Protect Yourself from POS Scammers with TfScammerslist
Point of Sale (POS) fraud is on the rise, targeting businesses of all sizes. TfScammerslist empowers you with the knowledge to recognize suspicious activity, identify scam patterns, and take preventative action. Stay informed about the latest tactics used by POS scammers and protect your business from financial and reputational harm. With our resources, you can make safer decisions and secure every transaction.
Additional info:- http://tfscammerslist.com/
#POSFraud #TfScammerslist #BusinessSecurity #POSScams #FraudAwareness #SecureTransactions #ScamPrevention
Point of Sale (POS) fraud is on the rise, targeting businesses of all sizes. TfScammerslist empowers you with the knowledge to recognize suspicious activity, identify scam patterns, and take preventative action. Stay informed about the latest tactics used by POS scammers and protect your business from financial and reputational harm. With our resources, you can make safer decisions and secure every transaction.
Additional info:- http://tfscammerslist.com/
#POSFraud #TfScammerslist #BusinessSecurity #POSScams #FraudAwareness #SecureTransactions #ScamPrevention
08:44 AM - Apr 10, 2025 (UTC)
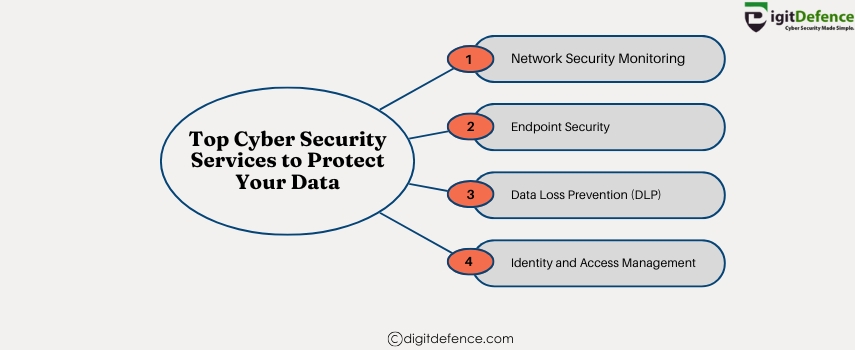
Top Cybersecurity Services to Protect Your Data | Digitdefence
Top cybersecurity services include threat detection, data encryption, and continuous monitoring to safeguard your sensitive information from cyberattacks. Investing in these solutions helps businesses maintain trust and ensure regulatory compliance.
#CyberSecurity #DataProtection #ThreatDetection #encryption #BusinessSecurity #infosec
Top cybersecurity services include threat detection, data encryption, and continuous monitoring to safeguard your sensitive information from cyberattacks. Investing in these solutions helps businesses maintain trust and ensure regulatory compliance.
#CyberSecurity #DataProtection #ThreatDetection #encryption #BusinessSecurity #infosec
09:43 AM - May 24, 2025 (UTC)
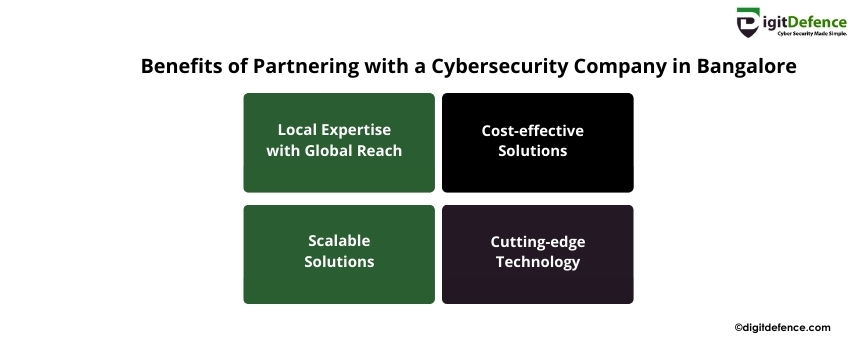
Benefits of Partnering with a Cybersecurity Company in Bangalore
Partnering with a cybersecurity company in Bangalore helps safeguard your business from evolving cyber threats, ensuring data security and compliance. Experts offer tailored solutions to protect critical assets.
#CyberSecurity #DataProtection #Bangalore #CyberDefense #BusinessSecurity #riskmanagement #TechSolutions #ITSecurity
Partnering with a cybersecurity company in Bangalore helps safeguard your business from evolving cyber threats, ensuring data security and compliance. Experts offer tailored solutions to protect critical assets.
#CyberSecurity #DataProtection #Bangalore #CyberDefense #BusinessSecurity #riskmanagement #TechSolutions #ITSecurity
09:32 AM - May 19, 2025 (UTC)
How To Implement Pentesting Network For Your Business | Digitdefence
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
Implementing pentesting network helps identify vulnerabilities before cybercriminals do, ensuring a secure business environment. Protect your assets with regular network testing.
#pentesting #networksecurity #CyberProtection #BusinessSecurity #EthicalHacking #CyberThreats #securitytesting
08:55 AM - May 10, 2025 (UTC)
How To Choose the Right Security Tools for Your Business
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
08:55 AM - Jun 02, 2025 (UTC)
Digital Signature Software Will Grow at Highest Pace Owing to Rising Demand for Document Digitalization
The increasing adoption of Digital Signature Software Market Demand across industries such as BFSI, government, IT & telecom, healthcare, and legal is driving the market growth.
Digital signature software offers an efficient and secure means of signing documents electronically. It allows users to sign documents digitally instead of physically signing paper documents. The digital signature acts as an electronic signature and carries the same legal validity as a handwritten signature.
Digital Signature Software Market
https://www.coherentmarket...
#DigitalSignatures ,#EbusinessSecurity,#BlockchainIntegration,#PaperlessTransformation, #DigitalWorkflows ,#CoherentMarketInsights.
The increasing adoption of Digital Signature Software Market Demand across industries such as BFSI, government, IT & telecom, healthcare, and legal is driving the market growth.
Digital signature software offers an efficient and secure means of signing documents electronically. It allows users to sign documents digitally instead of physically signing paper documents. The digital signature acts as an electronic signature and carries the same legal validity as a handwritten signature.
Digital Signature Software Market
https://www.coherentmarket...
#DigitalSignatures ,#EbusinessSecurity,#BlockchainIntegration,#PaperlessTransformation, #DigitalWorkflows ,#CoherentMarketInsights.
10:36 AM - May 13, 2025 (UTC)
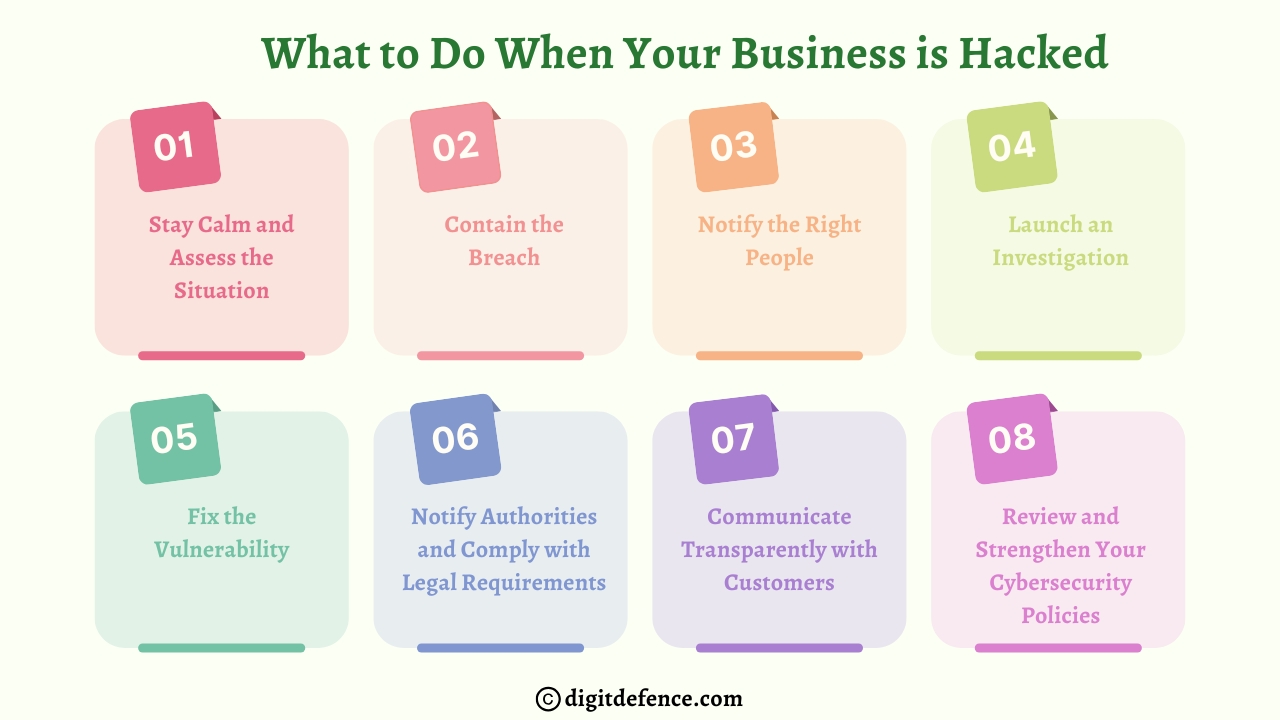
What to Do When Your Business is Hacked | Digitdefence
If your business is hacked, immediately isolate affected systems, notify your IT team, and change all passwords to prevent further damage. Then, report the breach to authorities and start a thorough investigation to identify the cause and secure your data.
#CyberAttack #BusinessSecurity #DataBreach #IncidentResponse
If your business is hacked, immediately isolate affected systems, notify your IT team, and change all passwords to prevent further damage. Then, report the breach to authorities and start a thorough investigation to identify the cause and secure your data.
#CyberAttack #BusinessSecurity #DataBreach #IncidentResponse
09:39 AM - Jun 03, 2025 (UTC)
Secure Your Space: The Ultimate CCTV Camera Installations Guide
Ensuring security is paramount for residential and commercial properties in the modern landscape. As worries about theft, vandalism, and unauthorised entry rise, CCTV camera installations have emerged as an essential measure for protecting assets. Nevertheless, meticulous planning and correct installation are most important to achieve optimal results.
Read more:https://tkelectric.com.au/...
#CCTVInstallation #homesecurity #BusinessSecurity #WirelessCCTV #SecurityCameras #SmartSurveillance #CCTVGuide #ResidentialSecurity #CommercialSecurity #SecureYourHome
Ensuring security is paramount for residential and commercial properties in the modern landscape. As worries about theft, vandalism, and unauthorised entry rise, CCTV camera installations have emerged as an essential measure for protecting assets. Nevertheless, meticulous planning and correct installation are most important to achieve optimal results.
Read more:https://tkelectric.com.au/...
#CCTVInstallation #homesecurity #BusinessSecurity #WirelessCCTV #SecurityCameras #SmartSurveillance #CCTVGuide #ResidentialSecurity #CommercialSecurity #SecureYourHome
02:31 PM - May 15, 2025 (UTC)
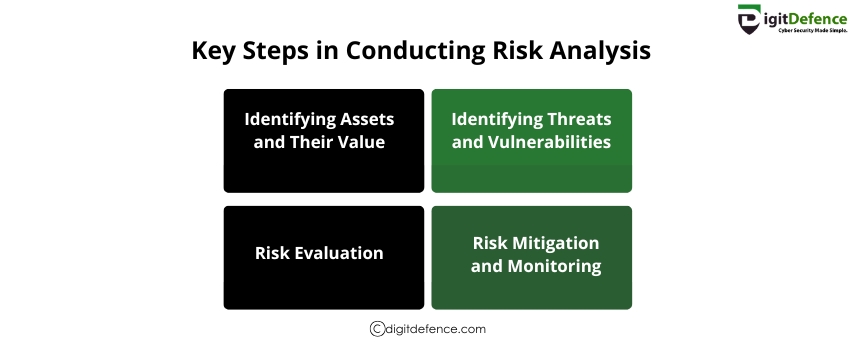
Key Steps in Conducting Risk Analysis | Digitdefence
Learn the essential steps in conducting risk analysis to identify vulnerabilities and strengthen your business security. Protect your assets with a proactive approach.
#RiskAnalysis #BusinessSecurity #CyberRisk #DataProtection #riskmanagement
Learn the essential steps in conducting risk analysis to identify vulnerabilities and strengthen your business security. Protect your assets with a proactive approach.
#RiskAnalysis #BusinessSecurity #CyberRisk #DataProtection #riskmanagement
09:33 AM - May 15, 2025 (UTC)
Sponsored by
OWT
4 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
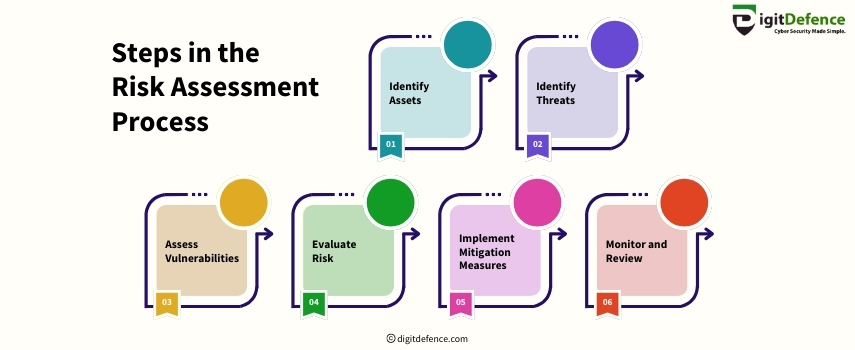
Steps in the Risk Assessment Process | Digitdefence
Risk assessment helps identify, evaluate, and mitigate potential risks to protect your business. It ensures that you can proactively address vulnerabilities and strengthen security.
#RiskAssessment #BusinessSecurity #riskmanagement #CyberSecurity #DataProtection #SecurityStrategy #VulnerabilityManagement
Risk assessment helps identify, evaluate, and mitigate potential risks to protect your business. It ensures that you can proactively address vulnerabilities and strengthen security.
#RiskAssessment #BusinessSecurity #riskmanagement #CyberSecurity #DataProtection #SecurityStrategy #VulnerabilityManagement
09:32 AM - May 20, 2025 (UTC)
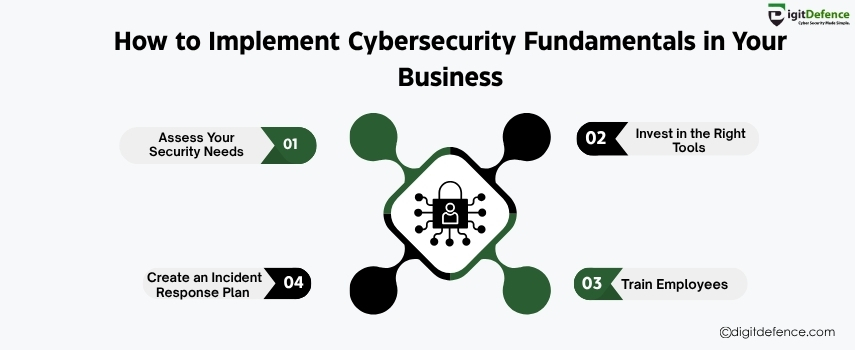
How to Implement Cybersecurity Fundamentals in Your Business | Digitdefence
Implementing cybersecurity fundamentals in your business is crucial to protect sensitive data and prevent cyber threats. By adopting strong password policies, regular software updates, and employee training, you can safeguard your business from potential attacks. Secure your business today and ensure long-term safety
#CyberSecurity #BusinessSecurity #DataProtection #DigitalSafety #SecureBusiness
Implementing cybersecurity fundamentals in your business is crucial to protect sensitive data and prevent cyber threats. By adopting strong password policies, regular software updates, and employee training, you can safeguard your business from potential attacks. Secure your business today and ensure long-term safety
#CyberSecurity #BusinessSecurity #DataProtection #DigitalSafety #SecureBusiness
09:11 AM - May 14, 2025 (UTC)
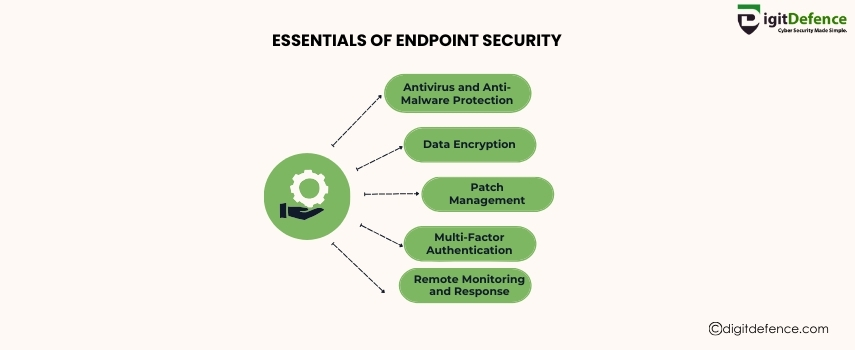
Essentials of Endpoint Security | Digitdefence
Endpoint security is crucial for protecting your business from cyber threats by securing devices like laptops, smartphones, and servers. Safeguard your endpoints to prevent unauthorized access and data breaches.
#EndpointSecurity #CyberSecurity #DataProtection #BusinessSecurity #ThreatPrevention #networksecurity #DataBreachPrevention
Endpoint security is crucial for protecting your business from cyber threats by securing devices like laptops, smartphones, and servers. Safeguard your endpoints to prevent unauthorized access and data breaches.
#EndpointSecurity #CyberSecurity #DataProtection #BusinessSecurity #ThreatPrevention #networksecurity #DataBreachPrevention
09:08 AM - May 10, 2025 (UTC)
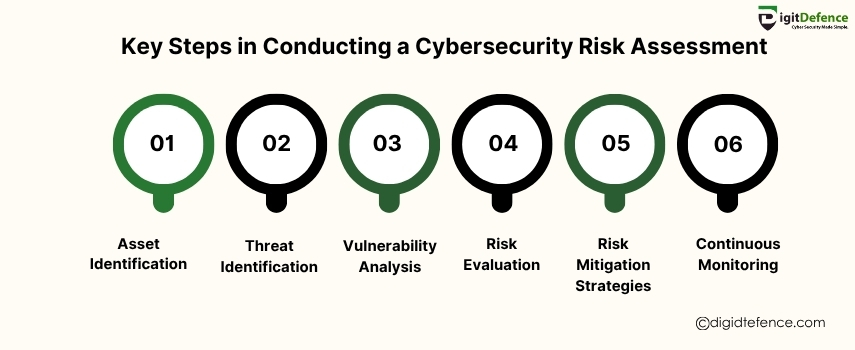
Key Steps in Conducting a Cybersecurity Risk Assessment
Conducting a cybersecurity risk assessment involves identifying potential threats and vulnerabilities to your business’s digital assets, then prioritizing risks to implement effective security measures. It’s crucial for protecting sensitive data and ensuring business continuity.
#CyberSecurity #RiskAssessment #DataProtection #BusinessSecurity
Conducting a cybersecurity risk assessment involves identifying potential threats and vulnerabilities to your business’s digital assets, then prioritizing risks to implement effective security measures. It’s crucial for protecting sensitive data and ensuring business continuity.
#CyberSecurity #RiskAssessment #DataProtection #BusinessSecurity
09:29 AM - Jun 03, 2025 (UTC)
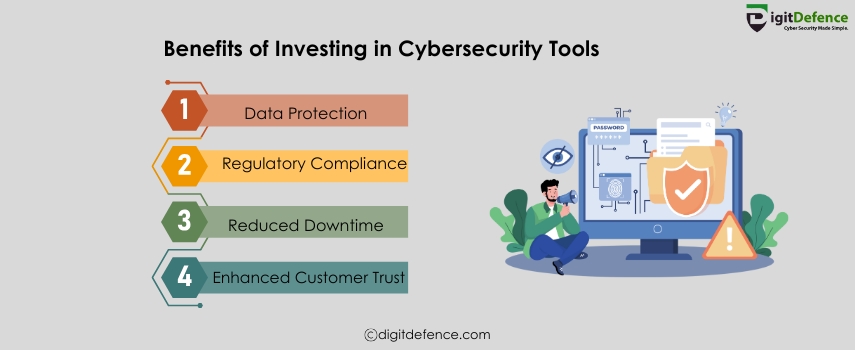
Benefits of Investing In Cybersecurity Tools | Digitdefence
Investing in cybersecurity tools is essential for protecting your business from data breaches, malware, and cyberattacks. These tools help secure sensitive information, ensure compliance with regulations, and maintain customer trust, ultimately reducing the risk of costly incidents. Safeguard your business’s future today.
#CyberSecurity #BusinessSecurity #DataProtection #CyberDefense #SecureYourBusiness
Investing in cybersecurity tools is essential for protecting your business from data breaches, malware, and cyberattacks. These tools help secure sensitive information, ensure compliance with regulations, and maintain customer trust, ultimately reducing the risk of costly incidents. Safeguard your business’s future today.
#CyberSecurity #BusinessSecurity #DataProtection #CyberDefense #SecureYourBusiness
09:19 AM - May 14, 2025 (UTC)
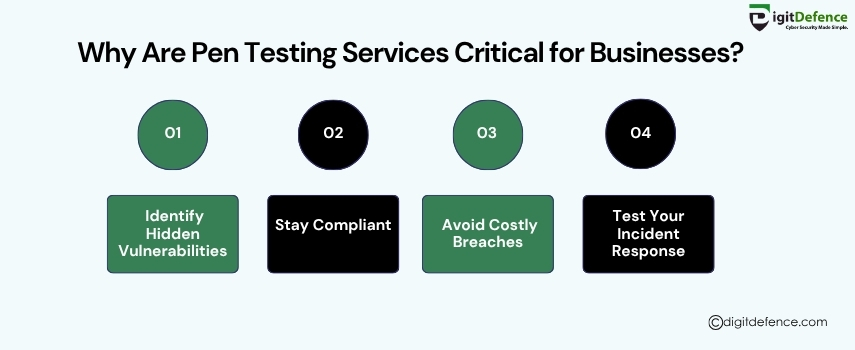
Why are Pen Testing Services Critical For Businesses
Pen Testing Services are essential for identifying hidden security gaps before attackers do, helping businesses prevent costly breaches and ensure compliance.
#pentesting #CyberSecurity #BusinessSecurity #VulnerabilityAssessment #DataProtection
Pen Testing Services are essential for identifying hidden security gaps before attackers do, helping businesses prevent costly breaches and ensure compliance.
#pentesting #CyberSecurity #BusinessSecurity #VulnerabilityAssessment #DataProtection
09:12 AM - Jun 05, 2025 (UTC)