The Mother of All Leakes and One Tech Giant Who Saw It Coming
Before the world woke up to 16 billion stolen credentials, one client moved early. Why? Maybe they sensed something others didn’t.
We're proud to have led the research that helped them act before it became a nightmare. Cyber defense isn’t just about firewalls—it’s about foresight.
https://www.jaspercolin.co...
#DatatoDecision #CyberSecurity #JasperColin #marketresearch #16BillionLeak #CyberRisk #PasswordSecurity
Before the world woke up to 16 billion stolen credentials, one client moved early. Why? Maybe they sensed something others didn’t.
We're proud to have led the research that helped them act before it became a nightmare. Cyber defense isn’t just about firewalls—it’s about foresight.
https://www.jaspercolin.co...
#DatatoDecision #CyberSecurity #JasperColin #marketresearch #16BillionLeak #CyberRisk #PasswordSecurity
A Breach Foretold: How a Tech Giant Fortify Its Security Before the Largest Password Leak in History
We're proud to have led the research that helped them act before it became a nightmare. Cyber defense isn’t just about firewalls—it’s about foresight.
https://www.jaspercolin.com/resources/success-stories/a-breach-foretold-how-a-tech-giant-fortify-its-security-before-the-largest-password-leak-in-history
02:19 PM - Jun 25, 2025 (UTC)
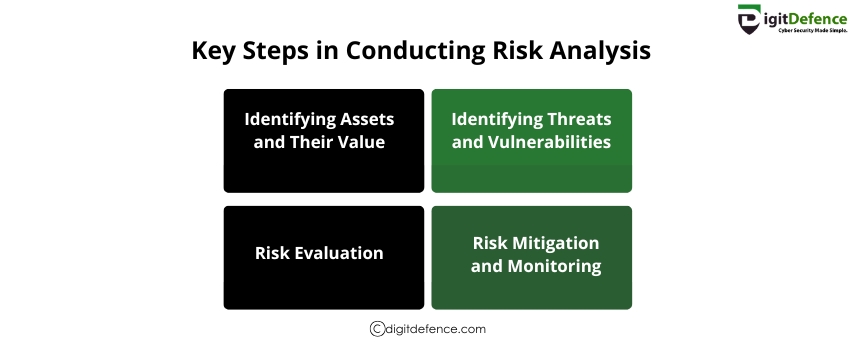
Key Steps in Conducting Risk Analysis | Digitdefence
Learn the essential steps in conducting risk analysis to identify vulnerabilities and strengthen your business security. Protect your assets with a proactive approach.
#RiskAnalysis #BusinessSecurity #CyberRisk #DataProtection #riskmanagement
Learn the essential steps in conducting risk analysis to identify vulnerabilities and strengthen your business security. Protect your assets with a proactive approach.
#RiskAnalysis #BusinessSecurity #CyberRisk #DataProtection #riskmanagement
09:33 AM - May 15, 2025 (UTC)
Sponsored by
OWT
6 months ago
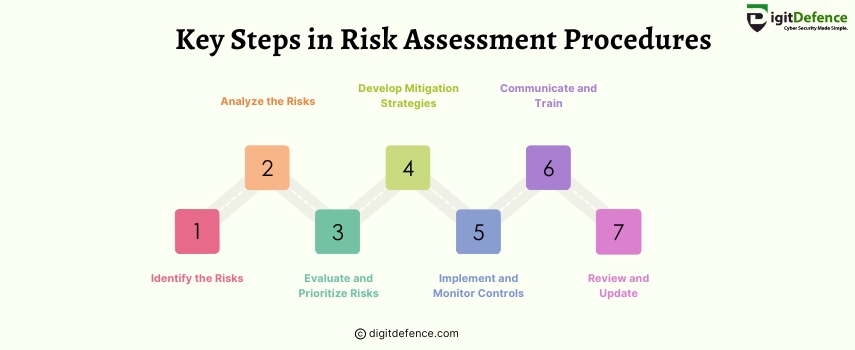
Key Steps in Risk Assessment Procedures | Digitdefence
Key Steps in Risk Assessment Procedures involve identifying potential threats, analyzing vulnerabilities, evaluating impact, and implementing controls. This structured approach helps organizations minimize risks and enhance decision-making.
#RiskAssessment #riskmanagement #BusinessContinuity #CyberRisk #SecurityPlanning
Key Steps in Risk Assessment Procedures involve identifying potential threats, analyzing vulnerabilities, evaluating impact, and implementing controls. This structured approach helps organizations minimize risks and enhance decision-making.
#RiskAssessment #riskmanagement #BusinessContinuity #CyberRisk #SecurityPlanning
09:24 AM - Jun 04, 2025 (UTC)