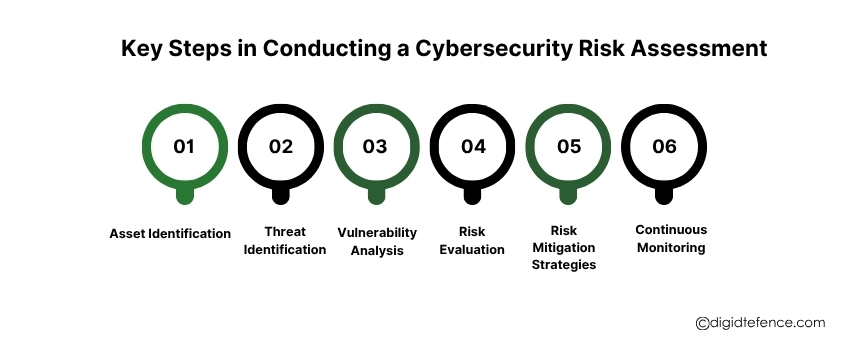
Key Steps in Conducting a Cybersecurity Risk Assessment | Digitdefence
Conducting a cybersecurity risk assessment helps identify vulnerabilities, evaluate threats, and prioritize actions to protect your business data and systems. It's the first step toward building a strong security posture
#CyberSecurity #RiskAssessment #DataProtection #SecurityAudit #CyberThreats #BusinessSecurity #ITRiskManagement #VulnerabilityScan #infosec #Compliance
Conducting a cybersecurity risk assessment helps identify vulnerabilities, evaluate threats, and prioritize actions to protect your business data and systems. It's the first step toward building a strong security posture
#CyberSecurity #RiskAssessment #DataProtection #SecurityAudit #CyberThreats #BusinessSecurity #ITRiskManagement #VulnerabilityScan #infosec #Compliance
09:20 AM - Jul 10, 2025 (UTC)
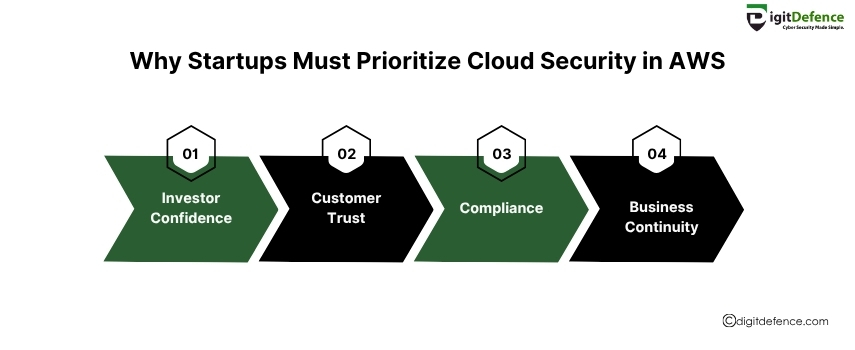
Why Startups Must Prioritize Cloud Security In AWS | Digitdefence
Startups often scale fast, but overlooking cloud security in AWS can lead to major data risks. Protecting workloads from day one ensures long-term success.
#cloudsecurity #AWSStartups #CyberSecurity #DataProtection #StartupGrowth #SecureCloud #CloudCompliance #DevSecOps #TechSecurity #awscloud
Startups often scale fast, but overlooking cloud security in AWS can lead to major data risks. Protecting workloads from day one ensures long-term success.
#cloudsecurity #AWSStartups #CyberSecurity #DataProtection #StartupGrowth #SecureCloud #CloudCompliance #DevSecOps #TechSecurity #awscloud
09:05 AM - Jul 10, 2025 (UTC)
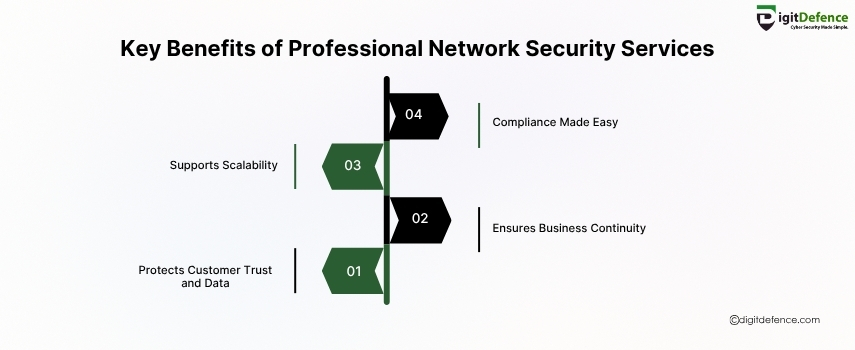
Key Benefits of Professional Network Security Services
Professional network security services help small businesses prevent data breaches, ensure system uptime, and build customer trust. They offer 24/7 monitoring, threat detection, and peace of mind.
#networksecurity #Cybersecurityservices #SmallBusinessIT #DataProtection #SecureNetwork #BusinessSecurity #ThreatDetection #ITSupport #CyberResilience #SMBSecurity
Professional network security services help small businesses prevent data breaches, ensure system uptime, and build customer trust. They offer 24/7 monitoring, threat detection, and peace of mind.
#networksecurity #Cybersecurityservices #SmallBusinessIT #DataProtection #SecureNetwork #BusinessSecurity #ThreatDetection #ITSupport #CyberResilience #SMBSecurity
09:24 AM - Jul 09, 2025 (UTC)
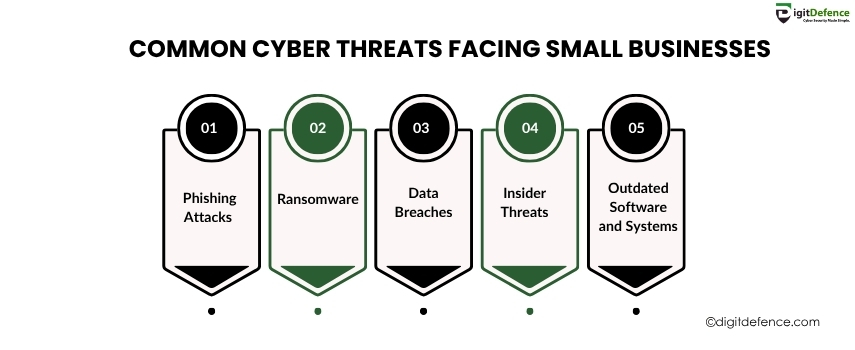
Common Cyber Threats Facing Small Businesses | Digitdefence
Small businesses are frequent targets of cyber threats like phishing, ransomware, and data breaches due to limited security measures and awareness. Understanding these risks is the first step toward protection.
#CyberThreats #SmallBusinessSecurity #PhishingScams #Ransomware #networksecurity #CyberProtection #DataBreach #CyberAwareness #BusinessSafety #CyberRiskManagement
Small businesses are frequent targets of cyber threats like phishing, ransomware, and data breaches due to limited security measures and awareness. Understanding these risks is the first step toward protection.
#CyberThreats #SmallBusinessSecurity #PhishingScams #Ransomware #networksecurity #CyberProtection #DataBreach #CyberAwareness #BusinessSafety #CyberRiskManagement
09:16 AM - Jul 09, 2025 (UTC)
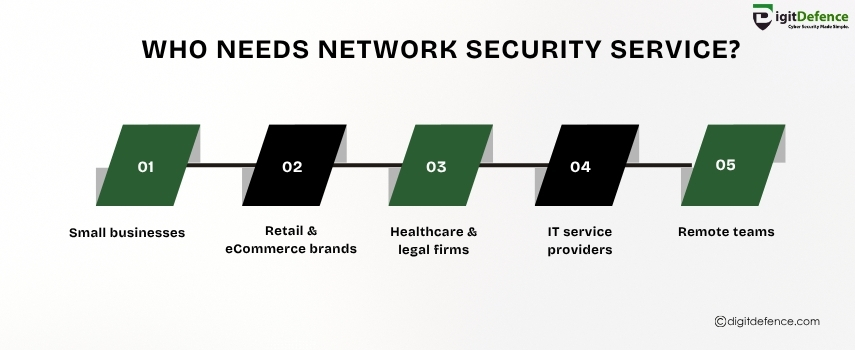
Who Needs Network Security Service | Digitdefence
Any business that relies on internet-connected systems, stores sensitive data, or supports remote teams needs network security. From startups to enterprises, securing your network is critical to protect against cyber threats.
#networksecurity #CyberSafety #BusinessSecurity #ITProtection #SecureYourNetwork
Any business that relies on internet-connected systems, stores sensitive data, or supports remote teams needs network security. From startups to enterprises, securing your network is critical to protect against cyber threats.
#networksecurity #CyberSafety #BusinessSecurity #ITProtection #SecureYourNetwork
09:41 AM - Jul 08, 2025 (UTC)
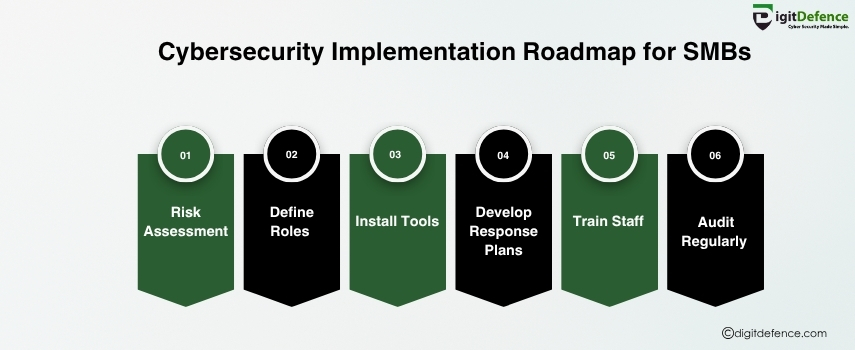
Cybersecurity Implementation Roadmap for SMBs | Digitdefence
Small and mid-sized businesses are top targets for cyber threats. This roadmap helps SMBs build a strong cybersecurity foundation with step-by-step actions to protect data, systems, and customer trust.
#CybersecurityForSMBs #SMBSecurity #CyberProtection #datasecurity #ITSecurityPlan
Small and mid-sized businesses are top targets for cyber threats. This roadmap helps SMBs build a strong cybersecurity foundation with step-by-step actions to protect data, systems, and customer trust.
#CybersecurityForSMBs #SMBSecurity #CyberProtection #datasecurity #ITSecurityPlan
09:31 AM - Jul 08, 2025 (UTC)
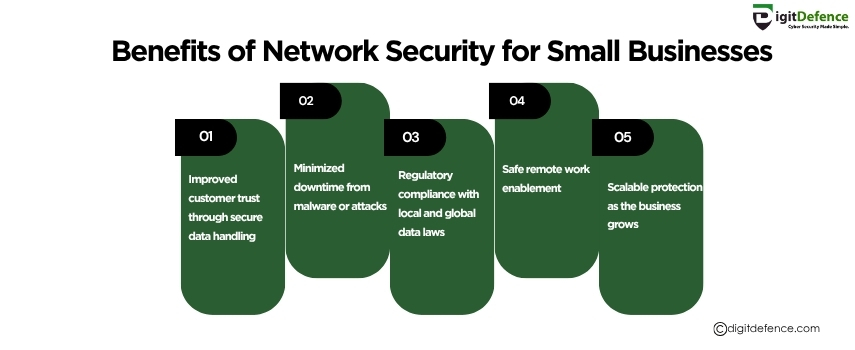
Benefits of Network Security For Small Businesses | Digitdefence
Network security safeguards small businesses from cyber threats, data breaches, and unauthorized access. It ensures smooth operations, protects customer trust, and supports compliance with industry standards.
#networksecurity #SmallBusinessSecurity #CyberProtection #DataSafety #SMBSecurity #BusinessContinuity #SecureNetwork #ITSecurity #DigitalProtection #CyberResilience
Network security safeguards small businesses from cyber threats, data breaches, and unauthorized access. It ensures smooth operations, protects customer trust, and supports compliance with industry standards.
#networksecurity #SmallBusinessSecurity #CyberProtection #DataSafety #SMBSecurity #BusinessContinuity #SecureNetwork #ITSecurity #DigitalProtection #CyberResilience
10:08 AM - Jul 07, 2025 (UTC)
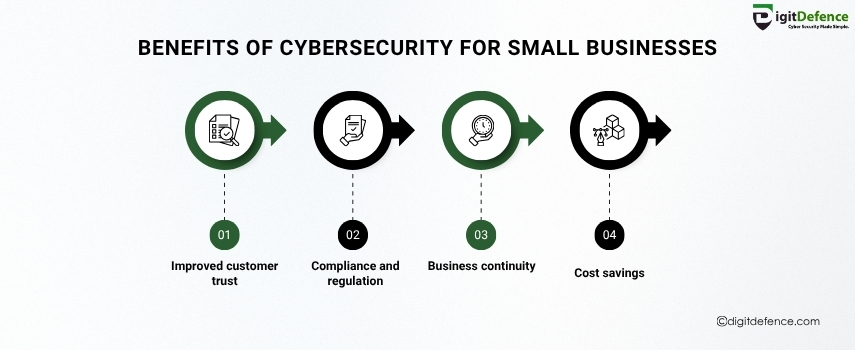
Benefits of Cybersecurity for Small Businesses | Digitdefence
Protect your small business from data breaches, malware, and cyber threats with tailored cybersecurity solutions. Stay secure, compliant, and resilient—even without a big IT team.
#CybersecuritySolutions #SmallBusinessSecurity #DataProtection #CyberThreats #SMBSecurity #DigitalProtection #networksecurity #CyberResilience #OnlineSafety #BusinessSecurity
Protect your small business from data breaches, malware, and cyber threats with tailored cybersecurity solutions. Stay secure, compliant, and resilient—even without a big IT team.
#CybersecuritySolutions #SmallBusinessSecurity #DataProtection #CyberThreats #SMBSecurity #DigitalProtection #networksecurity #CyberResilience #OnlineSafety #BusinessSecurity
10:00 AM - Jul 07, 2025 (UTC)
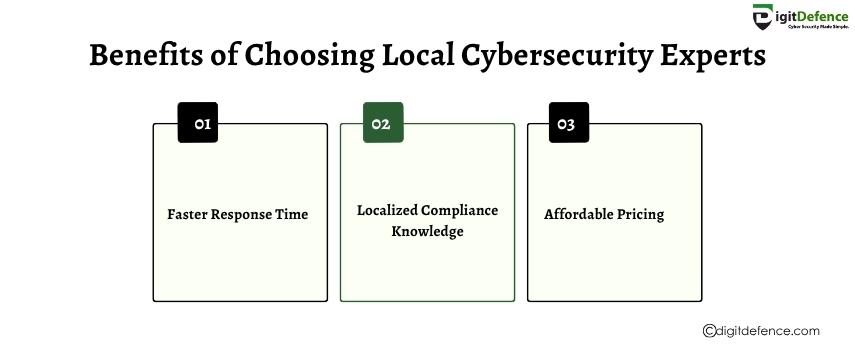
Benefits of Choosing Local Cybersecurity Experts | Digitdefence
Choosing local cybersecurity experts means faster response times, personalized support, and a deeper understanding of regional threats and compliance needs. Strengthen your defense with professionals who know your business environment.
#CyberSecurity #LocalExperts #ITSecuritySupport #DataProtection #riskmanagement #Compliance #CyberDefense #SmallBusinessSecurity #EndpointSecurity #NetworkProtection
Choosing local cybersecurity experts means faster response times, personalized support, and a deeper understanding of regional threats and compliance needs. Strengthen your defense with professionals who know your business environment.
#CyberSecurity #LocalExperts #ITSecuritySupport #DataProtection #riskmanagement #Compliance #CyberDefense #SmallBusinessSecurity #EndpointSecurity #NetworkProtection
09:47 AM - Jul 03, 2025 (UTC)
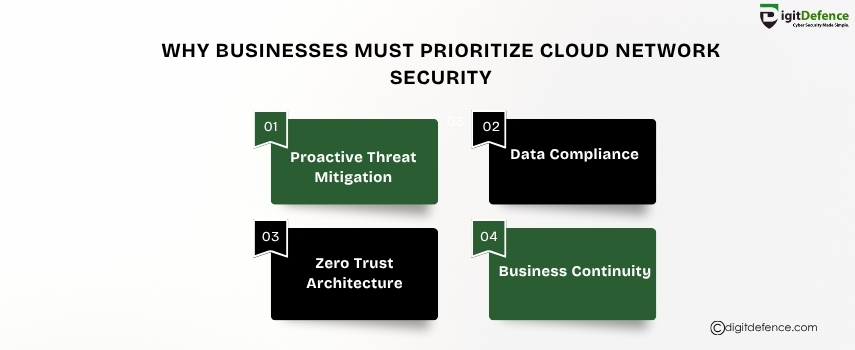
Why Businesses Must Prioritize Cloud Network Security
As businesses move to the cloud, securing network infrastructure becomes critical. Protect sensitive data, ensure uptime, and stay compliant with robust cloud security.
#cloudsecurity #networksecurity #DataProtection #CyberSecurity #CloudCompliance #BusinessSecurity #ITInfrastructure #cloudcomputing #riskmanagement
As businesses move to the cloud, securing network infrastructure becomes critical. Protect sensitive data, ensure uptime, and stay compliant with robust cloud security.
#cloudsecurity #networksecurity #DataProtection #CyberSecurity #CloudCompliance #BusinessSecurity #ITInfrastructure #cloudcomputing #riskmanagement
09:33 AM - Jul 03, 2025 (UTC)
Sponsored by
OWT
6 months ago