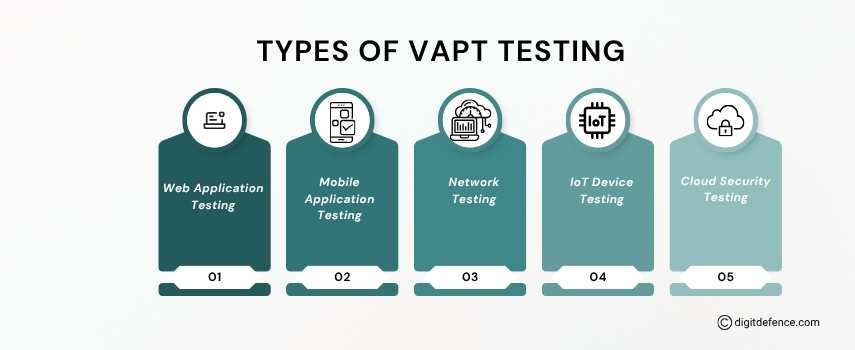
Types of VAPT Testing | Digitdefence
Types of VAPT (Vulnerability Assessment and Penetration Testing) include Network VAPT, Web Application VAPT, Mobile Application VAPT, and Wireless Network VAPT, each focusing on identifying vulnerabilities in specific areas of your infrastructure. These tests help businesses uncover potential security flaws, assess risk, and strengthen their defense mechanisms against cyber threats.
#VAPT #CyberSecurity #PenetrationTesting #networksecurity #WebApplicationSecurity #MobileSecurity #RiskAssessment #CyberThreats #securitytesting #DataProtection
Types of VAPT (Vulnerability Assessment and Penetration Testing) include Network VAPT, Web Application VAPT, Mobile Application VAPT, and Wireless Network VAPT, each focusing on identifying vulnerabilities in specific areas of your infrastructure. These tests help businesses uncover potential security flaws, assess risk, and strengthen their defense mechanisms against cyber threats.
#VAPT #CyberSecurity #PenetrationTesting #networksecurity #WebApplicationSecurity #MobileSecurity #RiskAssessment #CyberThreats #securitytesting #DataProtection
09:40 AM - Jun 11, 2025 (UTC)
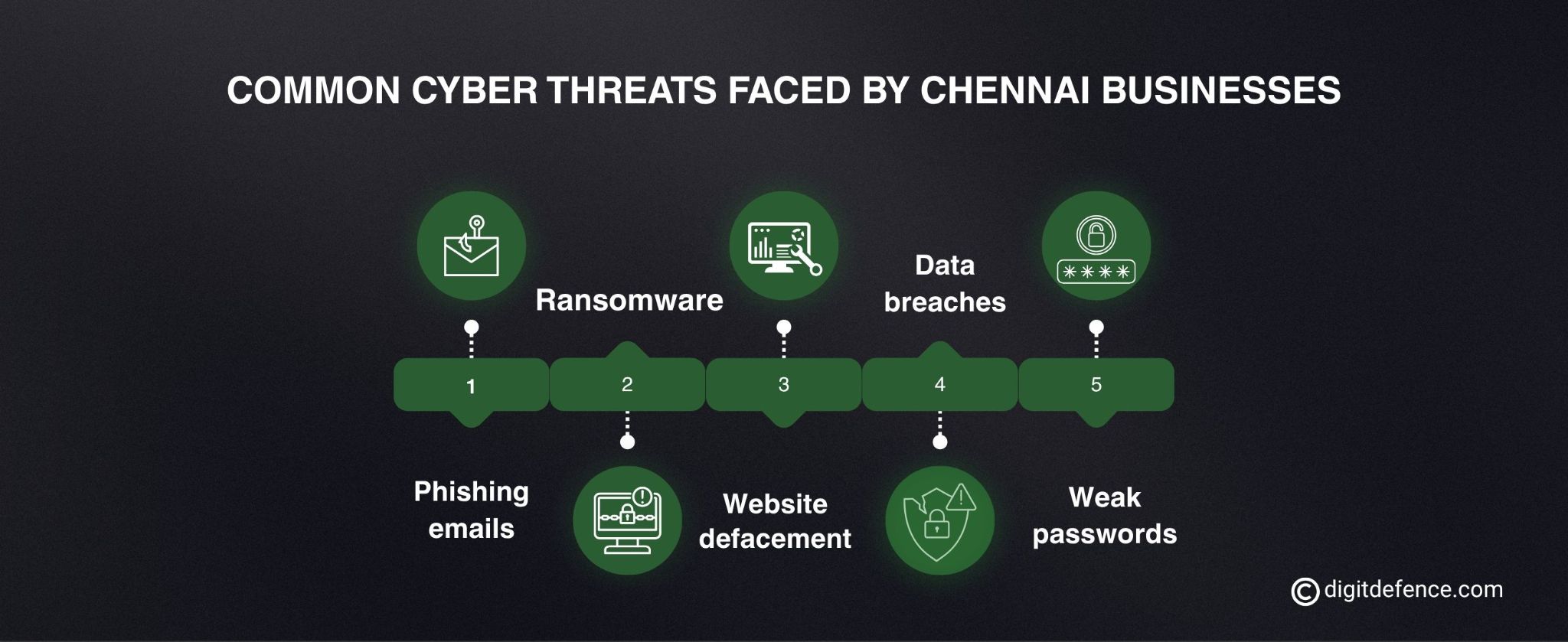
Common Cyber Threats Faced By Chennai Businesses | Digitdefence
Chennai businesses face cyber threats like phishing, ransomware, data breaches, and insider attacks that can compromise sensitive information and disrupt operations. Staying vigilant with strong cybersecurity measures is essential to protect your assets.
#CybersecurityChennai #DataProtection #Phishing #Ransomware #CyberThreats #BusinessSecurity
Chennai businesses face cyber threats like phishing, ransomware, data breaches, and insider attacks that can compromise sensitive information and disrupt operations. Staying vigilant with strong cybersecurity measures is essential to protect your assets.
#CybersecurityChennai #DataProtection #Phishing #Ransomware #CyberThreats #BusinessSecurity
07:53 AM - Jun 20, 2025 (UTC)
Common Cyber Threats | Digitdefence
Common cyber threats include phishing attacks, where hackers trick you into giving up personal info, and malware, which can silently steal data or damage systems. Staying alert and using good security tools can help keep you safe.
#CyberSecurity #PhishingAwareness#MalwareProtection
#OnlineSafety #CyberThreats#DataSecurity#StaySafeOnline
Common cyber threats include phishing attacks, where hackers trick you into giving up personal info, and malware, which can silently steal data or damage systems. Staying alert and using good security tools can help keep you safe.
#CyberSecurity #PhishingAwareness#MalwareProtection
#OnlineSafety #CyberThreats#DataSecurity#StaySafeOnline
07:01 AM - Jun 16, 2025 (UTC)
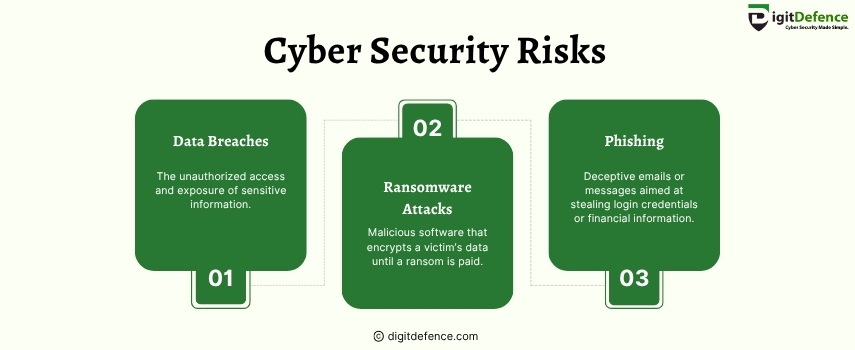
Cyber Security Risks | Digitdefence
Cyber security risks include threats like data breaches, malware attacks, and phishing scams that can compromise sensitive information and disrupt business operations. Staying vigilant and implementing strong security measures is essential to protect your assets.
#CyberSecurityRisks #DataProtection #CyberThreats #infosec #DigitalSecurity
Cyber security risks include threats like data breaches, malware attacks, and phishing scams that can compromise sensitive information and disrupt business operations. Staying vigilant and implementing strong security measures is essential to protect your assets.
#CyberSecurityRisks #DataProtection #CyberThreats #infosec #DigitalSecurity
09:11 AM - Jun 02, 2025 (UTC)
Why Network Pen Testing Is Essential | Digitdefence
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
10:55 AM - Jun 12, 2025 (UTC)
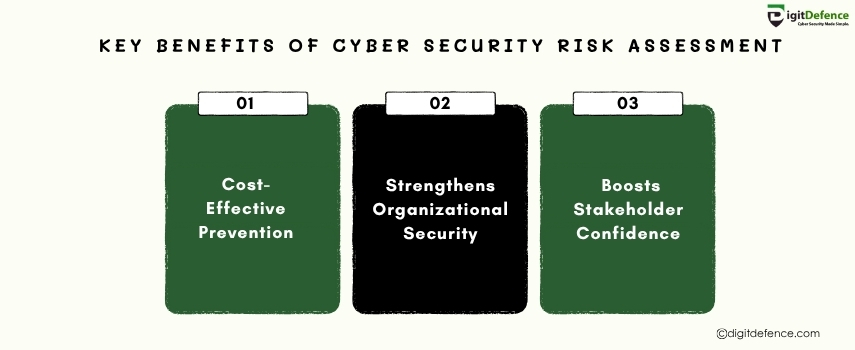
Key Benefits of Cyber Security Risk Assessment | Digitdefence
A thorough cyber security risk assessment helps organizations identify vulnerabilities, prevent data breaches, and enhance their overall security posture. By proactively addressing potential risks, businesses can avoid costly security incidents and ensure the protection of sensitive data.
#CyberSecurity #RiskAssessment #DataProtection #SecurityFirst #BusinessContinuity #DataBreachPrevention #riskmanagement #CyberThreats #SecurityStrategy #protectyourbusiness
A thorough cyber security risk assessment helps organizations identify vulnerabilities, prevent data breaches, and enhance their overall security posture. By proactively addressing potential risks, businesses can avoid costly security incidents and ensure the protection of sensitive data.
#CyberSecurity #RiskAssessment #DataProtection #SecurityFirst #BusinessContinuity #DataBreachPrevention #riskmanagement #CyberThreats #SecurityStrategy #protectyourbusiness
09:42 AM - Jun 10, 2025 (UTC)
Sponsored by
OWT
6 months ago
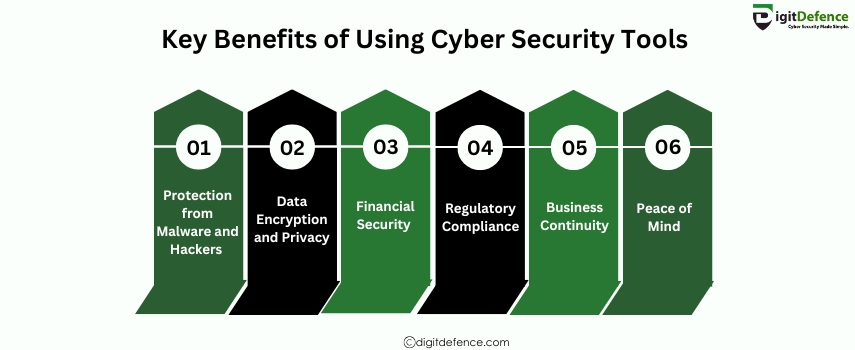
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:26 AM - Jun 13, 2025 (UTC)
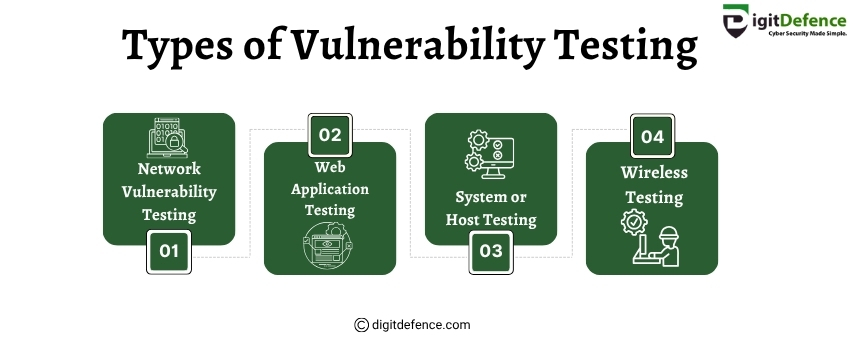
Types of Vulnerability Testing
Identify weak points before attackers do with key types of vulnerability testing: network, web, system & wireless.
To explore more, let’s connect.
https://digitdefence.com/
#CyberSecurity #VulnerabilityTesting #CyberThreats
Identify weak points before attackers do with key types of vulnerability testing: network, web, system & wireless.
To explore more, let’s connect.
https://digitdefence.com/
#CyberSecurity #VulnerabilityTesting #CyberThreats
11:39 AM - Jun 24, 2025 (UTC)