DigitDefence Cybersecurity Services
Strengthen Your Business with Top-Notch Cybersecurity Services!
In today’s digital age, protecting your business from cyber threats is more important than ever. Our expert cybersecurity services offer comprehensive protection against data breaches, malware, and ransomware.
Whether you're a small startup or a growing enterprise, we tailor solutions to fit your unique needs, ensuring your data and systems are always secure.
Stay ahead of threats and safeguard your business with cutting-edge cybersecurity solutions. Let us be your trusted partner in protecting your digital assets.
https://digitdefence.com/
Strengthen Your Business with Top-Notch Cybersecurity Services!
In today’s digital age, protecting your business from cyber threats is more important than ever. Our expert cybersecurity services offer comprehensive protection against data breaches, malware, and ransomware.
Whether you're a small startup or a growing enterprise, we tailor solutions to fit your unique needs, ensuring your data and systems are always secure.
Stay ahead of threats and safeguard your business with cutting-edge cybersecurity solutions. Let us be your trusted partner in protecting your digital assets.
https://digitdefence.com/
12:54 PM - Mar 11, 2025 (UTC)
2025 Cybersecurity Predictions
https://treacletech.com/20...
Explore 2025 cybersecurity trends & how deception technology helps combat AI-driven attacks, ransomware, IoT threats, and supply chain risks.
https://treacletech.com/20...
Explore 2025 cybersecurity trends & how deception technology helps combat AI-driven attacks, ransomware, IoT threats, and supply chain risks.
06:36 AM - Apr 01, 2025 (UTC)
In 2025, the pharmaceutical industry faces growing challenges: counterfeit drugs, IP theft, and digital risk in pharmaceuticals like ransomware and rogue pharmacies. Our new article dives into these pharmaceutical industry risks and shares actionable strategies to safeguard your brand. From securing supply chains to tackling online fraud, learn how to stay ahead. Bonus:
Discover how solutions like BrandShield are helping pharma companies fight digital threats.
Read more: https://www.myvipon.com/po...
#PharmaceuticalIndustry #BrandProtection #CyberSecurity #OnlineBrandProtection
Discover how solutions like BrandShield are helping pharma companies fight digital threats.
Read more: https://www.myvipon.com/po...
#PharmaceuticalIndustry #BrandProtection #CyberSecurity #OnlineBrandProtection
06:44 AM - Mar 17, 2025 (UTC)
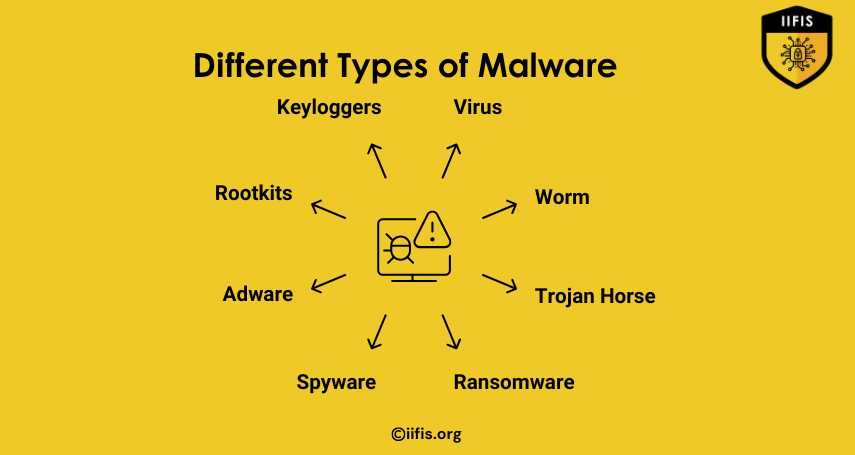
Different Types of Malware | IIFIS
This image shows common harmful programs that can affect computers. These include viruses, worms, and spyware. Others like ransomware and trojan horses can steal or lock data. Each type causes problems and needs protection to keep devices safe.
https://iifis.org/blog/wha...
This image shows common harmful programs that can affect computers. These include viruses, worms, and spyware. Others like ransomware and trojan horses can steal or lock data. Each type causes problems and needs protection to keep devices safe.
https://iifis.org/blog/wha...
11:49 AM - Apr 30, 2025 (UTC)
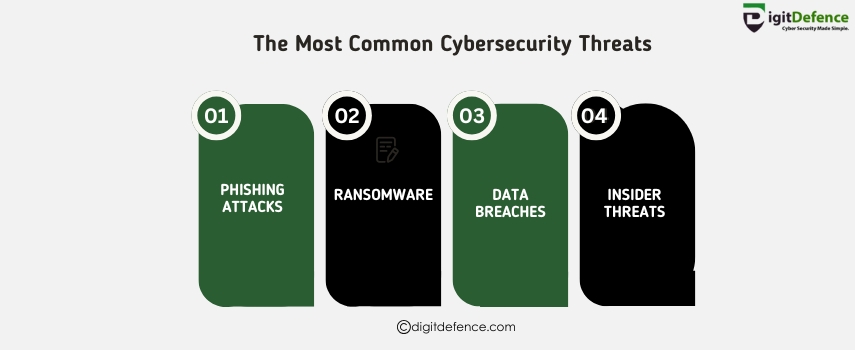
The Most Common Cybersecurity Threats| Digitdefence
Cybersecurity threats like ransomware, phishing, and data breaches can disrupt business operations and compromise sensitive data. Stay vigilant and secure your systems.
https://digitdefence.com/b...
Cybersecurity threats like ransomware, phishing, and data breaches can disrupt business operations and compromise sensitive data. Stay vigilant and secure your systems.
https://digitdefence.com/b...
09:44 AM - Apr 11, 2025 (UTC)
Protect your business devices with Wizard IT's Endpoint Protection Service in Auckland. Our expert team offers robust solutions designed to secure all endpoints, including computers, mobile devices, and servers, against malware, ransomware, and other cyber threats. We implement advanced security measures tailored to your business needs, providing continuous monitoring and rapid incident response. With our comprehensive endpoint protection, you can ensure the safety of your sensitive data and maintain operational integrity. Trust Wizard IT for reliable and effective endpoint security. Contact us today to learn more!
https://wizard-it.co.nz/se...
https://wizard-it.co.nz/se...
06:43 AM - May 05, 2025 (UTC)
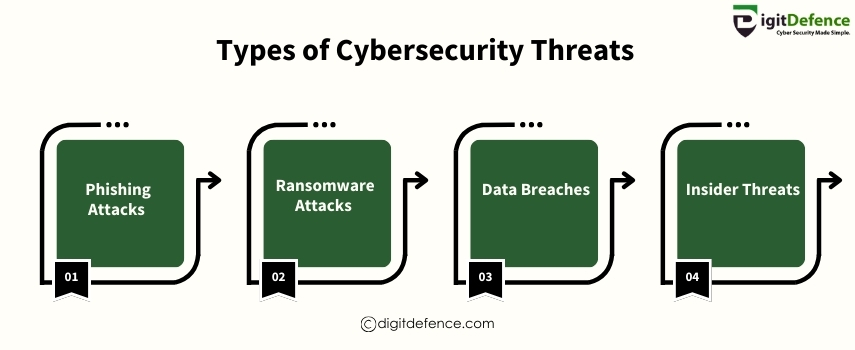
Types of Cyber Security Threats | Digitdefence
Cybersecurity threats come in various forms, including malware, phishing, and ransomware. Understanding these risks is crucial for protecting your business.
Cybersecurity threats come in various forms, including malware, phishing, and ransomware. Understanding these risks is crucial for protecting your business.
09:38 AM - Apr 23, 2025 (UTC)
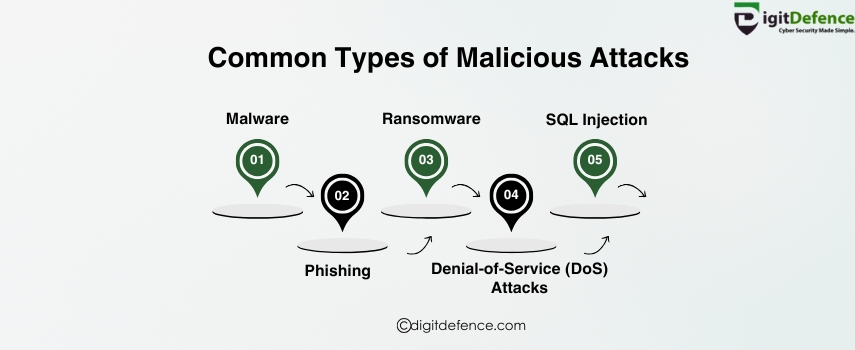
Common Types of Malicious Attacks | Digitdefence
Malicious attacks like malware, phishing, and ransomware threaten business security by exploiting vulnerabilities. Protect your data and systems with strong security measures.
https://digitdefence.com/
Malicious attacks like malware, phishing, and ransomware threaten business security by exploiting vulnerabilities. Protect your data and systems with strong security measures.
https://digitdefence.com/
10:33 AM - Apr 03, 2025 (UTC)
Why Virus Ransomware Is Dangerous | Digitdefence
Virus ransomware is dangerous because it encrypts your files and demands payment for access, often causing data loss, financial damage, and business disruption. It targets both individuals and organizations with increasing sophistication.
https://digitdefence.com/
Virus ransomware is dangerous because it encrypts your files and demands payment for access, often causing data loss, financial damage, and business disruption. It targets both individuals and organizations with increasing sophistication.
https://digitdefence.com/
10:08 AM - Mar 26, 2025 (UTC)
Cybersecurity Company in Bangalore
Protect Your Business with Expert Cybersecurity Services in Bangalore
Worried about data breaches, ransomware, or phishing attacks? At DigitDefence, we provide advanced cybersecurity solutions tailored for businesses of all sizes. From vulnerability assessments to 24/7 monitoring, we help secure your digital assets so you can focus on growth.
Our services include:
Network Security
Endpoint Protection
Risk Assessment
Compliance Support
Based in Bangalore | Serving PAN India
Protect Your Business with Expert Cybersecurity Services in Bangalore
Worried about data breaches, ransomware, or phishing attacks? At DigitDefence, we provide advanced cybersecurity solutions tailored for businesses of all sizes. From vulnerability assessments to 24/7 monitoring, we help secure your digital assets so you can focus on growth.
Our services include:
Network Security
Endpoint Protection
Risk Assessment
Compliance Support
Based in Bangalore | Serving PAN India
08:52 AM - Apr 30, 2025 (UTC)
Sponsored by
OWT
3 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
Endpoint Detection and Response (EDR) Market to Grow on AI-Driven Insights
Endpoint Detection and Response (EDR) Market to Grow on AI-Driven Insights
Endpoint Detection and Response (EDR) solutions are advanced cybersecurity tools designed to monitor, detect, and mitigate threats at the endpoint level—laptops, desktops, servers, and mobile devices. By leveraging behavioral analysis, machine learning, and artificial intelligence, EDR platforms provide real-time threat detection, automated incident response, and forensic investigation capabilities.
These products address the growing need for proactive threat hunting and rapid breach containment, particularly as organizations face increasingly sophisticated malware, ransomware, and zero-day exploits.
The integration of cloud-based analytics and threat intelligence feeds enhances visibility across the entire attack surface, enabling IT teams to prioritize alerts and remediate vulnerabilities efficiently. Advantages such as improved incident response times, reduced dwell time for intruders, and consolidated security management contribute to stronger overall network hygiene.
Endpoint Detection and Response (EDR) Market
https://www.coherentmarket...
Get More Insights On Endpoint Detection and Response (EDR) Market
https://justpaste.it/jdvw6
Endpoint Detection and Response (EDR) Market to Grow on AI-Driven Insights
Endpoint Detection and Response (EDR) solutions are advanced cybersecurity tools designed to monitor, detect, and mitigate threats at the endpoint level—laptops, desktops, servers, and mobile devices. By leveraging behavioral analysis, machine learning, and artificial intelligence, EDR platforms provide real-time threat detection, automated incident response, and forensic investigation capabilities.
These products address the growing need for proactive threat hunting and rapid breach containment, particularly as organizations face increasingly sophisticated malware, ransomware, and zero-day exploits.
The integration of cloud-based analytics and threat intelligence feeds enhances visibility across the entire attack surface, enabling IT teams to prioritize alerts and remediate vulnerabilities efficiently. Advantages such as improved incident response times, reduced dwell time for intruders, and consolidated security management contribute to stronger overall network hygiene.
Endpoint Detection and Response (EDR) Market
https://www.coherentmarket...
Get More Insights On Endpoint Detection and Response (EDR) Market
https://justpaste.it/jdvw6
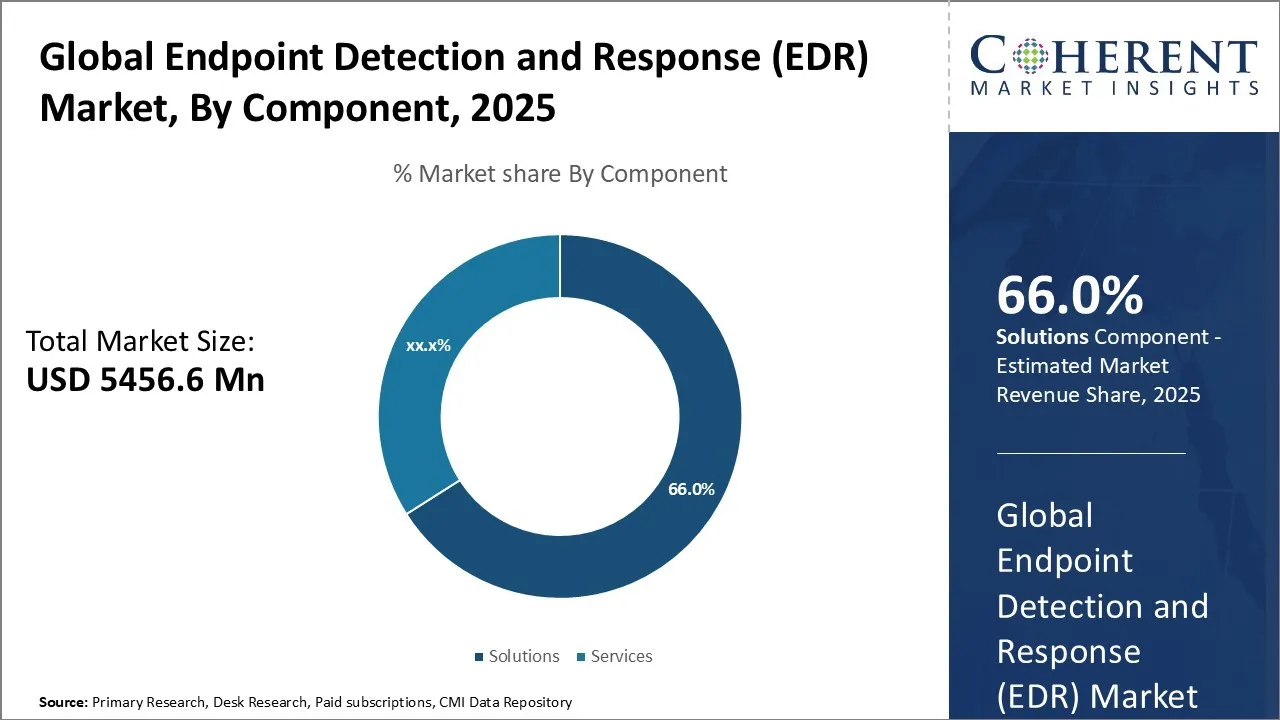
Endpoint Detection and Response (EDR) Market Forecast, 2032
Endpoint Detection and Response Market is estimated to reach USD 5,456.6 Mn in 2025 and is anticipated to grow USD 27,695.5 Mn by 2032 with CAGR of 26.12%.
https://www.coherentmarketinsights.com/market-insight/endpoint-detection-and-response-edr-market-5564
10:36 AM - May 12, 2025 (UTC)
(E)
🛡️ Cybersecurity in 2025: Are You Truly Protected? 🛡️
With cyber threats evolving every second, one question becomes more urgent than ever:
👉 Is your digital life really secure?
From phishing scams to ransomware attacks, cybersecurity is no longer optional — it’s essential. Here's what you must stay on top of:
✅ Use strong, unique passwords
✅ Enable 2FA (Two-Factor Authentication)
✅ Keep software and apps updated
✅ Avoid clicking on suspicious links
✅ Educate yourself about common scams
Whether you're a business owner or a casual user, digital awareness is your first line of defense. 🔐
💬 Want expert help to secure your systems and data?
Explore our https://invortech.com/cybe...
#CyberSecurity2025 #staysafeonline #DigitalProtection #invortech #OnlineSecurity #CyberAware #TechTips
With cyber threats evolving every second, one question becomes more urgent than ever:
👉 Is your digital life really secure?
From phishing scams to ransomware attacks, cybersecurity is no longer optional — it’s essential. Here's what you must stay on top of:
✅ Use strong, unique passwords
✅ Enable 2FA (Two-Factor Authentication)
✅ Keep software and apps updated
✅ Avoid clicking on suspicious links
✅ Educate yourself about common scams
Whether you're a business owner or a casual user, digital awareness is your first line of defense. 🔐
💬 Want expert help to secure your systems and data?
Explore our https://invortech.com/cybe...
#CyberSecurity2025 #staysafeonline #DigitalProtection #invortech #OnlineSecurity #CyberAware #TechTips
04:34 PM - Apr 19, 2025 (UTC)
(E)
Top Cybersecurity Threats Facing India in 2025 and How to Protect Against Them
https://seqrite.hashnode.d...
The India Cyber Threat Report 2025 highlights rising ransomware, AI-based phishing, and infrastructure attacks. Read this blog to explore key threats and learn practical steps to strengthen your cyber defenses. Stay ahead, stay secure.
#IndiaCyberThreatReport #CybersecurityIndia #CyberSecurity
https://seqrite.hashnode.d...
The India Cyber Threat Report 2025 highlights rising ransomware, AI-based phishing, and infrastructure attacks. Read this blog to explore key threats and learn practical steps to strengthen your cyber defenses. Stay ahead, stay secure.
#IndiaCyberThreatReport #CybersecurityIndia #CyberSecurity
01:44 PM - Apr 29, 2025 (UTC)
Adapting to Evolving Cyber Threats: Best Practices for Organizations
Cyber threats have transformed significantly over the years, evolving from simple viruses to complex, targeted attacks. Modern threats include advanced persistent threats (APTs), ransomware, phishing schemes, and zero-day exploits. Read full blog on medium:-
Cyber threats have transformed significantly over the years, evolving from simple viruses to complex, targeted attacks. Modern threats include advanced persistent threats (APTs), ransomware, phishing schemes, and zero-day exploits. Read full blog on medium:-

Adapting to Evolving Cyber Threats: Best Practices for Organizations | by GoTrust Tech | Mar, 2025 | Medium
In today’s rapidly evolving digital landscape, organizations face an unprecedented array of cyber threats that continually adapt and become more sophisticated. To safeguard sensitive information and…
https://medium.com/@gotrust_tech/adapting-to-evolving-cyber-threats-best-practices-for-organizations-e76f890d8ca3
09:51 AM - Mar 13, 2025 (UTC)
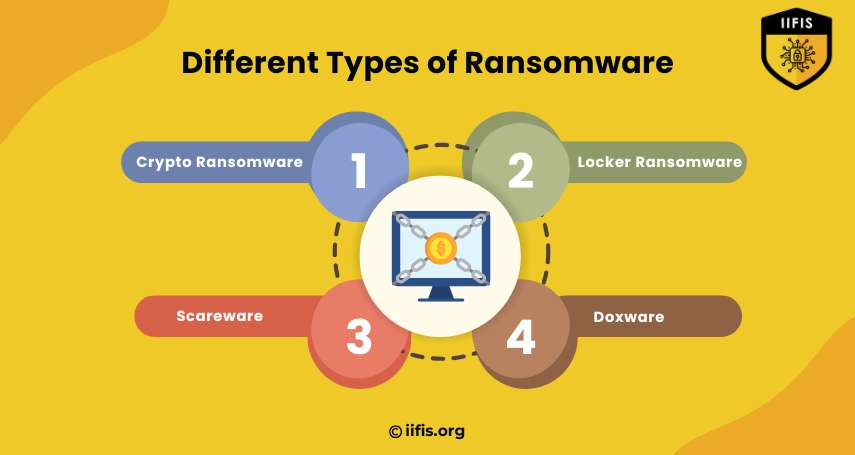
Different Types of Ransomware | IIFIS
This image shows four types of ransomware: crypto ransomware, locker ransomware, scareware, and doxware. Each type locks or threatens the user’s files or data and demands payment. It highlights how different ransomware attacks work to cause harm.
https://iifis.org/blog/wha...
This image shows four types of ransomware: crypto ransomware, locker ransomware, scareware, and doxware. Each type locks or threatens the user’s files or data and demands payment. It highlights how different ransomware attacks work to cause harm.
https://iifis.org/blog/wha...
12:12 PM - Apr 25, 2025 (UTC)