How a Cybersecurity Solutions Company Protects Against Ransomware Attacks
https://cyberdefenderinsig...
A Cybersecurity Solutions Company combats ransomware through continuous threat monitoring, employee training, secure data backups, and robust endpoint protection. Read this blog to discover how these strategies, including AI-driven detection and incident response planning, fortify defenses against evolving cyber threats.
#CybersecuritySolutionsCompany #CyberDefense #EndpointSecurity #cybersecuritysolutionproviders
https://cyberdefenderinsig...
A Cybersecurity Solutions Company combats ransomware through continuous threat monitoring, employee training, secure data backups, and robust endpoint protection. Read this blog to discover how these strategies, including AI-driven detection and incident response planning, fortify defenses against evolving cyber threats.
#CybersecuritySolutionsCompany #CyberDefense #EndpointSecurity #cybersecuritysolutionproviders
07:46 AM - May 26, 2025 (UTC)
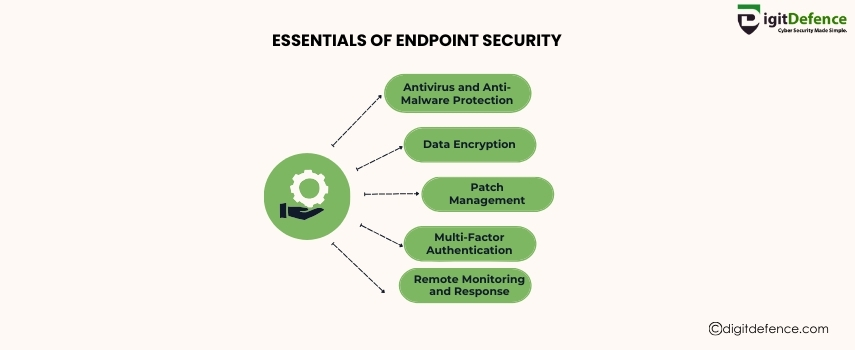
Essentials of Endpoint Security | Digitdefence
Endpoint security is crucial for protecting your business from cyber threats by securing devices like laptops, smartphones, and servers. Safeguard your endpoints to prevent unauthorized access and data breaches.
#EndpointSecurity #CyberSecurity #DataProtection #BusinessSecurity #ThreatPrevention #networksecurity #DataBreachPrevention
Endpoint security is crucial for protecting your business from cyber threats by securing devices like laptops, smartphones, and servers. Safeguard your endpoints to prevent unauthorized access and data breaches.
#EndpointSecurity #CyberSecurity #DataProtection #BusinessSecurity #ThreatPrevention #networksecurity #DataBreachPrevention
09:08 AM - May 10, 2025 (UTC)
Sponsored by
OWT
6 months ago
The Importance of Securing Endpoint Devices | Digitdefence
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
Endpoint devices, such as smartphones, laptops, and desktops, are often the entry points for cyberattacks. Securing these devices is critical to prevent unauthorized access, data breaches, and malware infections, safeguarding both personal and business information.
#EndpointSecurity #CyberSecurity #DataProtection #MalwarePrevention #SecureDevices #ITSecurity #BusinessSecurity #DigitalProtection #CyberThreats #DataBreachPrevention
09:51 AM - Jun 10, 2025 (UTC)
EDR vs XDR: Understanding the Key Differences and Choosing the Right Solution
https://app.box.com/s/3mqq...
Discover the core differences between EDR and XDR to strengthen your cybersecurity posture. From endpoint protection to extended threat detection, each solution offers unique advantages. Click here to learn which is right for your organization and improve your defense strategy today.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR
https://app.box.com/s/3mqq...
Discover the core differences between EDR and XDR to strengthen your cybersecurity posture. From endpoint protection to extended threat detection, each solution offers unique advantages. Click here to learn which is right for your organization and improve your defense strategy today.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR
06:03 PM - May 27, 2025 (UTC)
EDR vs XDR: Understanding the Differences and Choosing the Right Solution
https://www.seqrite.com/bl...
Navigate the complexities of cybersecurity with our deep dive into EDR vs XDR. Learn the core differences, functionalities, and how each solution contributes to your overall security posture. Read this blog to make an informed decision for robust threat detection and response.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR
https://www.seqrite.com/bl...
Navigate the complexities of cybersecurity with our deep dive into EDR vs XDR. Learn the core differences, functionalities, and how each solution contributes to your overall security posture. Read this blog to make an informed decision for robust threat detection and response.
#EDR #XDR #CyberSecurity #ThreatDetection #EndpointSecurity #ExtendedDetection #EDRandXDR

EDR vs XDR: Understand the Key Differences & Choose the Right Solution
Learn the critical differences between EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) aka EDR vs. XDR. Discover their features, benefits, and when to choose each for optimal cybersecurity.
https://www.seqrite.com/blog/edr-vs-xdr-differences-choosing-right-solution/
09:53 AM - Jun 10, 2025 (UTC)