How to Choose the Right Web App Pentesting Provider | Digitdefence
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
09:51 AM - Jun 27, 2025 (UTC)
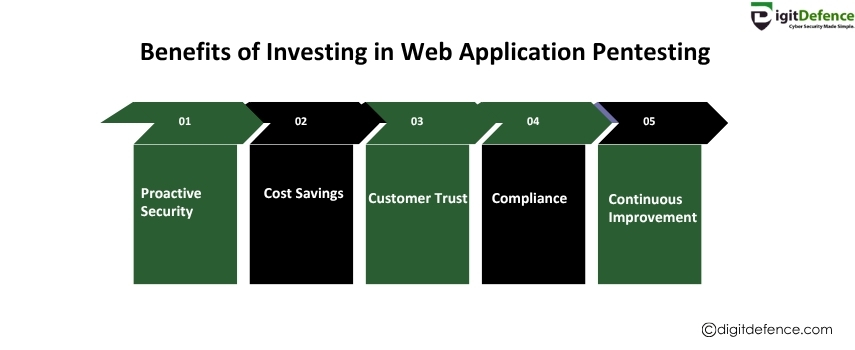
Benefits of Investing in Web Application Pentesting
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
07:12 AM - Jun 26, 2025 (UTC)
Other Specialized Types of Testing: A Comprehensive Guide
#PerformanceTesting #securitytesting #UsabilityTesting #CompatibilityTesting #RegressionTesting #StressTesting #LoadTesting #AcceptanceTesting #automationtesting
https://eautocar.co.uk/oth...
#PerformanceTesting #securitytesting #UsabilityTesting #CompatibilityTesting #RegressionTesting #StressTesting #LoadTesting #AcceptanceTesting #automationtesting
https://eautocar.co.uk/oth...

Other Specialized Types of Testing: A Comprehensive Guide - vehicle information and reviews
In the fast-paced world of software development, testing plays a critical role in ensuring applications function seamlessly, meet user expectations,...
https://eautocar.co.uk/other-specialized-types-of-testing-a-comprehensive-guide/
05:06 AM - Dec 24, 2024 (UTC)
Quality Assurance Services - Innow8 Apps
Ensure flawless performance with Innow8 Apps' Quality Assurance Services! Our expert QA team rigorously tests your software for functionality, security, and user experience, guaranteeing a seamless and bug-free product. Deliver top-notch applications with our end-to-end testing solutions.
Visit: https://innow8apps.com/qua...
#QualityAssurance #softwaretesting #BugFreeApps #QAExperts #apptesting #SoftwareDevelopment #testingservices #PerformanceTesting #securitytesting #Innow8Apps
Ensure flawless performance with Innow8 Apps' Quality Assurance Services! Our expert QA team rigorously tests your software for functionality, security, and user experience, guaranteeing a seamless and bug-free product. Deliver top-notch applications with our end-to-end testing solutions.
Visit: https://innow8apps.com/qua...
#QualityAssurance #softwaretesting #BugFreeApps #QAExperts #apptesting #SoftwareDevelopment #testingservices #PerformanceTesting #securitytesting #Innow8Apps
09:15 AM - Feb 06, 2025 (UTC)
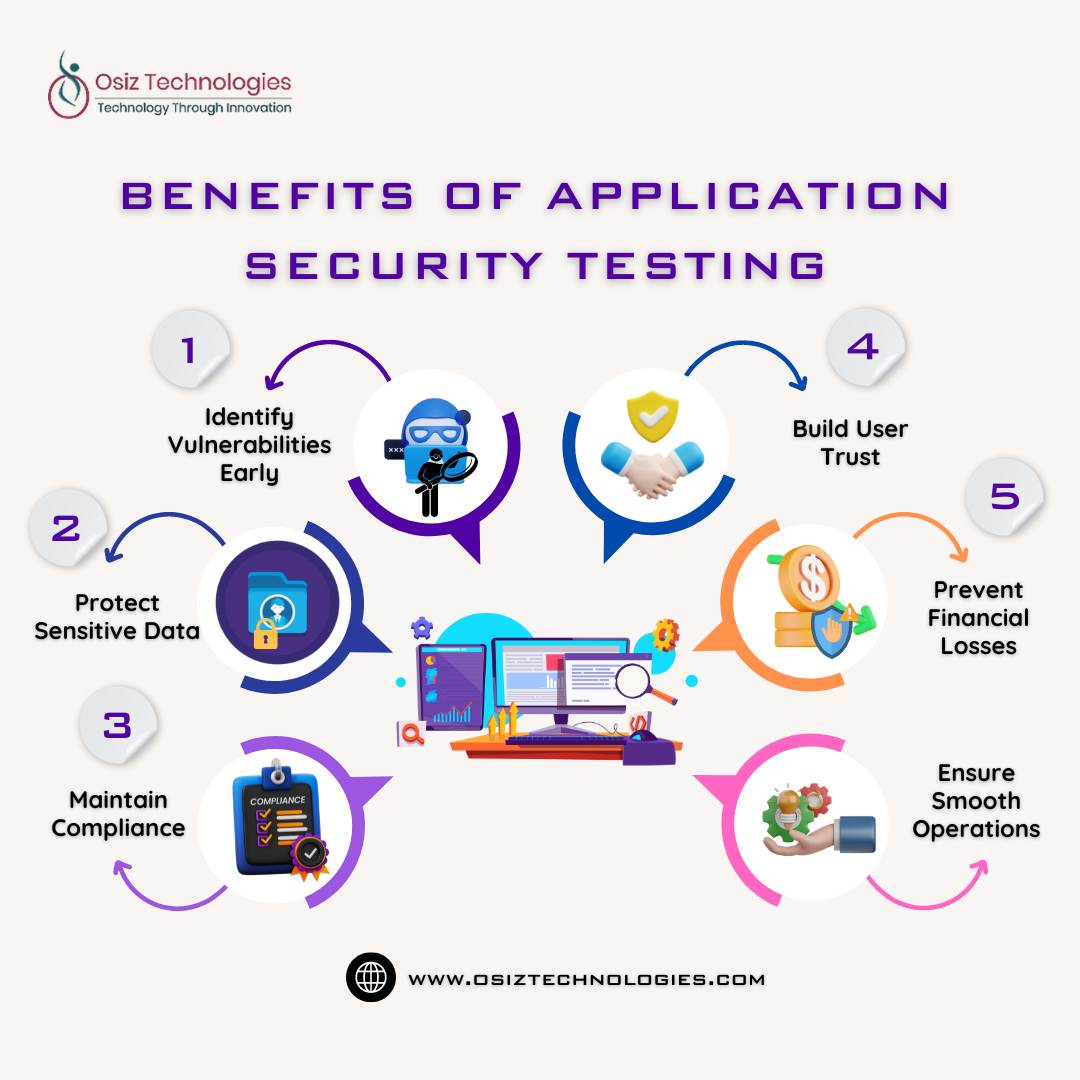
In today's threat landscape, robust application security is crucial. Osiz offers a suite of services to protect your applications, including penetration testing, vulnerability scanning, and DDoS mitigation. Our experienced consultants ensure your applications are built with security in mind, from design to deployment.
Contact Us >> https://www.osiztechnologi...
#appsecurity #applicationsecuritytesting #testing #securitytesting #appsecuritytesting #CyberSecurity #CybersecuritySolutions #osizdigitalsolutions #Osiztechnologies
Contact Us >> https://www.osiztechnologi...
#appsecurity #applicationsecuritytesting #testing #securitytesting #appsecuritytesting #CyberSecurity #CybersecuritySolutions #osizdigitalsolutions #Osiztechnologies
01:01 PM - Jul 09, 2024 (UTC)
What Happens During a Penetration Test | Digitdefence
During a penetration test, ethical hackers simulate cyberattacks to identify vulnerabilities in your systems and applications, helping to improve security. It's a proactive approach to safeguarding your data.
#PenetrationTesting #CyberSecurity #EthicalHacking #VulnerabilityAssessment #DataProtection #CyberDefense #securitytesting #BusinessSafety
During a penetration test, ethical hackers simulate cyberattacks to identify vulnerabilities in your systems and applications, helping to improve security. It's a proactive approach to safeguarding your data.
#PenetrationTesting #CyberSecurity #EthicalHacking #VulnerabilityAssessment #DataProtection #CyberDefense #securitytesting #BusinessSafety
09:36 AM - Apr 29, 2025 (UTC)
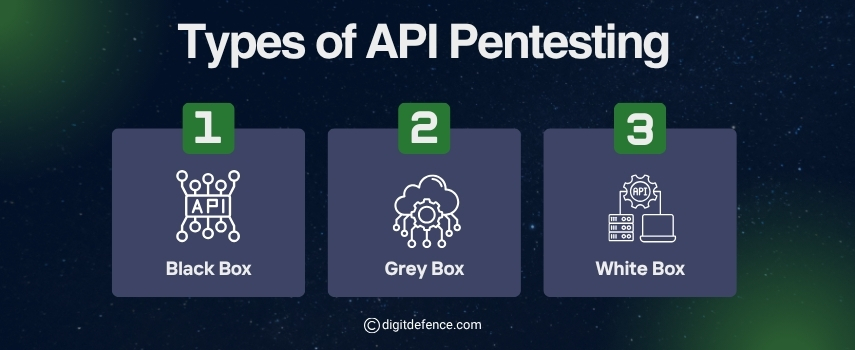
Types of API Testing | Digitdefence
API testing involves verifying that application programming interfaces (APIs) function correctly, reliably, and securely. It includes types like functional testing, load testing, security testing, and validation of data responses to ensure seamless integration between software components.
#APItesting #softwaretesting #FunctionalTesting #LoadTesting #securitytesting #automationtesting #QualityAssurance #TechTesting
API testing involves verifying that application programming interfaces (APIs) function correctly, reliably, and securely. It includes types like functional testing, load testing, security testing, and validation of data responses to ensure seamless integration between software components.
#APItesting #softwaretesting #FunctionalTesting #LoadTesting #securitytesting #automationtesting #QualityAssurance #TechTesting
08:48 AM - Jun 18, 2025 (UTC)
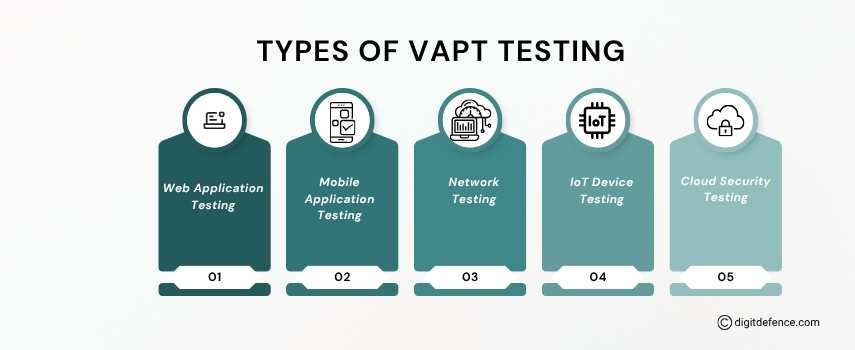
Types of VAPT Testing | Digitdefence
Types of VAPT (Vulnerability Assessment and Penetration Testing) include Network VAPT, Web Application VAPT, Mobile Application VAPT, and Wireless Network VAPT, each focusing on identifying vulnerabilities in specific areas of your infrastructure. These tests help businesses uncover potential security flaws, assess risk, and strengthen their defense mechanisms against cyber threats.
#VAPT #CyberSecurity #PenetrationTesting #networksecurity #WebApplicationSecurity #MobileSecurity #RiskAssessment #CyberThreats #securitytesting #DataProtection
Types of VAPT (Vulnerability Assessment and Penetration Testing) include Network VAPT, Web Application VAPT, Mobile Application VAPT, and Wireless Network VAPT, each focusing on identifying vulnerabilities in specific areas of your infrastructure. These tests help businesses uncover potential security flaws, assess risk, and strengthen their defense mechanisms against cyber threats.
#VAPT #CyberSecurity #PenetrationTesting #networksecurity #WebApplicationSecurity #MobileSecurity #RiskAssessment #CyberThreats #securitytesting #DataProtection
09:40 AM - Jun 11, 2025 (UTC)
Why Network Pen Testing Is Essential | Digitdefence
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
10:55 AM - Jun 12, 2025 (UTC)
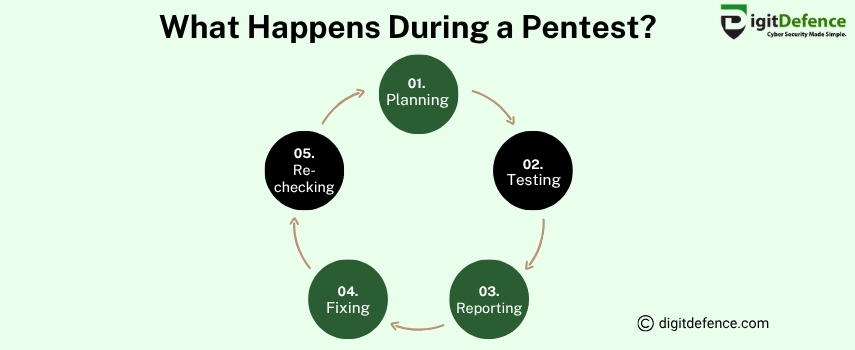
What Happens During a Pentest | Digitdefence
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
07:21 AM - Jun 26, 2025 (UTC)
Types of Software Testing You Need to Know
#softwaretesting #QualityAssurance #UnitTesting #IntegrationTesting #FunctionalTesting #PerformanceTesting #securitytesting #UserAcceptanceTesting
https://www.gettoplists.co...
#softwaretesting #QualityAssurance #UnitTesting #IntegrationTesting #FunctionalTesting #PerformanceTesting #securitytesting #UserAcceptanceTesting
https://www.gettoplists.co...

Types of Software Testing You Need to Know - Get Top Lists
Software testing is an essential part of the software development process, ensuring that applications run smoothly and meet required standards. Through
https://www.gettoplists.com/2024/10/19/types-of-software-testing-you-need-to-know/
04:37 AM - Oct 21, 2024 (UTC)
How To Implement Pentesting Network For Your Business | Digitdefence
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
08:55 AM - May 10, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
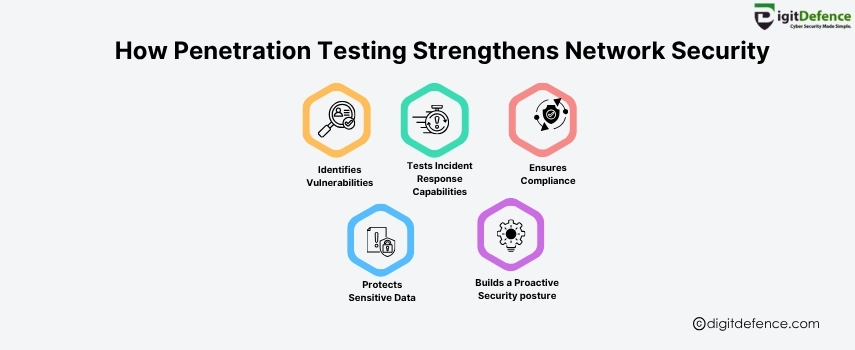
How Penetration Testing Strengthens Network Security | Digitdefence
Penetration testing identifies hidden vulnerabilities before attackers can exploit them, strengthening your network’s defense proactively.
#PenetrationTesting #networksecurity #CyberDefense #VAPT #securitytesting
Penetration testing identifies hidden vulnerabilities before attackers can exploit them, strengthening your network’s defense proactively.
#PenetrationTesting #networksecurity #CyberDefense #VAPT #securitytesting
09:12 AM - Jun 07, 2025 (UTC)
How To Implement Effective Security Testing For Your Business
Implementing effective security testing helps safeguard your business from cyber threats and ensures data protection. Stay ahead with proactive security measures!
#securitytesting #CyberSecurity #BusinessProtection #riskmanagement #datasecurity #PenetrationTesting #ITSecurity
Implementing effective security testing helps safeguard your business from cyber threats and ensures data protection. Stay ahead with proactive security measures!
#securitytesting #CyberSecurity #BusinessProtection #riskmanagement #datasecurity #PenetrationTesting #ITSecurity
09:24 AM - May 20, 2025 (UTC)