How to Choose the Right Hidden Wiki URL
Choosing the right Hidden Wiki URL is essential for safe and secure dark web browsing. This guide helps you identify legitimate directories, avoid phishing traps, and ensure private access through verified onion links. Learn how to spot trustworthy sources and protect your digital identity while exploring the deep web.
https://www.apsense.com/ar...
Choosing the right Hidden Wiki URL is essential for safe and secure dark web browsing. This guide helps you identify legitimate directories, avoid phishing traps, and ensure private access through verified onion links. Learn how to spot trustworthy sources and protect your digital identity while exploring the deep web.
https://www.apsense.com/ar...
12:05 PM - Jul 19, 2025 (UTC)
Cyber Safety Lessons Every School Should Teach
Every school should teach cyber safety lessons covering secure passwords, recognizing phishing scams, protecting personal information, and responsible social media use. Students must understand the risks of cyberbullying, data theft, and online predators. Teaching digital citizenship helps them navigate the internet safely, respect others online, and develop smart habits for a secure digital future.
For more info visit... https://www.edu123.in/cate...
Every school should teach cyber safety lessons covering secure passwords, recognizing phishing scams, protecting personal information, and responsible social media use. Students must understand the risks of cyberbullying, data theft, and online predators. Teaching digital citizenship helps them navigate the internet safely, respect others online, and develop smart habits for a secure digital future.
For more info visit... https://www.edu123.in/cate...
05:24 AM - Jul 30, 2025 (UTC)
How to Choose the Hidden Wiki Safely and Effectively
Navigating the dark web requires caution—especially when selecting a Hidden Wiki link. This guide walks you through safe and effective ways to access the Hidden Wiki without compromising your privacy. Learn how to verify trustworthy links, use Tor securely, and avoid phishing or scam directories. Whether you're a curious explorer or a privacy-focused researcher, this article ensures you take the right precautions.
https://diigo.com/0109q6d
Navigating the dark web requires caution—especially when selecting a Hidden Wiki link. This guide walks you through safe and effective ways to access the Hidden Wiki without compromising your privacy. Learn how to verify trustworthy links, use Tor securely, and avoid phishing or scam directories. Whether you're a curious explorer or a privacy-focused researcher, this article ensures you take the right precautions.
https://diigo.com/0109q6d
12:36 PM - Jul 19, 2025 (UTC)
Common Cyber Threats You Should Know | IIFIS
This image explains common cyber threats like phishing, malware, ransomware, and man-in-the-middle (MitM) attacks. It highlights how cybercriminals steal data, encrypt files for ransom, or eavesdrop on communications through fake emails, malicious software, or unsecured networks.
https://iifis.org/blog/cyb...
This image explains common cyber threats like phishing, malware, ransomware, and man-in-the-middle (MitM) attacks. It highlights how cybercriminals steal data, encrypt files for ransom, or eavesdrop on communications through fake emails, malicious software, or unsecured networks.
https://iifis.org/blog/cyb...
12:37 PM - Jul 30, 2025 (UTC)
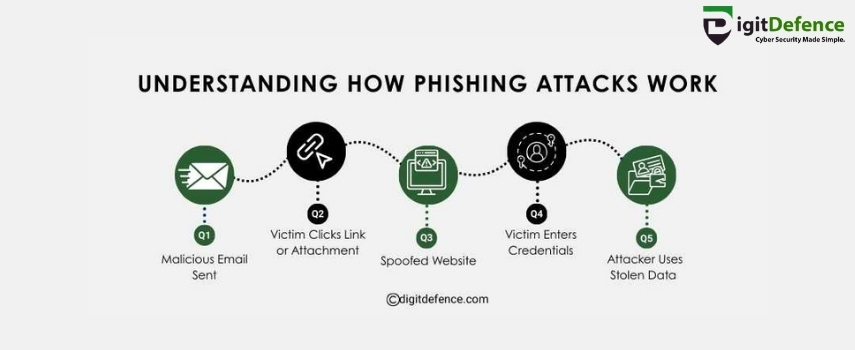
Understanding How Phishing Attacks work
Phishing attacks trick users through fake emails and websites to steal sensitive data.
Learn how cyber threats work and protect your online security.
Visit www.digitdefence.com to stay safe.
Phishing attacks trick users through fake emails and websites to steal sensitive data.
Learn how cyber threats work and protect your online security.
Visit www.digitdefence.com to stay safe.
11:10 AM - Jul 11, 2025 (UTC)
Overview: “AI in Cybersecurity: Double‑Edged Sword”
The Good: AI as a Cybersecurity Game-Changer
AI has dramatically transformed how we defend digital infrastructures. Its ability to analyze vast datasets, detect anomalies, and respond to threats in real-time is unparalleled. With machine learning algorithms, AI tools can predict and neutralize threats before they manifest.
AI-driven cybersecurity empower organizations to:
Detect zero-day vulnerabilities
Automate threat response
Identify insider threats
Optimize security workflows
The Bad: AI as a Weapon for Cybercriminals
Unfortunately, the same technologies that protect us can be weaponized. Hackers now deploy AI to craft more sophisticated phishing attacks, generate malicious deepfakes, and bypass traditional security measures with alarming precision.
The dark side of AI includes:
AI-Powered Malware: Capable of morphing signatures to evade detection.
Smart Phishing: AI tools can personalize and scale phishing campaigns using scraped data.
Deepfake Technology: Creates convincing audio/video fabrications that deceive users and systems.
Organizations must embrace AI-enhanced cybersecurity solutions while remaining vigilant against AI-driven threats. The key is not just adoption but ethical implementation, robust regulation, and continuous education.
For more information, visit us: https://www.datspy.com/
The Good: AI as a Cybersecurity Game-Changer
AI has dramatically transformed how we defend digital infrastructures. Its ability to analyze vast datasets, detect anomalies, and respond to threats in real-time is unparalleled. With machine learning algorithms, AI tools can predict and neutralize threats before they manifest.
AI-driven cybersecurity empower organizations to:
Detect zero-day vulnerabilities
Automate threat response
Identify insider threats
Optimize security workflows
The Bad: AI as a Weapon for Cybercriminals
Unfortunately, the same technologies that protect us can be weaponized. Hackers now deploy AI to craft more sophisticated phishing attacks, generate malicious deepfakes, and bypass traditional security measures with alarming precision.
The dark side of AI includes:
AI-Powered Malware: Capable of morphing signatures to evade detection.
Smart Phishing: AI tools can personalize and scale phishing campaigns using scraped data.
Deepfake Technology: Creates convincing audio/video fabrications that deceive users and systems.
Organizations must embrace AI-enhanced cybersecurity solutions while remaining vigilant against AI-driven threats. The key is not just adoption but ethical implementation, robust regulation, and continuous education.
For more information, visit us: https://www.datspy.com/
09:47 AM - Jun 30, 2025 (UTC)
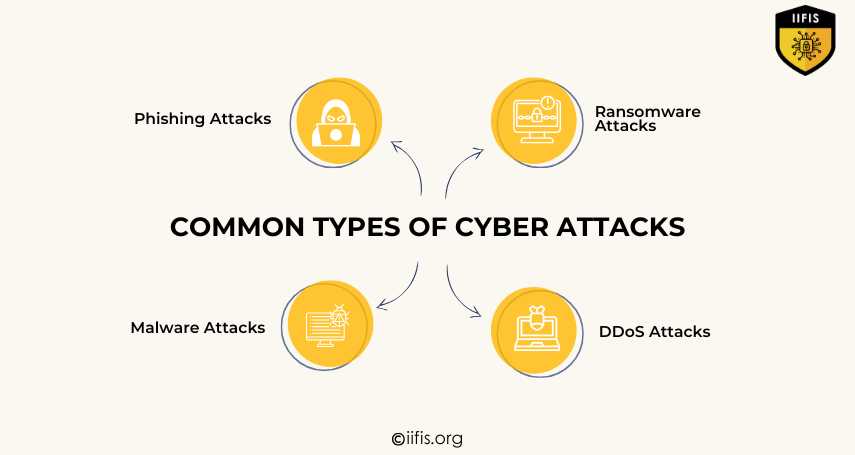
Common Types of Cyber Attacks | IIFIS
This image highlights common types of cyberattacks: phishing, ransomware, malware, and DDoS attacks. These threats target systems to steal data, lock access, spread viruses, or overwhelm networks, posing serious security risks to individuals and organizations.
https://iifis.org/blog/how...
This image highlights common types of cyberattacks: phishing, ransomware, malware, and DDoS attacks. These threats target systems to steal data, lock access, spread viruses, or overwhelm networks, posing serious security risks to individuals and organizations.
https://iifis.org/blog/how...
12:49 PM - Jul 28, 2025 (UTC)
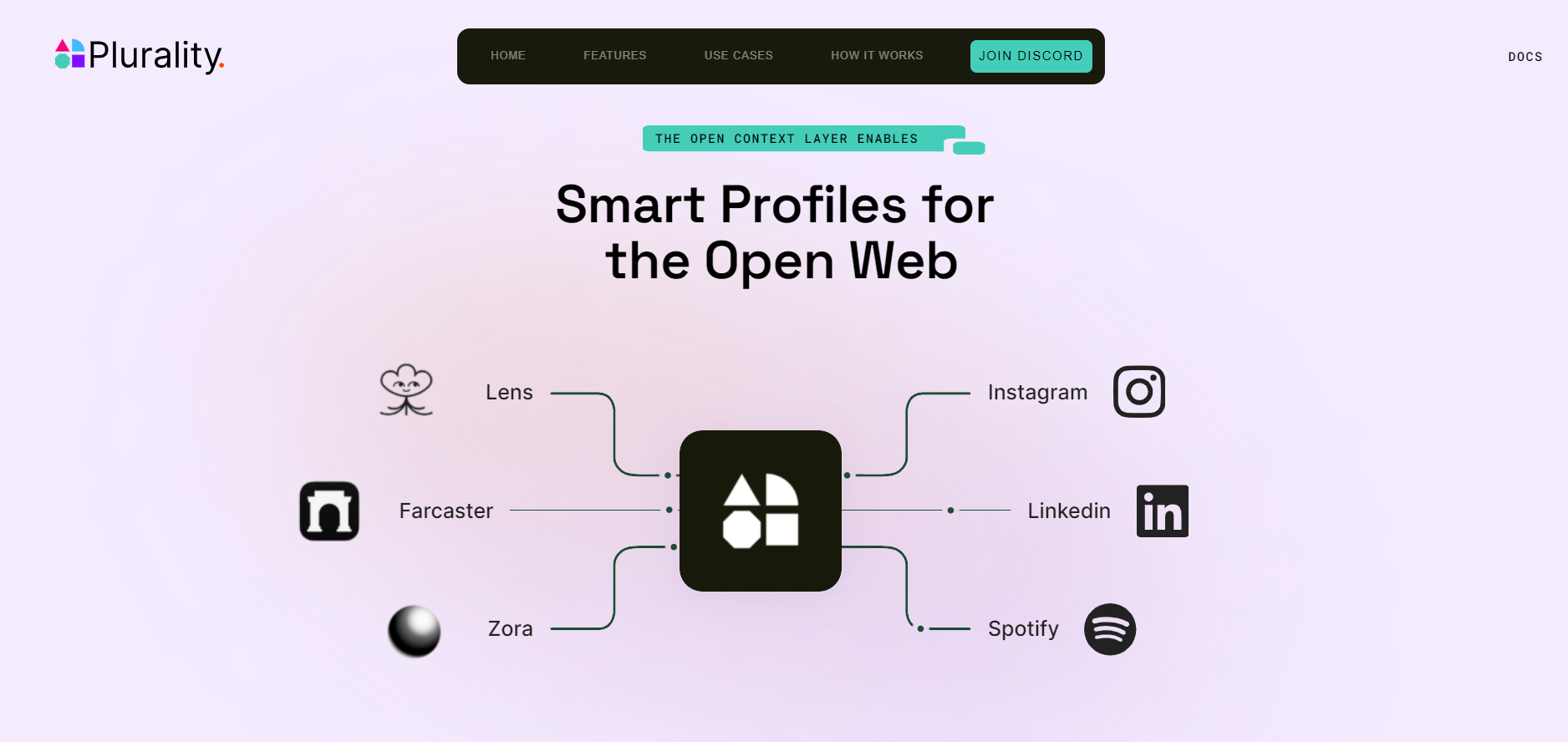
How secure is the Web3 wallet by Plurality Network?
Security is at the core of the Plurality Network Web3 wallet, employing robust features like end-to-end encryption, hardware wallet compatibility, and biometric verification to ensure data integrity and user privacy. It uses the latest cryptographic technologies including multi-signature authentication and phishing protection to keep wallets safe from threats.
https://plurality.network/
With added protections like transaction previews and anti-malware integrations, the Web3 wallet ensures a secure environment for interacting with decentralized applications, NFTs, and DeFi protocols making it one of the safest wallets for storing and transacting in digital assets.
Security is at the core of the Plurality Network Web3 wallet, employing robust features like end-to-end encryption, hardware wallet compatibility, and biometric verification to ensure data integrity and user privacy. It uses the latest cryptographic technologies including multi-signature authentication and phishing protection to keep wallets safe from threats.
https://plurality.network/
With added protections like transaction previews and anti-malware integrations, the Web3 wallet ensures a secure environment for interacting with decentralized applications, NFTs, and DeFi protocols making it one of the safest wallets for storing and transacting in digital assets.
06:02 AM - Jul 24, 2025 (UTC)
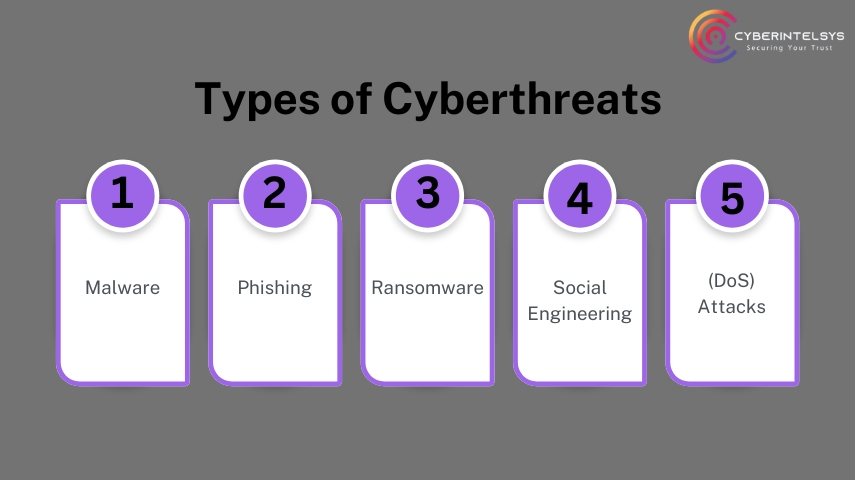
Types of Cyberthreats
Top 5 Cyberthreats Every Business Should Know
Stay alert and protect your systems from malware, phishing, and more!
To learn more,
https://cyberintelsys.com/...
Top 5 Cyberthreats Every Business Should Know
Stay alert and protect your systems from malware, phishing, and more!
To learn more,
https://cyberintelsys.com/...
02:31 PM - Jul 16, 2025 (UTC)
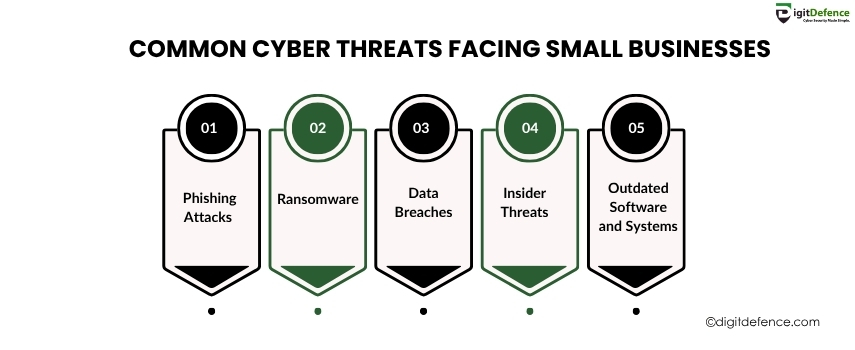
Common Cyber Threats Facing Small Businesses | Digitdefence
Small businesses are frequent targets of cyber threats like phishing, ransomware, and data breaches due to limited security measures and awareness. Understanding these risks is the first step toward protection.
#CyberThreats #SmallBusinessSecurity #PhishingScams #Ransomware #networksecurity #CyberProtection #DataBreach #CyberAwareness #BusinessSafety #CyberRiskManagement
Small businesses are frequent targets of cyber threats like phishing, ransomware, and data breaches due to limited security measures and awareness. Understanding these risks is the first step toward protection.
#CyberThreats #SmallBusinessSecurity #PhishingScams #Ransomware #networksecurity #CyberProtection #DataBreach #CyberAwareness #BusinessSafety #CyberRiskManagement
09:16 AM - Jul 09, 2025 (UTC)
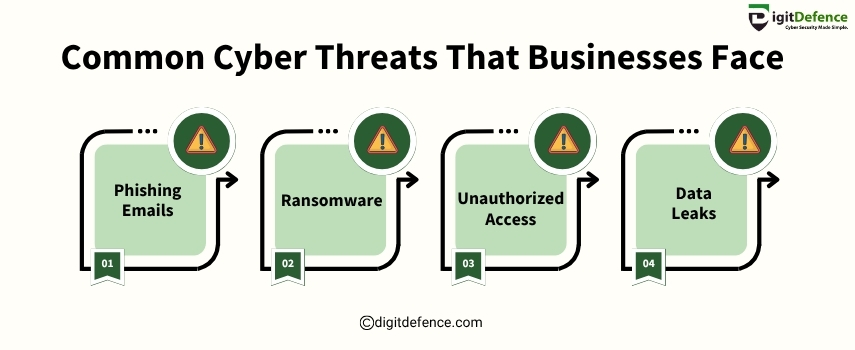
Common Cyber Threats That Businesses Face
Cyber attacks are rising fast, every business is a target. From phishing emails to data leaks, learn how to stay safe from the most common threats.
Visit https://digitdefence.com/ to protect your business now.
Cyber attacks are rising fast, every business is a target. From phishing emails to data leaks, learn how to stay safe from the most common threats.
Visit https://digitdefence.com/ to protect your business now.
09:22 AM - Jul 21, 2025 (UTC)
Add an MSP or DPO to Maximise Impact
Managing Intune on your own can be daunting. That’s why many SMEs work with a Managed Service Provider (MSP) or designate a Data Protection Officer (DPO). These roles ensure your policies are up-to-date, GDPR-compliant, and aligned with your business goals.
A proactive MSP can also integrate Intune with other systems, run security audits, and provide full SOC support for ongoing monitoring.
Pilot IQ: Intune Setup & Device Management for SMEs
At Pilot IQ, we help SMEs unlock the full potential of Microsoft Intune. Whether you’re setting it up for the first time or looking to optimise existing configurations, our team handles deployment, policy design, and ongoing management.
We combine cybersecurity consulting, cloud strategy, and real-time IT support to make your tech stack secure, scalable, and smart.
Conclusion: Intune Is the Future of Device Management
Your employees are mobile. Your data is in the cloud. Your security should be just as flexible.
Microsoft Intune isn’t just an IT tool—it’s your frontline defense in an era of ransomware, phishing, and compliance risk. With the right partner, it becomes the backbone of your IT infrastructure.
Visit www.pilotiq.co.uk to learn more or book an Intune consultation today.
Managing Intune on your own can be daunting. That’s why many SMEs work with a Managed Service Provider (MSP) or designate a Data Protection Officer (DPO). These roles ensure your policies are up-to-date, GDPR-compliant, and aligned with your business goals.
A proactive MSP can also integrate Intune with other systems, run security audits, and provide full SOC support for ongoing monitoring.
Pilot IQ: Intune Setup & Device Management for SMEs
At Pilot IQ, we help SMEs unlock the full potential of Microsoft Intune. Whether you’re setting it up for the first time or looking to optimise existing configurations, our team handles deployment, policy design, and ongoing management.
We combine cybersecurity consulting, cloud strategy, and real-time IT support to make your tech stack secure, scalable, and smart.
Conclusion: Intune Is the Future of Device Management
Your employees are mobile. Your data is in the cloud. Your security should be just as flexible.
Microsoft Intune isn’t just an IT tool—it’s your frontline defense in an era of ransomware, phishing, and compliance risk. With the right partner, it becomes the backbone of your IT infrastructure.
Visit www.pilotiq.co.uk to learn more or book an Intune consultation today.
10:07 AM - Jul 30, 2025 (UTC)
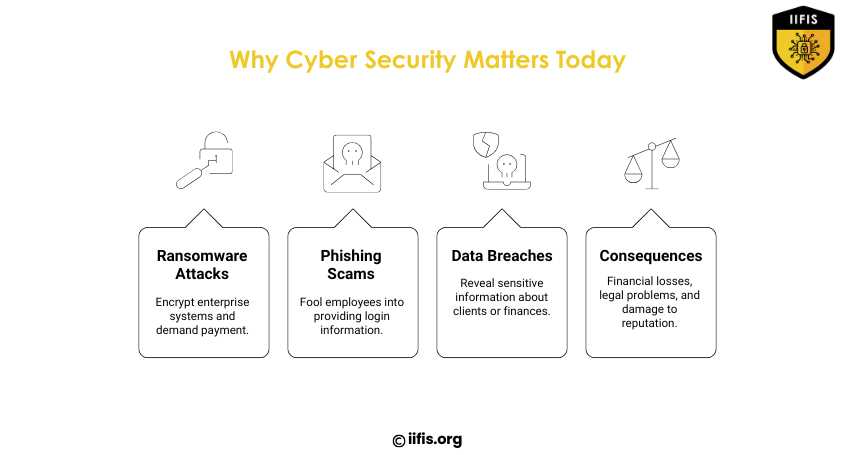
Why Cyber Security Matters Today | IIFIS
This image emphasizes the importance of cybersecurity by depicting common threats such as ransomware, phishing, and data breaches. It describes how these attacks can cause companies to suffer from monetary losses, legal problems, and reputational harm.
https://iifis.org/blog/how...
This image emphasizes the importance of cybersecurity by depicting common threats such as ransomware, phishing, and data breaches. It describes how these attacks can cause companies to suffer from monetary losses, legal problems, and reputational harm.
https://iifis.org/blog/how...
11:26 AM - Jul 26, 2025 (UTC)
Online Cricket ID – How to Stay Safe, Verified & Scam-Free
Online cricket ID Millions of members register every day with an online cricket ID to place bets on live matches, earn additional rewards, and get paid in real time. But as the popularity of the betting sites increases even further, there is also a greater chance of scams and fake online cricket ID.
Stay protected with your online Cricket ID.Learn how to verify safely, avoid scams, and use the online Cricket ID WhatsApp number for secure support.
How do you make your betting safe, secure, and scam-free?
We'll walk you through all you need to know in this guide, including how to properly validate your online Cricket ID, keep it safe, and how to avoid fraud through the online Cricket ID WhatsApp number.
Why Online Cricket ID Security Matters
An online cricket ID is not just a login—it's entry to your cash, betting history, and personal details. If it falls into the wrong hands or is created on an unverified page, you are vulnerable to:
Losing money
Your account being hacked
Being banned from reliable sites
Being targeted for phishing or scam
That's why it's especially critical to protect your online Cricket ID and authenticate it from authentic sources.
Warning Signs of a Legitimate Online Cricket ID Provider
Before registering with any ID, verify if the site meets the following requirements:
Licensed and Regulated Website
A genuine site always shows licensing details. Locate the certifications on the
Online cricket ID Millions of members register every day with an online cricket ID to place bets on live matches, earn additional rewards, and get paid in real time. But as the popularity of the betting sites increases even further, there is also a greater chance of scams and fake online cricket ID.
Stay protected with your online Cricket ID.Learn how to verify safely, avoid scams, and use the online Cricket ID WhatsApp number for secure support.
How do you make your betting safe, secure, and scam-free?
We'll walk you through all you need to know in this guide, including how to properly validate your online Cricket ID, keep it safe, and how to avoid fraud through the online Cricket ID WhatsApp number.
Why Online Cricket ID Security Matters
An online cricket ID is not just a login—it's entry to your cash, betting history, and personal details. If it falls into the wrong hands or is created on an unverified page, you are vulnerable to:
Losing money
Your account being hacked
Being banned from reliable sites
Being targeted for phishing or scam
That's why it's especially critical to protect your online Cricket ID and authenticate it from authentic sources.
Warning Signs of a Legitimate Online Cricket ID Provider
Before registering with any ID, verify if the site meets the following requirements:
Licensed and Regulated Website
A genuine site always shows licensing details. Locate the certifications on the
06:57 AM - Jul 12, 2025 (UTC)
Sponsored by
OWT
7 months ago
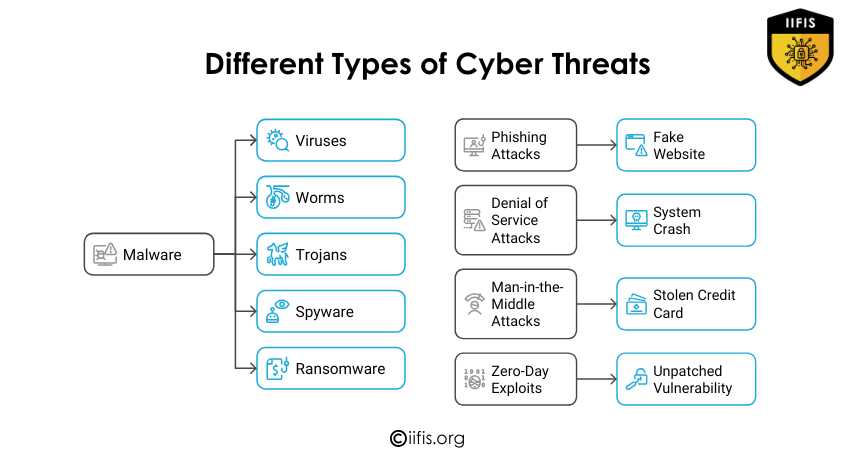
Different Types of Cyber Threats | IIFIS
Cyber threats come in many forms like viruses, phishing, and ransomware. They can crash systems, steal data, or expose weak points. Understanding these threats helps protect against fake websites, stolen credit cards, and unpatched security issues.
https://iifis.org/blog/wha...
Cyber threats come in many forms like viruses, phishing, and ransomware. They can crash systems, steal data, or expose weak points. Understanding these threats helps protect against fake websites, stolen credit cards, and unpatched security issues.
https://iifis.org/blog/wha...
12:34 PM - Jul 07, 2025 (UTC)