Benefits Of Choosing a Top Cyber Security Company in Ahmedabad
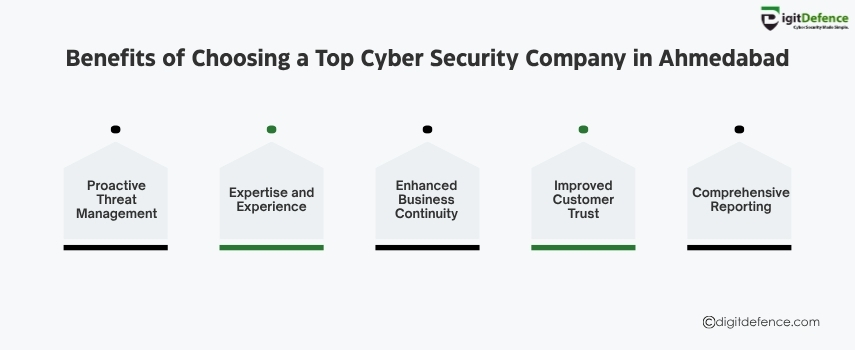
Choosing a top cybersecurity company in Ahmedabad ensures robust protection against evolving threats, minimizing risks and securing your critical business data. Benefit from expert threat detection and rapid incident response.
#CyberSecurityAhmedabad #DataProtection #ThreatDetection #CyberDefense #BusinessSecurity #networksecurity #CyberSafety #InformationSecurity #SecurityExperts #ahmedabadbusiness
Choosing a top cybersecurity company in Ahmedabad ensures robust protection against evolving threats, minimizing risks and securing your critical business data. Benefit from expert threat detection and rapid incident response.
#CyberSecurityAhmedabad #DataProtection #ThreatDetection #CyberDefense #BusinessSecurity #networksecurity #CyberSafety #InformationSecurity #SecurityExperts #ahmedabadbusiness
10:01 AM - Jun 27, 2025 (UTC)
(E)
Sponsored by
OWT
6 months ago
EDR vs XDR: Understanding the Key Differences and Choosing the Right Solution
https://app.box.com/s/3mqq...
Discover the core differences between EDR and XDR to strengthen your cybersecurity posture. From endpoint protection to extended threat detection, each solution offers unique advantages. Click here to learn which is right for your organization and improve your defense strategy today.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR
https://app.box.com/s/3mqq...
Discover the core differences between EDR and XDR to strengthen your cybersecurity posture. From endpoint protection to extended threat detection, each solution offers unique advantages. Click here to learn which is right for your organization and improve your defense strategy today.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR
06:03 PM - May 27, 2025 (UTC)
Key Benefits of Professional Network Security Services
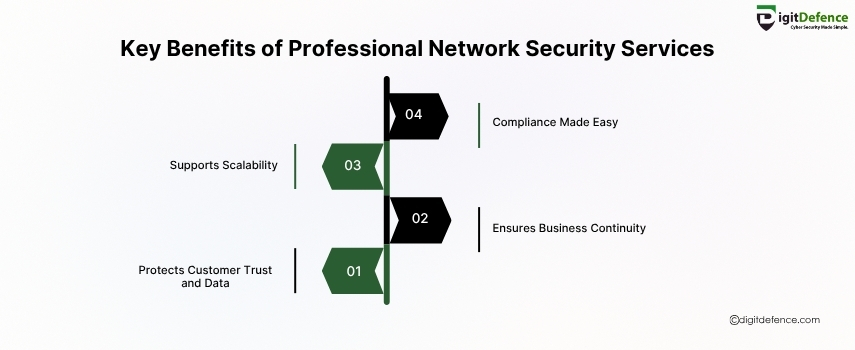
Professional network security services help small businesses prevent data breaches, ensure system uptime, and build customer trust. They offer 24/7 monitoring, threat detection, and peace of mind.
#networksecurity #Cybersecurityservices #SmallBusinessIT #DataProtection #SecureNetwork #BusinessSecurity #ThreatDetection #ITSupport #CyberResilience #SMBSecurity
Professional network security services help small businesses prevent data breaches, ensure system uptime, and build customer trust. They offer 24/7 monitoring, threat detection, and peace of mind.
#networksecurity #Cybersecurityservices #SmallBusinessIT #DataProtection #SecureNetwork #BusinessSecurity #ThreatDetection #ITSupport #CyberResilience #SMBSecurity
09:24 AM - Jul 09, 2025 (UTC)
Key Cyber Security Services For Total Protection| Digitdefence
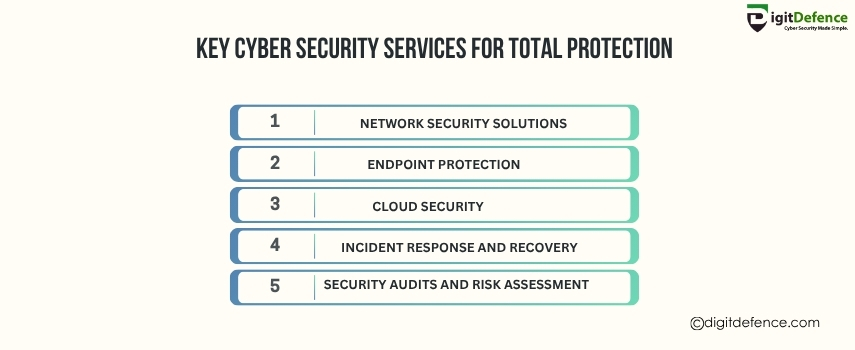
Key cybersecurity services offer comprehensive protection against cyber threats, ensuring your data, networks, and systems stay secure. These services include firewalls, encryption, and threat detection.
#CyberSecurity #DataProtection #networksecurity #BusinessProtection #ThreatDetection #encryption #CyberDefense #ITSecurity #SecureBusiness #TechSolutions
Key cybersecurity services offer comprehensive protection against cyber threats, ensuring your data, networks, and systems stay secure. These services include firewalls, encryption, and threat detection.
#CyberSecurity #DataProtection #networksecurity #BusinessProtection #ThreatDetection #encryption #CyberDefense #ITSecurity #SecureBusiness #TechSolutions
09:05 AM - May 13, 2025 (UTC)
Core Services Offered By a Cyber Security Company in Coimbatore
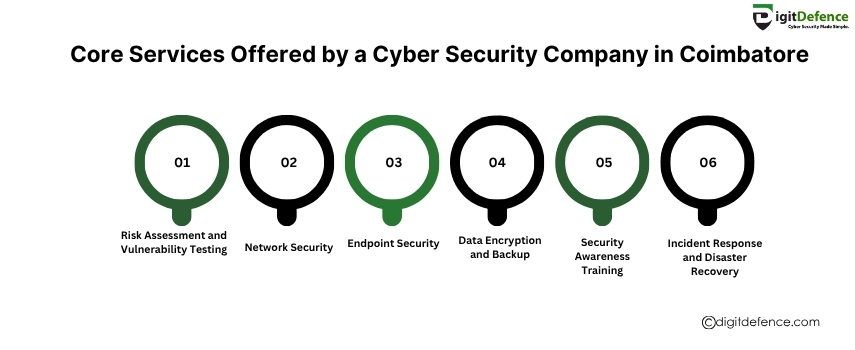
A reliable cyber security company in Coimbatore provides essential services like risk assessment, network security, threat detection, data encryption, and incident response to protect your business from evolving cyber threats.
#CyberSecurityCoimbatore #RiskAssessment #networksecurity #ThreatDetection #DataEncryption #IncidentResponse #BusinessProtection
A reliable cyber security company in Coimbatore provides essential services like risk assessment, network security, threat detection, data encryption, and incident response to protect your business from evolving cyber threats.
#CyberSecurityCoimbatore #RiskAssessment #networksecurity #ThreatDetection #DataEncryption #IncidentResponse #BusinessProtection
06:55 AM - Jun 21, 2025 (UTC)
How to Choose the Right Web App Pentesting Provider | Digitdefence
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
09:51 AM - Jun 27, 2025 (UTC)
Key Components of Cloud Network Security | Digitdefence
Key components of cloud network security include firewalls, encryption, identity and access management, and continuous monitoring to protect data and applications in the cloud.
#CloudNetworkSecurity #DataProtection #CyberSecurity #cloudsecurity #encryption #IAM #networksecurity #ThreatDetection #CloudSafety #SecureCloud
Key components of cloud network security include firewalls, encryption, identity and access management, and continuous monitoring to protect data and applications in the cloud.
#CloudNetworkSecurity #DataProtection #CyberSecurity #cloudsecurity #encryption #IAM #networksecurity #ThreatDetection #CloudSafety #SecureCloud
08:55 AM - Jun 30, 2025 (UTC)
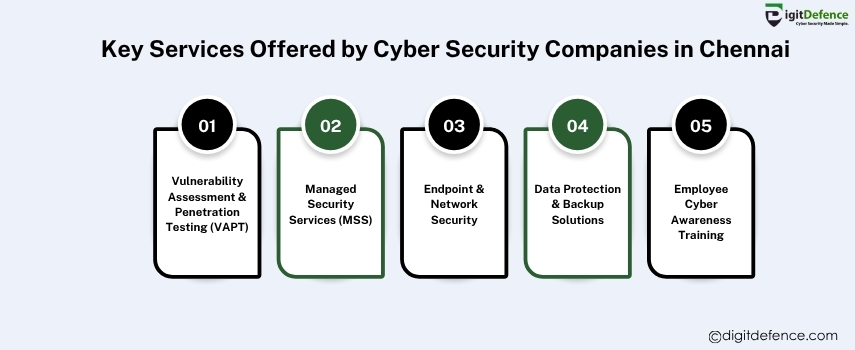
Key Services Offered By Cyber Security Companies in Chennai
Cyber security companies in Chennai provide essential services like threat detection, vulnerability assessment, penetration testing, and data protection to safeguard businesses from cyber attacks. They also offer managed security solutions and compliance consulting to ensure robust defense and regulatory adherence.
#CyberSecurity #DataProtection #ThreatDetection #PenetrationTesting #VulnerabilityAssessment #ManagedSecurity #infosec #ChennaiSecurity
Cyber security companies in Chennai provide essential services like threat detection, vulnerability assessment, penetration testing, and data protection to safeguard businesses from cyber attacks. They also offer managed security solutions and compliance consulting to ensure robust defense and regulatory adherence.
#CyberSecurity #DataProtection #ThreatDetection #PenetrationTesting #VulnerabilityAssessment #ManagedSecurity #infosec #ChennaiSecurity
08:58 AM - Jun 18, 2025 (UTC)
Revolutionizing XDR with Gen AI: Next-Level Security Analysis for Advanced Threat Protection
https://www.seqrite.com/bl...
Gen AI is transforming XDR by enabling faster, smarter threat detection and real-time response. This evolution boosts visibility, reduces alert fatigue, and enhances security workflows. Read this blog to discover how AI-driven XDR is reshaping modern cybersecurity strategies.
#XDR #GenAI #CyberSecurity #ThreatDetection #AdvancedThreatProtection #SeqriteXDR
https://www.seqrite.com/bl...
Gen AI is transforming XDR by enabling faster, smarter threat detection and real-time response. This evolution boosts visibility, reduces alert fatigue, and enhances security workflows. Read this blog to discover how AI-driven XDR is reshaping modern cybersecurity strategies.
#XDR #GenAI #CyberSecurity #ThreatDetection #AdvancedThreatProtection #SeqriteXDR

Revolutionizing XDR with Gen AI Cybersecurity | Seqrite
Discover how Seqrite XDR, powered by Gen AI cybersecurity, transforms threat detection and response for advanced protection. Explore SIA’s AI-driven security analysis.
https://www.seqrite.com/blog/revolutionizing-xdr-gen-ai-cybersecurity-seqrite/
11:00 AM - May 27, 2025 (UTC)
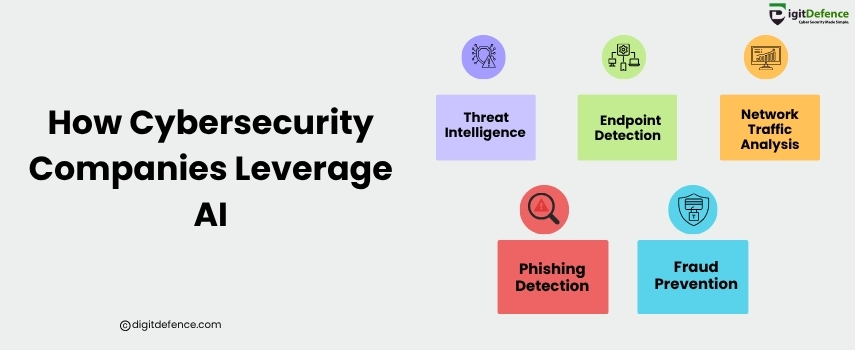
How Cybersecurity Companies Leverage AI | Digitdefence
Cybersecurity companies use AI to detect threats faster, automate responses, and analyze vast amounts of data in real time. This helps prevent breaches and strengthens overall security posture.
#CyberSecurity #AIinSecurity #ThreatDetection #SmartSecurity #CyberDefense
Cybersecurity companies use AI to detect threats faster, automate responses, and analyze vast amounts of data in real time. This helps prevent breaches and strengthens overall security posture.
#CyberSecurity #AIinSecurity #ThreatDetection #SmartSecurity #CyberDefense
09:18 AM - Jun 09, 2025 (UTC)
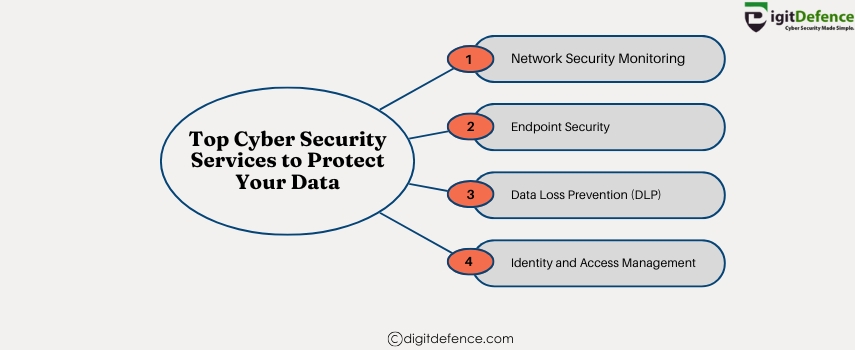
Top Cybersecurity Services to Protect Your Data | Digitdefence
Top cybersecurity services include threat detection, data encryption, and continuous monitoring to safeguard your sensitive information from cyberattacks. Investing in these solutions helps businesses maintain trust and ensure regulatory compliance.
#CyberSecurity #DataProtection #ThreatDetection #encryption #BusinessSecurity #infosec
Top cybersecurity services include threat detection, data encryption, and continuous monitoring to safeguard your sensitive information from cyberattacks. Investing in these solutions helps businesses maintain trust and ensure regulatory compliance.
#CyberSecurity #DataProtection #ThreatDetection #encryption #BusinessSecurity #infosec
09:43 AM - May 24, 2025 (UTC)
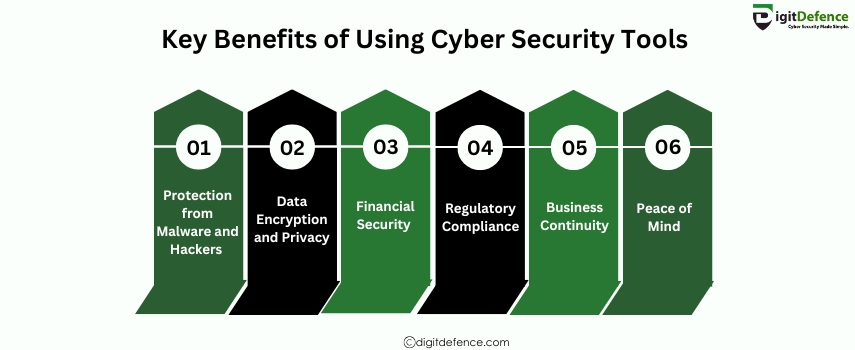
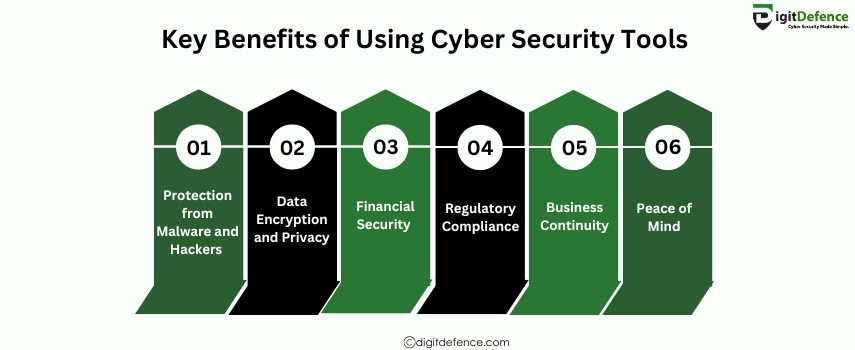
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:26 AM - Jun 13, 2025 (UTC)
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:28 AM - Jun 13, 2025 (UTC)
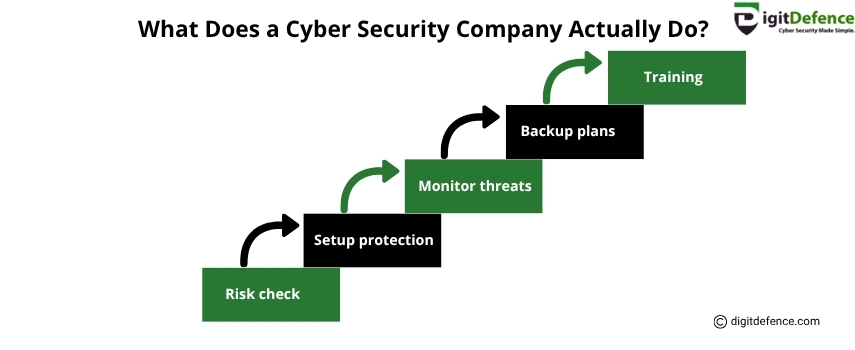
What Does a Cyber Security Company Do | Digitdefence
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
06:33 AM - Jun 25, 2025 (UTC)
EDR vs XDR: Understanding the Differences and Choosing the Right Solution
https://www.seqrite.com/bl...
Navigate the complexities of cybersecurity with our deep dive into EDR vs XDR. Learn the core differences, functionalities, and how each solution contributes to your overall security posture. Read this blog to make an informed decision for robust threat detection and response.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR
https://www.seqrite.com/bl...
Navigate the complexities of cybersecurity with our deep dive into EDR vs XDR. Learn the core differences, functionalities, and how each solution contributes to your overall security posture. Read this blog to make an informed decision for robust threat detection and response.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR

EDR vs XDR: Understand the Key Differences & Choose the Right Solution
Learn the critical differences between EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) aka EDR vs. XDR. Discover their features, benefits, and when to choose each for optimal cybersecurity.
https://www.seqrite.com/blog/edr-vs-xdr-differences-choosing-right-solution/
09:53 AM - Jun 10, 2025 (UTC)