Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
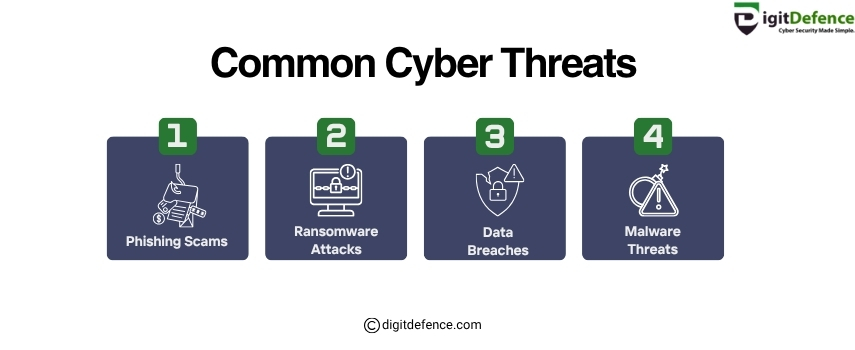
Common Cyber Threats | Digitdefence
Common cyber threats include malware, phishing attacks, ransomware, and data breaches. These threats can compromise sensitive information and disrupt business operations if not properly managed.
#CyberThreats #Malware #Phishing #Ransomware #DataBreach #CyberSecurityAwareness #OnlineSafety #infosec #ThreatPrevention #DigitalSecurity
Common cyber threats include malware, phishing attacks, ransomware, and data breaches. These threats can compromise sensitive information and disrupt business operations if not properly managed.
#CyberThreats #Malware #Phishing #Ransomware #DataBreach #CyberSecurityAwareness #OnlineSafety #infosec #ThreatPrevention #DigitalSecurity
06:44 AM - Jun 25, 2025 (UTC)
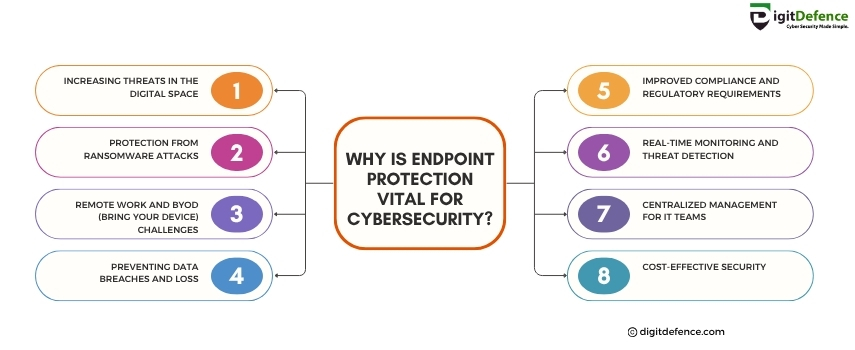
Why is Endpoint Protection Vital For CyberSecurity | Digitdefence
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
06:44 AM - Jun 13, 2025 (UTC)
A Step-by-Step Guide to Ledger Live Download
If you're looking to secure your cryptocurrency and manage your digital assets with confidence, Ledger Live download is the first step towards achieving that. This official application by Ledger helps you interact with your hardware wallet, making crypto management both safe and simple. Here's how you can easily download and set up Ledger Live.
The first and most crucial step is to ensure you’re downloading Ledger Live from the correct source. Always go to the official Ledger website—Ledger.com/start—to get the app. This guarantees you're getting the authentic version of the software, free from malware or third-party interference. Avoid downloading from unofficial sites to keep your crypto assets secure.
Ledger Live download is the first step to managing your cryptocurrency securely. By following these steps and downloading the app from the official source, you’re on your way to safely managing your digital assets with full control.
Visit our site- https://downlodeliveledge....
If you're looking to secure your cryptocurrency and manage your digital assets with confidence, Ledger Live download is the first step towards achieving that. This official application by Ledger helps you interact with your hardware wallet, making crypto management both safe and simple. Here's how you can easily download and set up Ledger Live.
The first and most crucial step is to ensure you’re downloading Ledger Live from the correct source. Always go to the official Ledger website—Ledger.com/start—to get the app. This guarantees you're getting the authentic version of the software, free from malware or third-party interference. Avoid downloading from unofficial sites to keep your crypto assets secure.
Ledger Live download is the first step to managing your cryptocurrency securely. By following these steps and downloading the app from the official source, you’re on your way to safely managing your digital assets with full control.
Visit our site- https://downlodeliveledge....
06:35 AM - Jun 16, 2025 (UTC)
Unlocking the Power of Your Digital Assets with Ledger Live Wallet
When it comes to managing your cryptocurrency securely, the Ledger Live Wallet stands out as one of the most reliable and user-friendly solutions available today. As a companion to Ledger’s hardware wallets, like the Ledger Nano X and Ledger Nano S, the Ledger Live Wallet offers a seamless experience for securely managing, sending, and receiving digital assets.
What makes the Ledger Live Wallet unique is its robust combination of security and convenience. It’s designed to work exclusively with Ledger’s hardware devices, ensuring that your private keys never leave the device and are never exposed to the internet. This makes your crypto holdings far less vulnerable to hacks or malware compared to software-only wallets. The only way to approve transactions is by physically confirming them on your Ledger device, adding an extra layer of protection.
In conclusion, if you’re looking for a secure, all-in-one solution to manage your digital assets, the Ledger Live Wallet is a top-tier choice. It combines cutting-edge security with ease of use, empowering you to take full control of your crypto portfolio.
Visit our site- https://live-ledgers-walle...
When it comes to managing your cryptocurrency securely, the Ledger Live Wallet stands out as one of the most reliable and user-friendly solutions available today. As a companion to Ledger’s hardware wallets, like the Ledger Nano X and Ledger Nano S, the Ledger Live Wallet offers a seamless experience for securely managing, sending, and receiving digital assets.
What makes the Ledger Live Wallet unique is its robust combination of security and convenience. It’s designed to work exclusively with Ledger’s hardware devices, ensuring that your private keys never leave the device and are never exposed to the internet. This makes your crypto holdings far less vulnerable to hacks or malware compared to software-only wallets. The only way to approve transactions is by physically confirming them on your Ledger device, adding an extra layer of protection.
In conclusion, if you’re looking for a secure, all-in-one solution to manage your digital assets, the Ledger Live Wallet is a top-tier choice. It combines cutting-edge security with ease of use, empowering you to take full control of your crypto portfolio.
Visit our site- https://live-ledgers-walle...
06:42 AM - Jun 11, 2025 (UTC)
Boost your online store’s performance with Australian website hosting by Creative People Web Hosting Services. Our powerful hosting platform is optimized for speed, security, and scalability - perfect for eCommerce websites on WooCommerce, Shopify, or Magento. Furthermore, we include features like free SSL, daily backups, and malware protection to keep your store running smoothly and securely. More: https://www.creativepeople...
05:10 AM - Jun 12, 2025 (UTC)
Common Cyber Threats to Businesses | IIFIS
This picture shows common cyber risks to businesses, such as phishing attacks, ransomware, data breaches, malware, and insider threats. These threats underline the importance of strong cybersecurity solutions to secure sensitive data and ensure corporate integrity.
https://iifis.org/blog/wha...
This picture shows common cyber risks to businesses, such as phishing attacks, ransomware, data breaches, malware, and insider threats. These threats underline the importance of strong cybersecurity solutions to secure sensitive data and ensure corporate integrity.
https://iifis.org/blog/wha...
12:10 PM - Jun 18, 2025 (UTC)
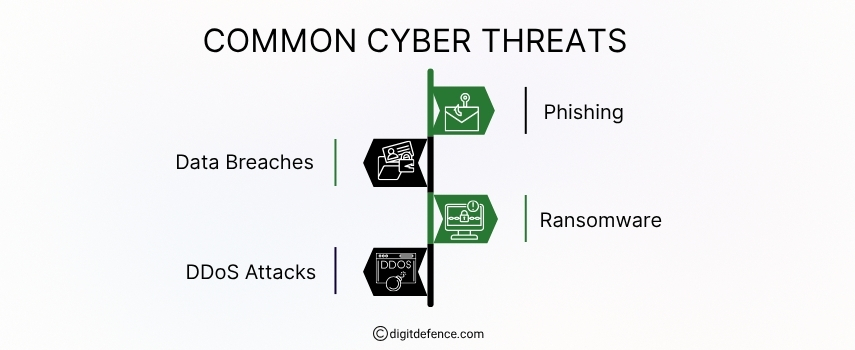
Common Cyber Threats | Digitdefence
Common cyber threats include phishing attacks, where hackers trick you into giving up personal info, and malware, which can silently steal data or damage systems. Staying alert and using good security tools can help keep you safe.
#CyberSecurity #PhishingAwareness#MalwareProtection
#OnlineSafety #CyberThreats#DataSecurity#StaySafeOnline
Common cyber threats include phishing attacks, where hackers trick you into giving up personal info, and malware, which can silently steal data or damage systems. Staying alert and using good security tools can help keep you safe.
#CyberSecurity #PhishingAwareness#MalwareProtection
#OnlineSafety #CyberThreats#DataSecurity#StaySafeOnline
07:01 AM - Jun 16, 2025 (UTC)
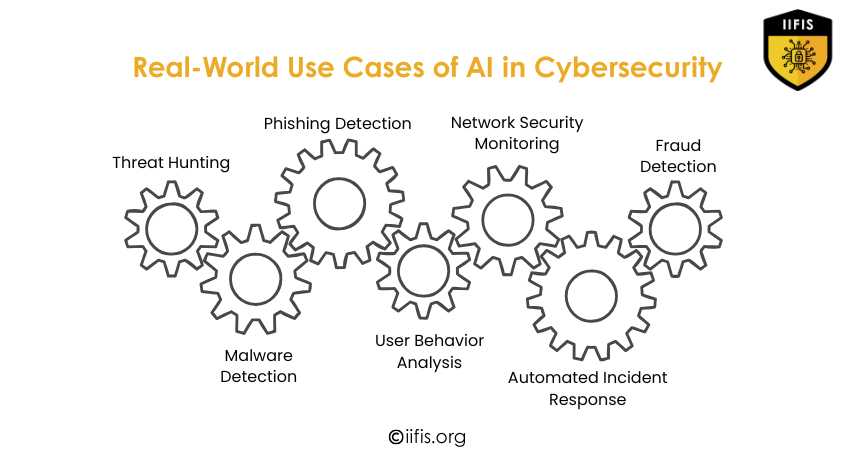
Real-World Use Cases of AI in Cybersecurity | IIFIS
Through real-time monitoring and smart decision-making, artificial intelligence (AI) in cybersecurity is essential for threat hunting, phishing detection, malware detection, user behavior analysis, and automated incident response. It also helps secure networks and stop fraud.
https://iifis.org/blog/wha...
Through real-time monitoring and smart decision-making, artificial intelligence (AI) in cybersecurity is essential for threat hunting, phishing detection, malware detection, user behavior analysis, and automated incident response. It also helps secure networks and stop fraud.
https://iifis.org/blog/wha...
12:16 PM - Jun 26, 2025 (UTC)
Fortigate Dubai | Firewall-dubai.com
Secure your organization with high-performance Fortigate Dubai firewalls available at Firewall-dubai.com. Designed to prevent malware, intrusions, and data breaches, FortiGate solutions offer advanced security with simplified management. We help businesses in Dubai implement Fortinet technology with ease and reliability.
https://firewall-dubai.com...
Secure your organization with high-performance Fortigate Dubai firewalls available at Firewall-dubai.com. Designed to prevent malware, intrusions, and data breaches, FortiGate solutions offer advanced security with simplified management. We help businesses in Dubai implement Fortinet technology with ease and reliability.
https://firewall-dubai.com...
08:04 AM - Jun 04, 2025 (UTC)
Protect Your Business with Expert Network Security Services
Is your business safe from cyber threats? At DigitDefence, we offer professional Network Security Services to keep your data, systems, and operations protected 24/7.
Firewall Configuration
Intrusion Detection & Prevention
Secure Network Architecture
Regular Vulnerability Scanning
24/7 Monitoring & Support
We help startups, SMEs, and enterprises secure their digital infrastructure from hacking, malware, phishing, and data breaches.
Contact us today
https://www.digitdefence.c...
Is your business safe from cyber threats? At DigitDefence, we offer professional Network Security Services to keep your data, systems, and operations protected 24/7.
Firewall Configuration
Intrusion Detection & Prevention
Secure Network Architecture
Regular Vulnerability Scanning
24/7 Monitoring & Support
We help startups, SMEs, and enterprises secure their digital infrastructure from hacking, malware, phishing, and data breaches.
Contact us today
https://www.digitdefence.c...
09:01 AM - Jun 05, 2025 (UTC)
Microsoft 365 Business Basic, priced at around ₹420 per user monthly or ₹5,040 yearly in India, offers web-based Office apps, 1TB OneDrive storage, and Microsoft Teams for seamless collaboration. Trusted resellers like Radiant Info Solutions and Shrevya Technologies provide competitive pricing, with discounts for bulk purchases, ideal for businesses in Hyderabad and Chennai. They offer 24/7 support, migration services, and compliance guidance, ensuring genuine licenses and cost-efficiency. The plan includes Exchange Online for 50GB mailboxes and advanced security features like anti-malware protection, perfect for small businesses. Resellers simplify renewals with automated reminders, preventing service disruptions. Contact a Microsoft supplier like Shrevya for personalized pricing to boost your business’s productivity with Microsoft 365 Business Basic.
https://radiant.in/microso...
https://radiant.in/microso...
04:52 AM - Jun 10, 2025 (UTC)
Why Virus Ransomware is Dangerous | Digitdefence
Ransomware encrypts your data and demands payment for its release, causing severe business disruptions and financial loss. It can compromise sensitive information and damage your reputation irreparably.
#Ransomware #CyberSecurity #DataProtection #VirusThreat #BusinessSecurity #Malware #CyberAttack
Ransomware encrypts your data and demands payment for its release, causing severe business disruptions and financial loss. It can compromise sensitive information and damage your reputation irreparably.
#Ransomware #CyberSecurity #DataProtection #VirusThreat #BusinessSecurity #Malware #CyberAttack
07:08 AM - Jun 21, 2025 (UTC)
2025 Cybersecurity Breach: A Silent Disaster Exposed 16 Billion Passwords
A Global Breach Like Never Before
What does anyone have to do? In one of the most startling digital events in internet history, Cybersecurity Breach 2025 has made over 16 billion login credentials available across the interwebs.
What’s most frightening about this brazen security breach is that it was not caused by one big corporation getting hacked, but by the increasing frequency of infostealer malware infecting individuals thousands of miles apart.
How the Breach Happened: A Look Inside
The far-reaching problem occurs when infovaluer use infostealer malware to hack millions of personal devices across the world.
Here's how it works:
Few individuals actually know they’ve been compromised.
These malware programs, being silent attacks, are first downloaded unknowingly.
They allow the perpetrator to breach the device and quietly collect usernames, passwords, and other sensitive data.
The stolen data is then uploaded to publicly exposed databases on the dark web or cloud-based repositories like GitHub.
These databases:
Require no password
Offer no encryption
Demand no hacking skills to access
Voila—billions of compromised records are available to anyone with minimal effort.
Major Brands and Government Systems Affected
The damages have impacted some of the most trusted names in tech, including:
Google
Facebook
Apple
GitHub
Telegram
VPN providers
G
A Global Breach Like Never Before
What does anyone have to do? In one of the most startling digital events in internet history, Cybersecurity Breach 2025 has made over 16 billion login credentials available across the interwebs.
What’s most frightening about this brazen security breach is that it was not caused by one big corporation getting hacked, but by the increasing frequency of infostealer malware infecting individuals thousands of miles apart.
How the Breach Happened: A Look Inside
The far-reaching problem occurs when infovaluer use infostealer malware to hack millions of personal devices across the world.
Here's how it works:
Few individuals actually know they’ve been compromised.
These malware programs, being silent attacks, are first downloaded unknowingly.
They allow the perpetrator to breach the device and quietly collect usernames, passwords, and other sensitive data.
The stolen data is then uploaded to publicly exposed databases on the dark web or cloud-based repositories like GitHub.
These databases:
Require no password
Offer no encryption
Demand no hacking skills to access
Voila—billions of compromised records are available to anyone with minimal effort.
Major Brands and Government Systems Affected
The damages have impacted some of the most trusted names in tech, including:
Apple
GitHub
Telegram
VPN providers
G

16 Billion Passwords Leaked in Biggest Data Breach Ever
Biggest Cybersecurity Data Breach: 16 billion passwords leaked in one mega dump. See how to respond quickly.
https://oragetechnologies.com/data-breach/
07:01 AM - Jun 25, 2025 (UTC)
The Importance of Securing Endpoint Devices | Digitdefence
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
09:51 AM - Jun 10, 2025 (UTC)
They look at digital evidence in real time while investigations are still going on. ogitforensics.com is a professional live forensics service in Malaysia. Our professional staff makes sure the system keeps going even when bad information is recorded. You need this to go to court and handle things that happen. We help you find and keep important data, like when your business is hacked or your personal information is stolen. Some of the other things we do really well are forensics on phones, photos, malware, and security tips. Many people trust us as digital forensic experts, and we work with police, lawyers, and private businesses to find digital evidence that can be used in court. OGIT Forensics is the company to call in Malaysia if you need accurate, quick, and private forensic services.Cyber Threat Intelligence Services Malaysia, Brand Protection, vacuum mixer malaysia, Malware Forensic in Malaysia, Phone forensic in Malaysia
Read More:-https://www.ogitforensics....
Read More:-https://www.ogitforensics....
08:16 AM - Jun 12, 2025 (UTC)