Key Steps in Conducting a Cybersecurity Risk Assessment
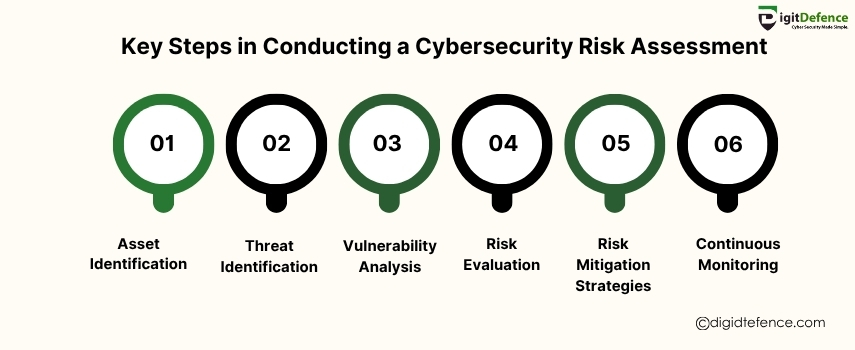
Conducting a cybersecurity risk assessment involves identifying potential threats and vulnerabilities to your business’s digital assets, then prioritizing risks to implement effective security measures. It’s crucial for protecting sensitive data and ensuring business continuity.
#CyberSecurity #RiskAssessment #DataProtection #BusinessSecurity
Conducting a cybersecurity risk assessment involves identifying potential threats and vulnerabilities to your business’s digital assets, then prioritizing risks to implement effective security measures. It’s crucial for protecting sensitive data and ensuring business continuity.
#CyberSecurity #RiskAssessment #DataProtection #BusinessSecurity
09:29 AM - Jun 03, 2025 (UTC)
Supply Chain Insurance Procurement Intelligence Report, 2023 - 2030 |
Download Sample Copy@ https://tinyurl.com/ywb9ad...
The supply chain insurance category is anticipated to grow at a CAGR of 4.5% from 2023 to 2030. There are several possible risks and interruptions for supply chain enterprises. Due to the intricate web of interactions between vendors, suppliers, and customers, a break in one link in the supply chain can result in bigger losses in several other links. For companies whose activities are directly dependent on a major supplier's manufacturing capacity, supply chain insurance coverage is crucial.
In 2021, according to Morningstar, the COVID-19 pandemic exposed the limitations of business interruption insurance. As a result of this, there has been an increased demand for supply chain insurance significantly. Insurance companies have expanded their offerings and coverage beyond their regular Business Interruption (BI) and Contingent Business Interruption (CBI) policies.
#SupplyChainInsurance #ProcurementIntelligence #RiskMitigation #SupplyChainResilience #InsuranceProcurement #SupplyChainManagement #ProcurementInsights #RiskAssessment #GlobalValueChain #SupplyChainIntelligence
Download Sample Copy@ https://tinyurl.com/ywb9ad...
The supply chain insurance category is anticipated to grow at a CAGR of 4.5% from 2023 to 2030. There are several possible risks and interruptions for supply chain enterprises. Due to the intricate web of interactions between vendors, suppliers, and customers, a break in one link in the supply chain can result in bigger losses in several other links. For companies whose activities are directly dependent on a major supplier's manufacturing capacity, supply chain insurance coverage is crucial.
In 2021, according to Morningstar, the COVID-19 pandemic exposed the limitations of business interruption insurance. As a result of this, there has been an increased demand for supply chain insurance significantly. Insurance companies have expanded their offerings and coverage beyond their regular Business Interruption (BI) and Contingent Business Interruption (CBI) policies.
#SupplyChainInsurance #ProcurementIntelligence #RiskMitigation #SupplyChainResilience #InsuranceProcurement #SupplyChainManagement #ProcurementInsights #RiskAssessment #GlobalValueChain #SupplyChainIntelligence
11:57 AM - May 10, 2024 (UTC)
Key Benefits of Cyber Security Risk Assessment | Digitdefence
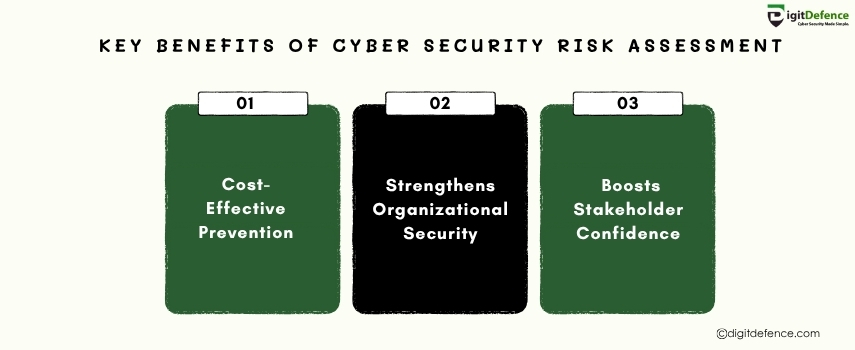
A thorough cyber security risk assessment helps organizations identify vulnerabilities, prevent data breaches, and enhance their overall security posture. By proactively addressing potential risks, businesses can avoid costly security incidents and ensure the protection of sensitive data.
#CyberSecurity #RiskAssessment #DataProtection #SecurityFirst #BusinessContinuity #DataBreachPrevention #riskmanagement #CyberThreats #SecurityStrategy #protectyourbusiness
A thorough cyber security risk assessment helps organizations identify vulnerabilities, prevent data breaches, and enhance their overall security posture. By proactively addressing potential risks, businesses can avoid costly security incidents and ensure the protection of sensitive data.
#CyberSecurity #RiskAssessment #DataProtection #SecurityFirst #BusinessContinuity #DataBreachPrevention #riskmanagement #CyberThreats #SecurityStrategy #protectyourbusiness
09:42 AM - Jun 10, 2025 (UTC)
What Happens During a Pentest | Digitdefence
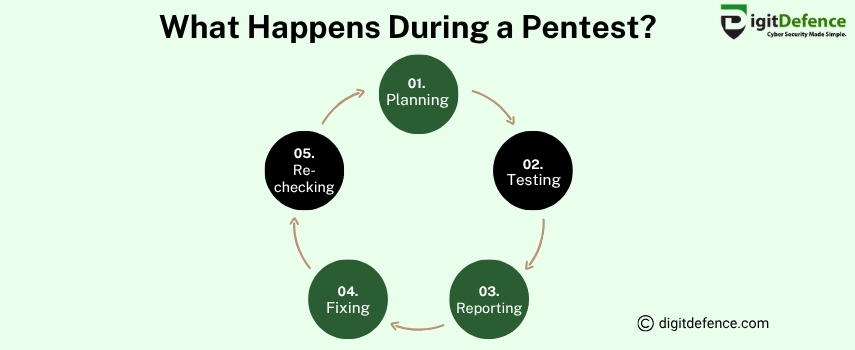
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
07:21 AM - Jun 26, 2025 (UTC)
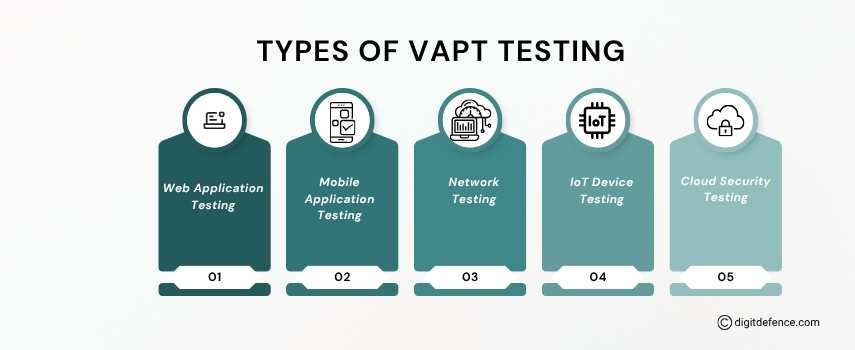
Types of VAPT Testing | Digitdefence
Types of VAPT (Vulnerability Assessment and Penetration Testing) include Network VAPT, Web Application VAPT, Mobile Application VAPT, and Wireless Network VAPT, each focusing on identifying vulnerabilities in specific areas of your infrastructure. These tests help businesses uncover potential security flaws, assess risk, and strengthen their defense mechanisms against cyber threats.
#VAPT #CyberSecurity #PenetrationTesting #networksecurity #WebApplicationSecurity #MobileSecurity #RiskAssessment #CyberThreats #securitytesting #DataProtection
Types of VAPT (Vulnerability Assessment and Penetration Testing) include Network VAPT, Web Application VAPT, Mobile Application VAPT, and Wireless Network VAPT, each focusing on identifying vulnerabilities in specific areas of your infrastructure. These tests help businesses uncover potential security flaws, assess risk, and strengthen their defense mechanisms against cyber threats.
#VAPT #CyberSecurity #PenetrationTesting #networksecurity #WebApplicationSecurity #MobileSecurity #RiskAssessment #CyberThreats #securitytesting #DataProtection
09:40 AM - Jun 11, 2025 (UTC)
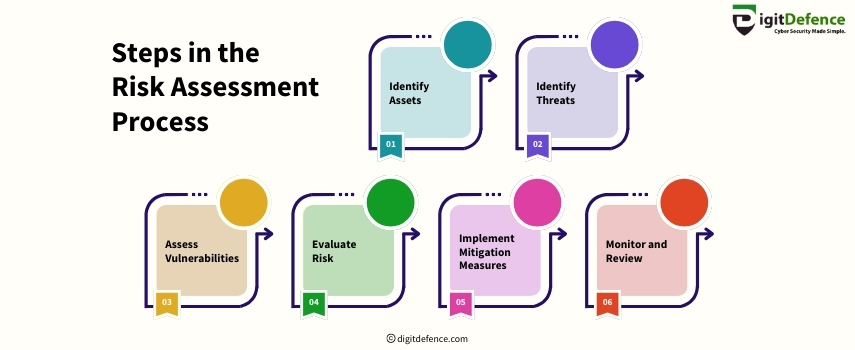
Steps in the Risk Assessment Process | Digitdefence
Risk assessment helps identify, evaluate, and mitigate potential risks to protect your business. It ensures that you can proactively address vulnerabilities and strengthen security.
#RiskAssessment #BusinessSecurity #riskmanagement #CyberSecurity #DataProtection #SecurityStrategy #VulnerabilityManagement
Risk assessment helps identify, evaluate, and mitigate potential risks to protect your business. It ensures that you can proactively address vulnerabilities and strengthen security.
#RiskAssessment #BusinessSecurity #riskmanagement #CyberSecurity #DataProtection #SecurityStrategy #VulnerabilityManagement
09:32 AM - May 20, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
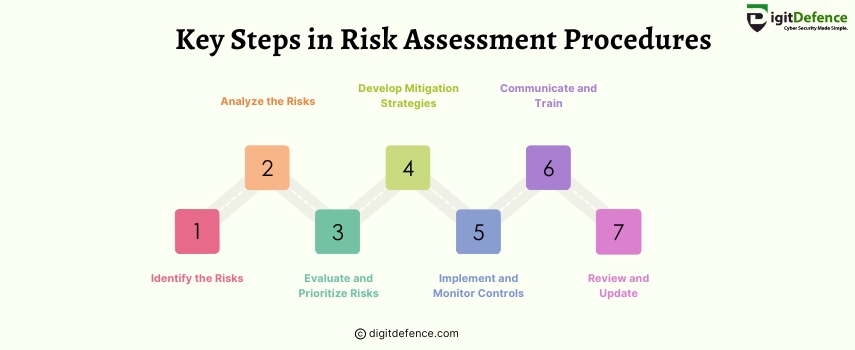
Key Steps in Risk Assessment Procedures | Digitdefence
Key Steps in Risk Assessment Procedures involve identifying potential threats, analyzing vulnerabilities, evaluating impact, and implementing controls. This structured approach helps organizations minimize risks and enhance decision-making.
#RiskAssessment #riskmanagement #BusinessContinuity #CyberRisk #SecurityPlanning
Key Steps in Risk Assessment Procedures involve identifying potential threats, analyzing vulnerabilities, evaluating impact, and implementing controls. This structured approach helps organizations minimize risks and enhance decision-making.
#RiskAssessment #riskmanagement #BusinessContinuity #CyberRisk #SecurityPlanning
09:24 AM - Jun 04, 2025 (UTC)
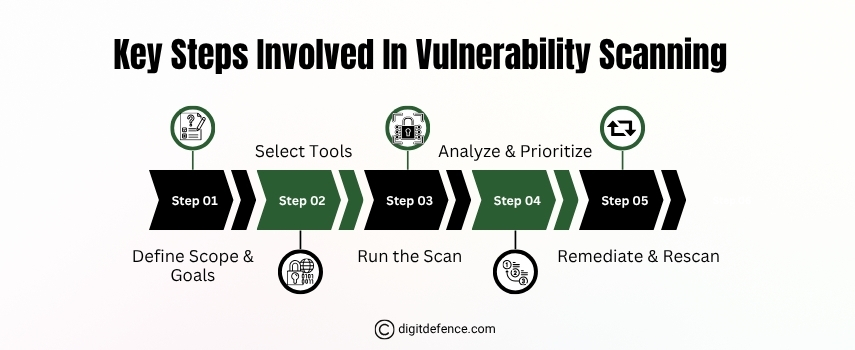
Key Steps Involved in Vulunerability Scanning | Digitdefence
Vulnerability scanning involves identifying security weaknesses in your system by scanning networks, servers, and applications for known threats. It helps businesses proactively fix issues before attackers exploit them.
#VulnerabilityScanning
#CyberSecurity
#networksecurity
#infosec
#SystemProtection
#RiskAssessment
#ITSecurity
Vulnerability scanning involves identifying security weaknesses in your system by scanning networks, servers, and applications for known threats. It helps businesses proactively fix issues before attackers exploit them.
#VulnerabilityScanning
#CyberSecurity
#networksecurity
#infosec
#SystemProtection
#RiskAssessment
#ITSecurity
06:06 AM - Jun 17, 2025 (UTC)
✔Generative AI's Flawed Code May Worsen Software Security Crisis, Warns Expert at Black Hat USA
At the Black Hat USA security prominent cybersecurity researcher Chris Wysopal raised alarms about the increasing reliance on generative AI for code development.
For More Information
?Read- https://cybrpro.com/genera...
and get insights
#GenerativeAI #SoftwareSecurity #FlawedCode #BlackHatUSA #CyberSecurity #AIThreats #TechExperts #Cyberpromagazine #SecurityCrisis #DataBreach #Malware #AIinCybersecurity #DigitalSafety #TechTalk #Vulnerabilities #InformationSecurity #AIConsensus #RiskAssessment #CyberAwareness #SecurityConcerns #FutureOfTech
At the Black Hat USA security prominent cybersecurity researcher Chris Wysopal raised alarms about the increasing reliance on generative AI for code development.
For More Information
?Read- https://cybrpro.com/genera...
and get insights
#GenerativeAI #SoftwareSecurity #FlawedCode #BlackHatUSA #CyberSecurity #AIThreats #TechExperts #Cyberpromagazine #SecurityCrisis #DataBreach #Malware #AIinCybersecurity #DigitalSafety #TechTalk #Vulnerabilities #InformationSecurity #AIConsensus #RiskAssessment #CyberAwareness #SecurityConcerns #FutureOfTech
04:46 AM - Aug 21, 2024 (UTC)
In our latest study, we explore how a leading pharmaceutical company outsourced their non-core activities to achieve significant cost savings, increased efficiency, and enhanced flexibility.
Curious to learn how outsourcing can unlock your business's full potential?
Read the full report below.
https://www.jaspercolin.co...
#HealthCare #PharmaIndustry #outsourcing #RiskAssessment #BenchmarkBusiness
Curious to learn how outsourcing can unlock your business's full potential?
Read the full report below.
https://www.jaspercolin.co...
#HealthCare #PharmaIndustry #outsourcing #RiskAssessment #BenchmarkBusiness

Breaking Free From Constraints: Benefits of Outsourcing Non-Core Activities
In our latest study, we explore how a leading pharmaceutical company outsourced their non-core activities to achieve significant cost savings, increased efficiency, and enhanced flexibility.
https://www.jaspercolin.com/insights/research-series/breaking-free-from-constraints-benefits-of-outsourcing-non-core-activities
04:20 PM - Oct 09, 2024 (UTC)
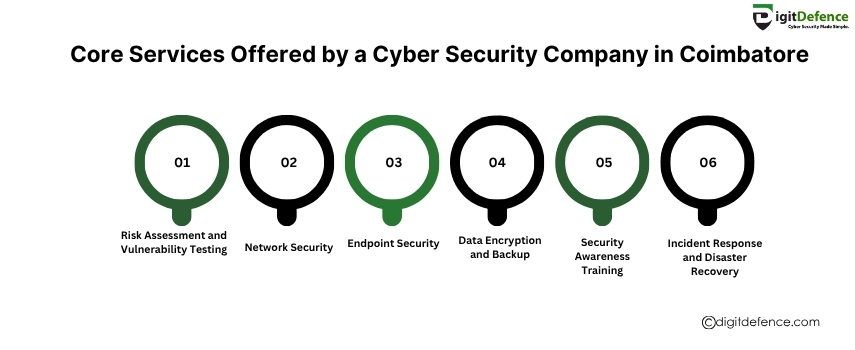
Core Services Offered By a Cyber Security Company in Coimbatore
A reliable cyber security company in Coimbatore provides essential services like risk assessment, network security, threat detection, data encryption, and incident response to protect your business from evolving cyber threats.
#CyberSecurityCoimbatore #RiskAssessment #networksecurity #ThreatDetection #DataEncryption #IncidentResponse #BusinessProtection
A reliable cyber security company in Coimbatore provides essential services like risk assessment, network security, threat detection, data encryption, and incident response to protect your business from evolving cyber threats.
#CyberSecurityCoimbatore #RiskAssessment #networksecurity #ThreatDetection #DataEncryption #IncidentResponse #BusinessProtection
06:55 AM - Jun 21, 2025 (UTC)