From Chaos to Control: How Codebeamer Enhances Risk Management & Change Impact Analysis
"Explore how Codebeamer transforms product development by streamlining risk management and change impact analysis. Improve traceability, compliance, and decision-making with this powerful ALM tool.
Read More : https://3hti.com/alm/from-...
Looking to upgrade, contact us: 609-303-3400"
#codebeamer #riskmanagement #ChangeImpactAnalysis #ALMSolutions #EngineeringExcellence #ProcessOptimization #TraceabilityTools
"Explore how Codebeamer transforms product development by streamlining risk management and change impact analysis. Improve traceability, compliance, and decision-making with this powerful ALM tool.
Read More : https://3hti.com/alm/from-...
Looking to upgrade, contact us: 609-303-3400"
#codebeamer #riskmanagement #ChangeImpactAnalysis #ALMSolutions #EngineeringExcellence #ProcessOptimization #TraceabilityTools

From Chaos to Control: Risk & Change with Codebeamer
Codebeamer simplifies risk tracking and change analysis for teams needing better project control.
https://3hti.com/alm/from-chaos-to-control-how-codebeamer-enables-risk-management-and-change-impact-analysis/
10:14 AM - Jun 30, 2025 (UTC)
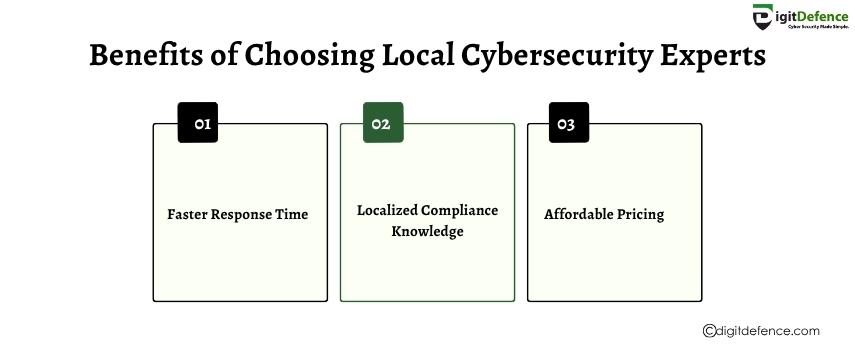
Benefits of Choosing Local Cybersecurity Experts | Digitdefence
Choosing local cybersecurity experts means faster response times, personalized support, and a deeper understanding of regional threats and compliance needs. Strengthen your defense with professionals who know your business environment.
#CyberSecurity #LocalExperts #ITSecuritySupport #DataProtection #riskmanagement #Compliance #CyberDefense #SmallBusinessSecurity #EndpointSecurity #NetworkProtection
Choosing local cybersecurity experts means faster response times, personalized support, and a deeper understanding of regional threats and compliance needs. Strengthen your defense with professionals who know your business environment.
#CyberSecurity #LocalExperts #ITSecuritySupport #DataProtection #riskmanagement #Compliance #CyberDefense #SmallBusinessSecurity #EndpointSecurity #NetworkProtection
09:47 AM - Jul 03, 2025 (UTC)
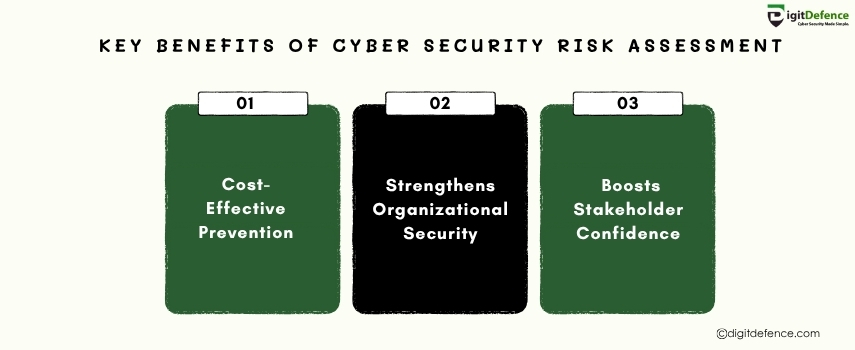
Key Benefits of Cyber Security Risk Assessment | Digitdefence
A thorough cyber security risk assessment helps organizations identify vulnerabilities, prevent data breaches, and enhance their overall security posture. By proactively addressing potential risks, businesses can avoid costly security incidents and ensure the protection of sensitive data.
#CyberSecurity #RiskAssessment #DataProtection #SecurityFirst #BusinessContinuity #DataBreachPrevention #riskmanagement #CyberThreats #SecurityStrategy #protectyourbusiness
A thorough cyber security risk assessment helps organizations identify vulnerabilities, prevent data breaches, and enhance their overall security posture. By proactively addressing potential risks, businesses can avoid costly security incidents and ensure the protection of sensitive data.
#CyberSecurity #RiskAssessment #DataProtection #SecurityFirst #BusinessContinuity #DataBreachPrevention #riskmanagement #CyberThreats #SecurityStrategy #protectyourbusiness
09:42 AM - Jun 10, 2025 (UTC)
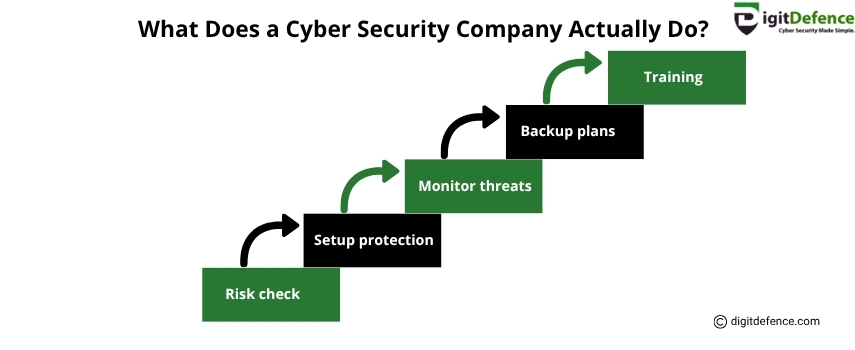
What Does a Cyber Security Company Do | Digitdefence
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
06:33 AM - Jun 25, 2025 (UTC)
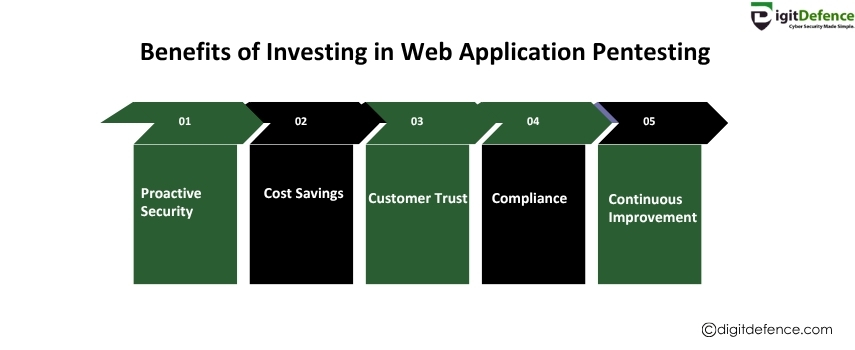
Benefits of Investing in Web Application Pentesting
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps
07:12 AM - Jun 26, 2025 (UTC)
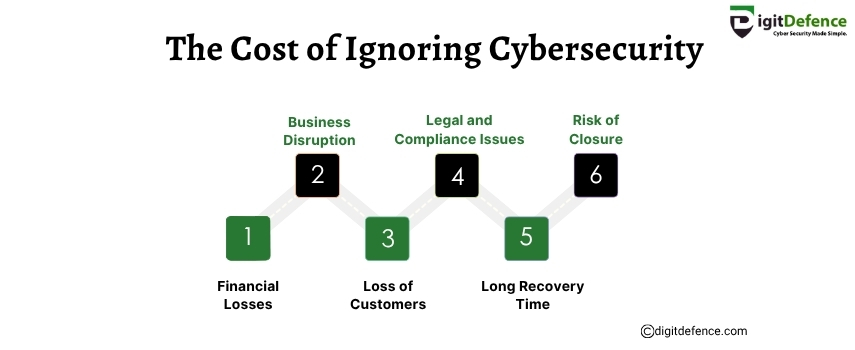
The Cost of Ignoring Cybersecurity | Digitdefence
Ignoring cybersecurity can lead to devastating data breaches, costly downtime, and severe damage to your brand’s reputation. Investing in robust security measures is essential to protect your business from financial losses and legal penalties.
#CyberSecurity #DataProtection #infosec #CyberAttack #BusinessSecurity #riskmanagement
Ignoring cybersecurity can lead to devastating data breaches, costly downtime, and severe damage to your brand’s reputation. Investing in robust security measures is essential to protect your business from financial losses and legal penalties.
#CyberSecurity #DataProtection #infosec #CyberAttack #BusinessSecurity #riskmanagement
06:54 AM - Jun 19, 2025 (UTC)
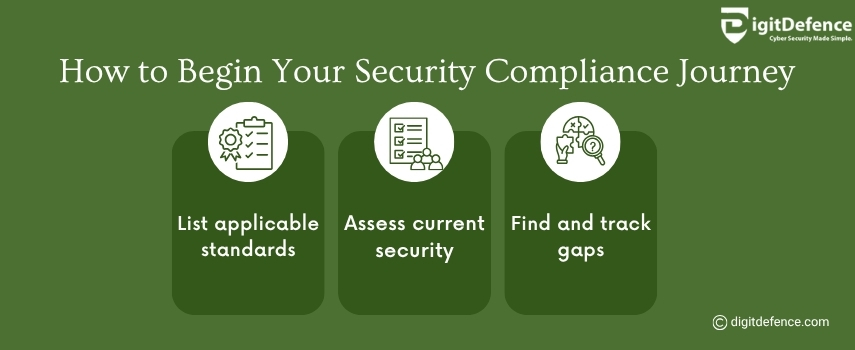
How to Begin Your Security Compliance Journey | Digitdefence
Starting your security compliance journey involves assessing current risks, understanding relevant regulations, and implementing robust policies and controls. Regular audits and employee training are key to maintaining compliance and protecting your business.
#SecurityCompliance #riskmanagement #DataProtection #CyberSecurity #ComplianceJourney
Starting your security compliance journey involves assessing current risks, understanding relevant regulations, and implementing robust policies and controls. Regular audits and employee training are key to maintaining compliance and protecting your business.
#SecurityCompliance #riskmanagement #DataProtection #CyberSecurity #ComplianceJourney
09:09 AM - Jun 23, 2025 (UTC)
Elevate Your Safety Standards with bizSAFE Certification – Powered by Greensafe
Want to grow your business credibility and qualify for more tenders in Singapore? Start your bizSAFE journey with Greensafe International, your trusted WSH consultant for bizSAFE Level 3, Level 4, bizSAFE STAR, and bizSAFE Partner certifications.
Our expert team helps you implement Risk Management Plans, build a WSH Management System (SS506/ISO 45001), and prepare for audits so you can achieve bizSAFE status smoothly and quickly. Whether you're a small business or a large organization, bizSAFE enhances safety culture, reduces incidents, and boosts client confidence.
✔ MOM & WSHC-compliant
✔ Fast-track certification support
✔ ISO 45001 & SS506 consultancy
✔ Recognized by major clients & contractors
Get certified. Get noticed. Get ahead—with Greensafe.
Learn more:
https://www.greensafe.com....
#bizSAFE #bizSAFELevel3 #bizSAFELevel4 #bizSAFESTAR #greensafe #WSHtraining #iso45001 #SingaporeBusiness #WorkplaceSafety #riskmanagement #bizSAFEconsultant #SS506 #SafetyFirst #GreensafeSingapore #culture
Want to grow your business credibility and qualify for more tenders in Singapore? Start your bizSAFE journey with Greensafe International, your trusted WSH consultant for bizSAFE Level 3, Level 4, bizSAFE STAR, and bizSAFE Partner certifications.
Our expert team helps you implement Risk Management Plans, build a WSH Management System (SS506/ISO 45001), and prepare for audits so you can achieve bizSAFE status smoothly and quickly. Whether you're a small business or a large organization, bizSAFE enhances safety culture, reduces incidents, and boosts client confidence.
✔ MOM & WSHC-compliant
✔ Fast-track certification support
✔ ISO 45001 & SS506 consultancy
✔ Recognized by major clients & contractors
Get certified. Get noticed. Get ahead—with Greensafe.
Learn more:
https://www.greensafe.com....
#bizSAFE #bizSAFELevel3 #bizSAFELevel4 #bizSAFESTAR #greensafe #WSHtraining #iso45001 #SingaporeBusiness #WorkplaceSafety #riskmanagement #bizSAFEconsultant #SS506 #SafetyFirst #GreensafeSingapore #culture

Advance from Bizsafe Level 2 Course to 3 & 4 Today!
Reach Bizsafe 3 or 4 with ease. Start from Level 2 course and let Greensafe guide your journey to Bizsafe Star certification in Singapore.
https://www.greensafe.com.sg/services/rma-bizsafe-levels-3-4-bizsafe-partner-bizsafe-star/
04:32 AM - Jun 18, 2025 (UTC)
In today’s volatile markets, effective risk management is crucial. Our AI-powered Hedge Trading Bot delivers automated, adaptive strategies to protect capital and gain profit. With real-time analytics, consistent exchange integration, and full transparency, it’s built for traders and institutions seeking smarter, more reliable trading automation.
Explore More : https://www.addustechnolog...
#HedgeTrading #riskmanagement #TradingTechnology #FintechSolutions #AITrading #AutomatedTrading #PortfolioProtection
Explore More : https://www.addustechnolog...
#HedgeTrading #riskmanagement #TradingTechnology #FintechSolutions #AITrading #AutomatedTrading #PortfolioProtection
08:54 AM - Jul 03, 2025 (UTC)
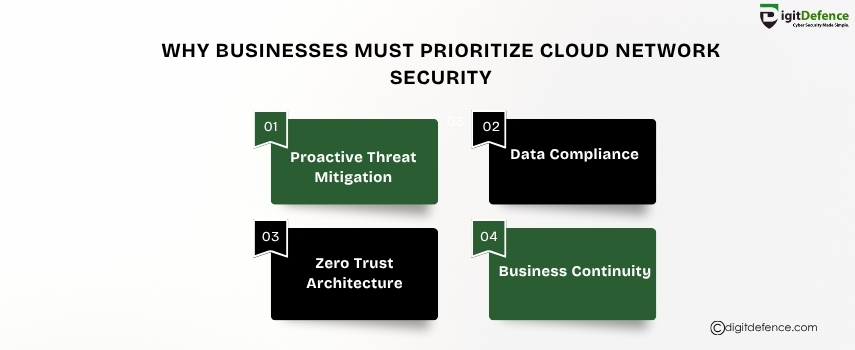
Why Businesses Must Prioritize Cloud Network Security
As businesses move to the cloud, securing network infrastructure becomes critical. Protect sensitive data, ensure uptime, and stay compliant with robust cloud security.
#cloudsecurity #networksecurity #DataProtection #CyberSecurity #CloudCompliance #BusinessSecurity #ITInfrastructure #cloudcomputing #riskmanagement
As businesses move to the cloud, securing network infrastructure becomes critical. Protect sensitive data, ensure uptime, and stay compliant with robust cloud security.
#cloudsecurity #networksecurity #DataProtection #CyberSecurity #CloudCompliance #BusinessSecurity #ITInfrastructure #cloudcomputing #riskmanagement
09:33 AM - Jul 03, 2025 (UTC)
From Chaos to Control: Codebeamer for Risk Management & Change Impact Analysis
"Explore how Codebeamer transforms product development with advanced risk management and change impact analysis. Streamline your ALM processes for better control and compliance.
Read More : https://3hti.com/alm/from-...
Looking to upgrade, contact us: 609-303-3400"
#codebeamer #riskmanagement #ChangeImpactAnalysis #alm #RequirementsManagement #ComplianceManagement #Traceability #3hti
"Explore how Codebeamer transforms product development with advanced risk management and change impact analysis. Streamline your ALM processes for better control and compliance.
Read More : https://3hti.com/alm/from-...
Looking to upgrade, contact us: 609-303-3400"
#codebeamer #riskmanagement #ChangeImpactAnalysis #alm #RequirementsManagement #ComplianceManagement #Traceability #3hti
11:41 AM - Jun 25, 2025 (UTC)
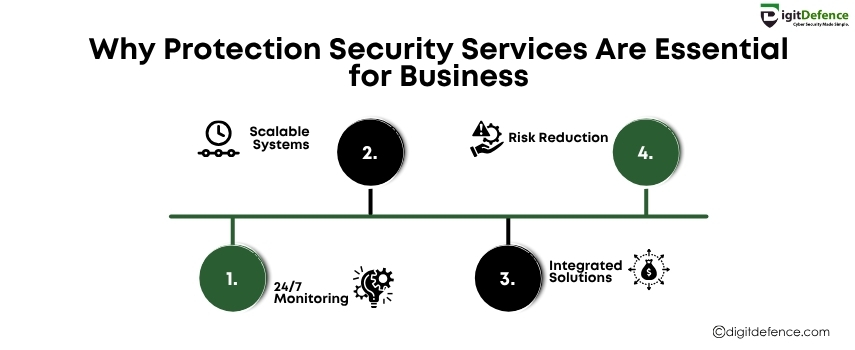
Why Protection Security Services are Essential For Business
| Digitdefence
Protection Security Services are vital for safeguarding business assets, data, and people from both physical and cyber threats. A proactive security approach reduces risk, ensures compliance, and builds customer trust.
#BusinessSecurity #ProtectionServices #CyberSecurity #riskmanagement #SecureBusiness
| Digitdefence
Protection Security Services are vital for safeguarding business assets, data, and people from both physical and cyber threats. A proactive security approach reduces risk, ensures compliance, and builds customer trust.
#BusinessSecurity #ProtectionServices #CyberSecurity #riskmanagement #SecureBusiness
09:10 AM - Jun 09, 2025 (UTC)
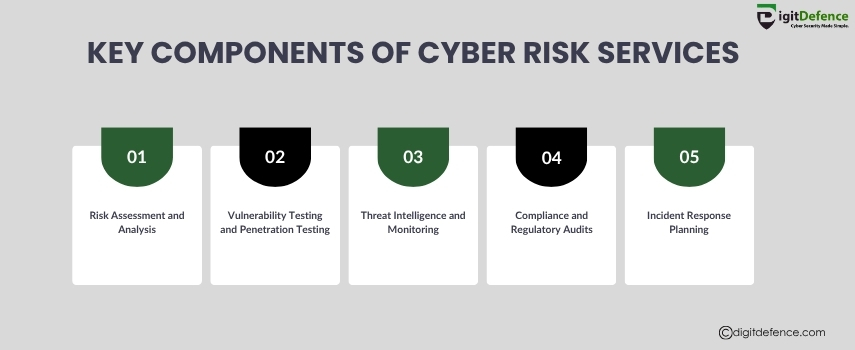
Key Components of Cyber Risk Services | Digitdefence
Understand the key components of cyber risk services — including threat assessment, vulnerability management, compliance support, and incident response. Strengthen your cybersecurity posture with a structured approach.
#CyberRisk #Cybersecurityservices #riskmanagement #ThreatAssessment #VulnerabilityManagement #ComplianceSupport #IncidentResponse #ITSecurity
Understand the key components of cyber risk services — including threat assessment, vulnerability management, compliance support, and incident response. Strengthen your cybersecurity posture with a structured approach.
#CyberRisk #Cybersecurityservices #riskmanagement #ThreatAssessment #VulnerabilityManagement #ComplianceSupport #IncidentResponse #ITSecurity
01:00 PM - Jul 02, 2025 (UTC)
How to Choose the Right Web App Pentesting Provider | Digitdefence
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
Selecting the right web app pentesting provider ensures your applications are thoroughly tested for vulnerabilities, protecting your business from cyber threats. Choose experts with proven experience and clear reporting.
#WebAppPentesting #CyberSecurity #pentesting #appsecurity #VulnerabilityAssessment #ThreatDetection #securitytesting #CyberProtection #riskmanagement #datasecurity
09:51 AM - Jun 27, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
Why Network Pen Testing Is Essential | Digitdefence
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
10:55 AM - Jun 12, 2025 (UTC)