The Business Impact of a Cyberattack | IIFIS
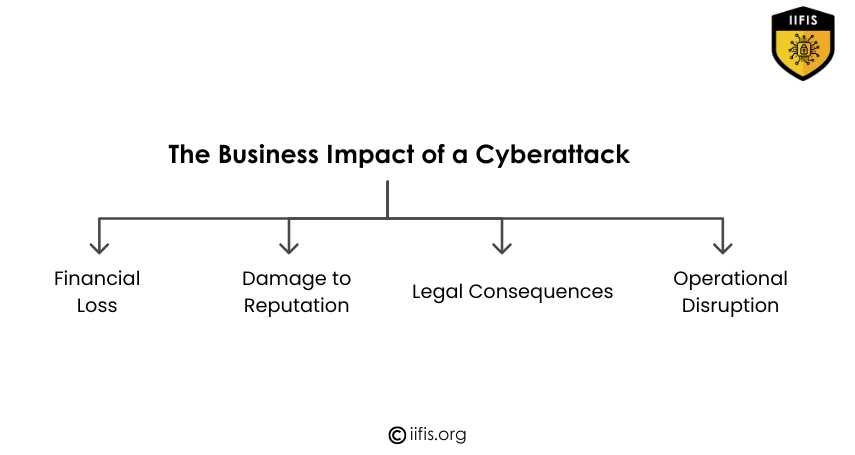
The main effects of a cyberattack on a company are depicted in this image. It illustrates four main outcomes: monetary loss, negative publicity, legal consequences, and business interruption. These consequences emphasize how crucial it is for businesses to have robust cybersecurity policies.
https://iifis.org/blog/wha...
The main effects of a cyberattack on a company are depicted in this image. It illustrates four main outcomes: monetary loss, negative publicity, legal consequences, and business interruption. These consequences emphasize how crucial it is for businesses to have robust cybersecurity policies.
https://iifis.org/blog/wha...
11:38 AM - Jun 21, 2025 (UTC)
(E)
What Happens During a Pentest | Digitdefence
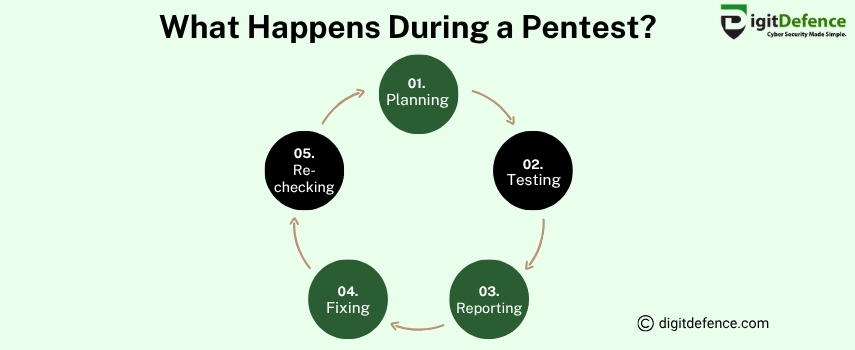
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
During a pentest, security experts simulate real cyberattacks to identify vulnerabilities in your web applications. They then provide detailed reports with recommendations to strengthen your defenses.
#pentesting #CyberSecurity #EthicalHacking #securitytesting #VulnerabilityAssessment #WebAppSecurity #RiskAssessment #infosec #CyberDefense #PenTestProcess
07:21 AM - Jun 26, 2025 (UTC)
External Network Penetration Testing Tools and Techniques
An organization's internet-facing assets, including websites, email servers, and firewalls, can have vulnerabilities that can be found and exploited through the use of external network penetration testing. In order to assess the ease with which an attacker could obtain unauthorised access, this test mimics actual cyberattacks from outside the company network. Finding flaws including improperly designed systems, out-of-date software, and subpar authentication procedures is its goal. The results assist organisations in adhering to industry norms and laws, enhancing their perimeter defences, and lowering their vulnerability to external attacks. For proactive cybersecurity management, regular testing is necessary. https://dev.to/secdesk/pro...
An organization's internet-facing assets, including websites, email servers, and firewalls, can have vulnerabilities that can be found and exploited through the use of external network penetration testing. In order to assess the ease with which an attacker could obtain unauthorised access, this test mimics actual cyberattacks from outside the company network. Finding flaws including improperly designed systems, out-of-date software, and subpar authentication procedures is its goal. The results assist organisations in adhering to industry norms and laws, enhancing their perimeter defences, and lowering their vulnerability to external attacks. For proactive cybersecurity management, regular testing is necessary. https://dev.to/secdesk/pro...
10:43 AM - Jun 18, 2025 (UTC)
Why Virus Ransomware is Dangerous | Digitdefence
Ransomware encrypts your data and demands payment for its release, causing severe business disruptions and financial loss. It can compromise sensitive information and damage your reputation irreparably.
#Ransomware #CyberSecurity #DataProtection #VirusThreat #BusinessSecurity #Malware #CyberAttack
Ransomware encrypts your data and demands payment for its release, causing severe business disruptions and financial loss. It can compromise sensitive information and damage your reputation irreparably.
#Ransomware #CyberSecurity #DataProtection #VirusThreat #BusinessSecurity #Malware #CyberAttack
07:08 AM - Jun 21, 2025 (UTC)
Why is Endpoint Protection Vital For CyberSecurity | Digitdefence
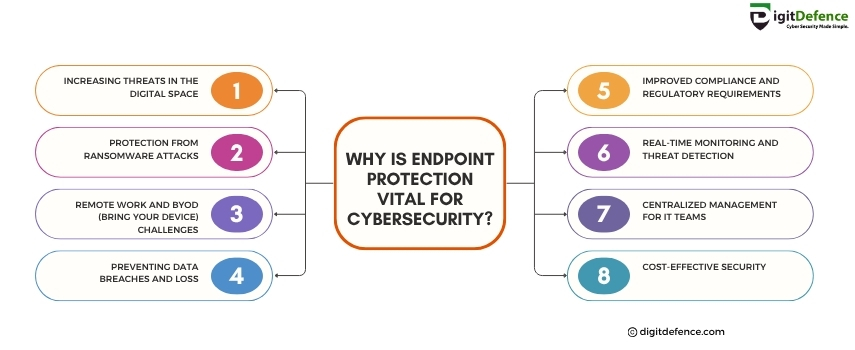
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
Endpoint Protection is vital for cybersecurity because it safeguards devices like laptops, smartphones, and desktops from threats like malware, ransomware, and unauthorized access. As more employees work remotely, securing endpoints becomes crucial to ensure that sensitive data and networks are protected from potential cyberattacks.
#EndpointProtection #CyberSecurity #datasecurity #MalwareProtection #networksecurity #RansomwareDefense #RemoteWorkSecurity #CyberThreats #ITSecurity #DataBreachPrevention
06:44 AM - Jun 13, 2025 (UTC)
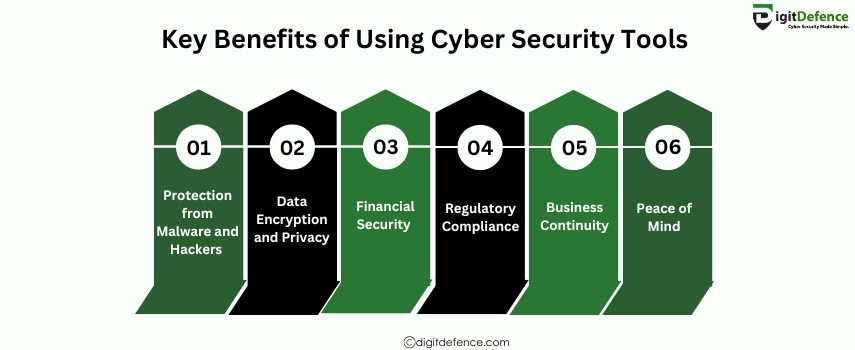
Key Benefits of Using Cyber Security Tools | Digitdefence
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
Key Benefits of Using Cyber Security Tools include enhanced protection against cyberattacks, improved threat detection, and better management of vulnerabilities. These tools help organizations maintain data security, ensure regulatory compliance, and prevent potential breaches before they happen.
#CyberSecurity #DataProtection #ThreatDetection #SecurityTools #CyberThreats #VulnerabilityManagement #dataprivacy #BusinessSecurity #RiskMitigation #infosec #DigitalSecurity
06:28 AM - Jun 13, 2025 (UTC)
The Benefits of Software-Defined Networking (SDN) in Office Security
Cyber attacks are rising, and local businesses in Mercer Island are not exempt. Offices here need more than antivirus software, they need smarter networks. Small businesses account for 43% of cyberattacks, and many lack the right tools to fight back. This is where Software-Defined Networking (SDN) changes everything.
Visit us- https://online.pubhtml5.co...
Cyber attacks are rising, and local businesses in Mercer Island are not exempt. Offices here need more than antivirus software, they need smarter networks. Small businesses account for 43% of cyberattacks, and many lack the right tools to fight back. This is where Software-Defined Networking (SDN) changes everything.
Visit us- https://online.pubhtml5.co...

The Benefits of Software-Defined Networking (SDN) in Office Security
Cyber attacks are rising, and local businesses in Mercer Island are not exempt. Offices here need more than antivirus software, they need smarter networks. Small businesses account for 43% of cyberattacks, and many lack the right tools to fight back. This is where Software-Defined Networking (SDN) c..
https://online.pubhtml5.com/hzzyz/yuho/
09:58 AM - Jun 16, 2025 (UTC)
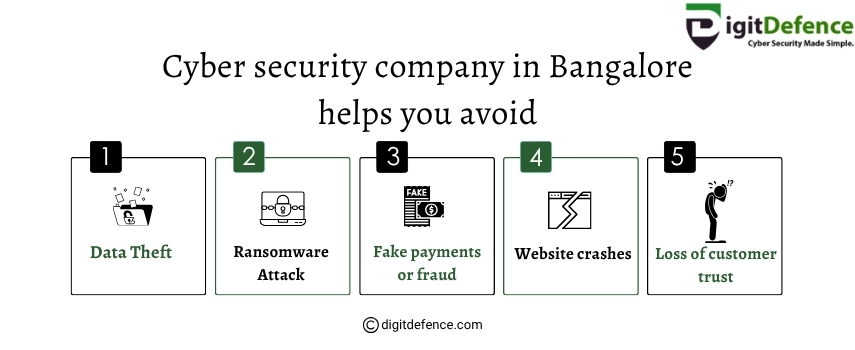
A cyber security company in Bangalore helps protect your business from data theft, ransomware attacks, and online fraud.
It also prevents website crashes and builds customer trust through strong digital protection.
Visit: www.digitdefence.com to learn more.
CyberSecurity | CybersecurityServices | Bangalore | Bengaluru | CyberAttacks | Digitdefence
It also prevents website crashes and builds customer trust through strong digital protection.
Visit: www.digitdefence.com to learn more.
CyberSecurity | CybersecurityServices | Bangalore | Bengaluru | CyberAttacks | Digitdefence
11:37 AM - Jun 26, 2025 (UTC)
🔐💻 “Hackers Don’t Sleep, Why Should Your Cybersecurity?” 🚨🧠
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
12:51 PM - Jun 23, 2025 (UTC)
Why Artificial Intelligence is No Longer Optional in Cybersecurity
With over 2,000 cyberattacks per day per device, traditional defenses fall short. Learn why artificial intelligence solutions are essential to safeguard data, detect threats early, and automate incident response. Read the full blog to understand why AI is now a necessity, not a luxury- in cybersecurity.
Click here: https://www.mooglelabs.com...
#AIinCybersecurity #AIservices #AIdevelopment
With over 2,000 cyberattacks per day per device, traditional defenses fall short. Learn why artificial intelligence solutions are essential to safeguard data, detect threats early, and automate incident response. Read the full blog to understand why AI is now a necessity, not a luxury- in cybersecurity.
Click here: https://www.mooglelabs.com...
#AIinCybersecurity #AIservices #AIdevelopment
10:01 AM - Jun 23, 2025 (UTC)
Using Cyber Security Consulting Services to Increase Business Resilience
We offer expert guidance to protect your business from online threats with our Cyber Security Consulting Services. To prevent cyberattacks, we provide robust security frameworks, detect vulnerabilities, and implement tailored strategies. Our team provides everything from risk assessment and compliance to incident response and ongoing monitoring to ensure the security and resilience of your IT infrastructure. Whether your business is new or well-established, we offer solutions that help you achieve your goals while following industry standards. You can rely on us to safeguard your data, systems, and reputation in an increasingly complex cyberspace. https://500px.com/photo/11...
We offer expert guidance to protect your business from online threats with our Cyber Security Consulting Services. To prevent cyberattacks, we provide robust security frameworks, detect vulnerabilities, and implement tailored strategies. Our team provides everything from risk assessment and compliance to incident response and ongoing monitoring to ensure the security and resilience of your IT infrastructure. Whether your business is new or well-established, we offer solutions that help you achieve your goals while following industry standards. You can rely on us to safeguard your data, systems, and reputation in an increasingly complex cyberspace. https://500px.com/photo/11...
12:20 PM - Jun 26, 2025 (UTC)
Sponsored by
OWT
6 months ago
Why Cybersecurity for Education Industry Must Be a Priority
https://livepositively.com...
Cybersecurity for Education Industry must be a top priority to protect student data, prevent cyberattacks, and ensure safe digital learning environments. Read this article to understand the growing threats and how institutions can stay secure.
#CyberSecurity #EducationTech #DataProtection #CybersecurityforEducationIndustry
https://livepositively.com...
Cybersecurity for Education Industry must be a top priority to protect student data, prevent cyberattacks, and ensure safe digital learning environments. Read this article to understand the growing threats and how institutions can stay secure.
#CyberSecurity #EducationTech #DataProtection #CybersecurityforEducationIndustry

Why Cybersecurity for Education Industry Must Be a Priority
Cybersecurity must be the top priority for schools. Online attacks are nevertheless prevalent and effective in the education sector, despite significant challe
https://livepositively.com/why-cybersecurity-for-education-industry-must-be-a-priority/
05:28 AM - Jun 25, 2025 (UTC)
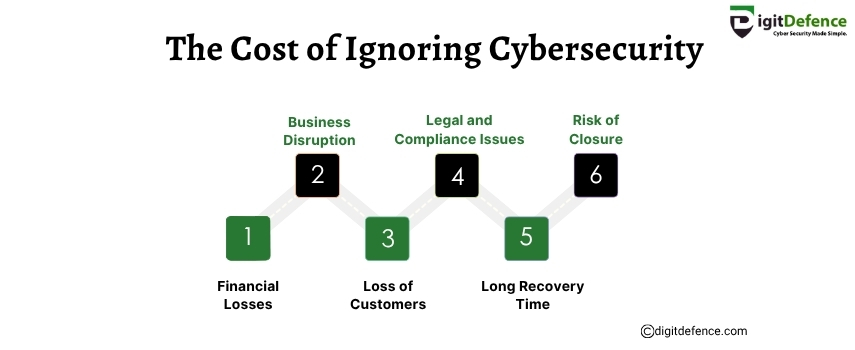
The Cost of Ignoring Cybersecurity | Digitdefence
Ignoring cybersecurity can lead to devastating data breaches, costly downtime, and severe damage to your brand’s reputation. Investing in robust security measures is essential to protect your business from financial losses and legal penalties.
#CyberSecurity #DataProtection #infosec #CyberAttack #BusinessSecurity #riskmanagement
Ignoring cybersecurity can lead to devastating data breaches, costly downtime, and severe damage to your brand’s reputation. Investing in robust security measures is essential to protect your business from financial losses and legal penalties.
#CyberSecurity #DataProtection #infosec #CyberAttack #BusinessSecurity #riskmanagement
06:54 AM - Jun 19, 2025 (UTC)
Data Center Perimeter Security: Strategies for Mitigating Cyber Threats – UAE
Data center perimeter security is essential for protecting sensitive data and ensuring that operations are smooth for data centers across the UAE. By implementing the multi-layered security method that incorporates physical barriers and access control and firewalls and monitoring systems, as in addition to employee education businesses are able successfully combat cyberattacks and lower the risk of a security breach. Data center services in Abu Dhabi, data center operations in Sharjah, and data center solutions in Dubai continue to innovate to tackle the constantly evolving cybersecurity threat that is threatening the entire region.
For more information contact us on:
Tektronix Technology Systems Dubai-Head Office
connecttektronixllc.ae
+971 50 814 4086
+971 55 232 2390
Office No.1E1 | Hamarain Center 132 Abu Baker Al Siddique Rd – Deira – Dubai P.O. Box 85955
Or click on the below link for more information:
https://tektronixllc.ae/da...
Data center perimeter security is essential for protecting sensitive data and ensuring that operations are smooth for data centers across the UAE. By implementing the multi-layered security method that incorporates physical barriers and access control and firewalls and monitoring systems, as in addition to employee education businesses are able successfully combat cyberattacks and lower the risk of a security breach. Data center services in Abu Dhabi, data center operations in Sharjah, and data center solutions in Dubai continue to innovate to tackle the constantly evolving cybersecurity threat that is threatening the entire region.
For more information contact us on:
Tektronix Technology Systems Dubai-Head Office
connecttektronixllc.ae
+971 50 814 4086
+971 55 232 2390
Office No.1E1 | Hamarain Center 132 Abu Baker Al Siddique Rd – Deira – Dubai P.O. Box 85955
Or click on the below link for more information:
https://tektronixllc.ae/da...
09:03 AM - Jun 14, 2025 (UTC)
Cyber Insurance Market Report 2025 | Share, and Demand Forecast by 2033
This market is experiencing robust growth due to the rapidly evolving cyber threat landscape, increasing cyberattacks, and stringent regulatory mandates for data protection. Trends include a surge in demand from SMEs, rising premiums, and the development of comprehensive coverage offerings that address data breaches, ransomware, business interruption, and legal costs associated with cyber incidents.
Read More: https://www.imarcgroup.com...
#marketresearch #business #marketstatistics
#MarketAnalysis #markettrends
This market is experiencing robust growth due to the rapidly evolving cyber threat landscape, increasing cyberattacks, and stringent regulatory mandates for data protection. Trends include a surge in demand from SMEs, rising premiums, and the development of comprehensive coverage offerings that address data breaches, ransomware, business interruption, and legal costs associated with cyber incidents.
Read More: https://www.imarcgroup.com...
#marketresearch #business #marketstatistics
#MarketAnalysis #markettrends

Cyber Insurance Market Size, Share & Growth Report 2033
The cyber insurance market size was valued at USD 14.2 Billion in 2024, expected to reach USD 73.5 Billion at a CAGR of 17.88% during 2025-2033.
https://www.imarcgroup.com/cyber-insurance-market
11:12 AM - Jun 26, 2025 (UTC)