Key Benefits of Using Cyber Security Tools | Digitdefence
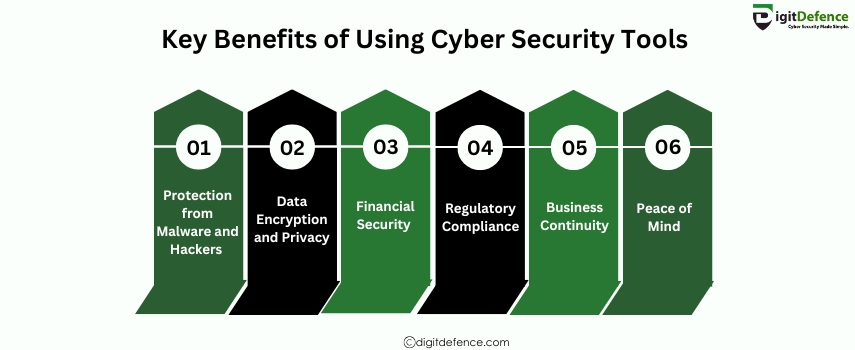
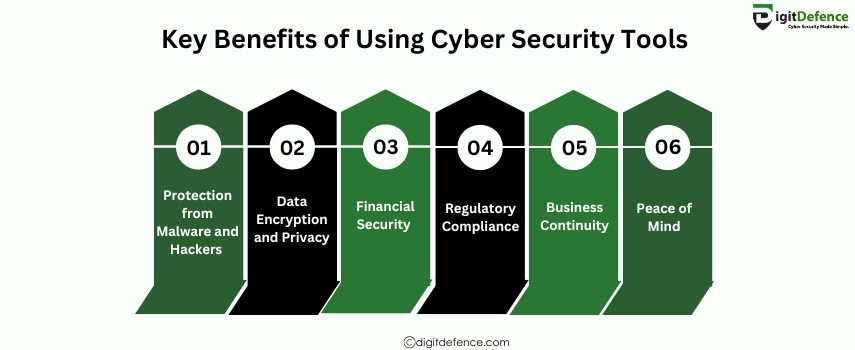
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:26 AM - Jun 13, 2025 (UTC)
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:28 AM - Jun 13, 2025 (UTC)
✔Cisco Issues Critical Security Patches for Vulnerabilities in Smart Licensing Utility and Identity Services Engine
Cisco has rolled out critical security updates addressing two significant vulnerabilities in its Cisco’s Smart Licensing Utility
For More Information
?Read - https://cybrpro.com/smart-...
and get insights
#Cisco #SecurityPatches #CriticalUpdates #SmartLicensing #IdentityServices #CyberSecurity #VulnerabilityManagement #technews #ITSecurity #NetworkSafety #CiscoSecurity #PatchManagement
Cisco has rolled out critical security updates addressing two significant vulnerabilities in its Cisco’s Smart Licensing Utility
For More Information
?Read - https://cybrpro.com/smart-...
and get insights
#Cisco #SecurityPatches #CriticalUpdates #SmartLicensing #IdentityServices #CyberSecurity #VulnerabilityManagement #technews #ITSecurity #NetworkSafety #CiscoSecurity #PatchManagement
06:22 AM - Sep 05, 2024 (UTC)
Key Components of Cyber Risk Services | Digitdefence
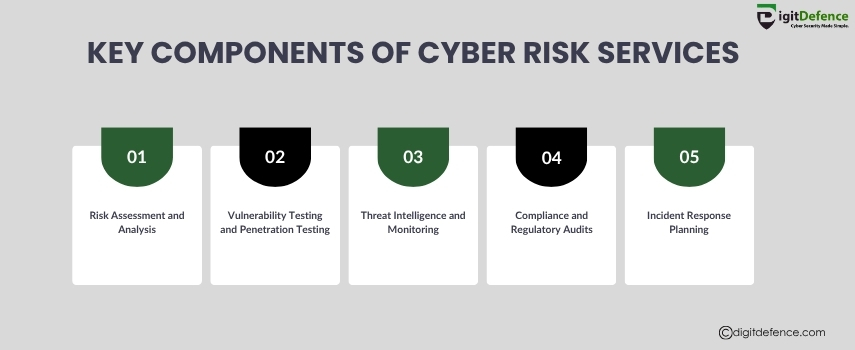
Understand the key components of cyber risk services — including threat assessment, vulnerability management, compliance support, and incident response. Strengthen your cybersecurity posture with a structured approach.
#CyberRisk #Cybersecurityservices #riskmanagement #ThreatAssessment #VulnerabilityManagement #ComplianceSupport #IncidentResponse #ITSecurity
Understand the key components of cyber risk services — including threat assessment, vulnerability management, compliance support, and incident response. Strengthen your cybersecurity posture with a structured approach.
#CyberRisk #Cybersecurityservices #riskmanagement #ThreatAssessment #VulnerabilityManagement #ComplianceSupport #IncidentResponse #ITSecurity
01:00 PM - Jul 02, 2025 (UTC)
Steps in the Risk Assessment Process | Digitdefence
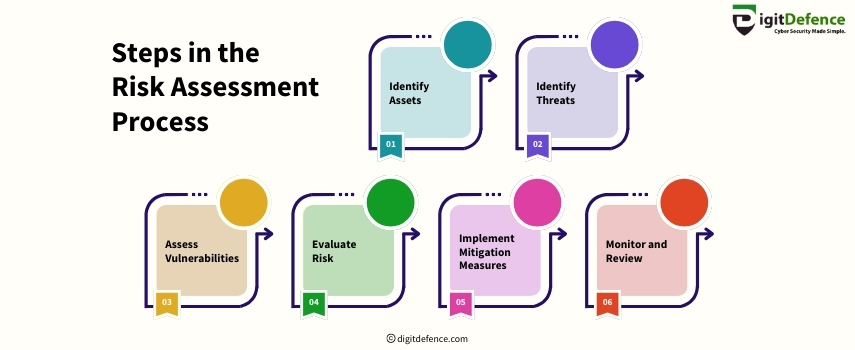
Risk assessment helps identify, evaluate, and mitigate potential risks to protect your business. It ensures that you can proactively address vulnerabilities and strengthen security.
#RiskAssessment #BusinessSecurity #riskmanagement #CyberSecurity #DataProtection #SecurityStrategy #VulnerabilityManagement
Risk assessment helps identify, evaluate, and mitigate potential risks to protect your business. It ensures that you can proactively address vulnerabilities and strengthen security.
#RiskAssessment #BusinessSecurity #riskmanagement #CyberSecurity #DataProtection #SecurityStrategy #VulnerabilityManagement
09:32 AM - May 20, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
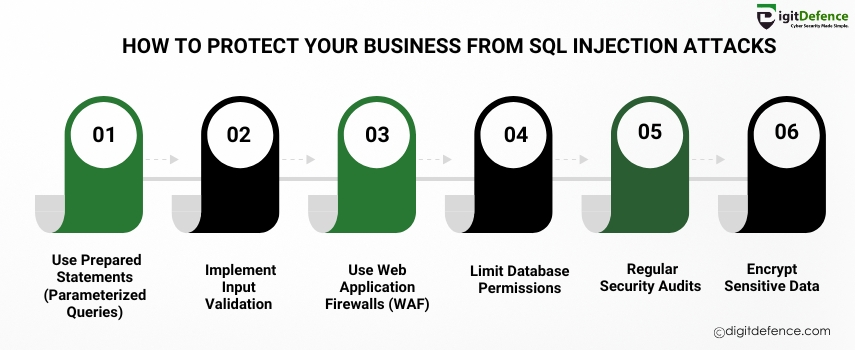
How to Protect Your Business From SQL Injection Attacks| Digitdefence
Protecting your business from SQL injection attacks requires implementing secure coding practices, such as using prepared statements and parameterized queries. Regularly updating your systems and conducting security audits can further reduce the risk of these attacks.
#SQLInjection #CyberSecurity #DataProtection #WebSecurity #SecureCoding #TechSecurity #HackingPrevention #VulnerabilityManagement #BusinessSecurity #CyberThreats
Protecting your business from SQL injection attacks requires implementing secure coding practices, such as using prepared statements and parameterized queries. Regularly updating your systems and conducting security audits can further reduce the risk of these attacks.
#SQLInjection #CyberSecurity #DataProtection #WebSecurity #SecureCoding #TechSecurity #HackingPrevention #VulnerabilityManagement #BusinessSecurity #CyberThreats
10:38 AM - Jun 12, 2025 (UTC)