AI Discovers Zero-Days: What You Must Know
Zero-day vulnerabilities—once uncovered only by expert hackers or nation-states—are now being identified by Artificial Intelligence (AI). This shift is transforming cybersecurity across industries. If you're in IT, development, or value digital safety, this matters.
What Are Zero-Day Vulnerabilities?
These are unknown software flaws with no patch. Hackers exploit them before developers react, causing data breaches and ransomware attacks.
How AI Is Changing Detection
Previously, finding zero-days meant manual code review and threat modeling. Now, AI uses machine learning and pattern recognition to analyze code, detect flaws, and simulate attacks—dramatically reducing response time.
AI can:
Automate code scanning
Spot known and unknown threats
Detect anomalies early
Benefits:
Proactive defense: AI identifies threats before attacks
Fewer errors: Better accuracy than manual scans
Scalable: Analyzes vast codebases instantly
Faster: Detects issues in minutes, not weeks
Risks:
Adversarial AI by hackers
Overreliance on flawed models
Privacy concerns from data access
Best Practices:
Combine AI with human review
Keep models updated
Use AI as part of a layered defense
Monitor AI systems for abuse
Bottom Line:
AI is revolutionizing how we find and fix zero-day vulnerabilities. It’s fast, powerful—and essential for modern cybersecurity.
Visit Us: https://www.datspy.com/
Zero-day vulnerabilities—once uncovered only by expert hackers or nation-states—are now being identified by Artificial Intelligence (AI). This shift is transforming cybersecurity across industries. If you're in IT, development, or value digital safety, this matters.
What Are Zero-Day Vulnerabilities?
These are unknown software flaws with no patch. Hackers exploit them before developers react, causing data breaches and ransomware attacks.
How AI Is Changing Detection
Previously, finding zero-days meant manual code review and threat modeling. Now, AI uses machine learning and pattern recognition to analyze code, detect flaws, and simulate attacks—dramatically reducing response time.
AI can:
Automate code scanning
Spot known and unknown threats
Detect anomalies early
Benefits:
Proactive defense: AI identifies threats before attacks
Fewer errors: Better accuracy than manual scans
Scalable: Analyzes vast codebases instantly
Faster: Detects issues in minutes, not weeks
Risks:
Adversarial AI by hackers
Overreliance on flawed models
Privacy concerns from data access
Best Practices:
Combine AI with human review
Keep models updated
Use AI as part of a layered defense
Monitor AI systems for abuse
Bottom Line:
AI is revolutionizing how we find and fix zero-day vulnerabilities. It’s fast, powerful—and essential for modern cybersecurity.
Visit Us: https://www.datspy.com/
07:13 AM - Jul 01, 2025 (UTC)
Embedded Security Market size is growing at a CAGR of 10%
The Global Embedded Security Market size is expected to be worth around USD 26.5 Billion By 2034, from USD 10.2 billion in 2024, growing at a CAGR of 10% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 40.2% share, holding USD 4.1 Billion revenue.
Read more - https://market.us/report/g...
The Embedded Security Market refers to the industry focused on integrating security solutions directly into hardware and software systems to protect devices from cyber threats. It encompasses technologies like encryption, secure boot, and authentication mechanisms embedded in devices such as IoT gadgets, automotive systems, and smart cards. This market is critical as it safeguards sensitive data and ensures the integrity of connected devices in an increasingly digital world. Its growth is driven by the need for robust protection against evolving cyber risks, making it essential for industries like healthcare, automotive, and consumer electronics.
The Embedded Security Market, in a broader sense, represents the ecosystem of solutions designed to secure embedded systems, which are specialized computing systems performing dedicated functions within larger devices. It includes hardware like secure microcontrollers and software like firmware updates, addressing vulnerabilities in connected environments.
The Global Embedded Security Market size is expected to be worth around USD 26.5 Billion By 2034, from USD 10.2 billion in 2024, growing at a CAGR of 10% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 40.2% share, holding USD 4.1 Billion revenue.
Read more - https://market.us/report/g...
The Embedded Security Market refers to the industry focused on integrating security solutions directly into hardware and software systems to protect devices from cyber threats. It encompasses technologies like encryption, secure boot, and authentication mechanisms embedded in devices such as IoT gadgets, automotive systems, and smart cards. This market is critical as it safeguards sensitive data and ensures the integrity of connected devices in an increasingly digital world. Its growth is driven by the need for robust protection against evolving cyber risks, making it essential for industries like healthcare, automotive, and consumer electronics.
The Embedded Security Market, in a broader sense, represents the ecosystem of solutions designed to secure embedded systems, which are specialized computing systems performing dedicated functions within larger devices. It includes hardware like secure microcontrollers and software like firmware updates, addressing vulnerabilities in connected environments.
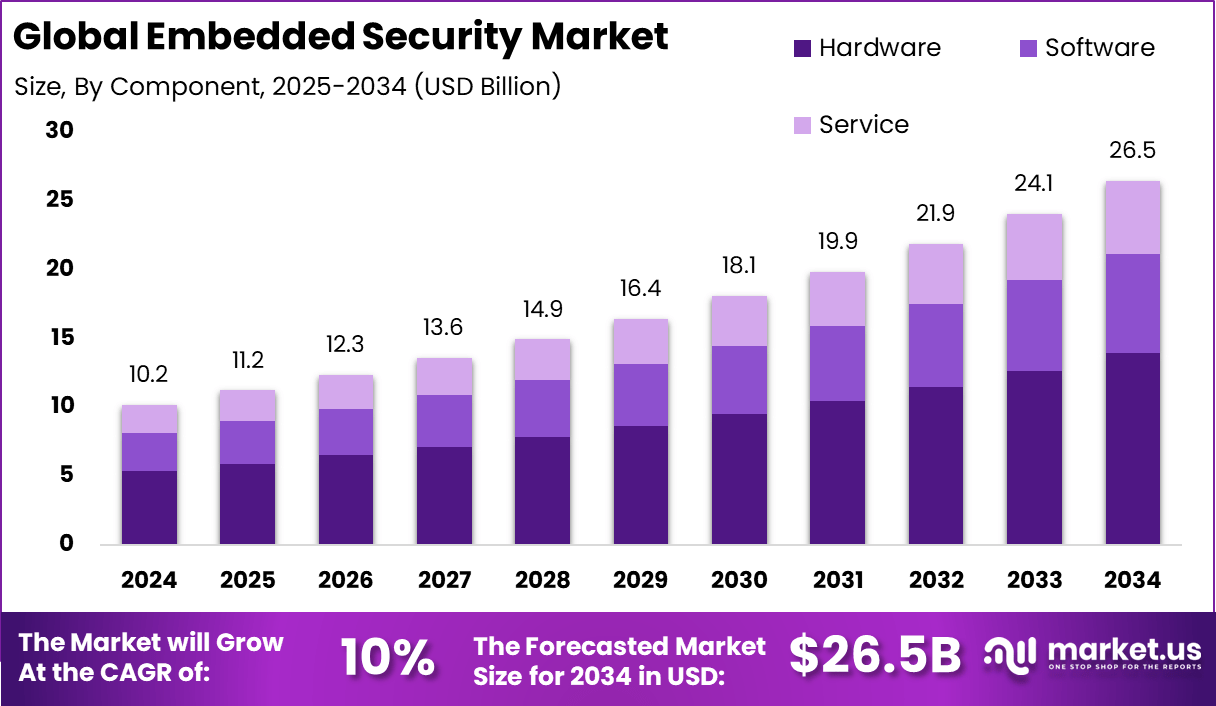
Embedded Security Market Size, Share | CAGR of 10%
By 2034, the Embedded Security Market is expected to reach a valuation of USD 26.5 billion, expanding at a healthy CAGR of 10%.
https://market.us/report/global-embedded-security-market/
04:24 AM - Jun 27, 2025 (UTC)
Reliable Building Security Services in Maryland
At Ingenuity Security Solutions, we specialize in providing top-tier building security services in Maryland, designed to ensure safety, protect assets, and promote peace of mind. Whether you manage a commercial complex, government facility, residential community, or educational institution, our expert team delivers customized security strategies tailored to your unique requirements. building security services
With a proactive approach and a commitment to conscious ingenuity, our security professionals combine the latest technologies with on-the-ground intelligence to offer a robust layer of protection. From 24/7 manned guarding and access control systems to advanced surveillance solutions, we ensure that every aspect of your property is monitored and secured. Our goal is to prevent incidents before they occur by detecting vulnerabilities early and responding swiftly to any threat.
As security solutions consultants, we go beyond standard protocols by conducting thorough risk assessments and advising clients on the best security upgrades and practices. Our integrated solutions include cutting-edge IT and security services in Maryland, helping clients bridge physical and digital security gaps. This holistic approach ensures your assets are protected from both physical intrusions and cyber threats. security service solutions
At Ingenuity Security Solutions, we specialize in providing top-tier building security services in Maryland, designed to ensure safety, protect assets, and promote peace of mind. Whether you manage a commercial complex, government facility, residential community, or educational institution, our expert team delivers customized security strategies tailored to your unique requirements. building security services
With a proactive approach and a commitment to conscious ingenuity, our security professionals combine the latest technologies with on-the-ground intelligence to offer a robust layer of protection. From 24/7 manned guarding and access control systems to advanced surveillance solutions, we ensure that every aspect of your property is monitored and secured. Our goal is to prevent incidents before they occur by detecting vulnerabilities early and responding swiftly to any threat.
As security solutions consultants, we go beyond standard protocols by conducting thorough risk assessments and advising clients on the best security upgrades and practices. Our integrated solutions include cutting-edge IT and security services in Maryland, helping clients bridge physical and digital security gaps. This holistic approach ensures your assets are protected from both physical intrusions and cyber threats. security service solutions
02:24 PM - Jun 28, 2025 (UTC)
Cyber Security Consultancy Services
Cyber threats have become more frequent and sophisticated, and I’ve learnt that taking a reactive approach simply isn’t enough anymore. That’s why I started working with cyber security consultancy services to strengthen our digital defences. I didn’t just want to tick boxes—I needed a comprehensive strategy that could identify gaps, improve resilience, and help our team respond effectively if an incident occurred. These services didn’t just offer technical fixes; they helped build a culture of awareness, which has made a lasting difference. From assessing vulnerabilities to developing a practical response plan, I was involved in every step. It was eye-opening to realise how many areas needed attention—network security, staff training, access controls, and even incident simulations. Working alongside experienced professionals made all the difference; their guidance turned a fragmented setup into a coordinated defence. I now understand the importance of having a clear, evolving strategy for cyber threats. If you’re managing any kind of data or infrastructure in today’s digital landscape, I believe it’s essential to take proactive steps.
Click our link for more details: https://www.cm-alliance.co...
Cyber threats have become more frequent and sophisticated, and I’ve learnt that taking a reactive approach simply isn’t enough anymore. That’s why I started working with cyber security consultancy services to strengthen our digital defences. I didn’t just want to tick boxes—I needed a comprehensive strategy that could identify gaps, improve resilience, and help our team respond effectively if an incident occurred. These services didn’t just offer technical fixes; they helped build a culture of awareness, which has made a lasting difference. From assessing vulnerabilities to developing a practical response plan, I was involved in every step. It was eye-opening to realise how many areas needed attention—network security, staff training, access controls, and even incident simulations. Working alongside experienced professionals made all the difference; their guidance turned a fragmented setup into a coordinated defence. I now understand the importance of having a clear, evolving strategy for cyber threats. If you’re managing any kind of data or infrastructure in today’s digital landscape, I believe it’s essential to take proactive steps.
Click our link for more details: https://www.cm-alliance.co...
05:50 AM - Jun 27, 2025 (UTC)
Many users search for “Wink Mod APK for iOS” https://winkapkp.com/for-i... hoping to unlock premium features or bypass restrictions in the Wink app. However, it’s important to clarify that APK files are specifically designed for Android devices and cannot be installed on iOS devices such as iPhones or iPads. iOS apps use a different file format called IPA, and modded APKs are incompatible with this system. Additionally, installing modded apps on iOS typically requires jailbreaking, which can expose your device to security vulnerabilities, void your warranty, and put your personal data at risk.
12:43 PM - Jun 28, 2025 (UTC)
Using Cyber Security Consulting Services to Increase Business Resilience
We offer expert guidance to protect your business from online threats with our Cyber Security Consulting Services. To prevent cyberattacks, we provide robust security frameworks, detect vulnerabilities, and implement tailored strategies. Our team provides everything from risk assessment and compliance to incident response and ongoing monitoring to ensure the security and resilience of your IT infrastructure. Whether your business is new or well-established, we offer solutions that help you achieve your goals while following industry standards. You can rely on us to safeguard your data, systems, and reputation in an increasingly complex cyberspace. https://500px.com/photo/11...
We offer expert guidance to protect your business from online threats with our Cyber Security Consulting Services. To prevent cyberattacks, we provide robust security frameworks, detect vulnerabilities, and implement tailored strategies. Our team provides everything from risk assessment and compliance to incident response and ongoing monitoring to ensure the security and resilience of your IT infrastructure. Whether your business is new or well-established, we offer solutions that help you achieve your goals while following industry standards. You can rely on us to safeguard your data, systems, and reputation in an increasingly complex cyberspace. https://500px.com/photo/11...
12:20 PM - Jun 26, 2025 (UTC)
Dallas Alarm System Installation Checklist What Every Property Owner Should Know
If you’re planning to install or upgrade your alarm system in Dallas, don’t miss this interactive Evernote checklist. Created by the experts at Dallas Alarm Systems, this all-in-one resource helps you assess your property’s vulnerabilities, compare system features, and evaluate professional installers.
Read More:- https://share.evernote.com...
If you’re planning to install or upgrade your alarm system in Dallas, don’t miss this interactive Evernote checklist. Created by the experts at Dallas Alarm Systems, this all-in-one resource helps you assess your property’s vulnerabilities, compare system features, and evaluate professional installers.
Read More:- https://share.evernote.com...
11:16 AM - Jun 24, 2025 (UTC)
Is Your Business at Risk? How a Security Testing Company Can Protect You
Cyber threats are evolving—are you prepared? This blog reveals how a trusted security testing company can help uncover hidden vulnerabilities in your systems, strengthen your defenses, and protect your business from costly breaches. Learn why regular security assessments are essential for staying ahead of hackers and maintaining business continuity.
https://qaontop.com/servic...
#CyberSecurity #securitytesting #DataProtection #BusinessSecurity #PenetrationTesting #VulnerabilityAssessment #infosec #CyberThreats #SecureYourBusiness #TechSecurity
Cyber threats are evolving—are you prepared? This blog reveals how a trusted security testing company can help uncover hidden vulnerabilities in your systems, strengthen your defenses, and protect your business from costly breaches. Learn why regular security assessments are essential for staying ahead of hackers and maintaining business continuity.
https://qaontop.com/servic...
#CyberSecurity #securitytesting #DataProtection #BusinessSecurity #PenetrationTesting #VulnerabilityAssessment #infosec #CyberThreats #SecureYourBusiness #TechSecurity
11:51 AM - Jul 02, 2025 (UTC)
How to Choose the Right Web App Pentesting Provider | Digitdefence
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
09:51 AM - Jun 27, 2025 (UTC)
API Security Market size is growing at a CAGR of 32.2%
The Global API Security Market size is expected to be worth around USD 12,245.7 million by 2034, from USD 751.05 million in 2024, growing at a CAGR of 32.2% during the forecast period from 2025 to 2034. North America held a dominant market position, capturing more than a 42% share, holding USD 315.4 million in revenue.
Read more - https://market.us/report/a...
The API Security Market refers to the industry focused on solutions and services designed to protect Application Programming Interfaces (APIs) from cyber threats. APIs are critical for enabling communication and data exchange between software systems, powering everything from mobile apps to cloud services. As businesses increasingly rely on APIs to drive digital transformation, the need to secure these interfaces against vulnerabilities like data breaches, unauthorized access, and injection attacks has grown. This market includes software, platforms, and services like API gateways, encryption tools, and threat detection systems, all aimed at ensuring secure and compliant API operations across industries such as finance, healthcare, and e-commerce.
The Global API Security Market size is expected to be worth around USD 12,245.7 million by 2034, from USD 751.05 million in 2024, growing at a CAGR of 32.2% during the forecast period from 2025 to 2034. North America held a dominant market position, capturing more than a 42% share, holding USD 315.4 million in revenue.
Read more - https://market.us/report/a...
The API Security Market refers to the industry focused on solutions and services designed to protect Application Programming Interfaces (APIs) from cyber threats. APIs are critical for enabling communication and data exchange between software systems, powering everything from mobile apps to cloud services. As businesses increasingly rely on APIs to drive digital transformation, the need to secure these interfaces against vulnerabilities like data breaches, unauthorized access, and injection attacks has grown. This market includes software, platforms, and services like API gateways, encryption tools, and threat detection systems, all aimed at ensuring secure and compliant API operations across industries such as finance, healthcare, and e-commerce.
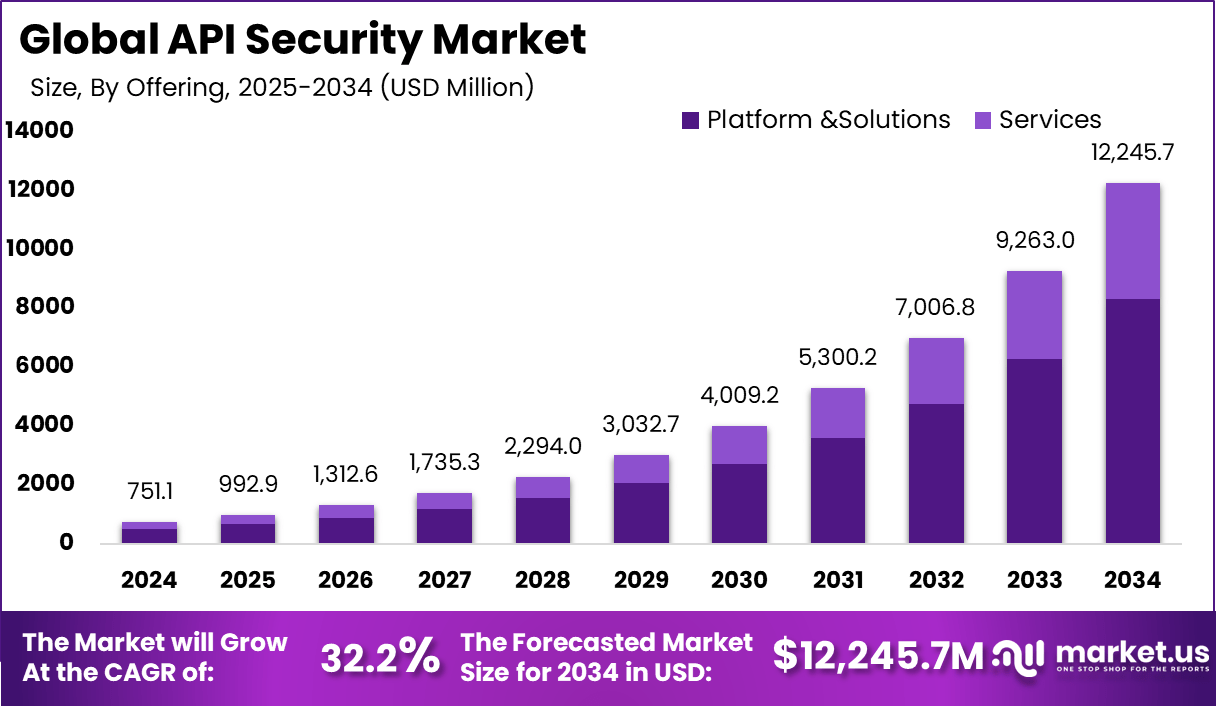
API Security Market Size, Share | CAGR of 32.2%
By 2034, the API Security Market is expected to reach a valuation of USD 12,245.7 Million, expanding at a healthy CAGR of 32.2%.
https://market.us/report/api-security-market/
04:16 AM - Jun 26, 2025 (UTC)
Overview: “AI in Cybersecurity: Double‑Edged Sword”
The Good: AI as a Cybersecurity Game-Changer
AI has dramatically transformed how we defend digital infrastructures. Its ability to analyze vast datasets, detect anomalies, and respond to threats in real-time is unparalleled. With machine learning algorithms, AI tools can predict and neutralize threats before they manifest.
AI-driven cybersecurity empower organizations to:
Detect zero-day vulnerabilities
Automate threat response
Identify insider threats
Optimize security workflows
The Bad: AI as a Weapon for Cybercriminals
Unfortunately, the same technologies that protect us can be weaponized. Hackers now deploy AI to craft more sophisticated phishing attacks, generate malicious deepfakes, and bypass traditional security measures with alarming precision.
The dark side of AI includes:
AI-Powered Malware: Capable of morphing signatures to evade detection.
Smart Phishing: AI tools can personalize and scale phishing campaigns using scraped data.
Deepfake Technology: Creates convincing audio/video fabrications that deceive users and systems.
Organizations must embrace AI-enhanced cybersecurity solutions while remaining vigilant against AI-driven threats. The key is not just adoption but ethical implementation, robust regulation, and continuous education.
For more information, visit us: https://www.datspy.com/
The Good: AI as a Cybersecurity Game-Changer
AI has dramatically transformed how we defend digital infrastructures. Its ability to analyze vast datasets, detect anomalies, and respond to threats in real-time is unparalleled. With machine learning algorithms, AI tools can predict and neutralize threats before they manifest.
AI-driven cybersecurity empower organizations to:
Detect zero-day vulnerabilities
Automate threat response
Identify insider threats
Optimize security workflows
The Bad: AI as a Weapon for Cybercriminals
Unfortunately, the same technologies that protect us can be weaponized. Hackers now deploy AI to craft more sophisticated phishing attacks, generate malicious deepfakes, and bypass traditional security measures with alarming precision.
The dark side of AI includes:
AI-Powered Malware: Capable of morphing signatures to evade detection.
Smart Phishing: AI tools can personalize and scale phishing campaigns using scraped data.
Deepfake Technology: Creates convincing audio/video fabrications that deceive users and systems.
Organizations must embrace AI-enhanced cybersecurity solutions while remaining vigilant against AI-driven threats. The key is not just adoption but ethical implementation, robust regulation, and continuous education.
For more information, visit us: https://www.datspy.com/
09:47 AM - Jun 30, 2025 (UTC)
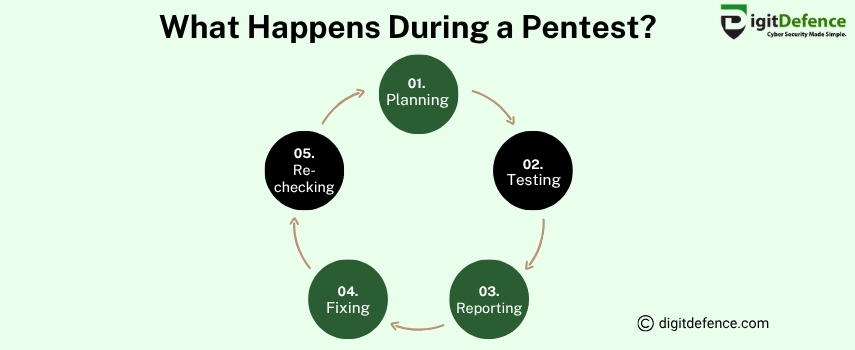
What Happens During a Pentest | Digitdefence
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
07:21 AM - Jun 26, 2025 (UTC)
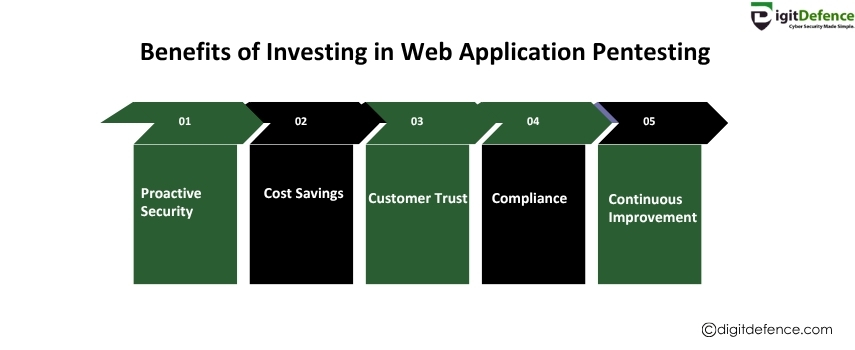
Benefits of Investing in Web Application Pentesting
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
07:12 AM - Jun 26, 2025 (UTC)
Anti-Drone Market size is growing at a CAGR of 27.3%
The Global Anti-Drone Market size is expected to be worth around USD 28.1 Billion By 2034, from USD 2.5 billion in 2024, growing at a CAGR of 27.3% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 46.8% share, holding USD 1.1 Billion revenue. In the United States, the market is valued at USD 0.74 Billion in 2024 and is projected to grow at a CAGR of 27.5% during the forecast period.
Read more - https://market.us/report/a...
The anti-drone market refers to the industry focused on developing and deploying technologies to detect, track, and neutralize unauthorized or malicious drones. It encompasses a range of solutions, from radar systems and radio frequency jammers to laser-based interception tools, all designed to address the growing threat of drones used for illegal activities like smuggling, espionage, or terrorism. This market serves various sectors, including military, government, critical infrastructure, and commercial industries, aiming to ensure airspace security and public safety. As drones become more accessible and sophisticated, the need for robust countermeasures has surged, driving innovation and investment in this space. The market is dynamic, with a strong emphasis on adapting to evolving drone technologies and addressing security vulnerabilities in both urban and remote environments.
The Global Anti-Drone Market size is expected to be worth around USD 28.1 Billion By 2034, from USD 2.5 billion in 2024, growing at a CAGR of 27.3% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 46.8% share, holding USD 1.1 Billion revenue. In the United States, the market is valued at USD 0.74 Billion in 2024 and is projected to grow at a CAGR of 27.5% during the forecast period.
Read more - https://market.us/report/a...
The anti-drone market refers to the industry focused on developing and deploying technologies to detect, track, and neutralize unauthorized or malicious drones. It encompasses a range of solutions, from radar systems and radio frequency jammers to laser-based interception tools, all designed to address the growing threat of drones used for illegal activities like smuggling, espionage, or terrorism. This market serves various sectors, including military, government, critical infrastructure, and commercial industries, aiming to ensure airspace security and public safety. As drones become more accessible and sophisticated, the need for robust countermeasures has surged, driving innovation and investment in this space. The market is dynamic, with a strong emphasis on adapting to evolving drone technologies and addressing security vulnerabilities in both urban and remote environments.
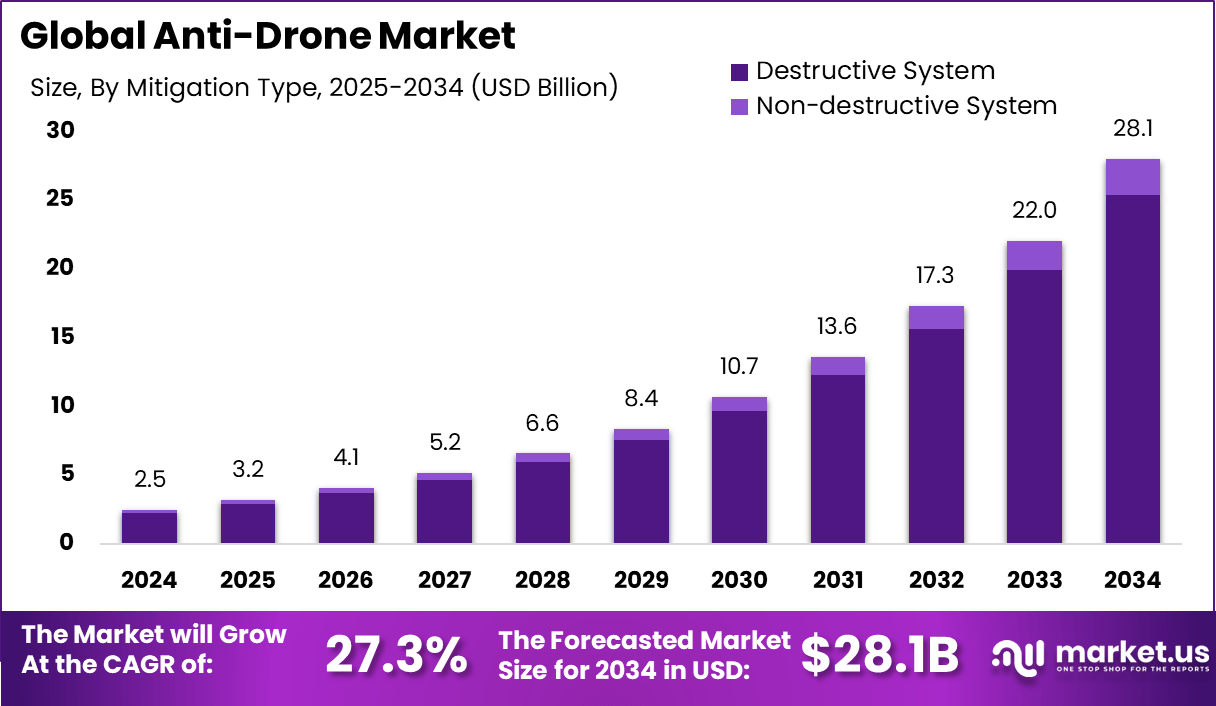
Anti-Drone Market Size, Share | CAGR of 27.3%
By 2034, the Anti-Drone Market is expected to reach a valuation of USD 28.1 billion, expanding at a healthy CAGR of 27.3%.
https://market.us/report/anti-drone-market/
04:17 AM - Jun 24, 2025 (UTC)
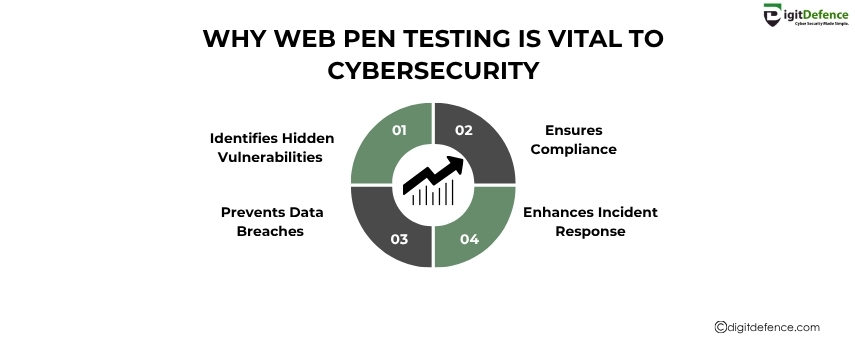
Why Web Pen Testing is Vital To Cybersecurity | Digitdefence
Web Pen Testing is vital to cybersecurity as it uncovers hidden vulnerabilities before attackers exploit them. Regular testing strengthens defenses, reduces breach risks, and ensures data protection.
#WebPenTesting #CyberSecurity #EthicalHacking #DataProtection #VulnerabilityAssessment #infosec
Web Pen Testing is vital to cybersecurity as it uncovers hidden vulnerabilities before attackers exploit them. Regular testing strengthens defenses, reduces breach risks, and ensures data protection.
#WebPenTesting #CyberSecurity #EthicalHacking #DataProtection #VulnerabilityAssessment #infosec
09:18 AM - Jun 24, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/