Top Web Application Firewall Companies | 2025 Market Analysis Report
https://www.renub.com/top-...
Discover the leading Web Application Firewall (WAF) companies protecting your business from cyber threats in 2025. Explore detailed market analysis, top global providers like Akamai and Cloudflare, and key WAF players in Bangladesh. Stay ahead in cybersecurity with this comprehensive report by Renub Research.
Web Application Firewall, WAF, Cybersecurity, Akamai, Cloudflare, Bangladesh WAF providers, Network Security, Data Protection, IT Security, Renub Research
#WebApplicationFirewall #WAF #CyberSecurity #networksecurity #DataProtection #Akamai #Cloudflare #Bangladesh #ITSecurity #RenubResearch
https://www.renub.com/top-...
Discover the leading Web Application Firewall (WAF) companies protecting your business from cyber threats in 2025. Explore detailed market analysis, top global providers like Akamai and Cloudflare, and key WAF players in Bangladesh. Stay ahead in cybersecurity with this comprehensive report by Renub Research.
Web Application Firewall, WAF, Cybersecurity, Akamai, Cloudflare, Bangladesh WAF providers, Network Security, Data Protection, IT Security, Renub Research
#WebApplicationFirewall #WAF #CyberSecurity #networksecurity #DataProtection #Akamai #Cloudflare #Bangladesh #ITSecurity #RenubResearch

Top Web Application Firewall Companies 2025 | WAF Leaders
Discover the top WAF companies protecting web apps against cyber threats with cutting-edge firewall solutions.
https://www.renub.com/top-web-application-firewall-companies-bd.php
07:44 AM - May 29, 2025 (UTC)
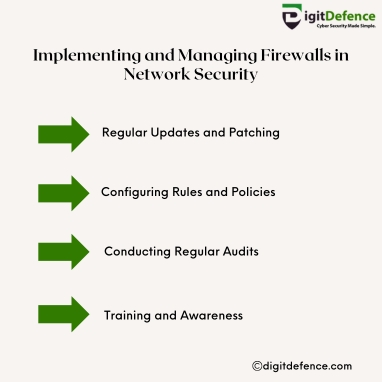
Implementing and Managing Firewalls in Network Security | Digitdefence
Implementing and managing firewalls is crucial for controlling network traffic and blocking unauthorized access. They serve as a vital shield, protecting your business from cyber threats.
#FirewallSecurity #NetworkProtection #CyberSecurity #ITSecurity #DataSafety #networksecurity #BusinessProtection
Implementing and managing firewalls is crucial for controlling network traffic and blocking unauthorized access. They serve as a vital shield, protecting your business from cyber threats.
#FirewallSecurity #NetworkProtection #CyberSecurity #ITSecurity #DataSafety #networksecurity #BusinessProtection
10:06 AM - May 21, 2025 (UTC)
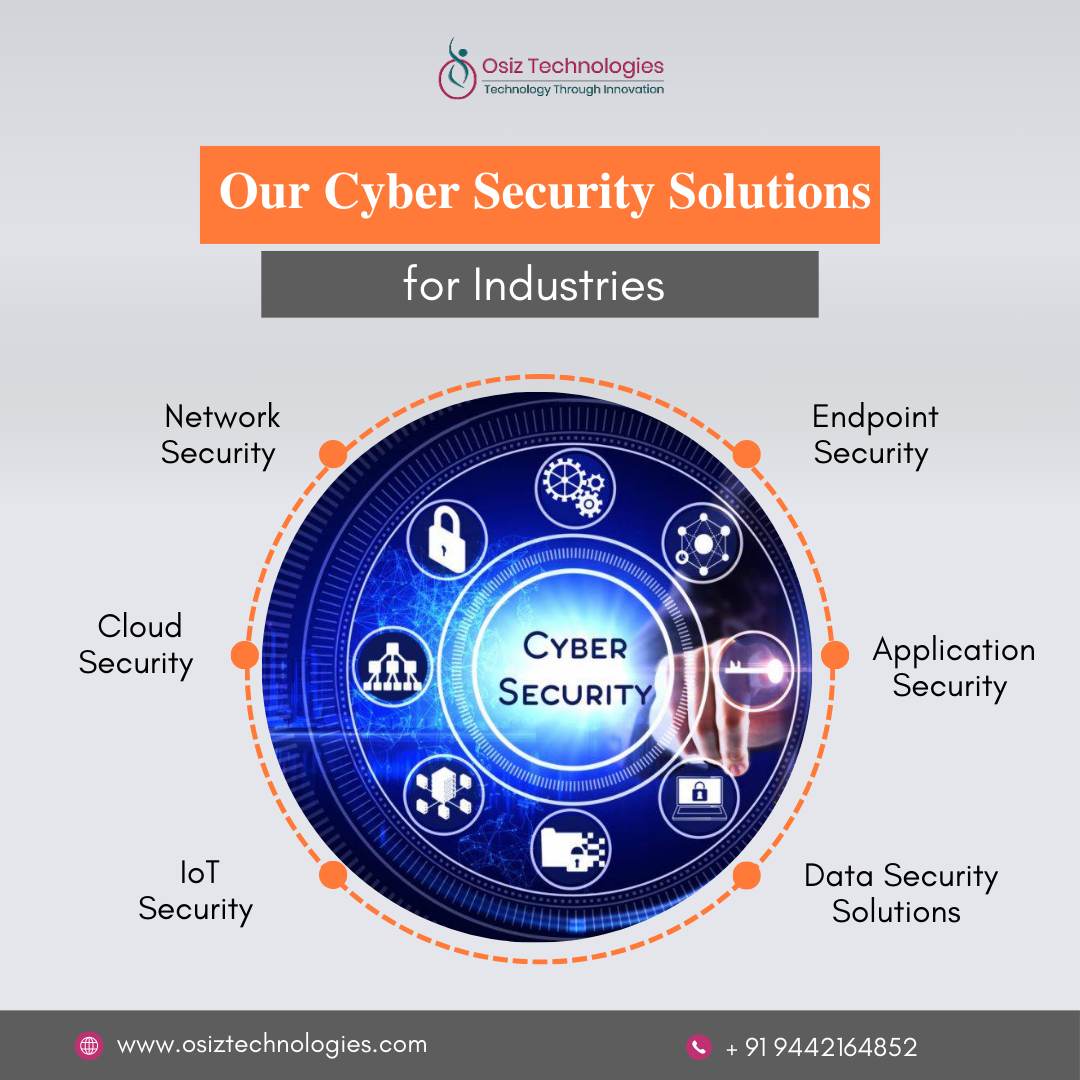
Safeguard Your Digital Assets with Osiz's Cybersecurity Solutions! ?
At #Osiz , we deliver cutting-edge #CyberSecurity solutions designed to protect your business from evolving threats. Our comprehensive services include threat detection, risk assessment, and advanced security protocols tailored to your needs.
?Visit: https://www.osiztechnologi...
#CybersecuritySolutions #Cybersecurityservices #BusinessSecurity #DigitalSecurity #networksecurity #BusinessProtection #business #startups #entrepreneur #usa #Singapore #uae
At #Osiz , we deliver cutting-edge #CyberSecurity solutions designed to protect your business from evolving threats. Our comprehensive services include threat detection, risk assessment, and advanced security protocols tailored to your needs.
?Visit: https://www.osiztechnologi...
#CybersecuritySolutions #Cybersecurityservices #BusinessSecurity #DigitalSecurity #networksecurity #BusinessProtection #business #startups #entrepreneur #usa #Singapore #uae
11:27 AM - Sep 04, 2024 (UTC)
Cyber Security Institute In Lucknow – Enroll Now!
Join The Leading Cyber Security Institute In Lucknow. Master Ethical Hacking, Network Security, And More. Gain Hands-On Training From Experts And Secure Your Future In Tech. Enroll Today And Start Your Journey Toward A Successful Cyber Security Career.
If You Have Any Queries, Please Contact Us.
Website Link - https://training.cyberhunt...
Mobile No - 91 8178395155, 8810652253
Email ID - enquirycyberhunterz.com
#CyberSecurity #EthicalHacking #TechTraining #CyberSecurityInstitute #lucknow #networksecurity #TechCareer #EnrollNow #LearnCyberSecurity #FutureInTech
Join The Leading Cyber Security Institute In Lucknow. Master Ethical Hacking, Network Security, And More. Gain Hands-On Training From Experts And Secure Your Future In Tech. Enroll Today And Start Your Journey Toward A Successful Cyber Security Career.
If You Have Any Queries, Please Contact Us.
Website Link - https://training.cyberhunt...
Mobile No - 91 8178395155, 8810652253
Email ID - enquirycyberhunterz.com
#CyberSecurity #EthicalHacking #TechTraining #CyberSecurityInstitute #lucknow #networksecurity #TechCareer #EnrollNow #LearnCyberSecurity #FutureInTech
11:22 AM - Mar 10, 2025 (UTC)
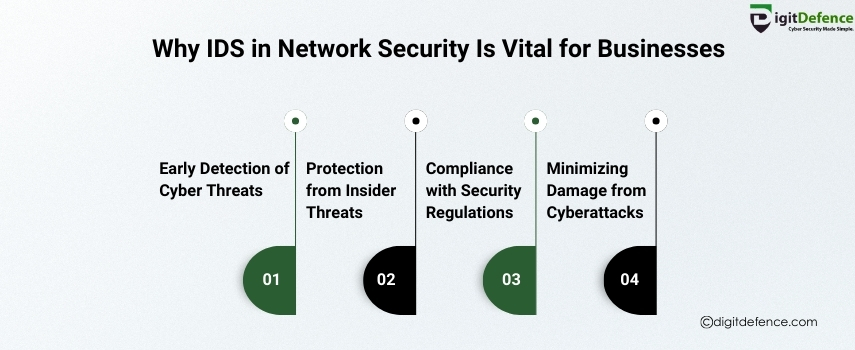
Why IDS In Network Security is Vital For Businesses| Digitdefence
Protect your business from cyber threats with IDS in network security. Early detection of intrusions can prevent data breaches and minimize risks.
#networksecurity #IDS #CyberSecurity #BusinessProtection #datasecurity #CyberDefense
Protect your business from cyber threats with IDS in network security. Early detection of intrusions can prevent data breaches and minimize risks.
#networksecurity #IDS #CyberSecurity #BusinessProtection #datasecurity #CyberDefense
09:24 AM - May 15, 2025 (UTC)
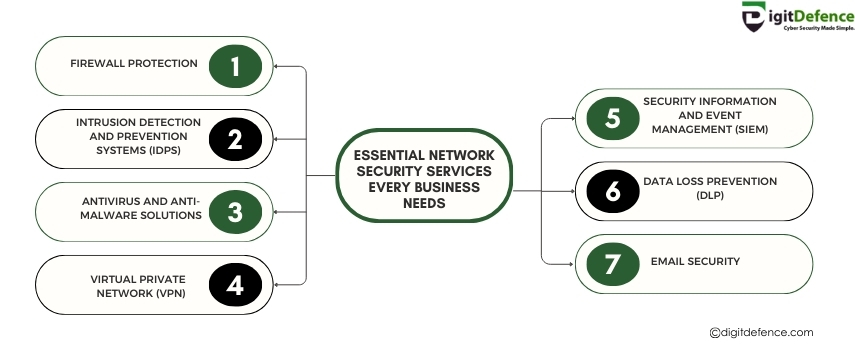
Essential Network Security Services Every Business Needs
Every business needs essential network security services to protect against cyber threats and safeguard sensitive data. Strong security measures ensure business continuity and build customer trust.
#networksecurity #CyberSecurity #DataProtection #BusinessSafety #SecurityServices #ITSecurity #riskmanagement
Every business needs essential network security services to protect against cyber threats and safeguard sensitive data. Strong security measures ensure business continuity and build customer trust.
#networksecurity #CyberSecurity #DataProtection #BusinessSafety #SecurityServices #ITSecurity #riskmanagement
09:55 AM - May 21, 2025 (UTC)
Top 5 Things to Consider When Choosing a Business Internet Provider
Read More:
https://postr.yruz.one/top...
#BusinessIntelligenceConsulting #networksecurity #CyberSecurity
Read More:
https://postr.yruz.one/top...
#BusinessIntelligenceConsulting #networksecurity #CyberSecurity

Top 5 Things to Consider When Choosing a Business Internet Provider - Premium Blogging Platform
Discover the top 5 must-know tips for selecting the ideal business internet provider and enhance your company’s connectivity with our expert advice.
https://postr.yruz.one/top-5-things-to-consider-when-choosing-a-business-internet-provider
12:58 PM - Dec 25, 2024 (UTC)
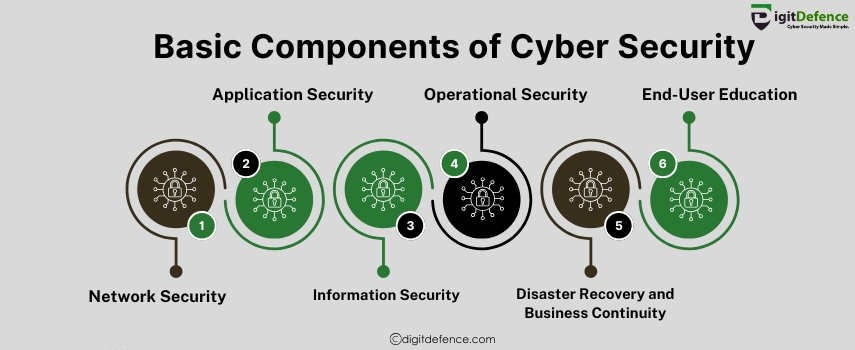
Basic Components of Cyber Security | Digitdefence
Cyber security is built on core components like network security, information security, and threat management. Protect your business by securing these critical areas.
#CyberSecurity #networksecurity #DataProtection
Cyber security is built on core components like network security, information security, and threat management. Protect your business by securing these critical areas.
#CyberSecurity #networksecurity #DataProtection
09:36 AM - Apr 22, 2025 (UTC)
How Unified Threat Management is Revolutionizing Enterprise Network Security Solutions?
Unified Threat Management (UTM) has emerged as a comprehensive security solution that combines multiple security features into a single platform, offering organizations a streamlined approach to protecting their networks and data.
Unified Threat Management represents a paradigm shift in network security architecture by consolidating various security functions into a single system. Unlike traditional security approaches that rely on multiple standalone solutions, UTM provides a holistic security framework that includes firewall capabilities, intrusion detection and prevention, antivirus protection, content filtering, and anti-spam functionality.
Get more insights on, Unified Threat Management- https://www.patreon.com/po...
#CoherentMarketInsights #CyberDefense #networksecurity #ThreatProtection #CyberSecuritySuite
Unified Threat Management (UTM) has emerged as a comprehensive security solution that combines multiple security features into a single platform, offering organizations a streamlined approach to protecting their networks and data.
Unified Threat Management represents a paradigm shift in network security architecture by consolidating various security functions into a single system. Unlike traditional security approaches that rely on multiple standalone solutions, UTM provides a holistic security framework that includes firewall capabilities, intrusion detection and prevention, antivirus protection, content filtering, and anti-spam functionality.
Get more insights on, Unified Threat Management- https://www.patreon.com/po...
#CoherentMarketInsights #CyberDefense #networksecurity #ThreatProtection #CyberSecuritySuite
09:45 AM - Apr 24, 2025 (UTC)
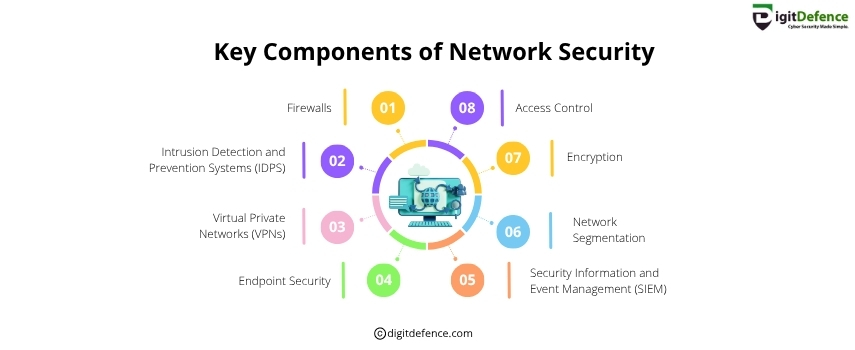
Key Components of Network Security | Digitdefence
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
09:16 AM - Jun 04, 2025 (UTC)
Global Application Delivery Network Market to Reach USD 18.68 Billion by 2030, Growing at a CAGR of 12.3%
#ApplicationDeliveryNetwork , #ADNMarket , #MarketGrowth , #cloudcomputing , #networksecurity , #DigitalInfrastructure
https://www.maximizemarket...
#ApplicationDeliveryNetwork , #ADNMarket , #MarketGrowth , #cloudcomputing , #networksecurity , #DigitalInfrastructure
https://www.maximizemarket...
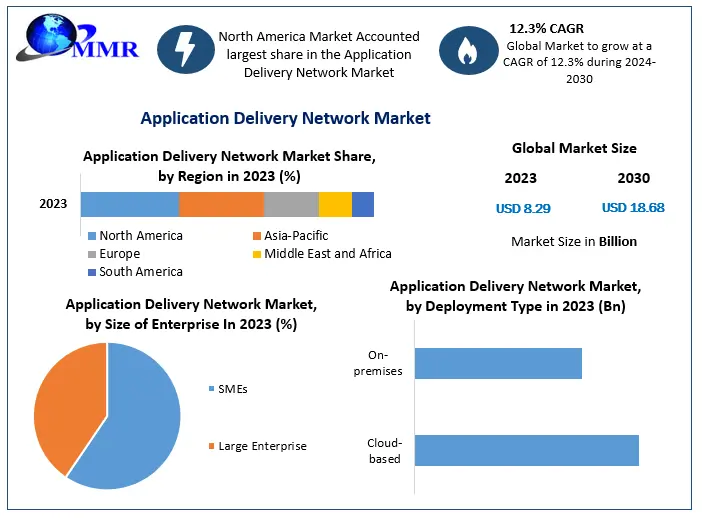
Application Delivery Network Market- Analysis and Forecast
Global Application Delivery Network Market value is projected to reach US$ 18.68 Bn and it is expected to grow at the CAGR of 12.3%.
https://www.maximizemarketresearch.com/market-report/global-application-delivery-network-market/64319/
03:19 AM - Sep 19, 2024 (UTC)
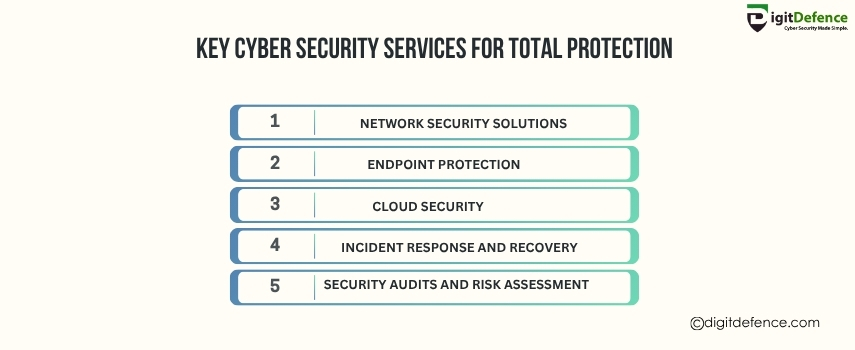
Key Cyber Security Services For Total Protection| Digitdefence
Key cybersecurity services offer comprehensive protection against cyber threats, ensuring your data, networks, and systems stay secure. These services include firewalls, encryption, and threat detection.
#CyberSecurity #DataProtection #networksecurity #BusinessProtection #ThreatDetection #encryption #CyberDefense #ITSecurity #SecureBusiness #TechSolutions
Key cybersecurity services offer comprehensive protection against cyber threats, ensuring your data, networks, and systems stay secure. These services include firewalls, encryption, and threat detection.
#CyberSecurity #DataProtection #networksecurity #BusinessProtection #ThreatDetection #encryption #CyberDefense #ITSecurity #SecureBusiness #TechSolutions
09:05 AM - May 13, 2025 (UTC)
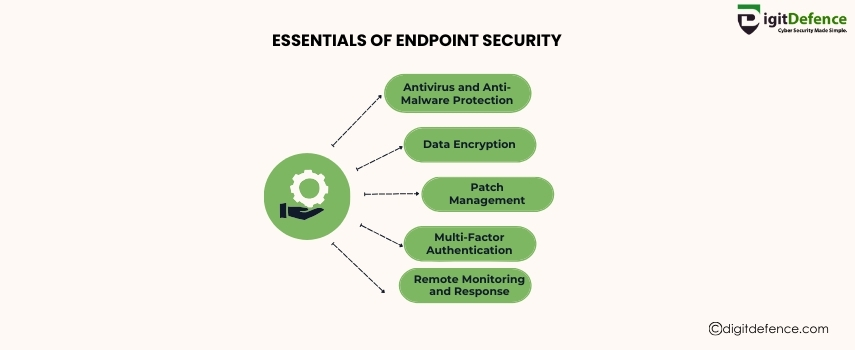
Essentials of Endpoint Security | Digitdefence
Endpoint security is crucial for protecting your business from cyber threats by securing devices like laptops, smartphones, and servers. Safeguard your endpoints to prevent unauthorized access and data breaches.
#EndpointSecurity #CyberSecurity #DataProtection #BusinessSecurity #ThreatPrevention #networksecurity #DataBreachPrevention
Endpoint security is crucial for protecting your business from cyber threats by securing devices like laptops, smartphones, and servers. Safeguard your endpoints to prevent unauthorized access and data breaches.
#EndpointSecurity #CyberSecurity #DataProtection #BusinessSecurity #ThreatPrevention #networksecurity #DataBreachPrevention
09:08 AM - May 10, 2025 (UTC)
✔Commvault Expands Cybersecurity Ecosystem with New Integrations
Commvault, a prominent player in the field of cyber resilience and data protection for hybrid cloud environments, has announced a significant expansion of its cybersecurity ecosystem
For More Information
?Read - https://cybrpro.com/commva...
and Get insights
#Commvault #CyberSecurity #Expands #Ecosystem #Integrations #DataProtection #Cyberpromagazine #cloudsecurity #BackupSolutions #ITInfrastructure #datamanagement #CyberThreats #SecurityCompliance #TechInnovation #networksecurity #EndpointProtection #DisasterRecovery #SecureData
Commvault, a prominent player in the field of cyber resilience and data protection for hybrid cloud environments, has announced a significant expansion of its cybersecurity ecosystem
For More Information
?Read - https://cybrpro.com/commva...
and Get insights
#Commvault #CyberSecurity #Expands #Ecosystem #Integrations #DataProtection #Cyberpromagazine #cloudsecurity #BackupSolutions #ITInfrastructure #datamanagement #CyberThreats #SecurityCompliance #TechInnovation #networksecurity #EndpointProtection #DisasterRecovery #SecureData

Commvault Expands Cybersecurity Ecosystem | CyberPro Magazine
Commvault, a prominent player in the field of cyber resilience and data protection for hybrid cloud environments, has announced a significant expansion of its cybersecurity ecosystem Read For more information
https://cybrpro.com/commvault-expands-cybersecurity-ecosystem/
04:28 AM - Aug 22, 2024 (UTC)
How To Implement Pentesting Network For Your Business | Digitdefence
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
08:55 AM - May 10, 2025 (UTC)
Sponsored by
OWT
5 months ago