Discover the power of a hidden call recorder and hidden voice tracker for discreetly monitoring conversations. Record important calls and track voice activity seamlessly with these powerful tools for personal, business, and security purposes.
#HiddenCallRecorder #VoiceTracker #CallRecording #PhoneMonitoring #DiscreetRecording #AudioTracker #callmonitoring #PrivacyProtection #SecurityTools #PersonalSafety #BusinessEfficiency #TechSolutions #PhoneSpy #HiddenRecording
#HiddenCallRecorder #VoiceTracker #CallRecording #PhoneMonitoring #DiscreetRecording #AudioTracker #callmonitoring #PrivacyProtection #SecurityTools #PersonalSafety #BusinessEfficiency #TechSolutions #PhoneSpy #HiddenRecording

Unlock the Power of Hidden Call Recorder and Voice Tracker for Seamless Monitoring | by One Spy | Feb, 2025 | Medium
In today’s fast-paced world, keeping track of important conversations is crucial, whether it’s for personal safety, business purposes, or simply staying connected. That’s where a hidden call recorder…
https://medium.com/@onespyapp04/unlock-the-power-of-hidden-call-recorder-and-voice-tracker-for-seamless-monitoring-0933ac437d64
09:21 AM - Feb 12, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
How To Choose the Right Security Tools for Your Business
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
08:55 AM - Jun 02, 2025 (UTC)
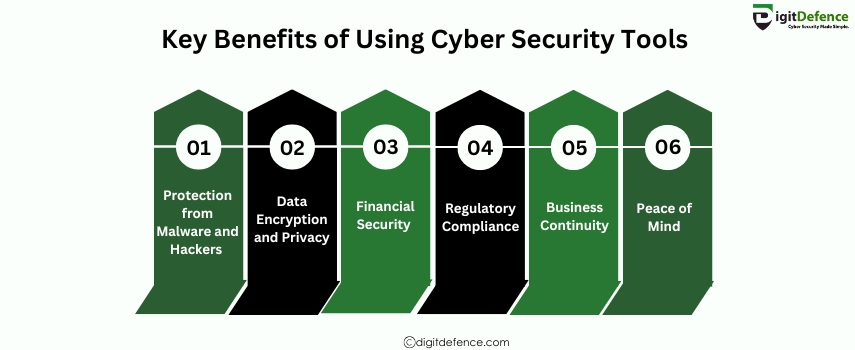
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:26 AM - Jun 13, 2025 (UTC)
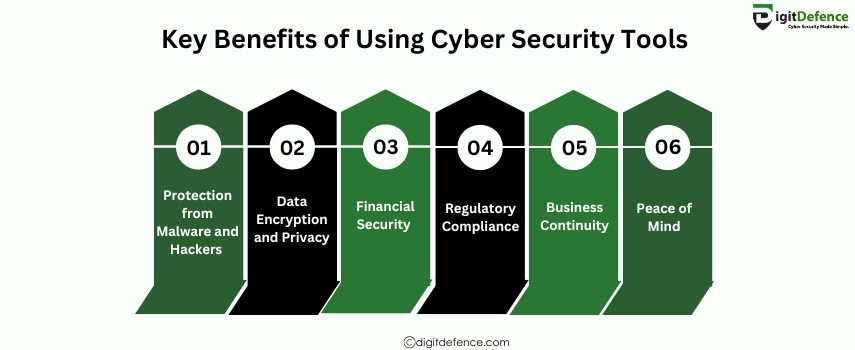
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:28 AM - Jun 13, 2025 (UTC)