Common Cloud Security Threats | Digitdefence
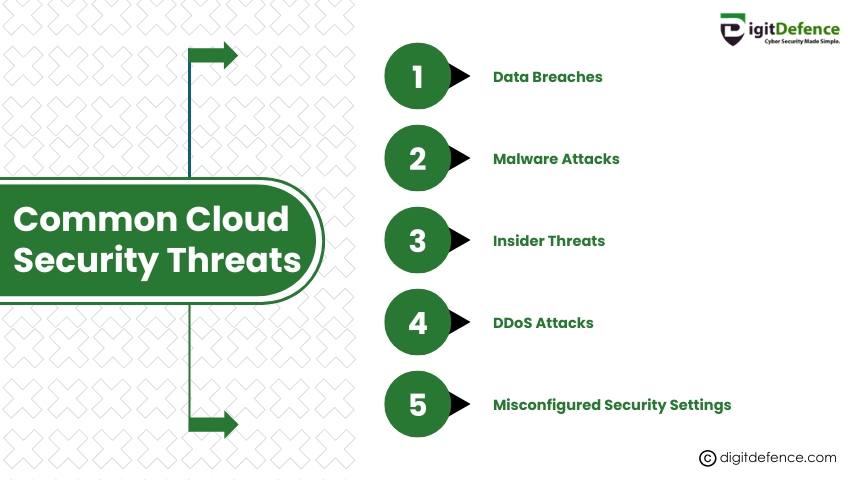
Common cloud security threats include data breaches, misconfigured settings, and insecure APIs. Understanding them is key to building a secure cloud environment.
#cloudsecurity #CyberThreats #DataBreach #cloudcomputing #infosec #CloudProtection #CloudRisk #SecurityAwareness #cloudinfrastructure #SecureCloud
Common cloud security threats include data breaches, misconfigured settings, and insecure APIs. Understanding them is key to building a secure cloud environment.
#cloudsecurity #CyberThreats #DataBreach #cloudcomputing #infosec #CloudProtection #CloudRisk #SecurityAwareness #cloudinfrastructure #SecureCloud
10:16 AM - Jun 06, 2025 (UTC)
Why Startups Must Prioritize Cloud Security In AWS | Digitdefence
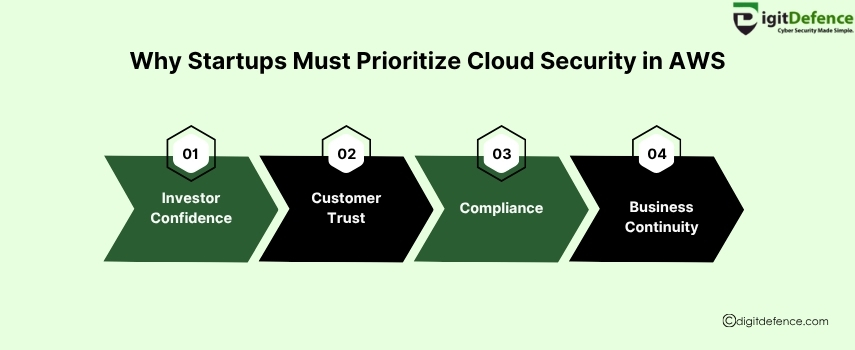
Startups face growing cyber threats, and AWS offers scalable, enterprise-grade security to protect data, build trust, and support rapid growth.
#cloudsecurity #awscloud #StartupSecurity #CyberSecurity #cloudcomputing #DataProtection #AWSSecurity #TechStartups #ScalableSecurity #SecureStartup
Startups face growing cyber threats, and AWS offers scalable, enterprise-grade security to protect data, build trust, and support rapid growth.
#cloudsecurity #awscloud #StartupSecurity #CyberSecurity #cloudcomputing #DataProtection #AWSSecurity #TechStartups #ScalableSecurity #SecureStartup
10:04 AM - Jun 06, 2025 (UTC)
Best Practices For Cloud Security | Digitdefence
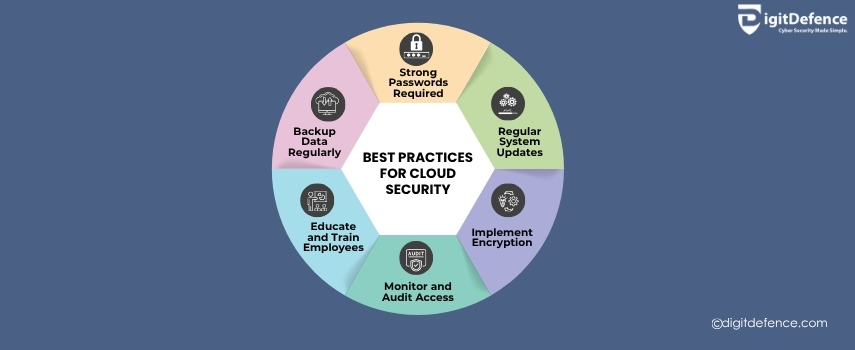
Implement strong access controls, encrypt data, and regularly audit your cloud infrastructure to prevent breaches and ensure business continuity.
#cloudsecurity #DataProtection #CybersecurityTips #CloudCompliance #SecureCloud
Implement strong access controls, encrypt data, and regularly audit your cloud infrastructure to prevent breaches and ensure business continuity.
#cloudsecurity #DataProtection #CybersecurityTips #CloudCompliance #SecureCloud
09:28 AM - Jun 05, 2025 (UTC)
Why are Pen Testing Services Critical For Businesses
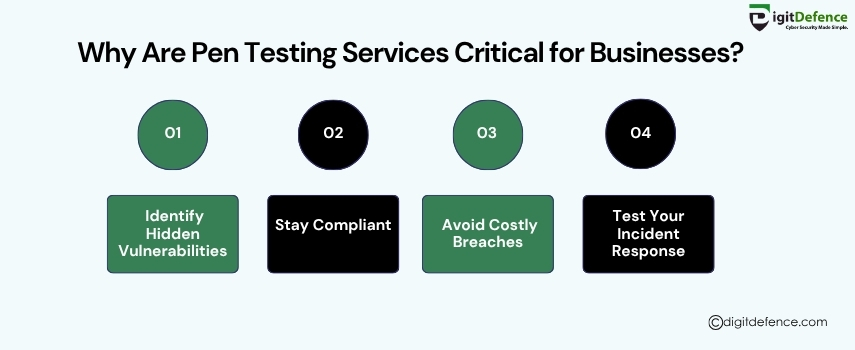
Pen Testing Services are essential for identifying hidden security gaps before attackers do, helping businesses prevent costly breaches and ensure compliance.
#pentesting #CyberSecurity #BusinessSecurity #VulnerabilityAssessment #DataProtection
Pen Testing Services are essential for identifying hidden security gaps before attackers do, helping businesses prevent costly breaches and ensure compliance.
#pentesting #CyberSecurity #BusinessSecurity #VulnerabilityAssessment #DataProtection
09:12 AM - Jun 05, 2025 (UTC)
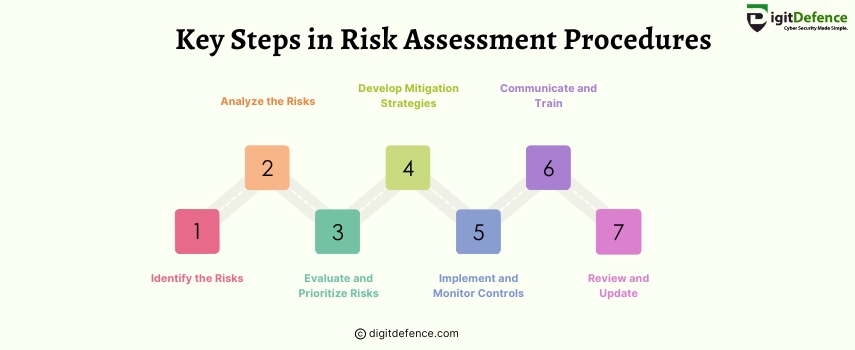
Key Steps in Risk Assessment Procedures | Digitdefence
Key Steps in Risk Assessment Procedures involve identifying potential threats, analyzing vulnerabilities, evaluating impact, and implementing controls. This structured approach helps organizations minimize risks and enhance decision-making.
#RiskAssessment #riskmanagement #BusinessContinuity #CyberRisk #SecurityPlanning
Key Steps in Risk Assessment Procedures involve identifying potential threats, analyzing vulnerabilities, evaluating impact, and implementing controls. This structured approach helps organizations minimize risks and enhance decision-making.
#RiskAssessment #riskmanagement #BusinessContinuity #CyberRisk #SecurityPlanning
09:24 AM - Jun 04, 2025 (UTC)
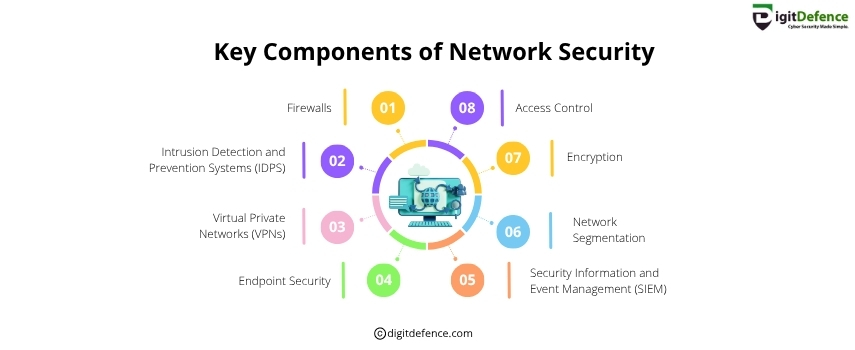
Key Components of Network Security | Digitdefence
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
09:16 AM - Jun 04, 2025 (UTC)
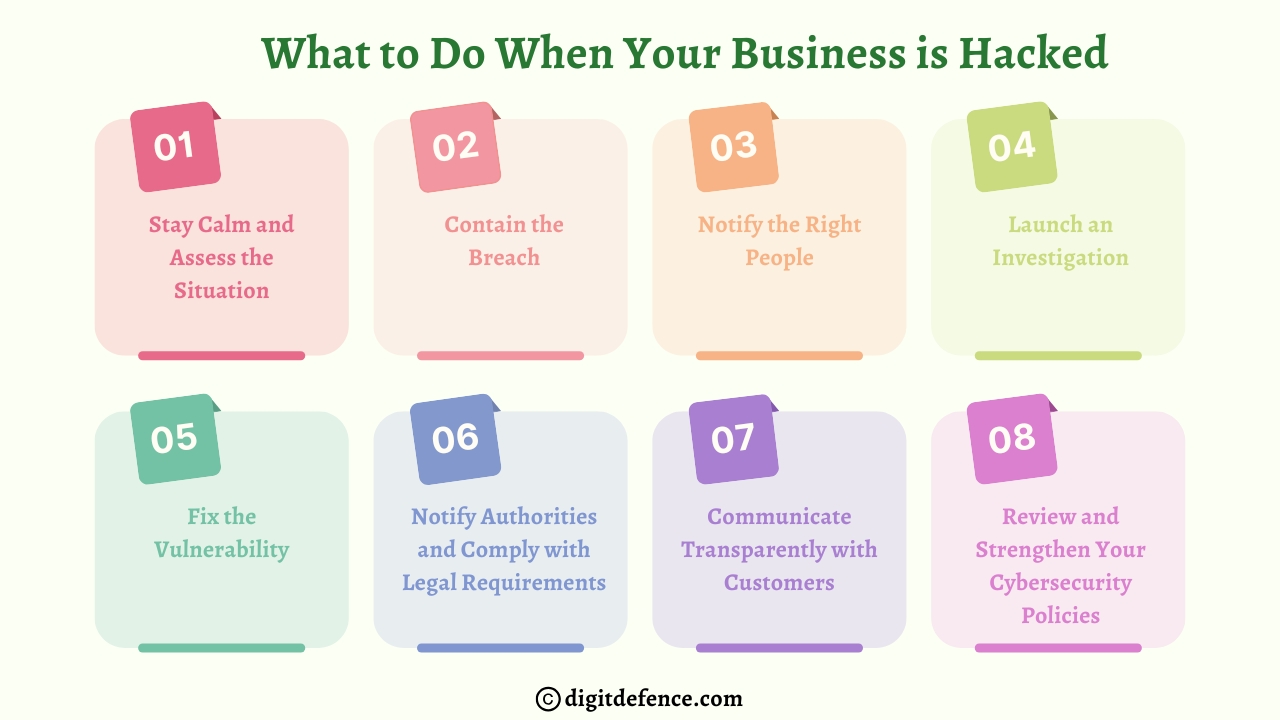
What to Do When Your Business is Hacked | Digitdefence
If your business is hacked, immediately isolate affected systems, notify your IT team, and change all passwords to prevent further damage. Then, report the breach to authorities and start a thorough investigation to identify the cause and secure your data.
#CyberAttack #BusinessSecurity #DataBreach #IncidentResponse
If your business is hacked, immediately isolate affected systems, notify your IT team, and change all passwords to prevent further damage. Then, report the breach to authorities and start a thorough investigation to identify the cause and secure your data.
#CyberAttack #BusinessSecurity #DataBreach #IncidentResponse
09:39 AM - Jun 03, 2025 (UTC)
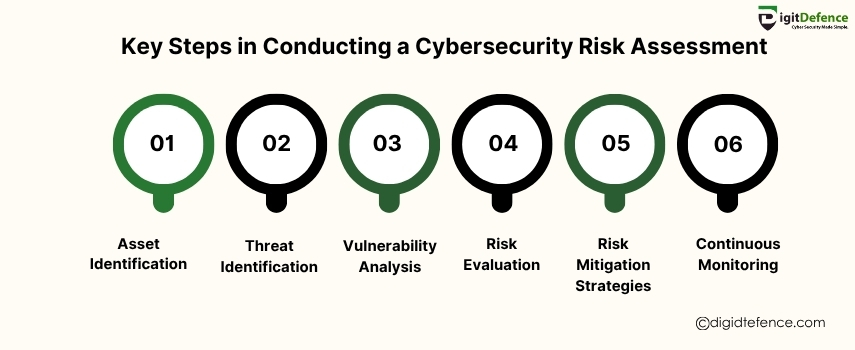
Key Steps in Conducting a Cybersecurity Risk Assessment
Conducting a cybersecurity risk assessment involves identifying potential threats and vulnerabilities to your business’s digital assets, then prioritizing risks to implement effective security measures. It’s crucial for protecting sensitive data and ensuring business continuity.
#CyberSecurity #RiskAssessment #DataProtection #BusinessSecurity
Conducting a cybersecurity risk assessment involves identifying potential threats and vulnerabilities to your business’s digital assets, then prioritizing risks to implement effective security measures. It’s crucial for protecting sensitive data and ensuring business continuity.
#CyberSecurity #RiskAssessment #DataProtection #BusinessSecurity
09:29 AM - Jun 03, 2025 (UTC)
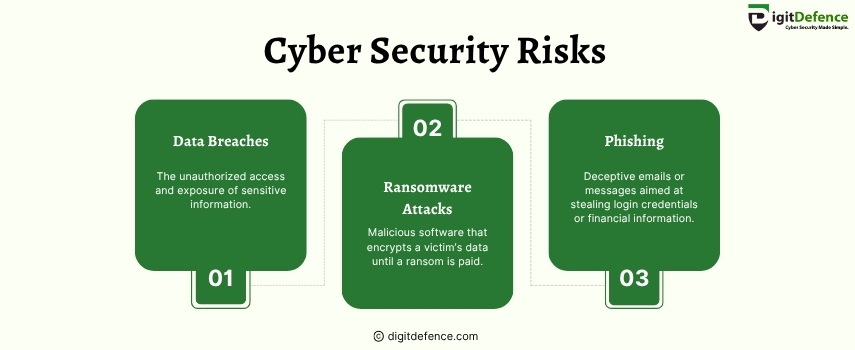
Cyber Security Risks | Digitdefence
Cyber security risks include threats like data breaches, malware attacks, and phishing scams that can compromise sensitive information and disrupt business operations. Staying vigilant and implementing strong security measures is essential to protect your assets.
#CyberSecurityRisks #DataProtection #CyberThreats #infosec #DigitalSecurity
Cyber security risks include threats like data breaches, malware attacks, and phishing scams that can compromise sensitive information and disrupt business operations. Staying vigilant and implementing strong security measures is essential to protect your assets.
#CyberSecurityRisks #DataProtection #CyberThreats #infosec #DigitalSecurity
09:11 AM - Jun 02, 2025 (UTC)
How To Choose the Right Security Tools for Your Business
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
Choosing the right security tools for your business involves assessing your specific risks, understanding your infrastructure, and selecting solutions that offer robust protection without compromising performance. Always prioritize tools that are scalable and easy to integrate.
#CyberSecurity #BusinessSecurity #SecurityTools #DataProtection #ITSecurity
08:55 AM - Jun 02, 2025 (UTC)
Sponsored by
OWT
4 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/