How Cybersecurity Companies Secure Your Business
Protect your business from cyber attacks with expert-driven, step-by-step security solutions.
From risk scans to ongoing monitoring, learn how cybersecurity companies keep your data safe.
Visit https://digitdefence.com/ to secure your business today.
Protect your business from cyber attacks with expert-driven, step-by-step security solutions.
From risk scans to ongoing monitoring, learn how cybersecurity companies keep your data safe.
Visit https://digitdefence.com/ to secure your business today.
08:30 AM - Jul 10, 2025 (UTC)
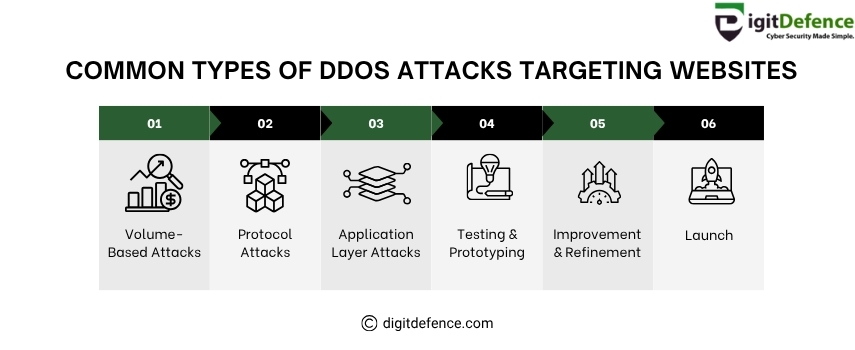
Common Types of DDoS Attacks Targeting Websites
Learn the top 6 DDoS attack types that can take your website offline.
From overwhelming traffic floods to protocol and application layer exploits, understand how attackers bring down sites and what to do next.
Stay ahead with powerful DDoS protection.
Visit: https://www.digitdefence.c... | Protect your website today
Learn the top 6 DDoS attack types that can take your website offline.
From overwhelming traffic floods to protocol and application layer exploits, understand how attackers bring down sites and what to do next.
Stay ahead with powerful DDoS protection.
Visit: https://www.digitdefence.c... | Protect your website today
10:03 AM - Jul 09, 2025 (UTC)
(E)
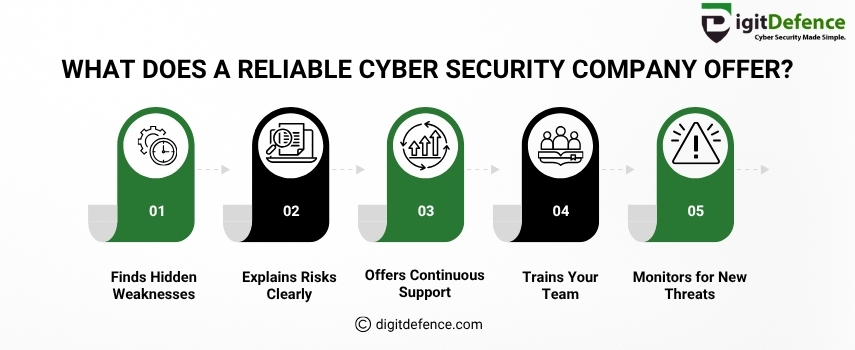
What Does a Reliable Cyber Security Company Offer?
A reliable cyber security company helps protect your business by finding weaknesses, offering support, and monitoring threats.
Stay secure, learn more at digitdefence.com
A reliable cyber security company helps protect your business by finding weaknesses, offering support, and monitoring threats.
Stay secure, learn more at digitdefence.com
09:16 AM - Jul 08, 2025 (UTC)
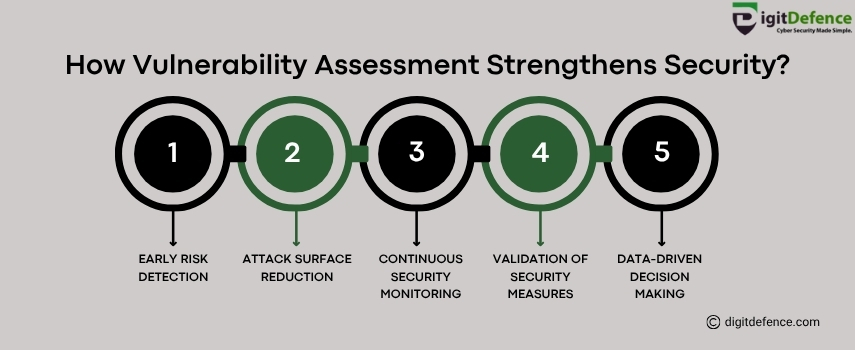
How Vulnerability Assessment Strengthens Security?
Strengthen your cyber defenses with comprehensive vulnerability assessments, detect risks early and make data-driven decisions. Stay one step ahead of threats with continuous monitoring and validation.
Ready to secure your digital assets? Visit digitdefence.com to learn more and get started today!
Strengthen your cyber defenses with comprehensive vulnerability assessments, detect risks early and make data-driven decisions. Stay one step ahead of threats with continuous monitoring and validation.
Ready to secure your digital assets? Visit digitdefence.com to learn more and get started today!
09:46 AM - Jul 07, 2025 (UTC)
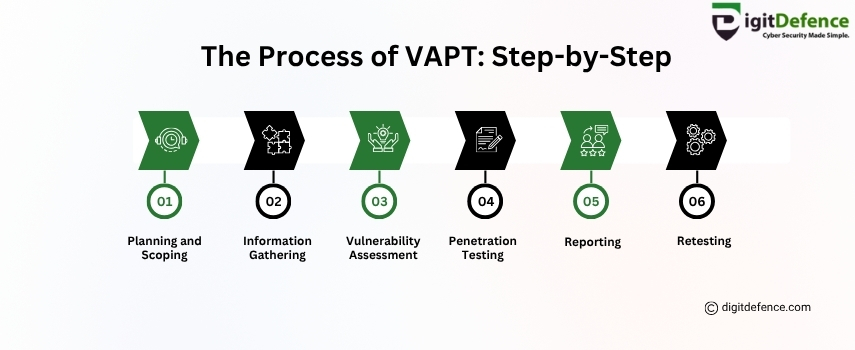
The Process of VAPT: Step-by-Step
Learn how Planning, Vulnerability Assessment, and Penetration Testing work together to protect your systems.
Secure your business now at www.digitdefence.com — Get your VAPT audit today!
Learn how Planning, Vulnerability Assessment, and Penetration Testing work together to protect your systems.
Secure your business now at www.digitdefence.com — Get your VAPT audit today!
09:31 AM - Jul 04, 2025 (UTC)
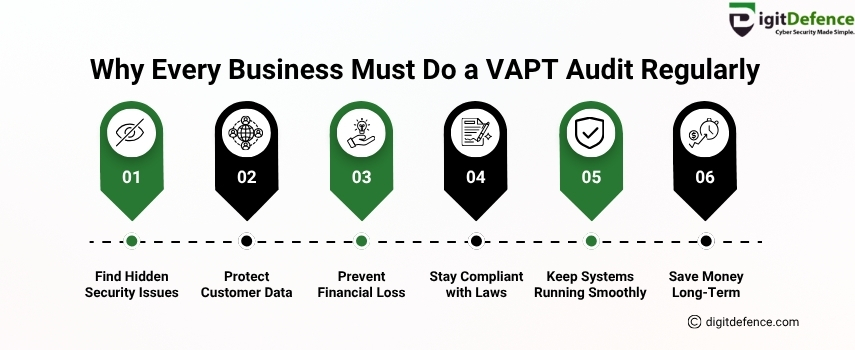
Why Every Business Must Do a VAPT Audit Regularly
Protect your business with regular VAPT audit services to find security issues, avoid data loss, and stay safe. VAPT helps you follow cyber laws and save money by preventing future attacks.
Visit www.digitdefence.com to secure your systems today.
Protect your business with regular VAPT audit services to find security issues, avoid data loss, and stay safe. VAPT helps you follow cyber laws and save money by preventing future attacks.
Visit www.digitdefence.com to secure your systems today.
10:30 AM - Jul 03, 2025 (UTC)
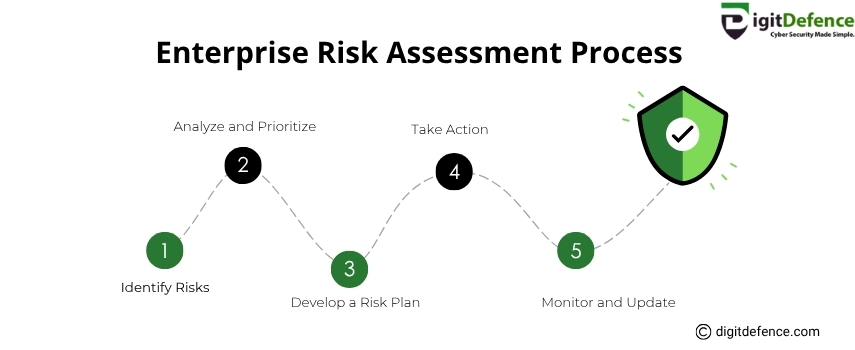
Enterprise Risk Assessment Process
Master your enterprise risk assessment with this simple 5-step strategy to protect your business from cyber threats.
Identify, prioritize, and act on risks effectively, then monitor and update regularly for long-term security.
Visit digitdefence.com to learn more
#CyberSecurity #EnterpriseRiskAssessment #Digitdefence
Master your enterprise risk assessment with this simple 5-step strategy to protect your business from cyber threats.
Identify, prioritize, and act on risks effectively, then monitor and update regularly for long-term security.
Visit digitdefence.com to learn more
#CyberSecurity #EnterpriseRiskAssessment #Digitdefence
09:40 AM - Jul 02, 2025 (UTC)
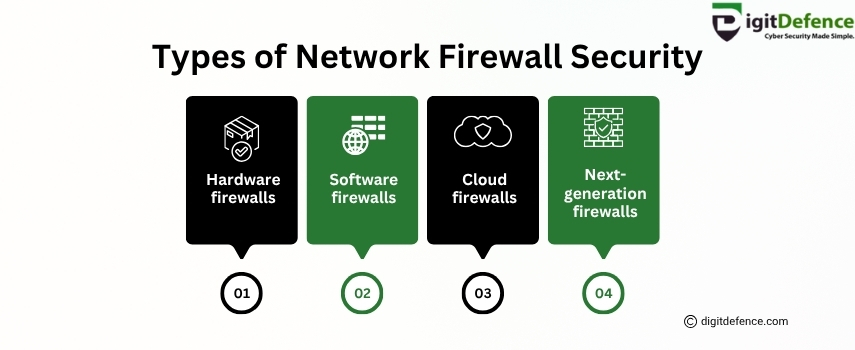
Types of Network Firewall Security
Protect Your Business with the Right Network Firewall!
Explore 4 powerful types of firewall security, Hardware, Software, Cloud & Next-Gen, to block threats and keep your data safe.
Learn more at www.digitdefence.com
Secure Your Network Today!
#CyberSecurity #Cybersecurityservices
Protect Your Business with the Right Network Firewall!
Explore 4 powerful types of firewall security, Hardware, Software, Cloud & Next-Gen, to block threats and keep your data safe.
Learn more at www.digitdefence.com
Secure Your Network Today!
#CyberSecurity #Cybersecurityservices
09:11 AM - Jul 01, 2025 (UTC)
Steps Involved in Web App Pentesting
Web app pentesting includes setting a clear goal, scanning for issues, testing manually, and fixing the problems. These steps help make the application safer and more secure.
Learn more at, www.digitdefence.com
Web app pentesting includes setting a clear goal, scanning for issues, testing manually, and fixing the problems. These steps help make the application safer and more secure.
Learn more at, www.digitdefence.com
09:40 AM - Jun 30, 2025 (UTC)
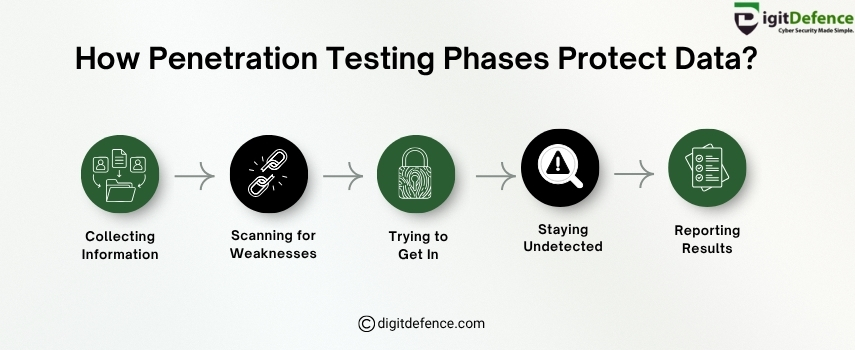
How Penetration Testing Phases Protect Data?
Penetration testing protects your data by following smart steps. It starts with collecting information, then scanning for weaknesses. Next, ethical hackers try to get in, stay hidden, and finally report the results. These phases help find and fix risks before hackers can use them.
Get your systems tested today.
Visit: www.digitdefence.com
#CyberSecurity #PenetrationTesting #pentesting #Digitdefence
Penetration testing protects your data by following smart steps. It starts with collecting information, then scanning for weaknesses. Next, ethical hackers try to get in, stay hidden, and finally report the results. These phases help find and fix risks before hackers can use them.
Get your systems tested today.
Visit: www.digitdefence.com
#CyberSecurity #PenetrationTesting #pentesting #Digitdefence
11:58 AM - Jun 27, 2025 (UTC)
Sponsored by
OWT
6 months ago