Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
Learn Ethical Hacking & Security Testing From Experts! Get Certified, Gain Hands-On Skills, And Boost Your Cybersecurity Career.
Enroll Now - https://training.cyberhunt...
#pentesting #CyberSecurity #EthicalHacking #ITSecurity #CareerBoost
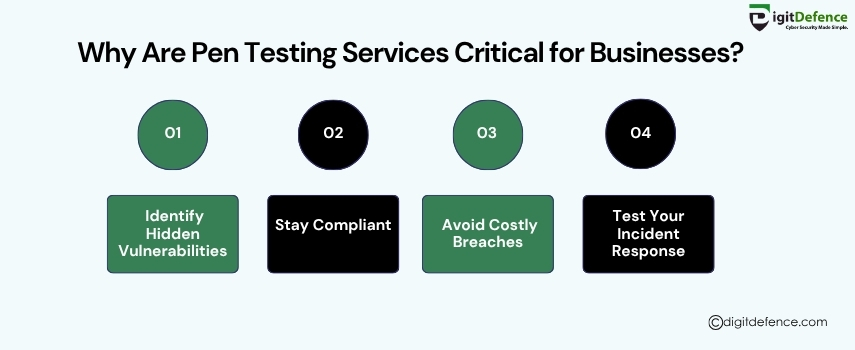
Pen Testing Services are essential for identifying hidden security gaps before attackers do, helping businesses prevent costly breaches and ensure compliance.
#pentesting #CyberSecurity #BusinessSecurity #VulnerabilityAssessment #DataProtection
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
While Mobile Application Pentesting focuses on technical breaches, Red Teaming takes security testing to the next level. Additionally, It simulates real-world cyberattacks to evaluate an organization’s overall defensive capacity. Red Teaming mimics real-world hacker strategies to test business security. It measures how efficiently security teams tackle cyber threats. Red Teaming also helps businesses redefine security tactics and defenses.
Read More: https://fortbridge.co.uk/r...
24/7, we are always dedicated to your service.
Email:-seodigitalz70gmail.com
Telegram:-seodigitalz
Skype:- seodigitalz
WhatsApp:- +1 (406) 217-0058
https://seodigitalz.com/pr...
#technology #pentesting #software #OpenSource #programmerlife #infosec #hackingtools
#php #peoplewhocode #nodejs #tech #fullstack #PythonProgramming #programmingmemes #Hack
#frontenddeveloper #ethicalhacker #programmers #reactjs #softwareengineer #fullstackdeveloper
#ProgrammingLanguage #cloudcomputing #AWS #frontend #webdev #webdesign #codingmemes #CyberSecurityAwareness #react

Buy Github Account | Verified & Aged GitHub Accounts 2025
Purchase Buy Github Account with full access. Get aged, high-reputation GitHub accounts for seamless development, collaboration, and credibility.
https://seodigitalz.com/product/buy-github-account/Learn more - https://training.cyberhunt...
#WebSecurity #VAPTServices #CyberSecurityExperts #ApplicationSecurity #VulnerabilityAssessment #pentesting #SecureApps #WebAppSecurity #DigitalDefense #EthicalHacking
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
Web app pentesting includes setting a clear goal, scanning for issues, testing manually, and fixing the problems. These steps help make the application safer and more secure.
Learn more at, www.digitdefence.com
While Mobile Application Pentesting urges upon technical breaches, Red Teaming takes security testing to the next level. Additionally, It boosts real-world cyberattacks to evaluate an organization’s overall defensive capacity.
Red Teaming acts like real-world hacker strategies to test business security.
It measures how efficiently security teams tackle cyber threats.
Read Teaming also helps businesses in redefining security tactics and defenses.
Read More: https://fortbridge.co.uk/r...

Red Teaming | FORTBRIDGE
Enhance your cybersecurity with FORTBRIDGE expert Red Teaming services. Identify vulnerabilities and strengthen your defenses effectively.
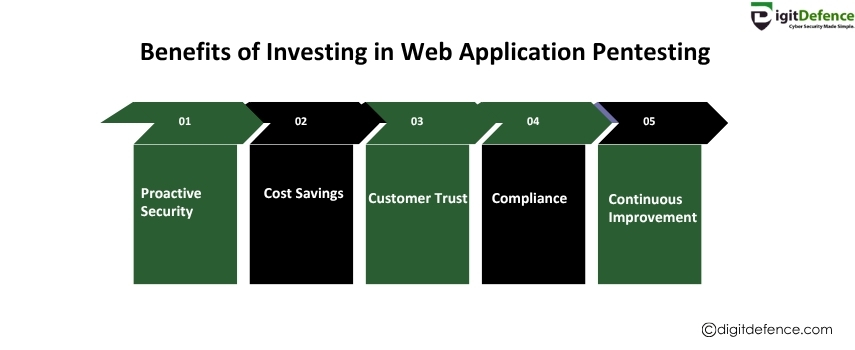
https://fortbridge.co.uk/red-teaming/Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
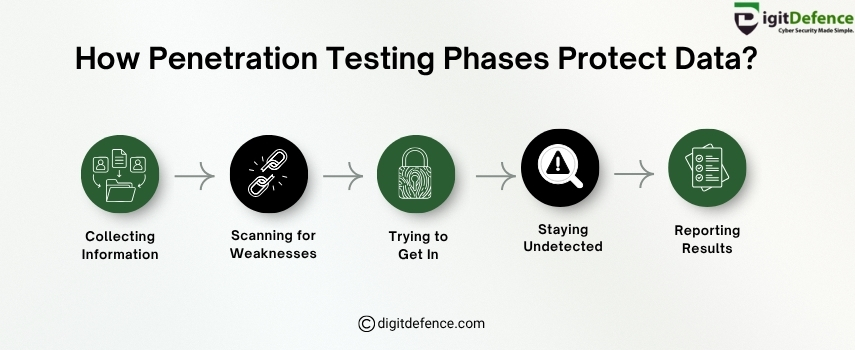
Penetration testing protects your data by following smart steps. It starts with collecting information, then scanning for weaknesses. Next, ethical hackers try to get in, stay hidden, and finally report the results. These phases help find and fix risks before hackers can use them.
Get your systems tested today.
Visit: www.digitdefence.com
#CyberSecurity #PenetrationTesting #pentesting #Digitdefence
Web Application Pentesting is like hiring someone to try and break into your online business—but it’s all just a simulation. These professionals are known as ethical hackers, and their job is to find weaknesses in your website before real hackers do. Through this process, they can uncover vulnerabilities such as account-related issues that provide easy entry points for attackers, flaws in how your site handles and stores sensitive information like credit card details, and small cracks in your website’s code that could be exploited. For more information contact @fortbridge .co.uk and call on 7842759960.
Read More: https://fortbridge.co.uk/w...

Web Application Pentesting | FORTBRIDGE
Ensure the security of your web applications with FORTBRIDGE UK's expert web application pentesting services. Protect your business from vulnerabilities.
https://fortbridge.co.uk/web-application-pen-testing/24/7, we are always dedicated to your service.
Email:-seodigitalz70gmail.com
Telegram:-seodigitalz
Skype:- seodigitalz
WhatsApp:- +1 (406) 217-0058
https://seodigitalz.com/pr...
#technology #pentesting #software #OpenSource #programmerlife #infosec #hackingtools
#php #peoplewhocode #nodejs #tech #fullstack #PythonProgramming #programmingmemes #Hack
#frontenddeveloper #ethicalhacker #programmers #reactjs #softwareengineer #fullstackdeveloper
#ProgrammingLanguage #cloudcomputing #AWS #frontend #webdev #webdesign #codingmemes #CyberSecurityAwareness #react

Buy Github Account | Verified & Aged GitHub Accounts 2025
Purchase Buy Github Account with full access. Get aged, high-reputation GitHub accounts for seamless development, collaboration, and credibility.
https://seodigitalz.com/product/buy-github-account/Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
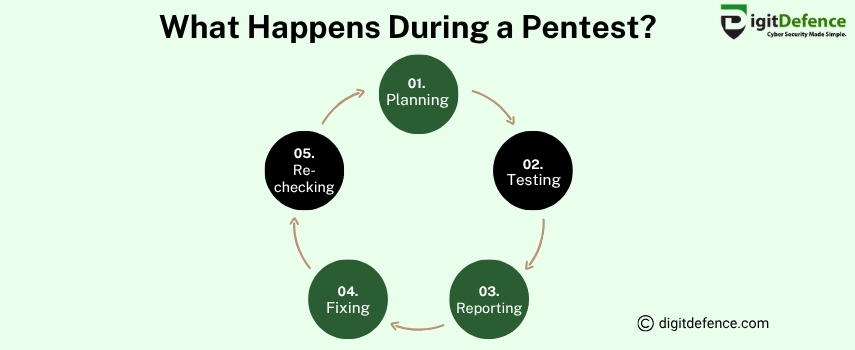
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess