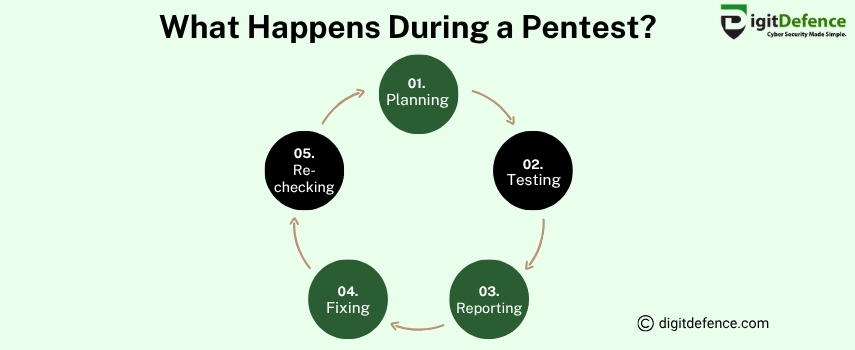
What Happens During a Pentest | Digitdefence
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
07:21 AM - Jun 26, 2025 (UTC)
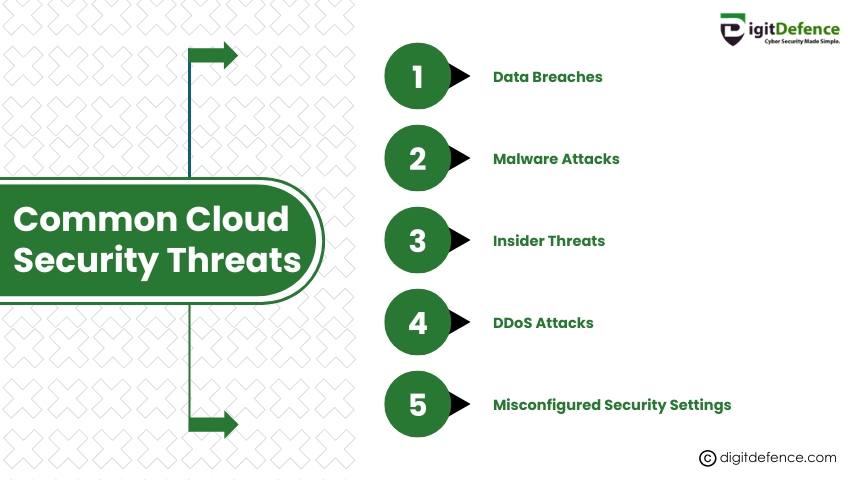
Common Cloud Security Threats | Digitdefence
Common cloud security threats include data breaches, misconfigured settings, and insecure APIs. Understanding them is key to building a secure cloud environment.
#cloudsecurity #CyberThreats #DataBreach #cloudcomputing #infosec #CloudProtection #CloudRisk #SecurityAwareness #cloudinfrastructure #SecureCloud
Common cloud security threats include data breaches, misconfigured settings, and insecure APIs. Understanding them is key to building a secure cloud environment.
#cloudsecurity #CyberThreats #DataBreach #cloudcomputing #infosec #CloudProtection #CloudRisk #SecurityAwareness #cloudinfrastructure #SecureCloud
10:16 AM - Jun 06, 2025 (UTC)
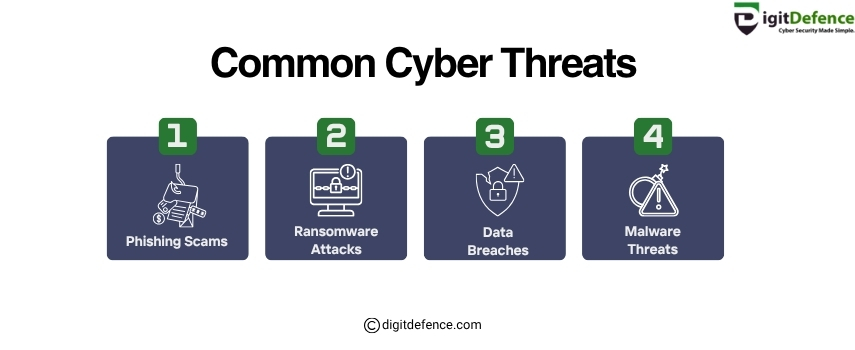
Common Cyber Threats | Digitdefence
Common cyber threats include malware, phishing attacks, ransomware, and data breaches. These threats can compromise sensitive information and disrupt business operations if not properly managed.
#CyberThreats #Malware #Phishing #Ransomware #DataBreach #CyberSecurityAwareness #OnlineSafety #infosec #ThreatPrevention #DigitalSecurity
Common cyber threats include malware, phishing attacks, ransomware, and data breaches. These threats can compromise sensitive information and disrupt business operations if not properly managed.
#CyberThreats #Malware #Phishing #Ransomware #DataBreach #CyberSecurityAwareness #OnlineSafety #infosec #ThreatPrevention #DigitalSecurity
06:44 AM - Jun 25, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
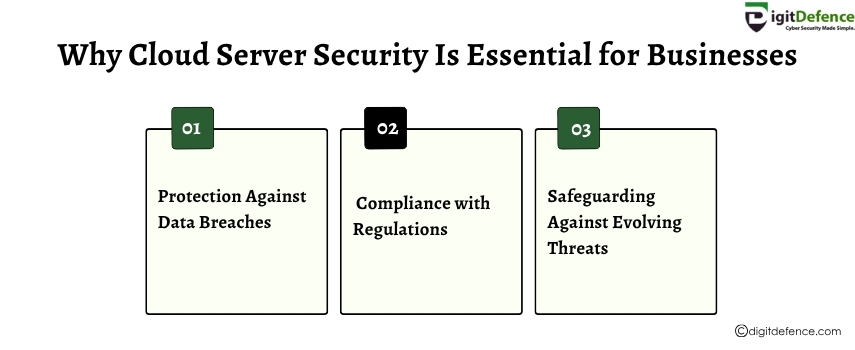
Why Cloud Server Security Is Essential For Businesses
Cloud Server Security is essential for businesses to protect sensitive data from breaches, ensure regulatory compliance, and maintain customer trust. Robust security safeguards against evolving cyber threats in cloud environments.
#CloudServerSecurity #DataProtection #CyberSecurity #cloudsecurity #BusinessSafety #Compliance #infosec
Cloud Server Security is essential for businesses to protect sensitive data from breaches, ensure regulatory compliance, and maintain customer trust. Robust security safeguards against evolving cyber threats in cloud environments.
#CloudServerSecurity #DataProtection #CyberSecurity #cloudsecurity #BusinessSafety #Compliance #infosec
09:26 AM - Jun 24, 2025 (UTC)
🔐💻 “Hackers Don’t Sleep, Why Should Your Cybersecurity?” 🚨🧠
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
12:51 PM - Jun 23, 2025 (UTC)
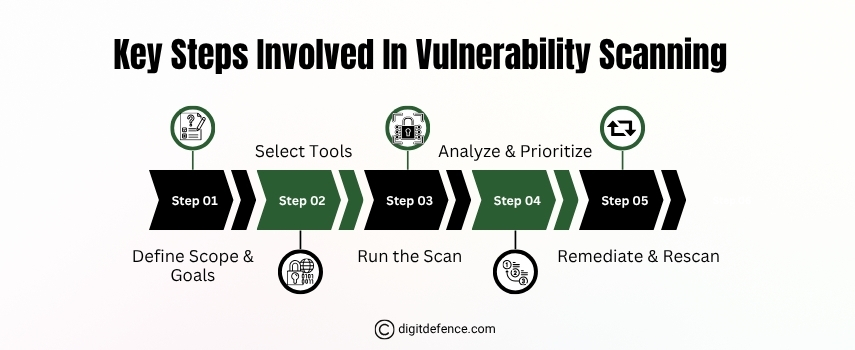
Key Steps Involved in Vulunerability Scanning | Digitdefence
Vulnerability scanning involves identifying security weaknesses in your system by scanning networks, servers, and applications for known threats. It helps businesses proactively fix issues before attackers exploit them.
#VulnerabilityScanning
#CyberSecurity
#networksecurity
#infosec
#SystemProtection
#RiskAssessment
#ITSecurity
Vulnerability scanning involves identifying security weaknesses in your system by scanning networks, servers, and applications for known threats. It helps businesses proactively fix issues before attackers exploit them.
#VulnerabilityScanning
#CyberSecurity
#networksecurity
#infosec
#SystemProtection
#RiskAssessment
#ITSecurity
06:06 AM - Jun 17, 2025 (UTC)
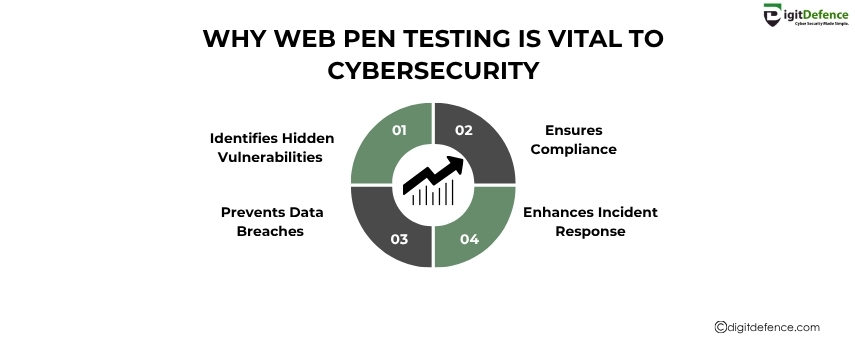
Why Web Pen Testing is Vital To Cybersecurity | Digitdefence
Web Pen Testing is vital to cybersecurity as it uncovers hidden vulnerabilities before attackers exploit them. Regular testing strengthens defenses, reduces breach risks, and ensures data protection.
#WebPenTesting #CyberSecurity #EthicalHacking #DataProtection #VulnerabilityAssessment #infosec
Web Pen Testing is vital to cybersecurity as it uncovers hidden vulnerabilities before attackers exploit them. Regular testing strengthens defenses, reduces breach risks, and ensures data protection.
#WebPenTesting #CyberSecurity #EthicalHacking #DataProtection #VulnerabilityAssessment #infosec
09:18 AM - Jun 24, 2025 (UTC)
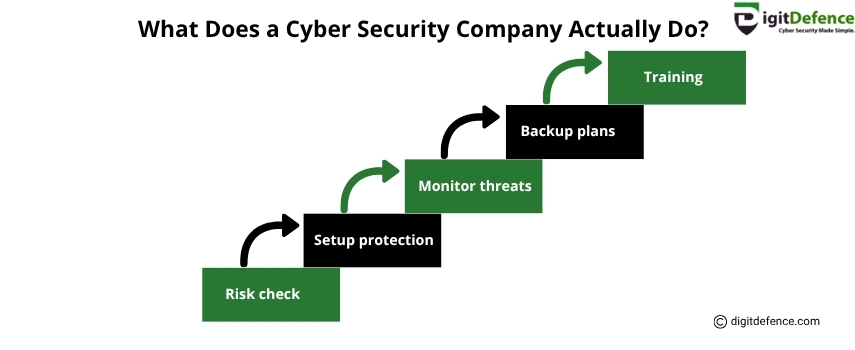
What Does a Cyber Security Company Do | Digitdefence
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
06:33 AM - Jun 25, 2025 (UTC)
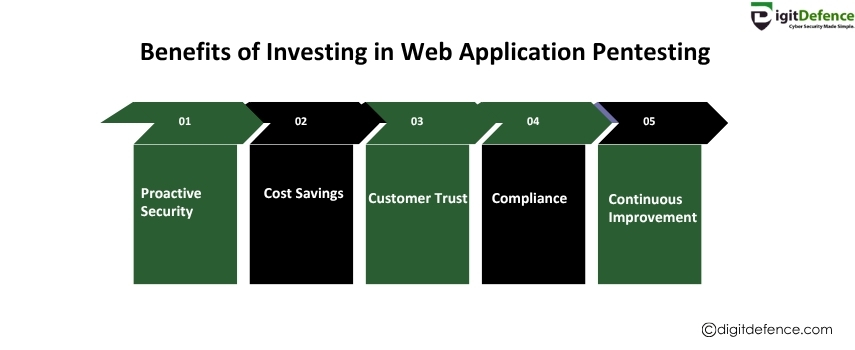
Benefits of Investing in Web Application Pentesting
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
07:12 AM - Jun 26, 2025 (UTC)
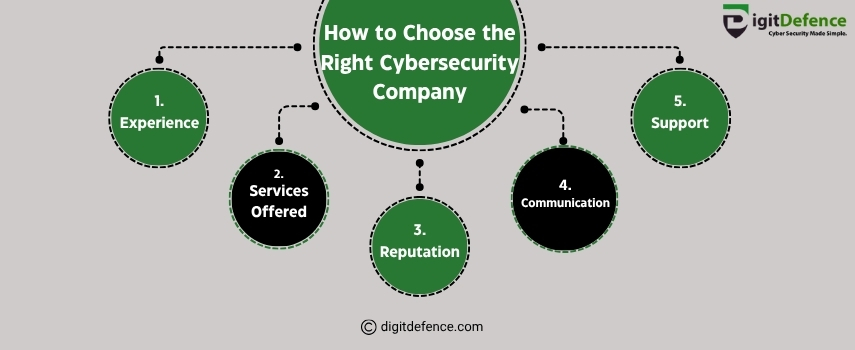
How to Choose the Right Cybersecurity Company | Digitdefence
Choosing the right cybersecurity company means finding experts who understand your business risks, offer tailored solutions, and provide proactive monitoring and quick response. Trust and proven experience are key to safeguarding your digital assets.
#CyberSecurity #ChooseRight #DataProtection #infosec #SecuritySolutions #CyberSecurityExperts
Choosing the right cybersecurity company means finding experts who understand your business risks, offer tailored solutions, and provide proactive monitoring and quick response. Trust and proven experience are key to safeguarding your digital assets.
#CyberSecurity #ChooseRight #DataProtection #infosec #SecuritySolutions #CyberSecurityExperts
07:03 AM - Jun 19, 2025 (UTC)
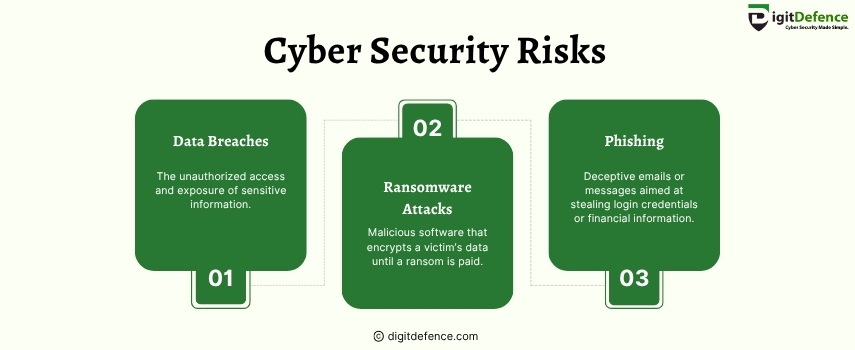
Cyber Security Risks | Digitdefence
Cyber security risks include threats like data breaches, malware attacks, and phishing scams that can compromise sensitive information and disrupt business operations. Staying vigilant and implementing strong security measures is essential to protect your assets.
#CyberSecurityRisks #DataProtection #CyberThreats #infosec #DigitalSecurity
Cyber security risks include threats like data breaches, malware attacks, and phishing scams that can compromise sensitive information and disrupt business operations. Staying vigilant and implementing strong security measures is essential to protect your assets.
#CyberSecurityRisks #DataProtection #CyberThreats #infosec #DigitalSecurity
09:11 AM - Jun 02, 2025 (UTC)
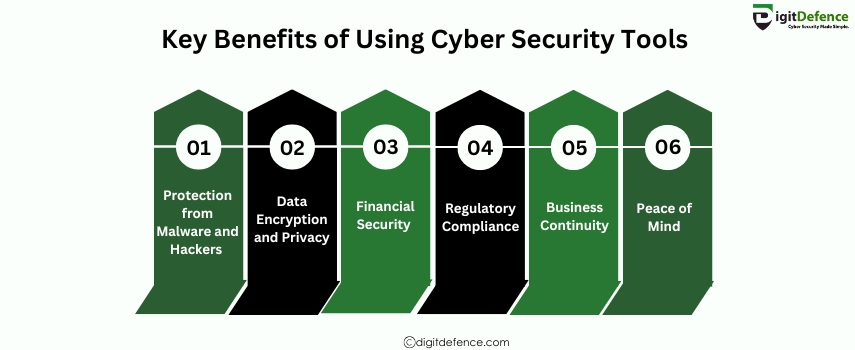
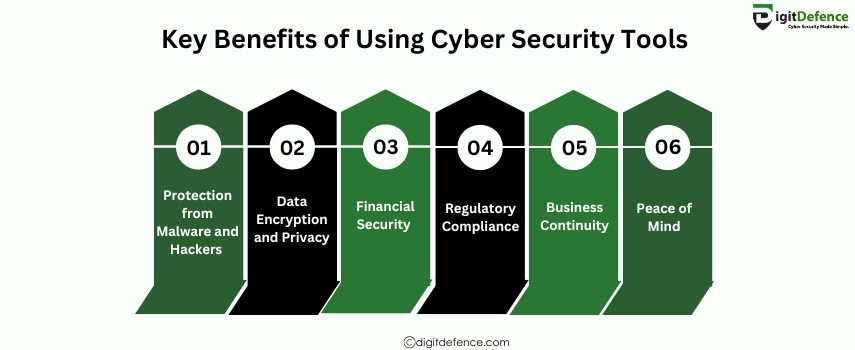
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:26 AM - Jun 13, 2025 (UTC)
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:28 AM - Jun 13, 2025 (UTC)
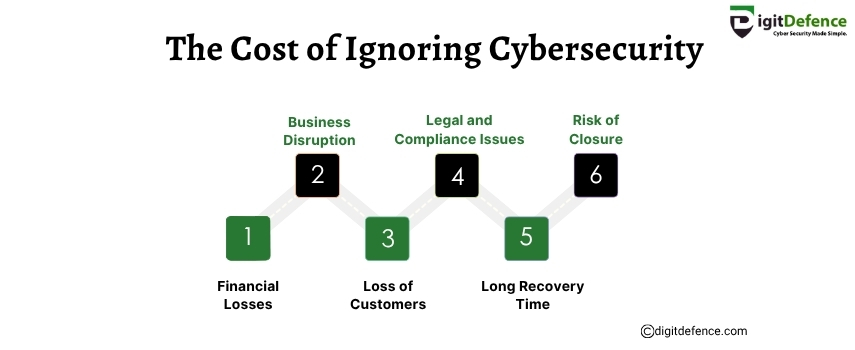
The Cost of Ignoring Cybersecurity | Digitdefence
Ignoring cybersecurity can lead to devastating data breaches, costly downtime, and severe damage to your brand’s reputation. Investing in robust security measures is essential to protect your business from financial losses and legal penalties.
#CyberSecurity #DataProtection #infosec #CyberAttack #BusinessSecurity #riskmanagement
Ignoring cybersecurity can lead to devastating data breaches, costly downtime, and severe damage to your brand’s reputation. Investing in robust security measures is essential to protect your business from financial losses and legal penalties.
#CyberSecurity #DataProtection #infosec #CyberAttack #BusinessSecurity #riskmanagement
06:54 AM - Jun 19, 2025 (UTC)
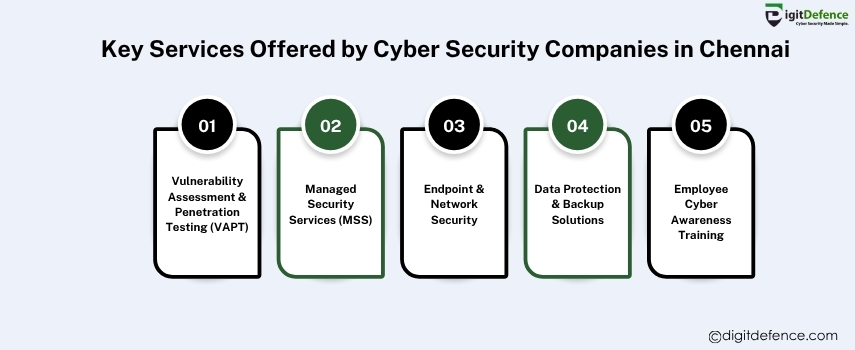
Key Services Offered By Cyber Security Companies in Chennai
Cyber security companies in Chennai provide essential services like threat detection, vulnerability assessment, penetration testing, and data protection to safeguard businesses from cyber attacks. They also offer managed security solutions and compliance consulting to ensure robust defense and regulatory adherence.
#CyberSecurity #DataProtection #ThreatDetection #PenetrationTesting #VulnerabilityAssessment #ManagedSecurity #infosec #ChennaiSecurity
Cyber security companies in Chennai provide essential services like threat detection, vulnerability assessment, penetration testing, and data protection to safeguard businesses from cyber attacks. They also offer managed security solutions and compliance consulting to ensure robust defense and regulatory adherence.
#CyberSecurity #DataProtection #ThreatDetection #PenetrationTesting #VulnerabilityAssessment #ManagedSecurity #infosec #ChennaiSecurity
08:58 AM - Jun 18, 2025 (UTC)