A Global Breach Like Never Before
What does anyone have to do? In one of the most startling digital events in internet history, Cybersecurity Breach 2025 has made over 16 billion login credentials available across the interwebs.
What’s most frightening about this brazen security breach is that it was not caused by one big corporation getting hacked, but by the increasing frequency of infostealer malware infecting individuals thousands of miles apart.
How the Breach Happened: A Look Inside
The far-reaching problem occurs when infovaluer use infostealer malware to hack millions of personal devices across the world.
Here's how it works:
Few individuals actually know they’ve been compromised.
These malware programs, being silent attacks, are first downloaded unknowingly.
They allow the perpetrator to breach the device and quietly collect usernames, passwords, and other sensitive data.
The stolen data is then uploaded to publicly exposed databases on the dark web or cloud-based repositories like GitHub.
These databases:
Require no password
Offer no encryption
Demand no hacking skills to access
Voila—billions of compromised records are available to anyone with minimal effort.
Major Brands and Government Systems Affected
The damages have impacted some of the most trusted names in tech, including:
Apple
GitHub
Telegram
VPN providers
G

16 Billion Passwords Leaked in Biggest Data Breach Ever
Biggest Cybersecurity Data Breach: 16 billion passwords leaked in one mega dump. See how to respond quickly.
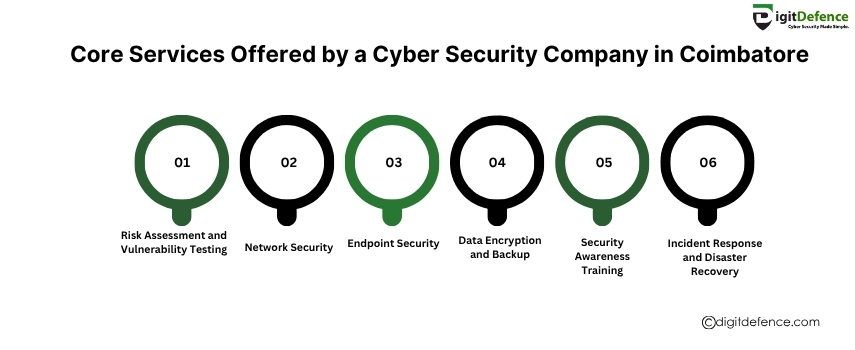
https://oragetechnologies.com/data-breach/A reliable cyber security company in Coimbatore provides essential services like risk assessment, network security, threat detection, data encryption, and incident response to protect your business from evolving cyber threats.
#CyberSecurityCoimbatore #RiskAssessment #networksecurity #ThreatDetection #DataEncryption #IncidentResponse #BusinessProtection
#Wappbiz #WhatsApp #whatsappapi #whatsappbusinessapi #whatsappmarketing #Marketing
https://www.wappbiz.com/bl...

End-to-End Encryption in WhatsApp: Privacy & Security Explained 2025
End-to-End Encryption in WhatsApp is a feature that ensures the privacy of your messages and calls. With E2EE, only the people involved in a conversation can read or listen back over what's written or spoken in that conversation not even WhatsApp itself can do so.
https://www.wappbiz.com/blogs/end-to-end-encryption-in-whatsapp/Dive into the world of NFC Smart Cards and explore how this cutting-edge technology is revolutionizing secure, contactless transactions across industries. Whether enabling fast, tap-to-pay experiences or streamlining secure access control in offices and public transport, NFC Smart Cards combine convenience with advanced encryption for a seamless user experience. Their versatility is driving adoption in retail, banking, healthcare, and more—making everyday interactions faster, safer, and smarter. With the growing demand for hygienic, touch-free solutions, these cards are becoming essential tools for digital transformation. As IoT and mobile integrations advance, NFC Smart Cards are set to play a pivotal role in connected ecosystems. Stay ahead in the digital era by understanding how this smart tech is shaping the future:
https://www.id-smartcards....
The Global API Security Market size is expected to be worth around USD 12,245.7 million by 2034, from USD 751.05 million in 2024, growing at a CAGR of 32.2% during the forecast period from 2025 to 2034. North America held a dominant market position, capturing more than a 42% share, holding USD 315.4 million in revenue.
Read more - https://market.us/report/a...
The API Security Market refers to the industry focused on solutions and services designed to protect Application Programming Interfaces (APIs) from cyber threats. APIs are critical for enabling communication and data exchange between software systems, powering everything from mobile apps to cloud services. As businesses increasingly rely on APIs to drive digital transformation, the need to secure these interfaces against vulnerabilities like data breaches, unauthorized access, and injection attacks has grown. This market includes software, platforms, and services like API gateways, encryption tools, and threat detection systems, all aimed at ensuring secure and compliant API operations across industries such as finance, healthcare, and e-commerce.
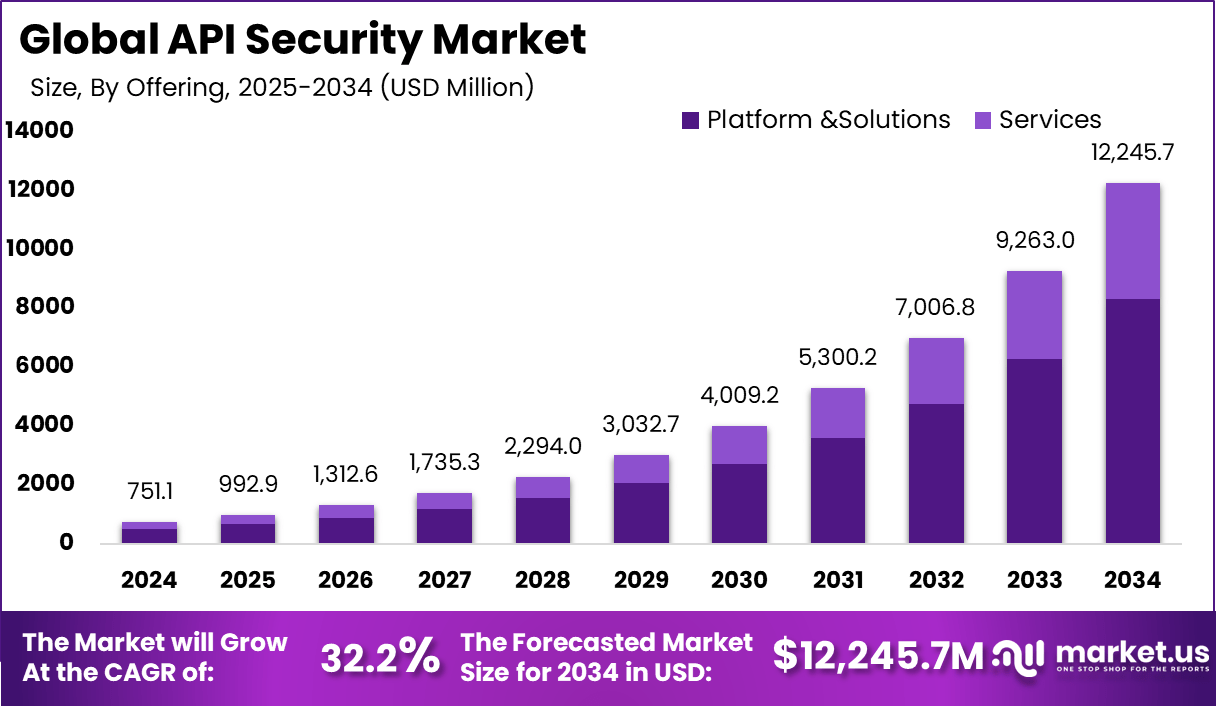
API Security Market Size, Share | CAGR of 32.2%
By 2034, the API Security Market is expected to reach a valuation of USD 12,245.7 Million, expanding at a healthy CAGR of 32.2%.
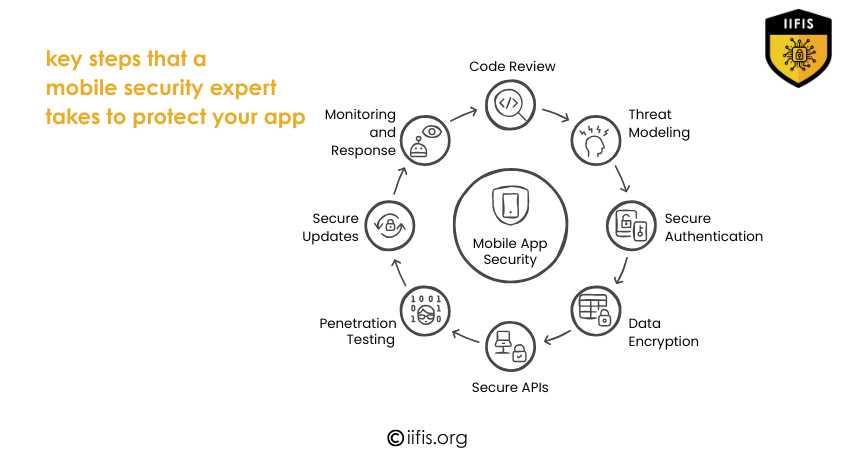
https://market.us/report/api-security-market/Learn the key steps mobile security experts follow to protect your app. From code review and threat modeling to encryption, secure APIs, and updates, each step ensures strong mobile app security and protects user data from threats.
https://iifis.org/blog/the...
Explore more at: https://www.sunrisetechs.c...
The Global Embedded Security Market size is expected to be worth around USD 26.5 Billion By 2034, from USD 10.2 billion in 2024, growing at a CAGR of 10% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 40.2% share, holding USD 4.1 Billion revenue.
Read more - https://market.us/report/g...
The Embedded Security Market refers to the industry focused on integrating security solutions directly into hardware and software systems to protect devices from cyber threats. It encompasses technologies like encryption, secure boot, and authentication mechanisms embedded in devices such as IoT gadgets, automotive systems, and smart cards. This market is critical as it safeguards sensitive data and ensures the integrity of connected devices in an increasingly digital world. Its growth is driven by the need for robust protection against evolving cyber risks, making it essential for industries like healthcare, automotive, and consumer electronics.
The Embedded Security Market, in a broader sense, represents the ecosystem of solutions designed to secure embedded systems, which are specialized computing systems performing dedicated functions within larger devices. It includes hardware like secure microcontrollers and software like firmware updates, addressing vulnerabilities in connected environments.
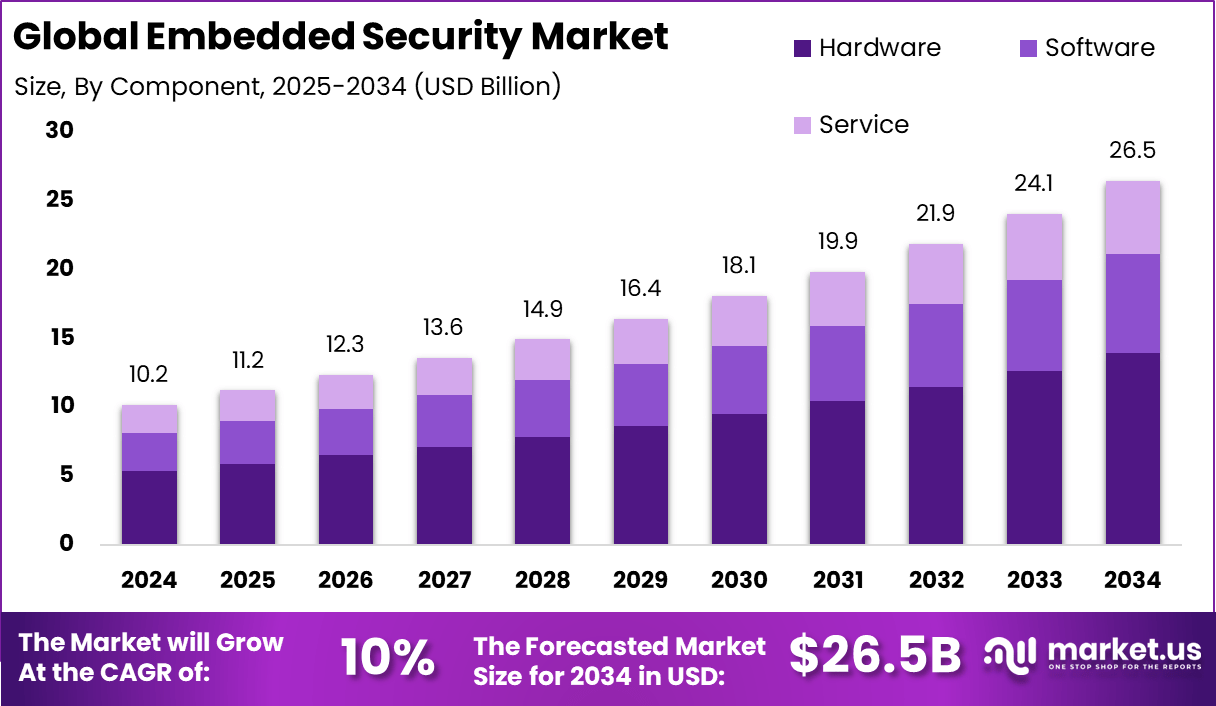
Embedded Security Market Size, Share | CAGR of 10%
By 2034, the Embedded Security Market is expected to reach a valuation of USD 26.5 billion, expanding at a healthy CAGR of 10%.
https://market.us/report/global-embedded-security-market/Japan Cybersecurity Market is flourishing as companies and consumers compete to shield their online habitat against more and more threats in a rapidly netted society. In the ever-increasing ranks of companies that use cloud technology, remote employment, and online trade, cases of cyber-threats have never been higher, necessitating effective defense against them. Protecting sensitive data to protective infrastructure, solutions such as AI-based threat assessor and simple-to-use encryption tools are in demand. Japan Cybersecurity Market is experiencing a massive surge in opportunity as the country stands on the edge of digitalization with the privacy and trust of its people in mind. Japan is taking the digital transition, with prerogative to take a step ahead in a rapidly changing, technology-driven world.
Read more: https://www.imarcgroup.com...
⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
Cybersecurity services are crucial in protecting businesses from increasingly sophisticated cyber threats. Ricoh offers advanced managed cybersecurity solutions that provide 24/7 monitoring, threat detection, and rapid incident response. Their services help prevent data breaches, ransomware attacks, and unauthorized access by implementing strong firewalls, encryption, and user authentication protocols. With Ricoh’s expert support, businesses can ensure compliance, protect customer data, and maintain operational continuity. As cyber risks evolve, Ricoh’s proactive approach adapts to new challenges, allowing organizations to focus on growth while staying secure in a digitally connected world. Visit: https://www.ricoh-usa.com/...
In centralized crypto exchange development, the right stack powers performance and user trust. A great crypto exchange development company helps you choose the best tools. 🏗️
Key Tech Stack Components 🛠️
🔸 Frontend: React.js, Angular, Vue.js for real-time, mobile-friendly UI
🔸 Backend: Node.js, Python, Go for low latency & scalability
🔸 Database: PostgreSQL, MongoDB, Redis for secure data storage
🔸 Matching Engine: Built with C++, Go, Rust for fast trade execution
🔸 Blockchain Integration: Web3.js, ethers.js for smooth transactions
🔸 Wallets: Hot & cold with encryption, multi-signature support
🔸 Security: 2FA, SSL, KYC/AML, DDoS protection 🔒
🔸 APIs: REST/WebSocket for bot & partner access
🔸 Cloud: AWS, Docker, Kubernetes for uptime & scaling ☁️
Build your exchange smartly with Justtry Technologies! 🚀
Visit: https://justtrytech.com/ce...
https://justtrytech.com/cr...
Whatsapp: 9500139200
Email Id: salesjusttrytech.com
Your privacy matters. That’s why WhatsApp uses end-to-end encryption, which means that only you and the person you're chatting with can read the messages.
Not even WhatsApp can access them. 🙌
🛡️ Protected texts, calls, photos & videos
🛡️ No third-party access
🛡️ Secure conversations, always
Do you want to understand how end-to-end encryption works and why it is important for your business and personal chats?
👉 Read the full blog: https://www.wappbiz.com/bl...
#WhatsAppSecurity #EndToEndEncryption #PrivacyFirst #whatsappmarketing #SecureMessaging #Wappbiz

End-to-End Encryption in WhatsApp: Privacy & Security Explained 2025
End-to-End Encryption in WhatsApp is a feature that ensures the privacy of your messages and calls. With E2EE, only the people involved in a conversation can read or listen back over what's written or spoken in that conversation not even WhatsApp itself can do so.
https://www.wappbiz.com/.../end-to-end-encryption-in.../Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
Network Encryption Market - Analysis, trend, Forecast 2022-2028
Global Network Encryption Market is expected to grow at a significant rate of around 9% during the forecast period 2022-2028....
https://univdatos.com/reports/network-encryption-markethttps://www.wappbiz.com/bl...