The Importance of Securing Endpoint Devices | Digitdefence
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
09:51 AM - Jun 10, 2025 (UTC)
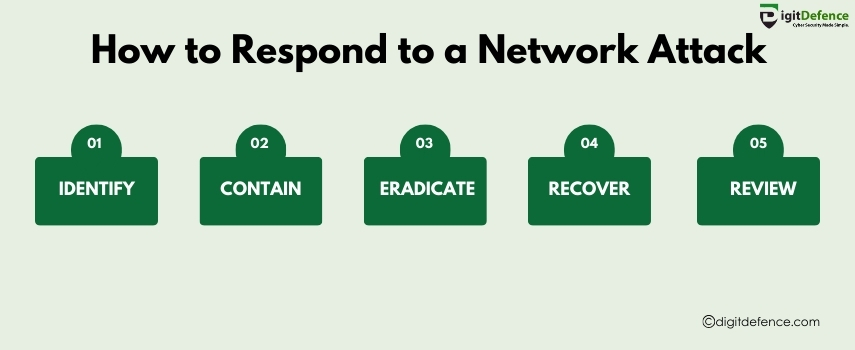
How To Respond To a Network Attack | Digitdefence
Learn the essential steps to quickly detect, contain, and recover from a network attack to minimize damage and secure your systems. Stay prepared with a solid incident response plan.
#CyberSecurity #NetworkAttack #IncidentResponse #DataProtection #ITSecurity
Learn the essential steps to quickly detect, contain, and recover from a network attack to minimize damage and secure your systems. Stay prepared with a solid incident response plan.
#CyberSecurity #NetworkAttack #IncidentResponse #DataProtection #ITSecurity
09:27 AM - May 22, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
How To Implement Effective Security Testing For Your Business
Implementing effective security testing helps safeguard your business from cyber threats and ensures data protection. Stay ahead with proactive security measures!
#securitytesting #CyberSecurity #BusinessProtection #riskmanagement #datasecurity #PenetrationTesting #ITSecurity
Implementing effective security testing helps safeguard your business from cyber threats and ensures data protection. Stay ahead with proactive security measures!
#securitytesting #CyberSecurity #BusinessProtection #riskmanagement #datasecurity #PenetrationTesting #ITSecurity
09:24 AM - May 20, 2025 (UTC)
How to Manage Cloud Computing Risks Effectively | Digitdefence
To manage cloud computing risks effectively, organizations should implement strong security protocols, conduct regular audits, and ensure compliance with industry standards. Employee training and using trusted cloud providers also play a crucial role in minimizing threats.
#cloudsecurity #riskmanagement #CyberSecurity #cloudcomputing #DataProtection #ITSecurity
To manage cloud computing risks effectively, organizations should implement strong security protocols, conduct regular audits, and ensure compliance with industry standards. Employee training and using trusted cloud providers also play a crucial role in minimizing threats.
#cloudsecurity #riskmanagement #CyberSecurity #cloudcomputing #DataProtection #ITSecurity
09:26 AM - May 23, 2025 (UTC)
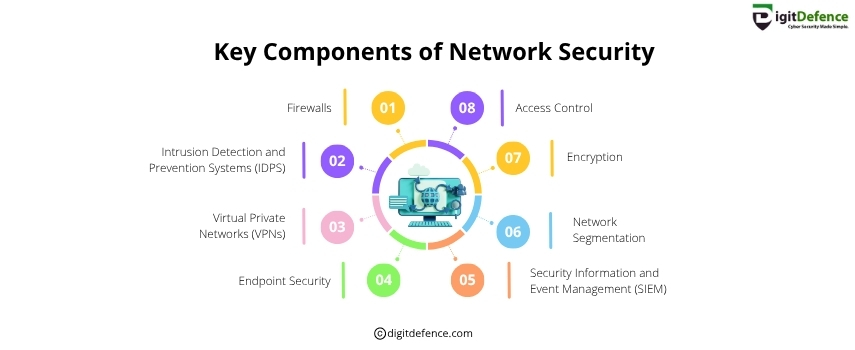
Key Components of Network Security | Digitdefence
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
09:16 AM - Jun 04, 2025 (UTC)
How To Choose the Right Security Tools for Your Business
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
08:55 AM - Jun 02, 2025 (UTC)
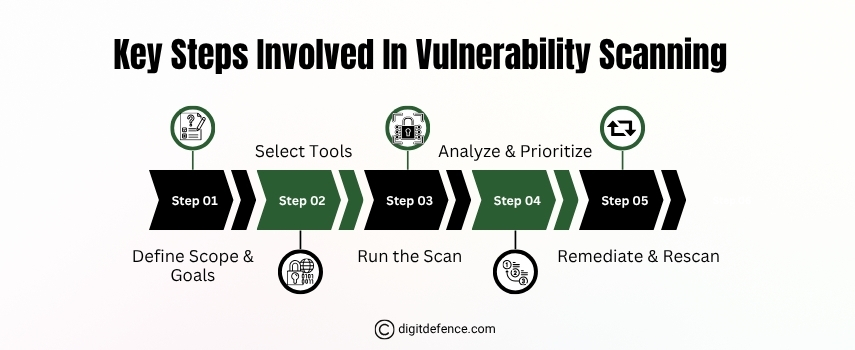
Key Steps Involved in Vulunerability Scanning | Digitdefence
Vulnerability scanning involves identifying security weaknesses in your system by scanning networks, servers, and applications for known threats. It helps businesses proactively fix issues before attackers exploit them.
#VulnerabilityScanning
#CyberSecurity
#networksecurity
#infosec
#SystemProtection
#RiskAssessment
#ITSecurity
Vulnerability scanning involves identifying security weaknesses in your system by scanning networks, servers, and applications for known threats. It helps businesses proactively fix issues before attackers exploit them.
#VulnerabilityScanning
#CyberSecurity
#networksecurity
#infosec
#SystemProtection
#RiskAssessment
#ITSecurity
06:06 AM - Jun 17, 2025 (UTC)
Top Web Application Firewall Companies | 2025 Market Analysis Report
https://www.renub.com/top-...
Discover the leading Web Application Firewall (WAF) companies protecting your business from cyber threats in 2025. Explore detailed market analysis, top global providers like Akamai and Cloudflare, and key WAF players in Bangladesh. Stay ahead in cybersecurity with this comprehensive report by Renub Research.
Web Application Firewall, WAF, Cybersecurity, Akamai, Cloudflare, Bangladesh WAF providers, Network Security, Data Protection, IT Security, Renub Research
#WebApplicationFirewall #WAF #CyberSecurity #networksecurity #DataProtection #Akamai #Cloudflare #Bangladesh #ITSecurity #RenubResearch
https://www.renub.com/top-...
Discover the leading Web Application Firewall (WAF) companies protecting your business from cyber threats in 2025. Explore detailed market analysis, top global providers like Akamai and Cloudflare, and key WAF players in Bangladesh. Stay ahead in cybersecurity with this comprehensive report by Renub Research.
Web Application Firewall, WAF, Cybersecurity, Akamai, Cloudflare, Bangladesh WAF providers, Network Security, Data Protection, IT Security, Renub Research
#WebApplicationFirewall #WAF #CyberSecurity #networksecurity #DataProtection #Akamai #Cloudflare #Bangladesh #ITSecurity #RenubResearch

Top Web Application Firewall Companies 2025 | WAF Leaders
Discover the top WAF companies protecting web apps against cyber threats with cutting-edge firewall solutions.
https://www.renub.com/top-web-application-firewall-companies-bd.php
07:44 AM - May 29, 2025 (UTC)
🔐💻 “Hackers Don’t Sleep, Why Should Your Cybersecurity?” 🚨🧠
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
12:51 PM - Jun 23, 2025 (UTC)
Why Network Pen Testing Is Essential | Digitdefence
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
Network penetration testing (pen testing) is essential to identify vulnerabilities in your network before cybercriminals can exploit them. It helps ensure that your systems are secure, compliant with regulations, and protected from unauthorized access.
#pentesting #networksecurity #CyberSecurity #VulnerabilityAssessment #DataProtection #EthicalHacking #CyberThreats #riskmanagement #securitytesting #ITSecurity
10:55 AM - Jun 12, 2025 (UTC)
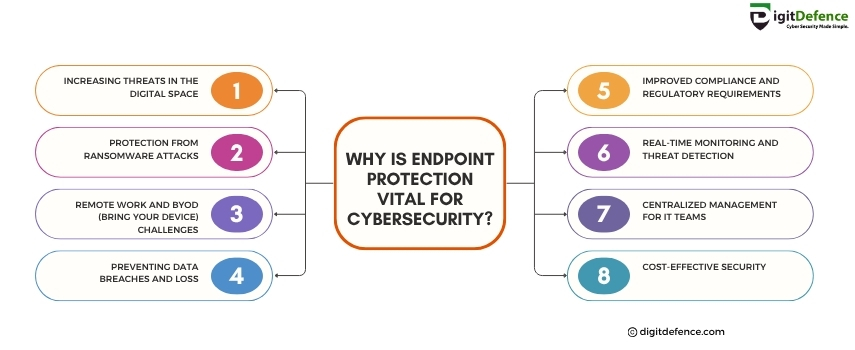
Why is Endpoint Protection Vital For CyberSecurity | Digitdefence
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
06:44 AM - Jun 13, 2025 (UTC)
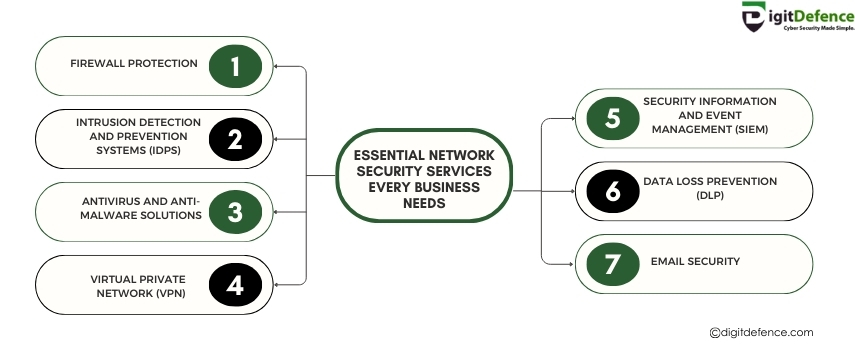
Essential Network Security Services Every Business Needs
Every business needs essential network security services to protect against cyber threats and safeguard sensitive data. Strong security measures ensure business continuity and build customer trust.
#networksecurity #CyberSecurity #DataProtection #BusinessSafety #SecurityServices #ITSecurity #riskmanagement
Every business needs essential network security services to protect against cyber threats and safeguard sensitive data. Strong security measures ensure business continuity and build customer trust.
#networksecurity #CyberSecurity #DataProtection #BusinessSafety #SecurityServices #ITSecurity #riskmanagement
09:55 AM - May 21, 2025 (UTC)
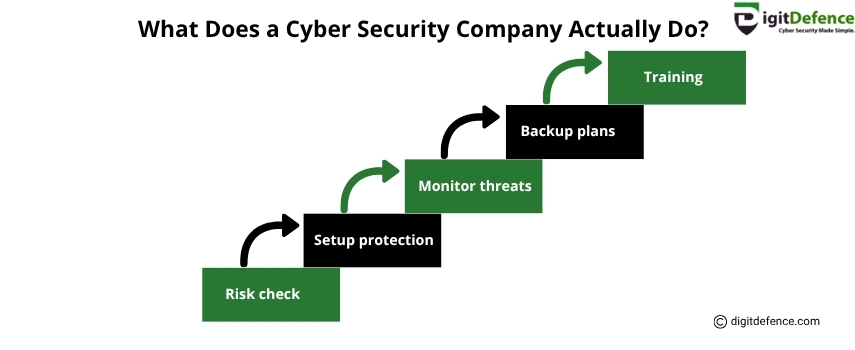
What Does a Cyber Security Company Do | Digitdefence
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
A cyber security company protects businesses from online threats by securing networks, systems, and data. They provide services like threat detection, risk assessment, and incident response to keep digital assets safe.
#CyberSecurity #DataProtection #cybersecuritycompany #infosec #ThreatDetection #networksecurity #CyberSafety #riskmanagement #DigitalSecurity #ITSecurity
06:33 AM - Jun 25, 2025 (UTC)
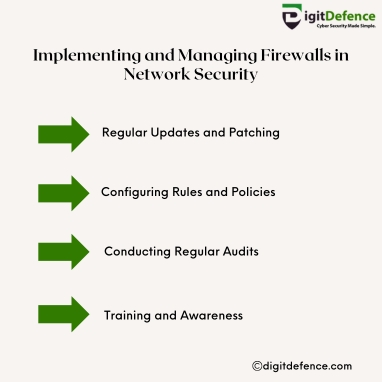
Implementing and Managing Firewalls in Network Security | Digitdefence
Implementing and managing firewalls is crucial for controlling network traffic and blocking unauthorized access. They serve as a vital shield, protecting your business from cyber threats.
#FirewallSecurity #NetworkProtection #CyberSecurity #ITSecurity #DataSafety #networksecurity #BusinessProtection
Implementing and managing firewalls is crucial for controlling network traffic and blocking unauthorized access. They serve as a vital shield, protecting your business from cyber threats.
#FirewallSecurity #NetworkProtection #CyberSecurity #ITSecurity #DataSafety #networksecurity #BusinessProtection
10:06 AM - May 21, 2025 (UTC)
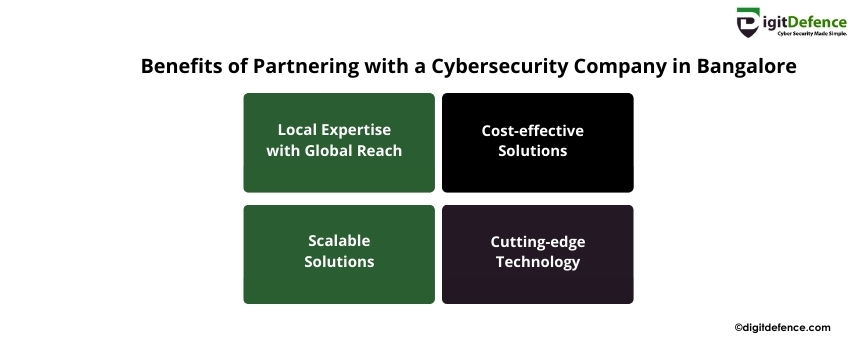
Benefits of Partnering with a Cybersecurity Company in Bangalore
Partnering with a cybersecurity company in Bangalore helps safeguard your business from evolving cyber threats, ensuring data security and compliance. Experts offer tailored solutions to protect critical assets.
#CyberSecurity #DataProtection #Bangalore #CyberDefense #BusinessSecurity #riskmanagement #TechSolutions #ITSecurity
Partnering with a cybersecurity company in Bangalore helps safeguard your business from evolving cyber threats, ensuring data security and compliance. Experts offer tailored solutions to protect critical assets.
#CyberSecurity #DataProtection #Bangalore #CyberDefense #BusinessSecurity #riskmanagement #TechSolutions #ITSecurity
09:32 AM - May 19, 2025 (UTC)