24/7, we are always dedicated to your service.
Email:-seodigitalz70gmail.com
Telegram:-seodigitalz
Skype:- seodigitalz
WhatsApp:- +1 (406) 217-0058
https://seodigitalz.com/pr...
#github #javascript #coding #programming #python #html #linux #programmer #Developer
#git #java #computerscience #css #kalilinux #coder #Coders #webdeveloper #WebDevelopment
#Hacking #softwaredeveloper #codinglife #MachineLearning #stackoverflow #EthicalHacking
#CyberSecurity #code #hacker #daysofcode #DevOps #Hackers
Decentralised exchanges (DEXs) are becoming increasingly popular venues for international bitcoin trading. Unlike traditional, centralized exchanges, DEXs allow users to trade cryptocurrencies directly with one another no middleman, no delays, and no need to give up control of your funds. In this blog, we’ll explore the real value of decentralized exchanges and why they’re gaining massive popularity, especially among those who care about privacy, security, and freedom in the crypto space.
1. Why more individuals are trading cryptocurrencies on DEXs
In recent years, we’ve seen a significant shift in the way people trade cryptocurrencies. Centralized exchanges, while popular and easy to use, come with major drawbacks: they require you to trust a third party with your funds, they’re often targeted by hackers, and they may suffer from outages or restrictions.
On the other hand, decentralized exchanges offer a safer and more flexible alternative. Since users retain full control of their crypto wallets and private keys, there’s no need to rely on a centralized platform to hold or protect your funds. Peer-to-peer communication is quick, effective, and transparent.
2. How DEXs give you more control and safety
Control is one of the main benefits of utilising a decentralised exchange. Your bitcoin stays in your wallet until you trade on a DEX.This removes a major point of failure common in centralized platforms, where funds are stored
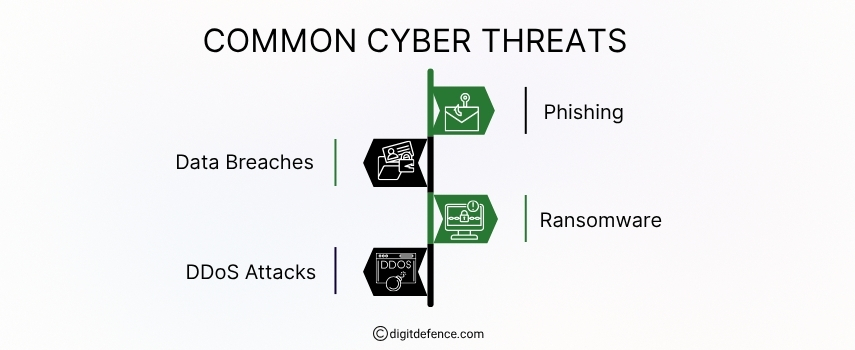
Common cyber threats include phishing attacks, where hackers trick you into giving up personal info, and malware, which can silently steal data or damage systems. Staying alert and using good security tools can help keep you safe.
#CyberSecurity #PhishingAwareness#MalwareProtection
#OnlineSafety #CyberThreats#DataSecurity#StaySafeOnline
Crypto exchanges are hot targets for hackers. With millions at stake, securing your crypto trading software is essential. Major threats include cyber attacks, phishing, insider breaches, DDoS, API flaws, and wallet vulnerabilities. Even smart contracts can carry fatal bugs.
🔒 How to Stay Secure?
Use end-to-end encryption
Require multi-signature wallets
Enforce two-factor authentication
Run regular audits & penetration testing
Follow KYC/AML compliance
If you're choosing the best crypto day trading platform, look for real-time security, transparency, and strong user protections. In this fast-moving market, security isn't optional—it’s your competitive edge. Is your platform protected?
visit : https://justtrytech.com/wa...
#crypto #CryptoExchange #security #development #cryptotrading #Blockchain
In an increasingly digital world, cybersecurity has become a top priority for organizations of all sizes. With growing threats from hackers, data breaches, and cyber attacks, the demand for skilled ethical hackers is higher than ever. If you're interested in a career that combines technology, investigation, and problem-solving, enrolling in an Ethical Hacking course in Bangalore could be the ideal step forward.
Why Ethical Hacking Matters Today
Ethical hacking involves identifying vulnerabilities in computer systems, networks, or applications and fixing them before malicious hackers can exploit them. It is a legal and structured practice aimed at strengthening security. As more companies move their operations online and deal with sensitive data, having certified ethical hackers on board has become a necessity rather than a choice.
Taking an Ethical Hacking course in Bangalore not only builds your technical expertise but also helps you understand the mindset of cybercriminals—allowing you to anticipate threats and design secure systems.
Why Choose Bangalore for Ethical Hacking?
Bangalore, known as India's IT capital, is a hotspot for cybersecurity training and innovation. With numerous tech companies, MNCs, and cybersecurity startups based in the city, there's a strong demand for trained professionals. By joining an Ethical Hacking course in Bangalore, you’ll get access to experienced trainers, real-

Ethical Hacking Course in Bangalore | Apponix Academy
Join Apponix Academy’s Ethical Hacking Course in Bangalore. Learn penetration testing, network security, and cyber defense with real-time projects and 100% placement support.
https://www.apponix.com/ethical-hacking-certification-in-Bangalore⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
In an increasingly digital world, cybersecurity has become a top priority for organizations of all sizes. With growing threats from hackers, data breaches, and cyber attacks, the demand for skilled ethical hackers is higher than ever. If you're interested in a career that combines technology, investigation, and problem-solving, enrolling in an Ethical Hacking course in Bangalore could be the ideal step forward.
Why Ethical Hacking Matters Today
Ethical hacking involves identifying vulnerabilities in computer systems, networks, or applications and fixing them before malicious hackers can exploit them. It is a legal and structured practice aimed at strengthening security. As more companies move their operations online and deal with sensitive data, having certified ethical hackers on board has become a necessity rather than a choice.
Taking an Ethical Hacking course in Bangalore not only builds your technical expertise but also helps you understand the mindset of cybercriminals—allowing you to anticipate threats and design secure systems.
Why Choose Bangalore for Ethical Hacking?
Bangalore, known as India's IT capital, is a hotspot for cybersecurity training and innovation. With numerous tech companies, MNCs, and cybersecurity startups based in the city, there's a strong demand for trained professionals. By joining an Ethical Hacking course in Bangalore, you’ll get access to experienced trainers, real-

Ethical Hacking Course in Bangalore | Apponix Academy
Join Apponix Academy’s Ethical Hacking Course in Bangalore. Learn penetration testing, network security, and cyber defense with real-time projects and 100% placement support.
https://www.apponix.com/ethical-hacking-certification-in-BangaloreWant to learn how to investigate cyber crimes? Hacker School offers a detailed Computer Hacking Forensic Investigator course that teaches you how to track hackers, collect digital evidence, and recover deleted data. With real-world tools, expert trainers, and hands-on practice, you’ll gain the skills needed to work in digital forensics. Hacker School also provides job support to help you start your career in cybercrime investigation.
https://www.hackerschool.i...

Computer Hacking Forensic Investigator (CHFI) Course Online or In-Person | CHFI Certification Cost | Cyber Forensics Course
Computer Hacking Forensic Investigator (CHFI) Certification provides necessary methods to identify, track and prosecute cybercrimes. Join this course Online or In-Person now. Contact us to know about CHFI certification cost.
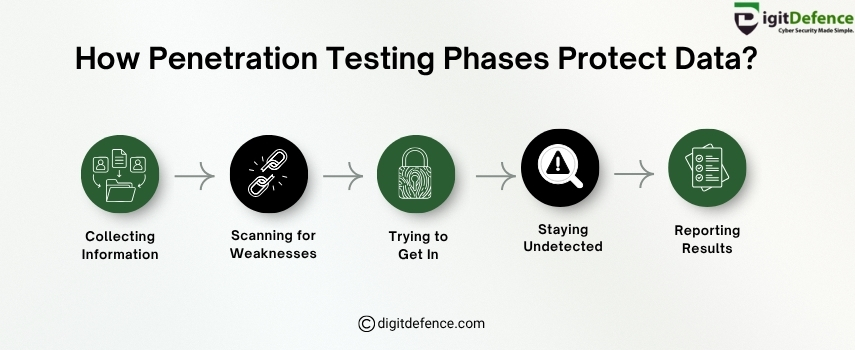
https://www.hackerschool.in/courses/computer-hacking-forensic-investigator-chfi/Penetration testing protects your data by following smart steps. It starts with collecting information, then scanning for weaknesses. Next, ethical hackers try to get in, stay hidden, and finally report the results. These phases help find and fix risks before hackers can use them.
Get your systems tested today.
Visit: www.digitdefence.com
#CyberSecurity #PenetrationTesting #pentesting #Digitdefence
To evaluate the security of an organization's internet-facing assets, including web servers, firewalls, and email systems, external network penetration testing simulates a cyberattack. This test finds weaknesses that could be used by outside attackers to obtain unauthorised access or interfere with services. Ethical hackers test the effectiveness of perimeter defences against intrusion attempts by simulating actual attack methods. Finding security flaws before bad actors do is the aim, and actionable insights are provided to strengthen defences and lower risk. It's an essential part of a thorough cybersecurity plan. https://blogosm.com/why-ch...
Interested in solving digital crimes? Hacker School offers a detailed Computer Hacking Forensic Investigator course that teaches you how to track hackers, recover lost data, and investigate cyber attacks. With hands-on tools, real case studies, and expert support, you'll gain the skills needed for cybercrime analysis. Hacker School helps you prepare for a strong career in digital forensics and cyber investigations.
https://www.hackerschool.i...

Computer Hacking Forensic Investigator (CHFI) Course Online or In-Person | CHFI Certification Cost | Cyber Forensics Course
Computer Hacking Forensic Investigator (CHFI) Certification provides necessary methods to identify, track and prosecute cybercrimes. Join this course Online or In-Person now. Contact us to know about CHFI certification cost.
https://www.hackerschool.in/courses/computer-hacking-forensic-investigator-chfi/The Good: AI as a Cybersecurity Game-Changer
AI has dramatically transformed how we defend digital infrastructures. Its ability to analyze vast datasets, detect anomalies, and respond to threats in real-time is unparalleled. With machine learning algorithms, AI tools can predict and neutralize threats before they manifest.
AI-driven cybersecurity empower organizations to:
Detect zero-day vulnerabilities
Automate threat response
Identify insider threats
Optimize security workflows
The Bad: AI as a Weapon for Cybercriminals
Unfortunately, the same technologies that protect us can be weaponized. Hackers now deploy AI to craft more sophisticated phishing attacks, generate malicious deepfakes, and bypass traditional security measures with alarming precision.
The dark side of AI includes:
AI-Powered Malware: Capable of morphing signatures to evade detection.
Smart Phishing: AI tools can personalize and scale phishing campaigns using scraped data.
Deepfake Technology: Creates convincing audio/video fabrications that deceive users and systems.
Organizations must embrace AI-enhanced cybersecurity solutions while remaining vigilant against AI-driven threats. The key is not just adoption but ethical implementation, robust regulation, and continuous education.
For more information, visit us: https://www.datspy.com/
24/7, we are always dedicated to your service.
Email:-seodigitalz70gmail.com
Telegram:-seodigitalz
Skype:- seodigitalz
WhatsApp:- +1 (406) 217-0058
https://seodigitalz.com/pr...
#github #javascript #coding #programming #python #html #linux #programmer #Developer
#git #java #computerscience #css #kalilinux #coder #Coders #webdeveloper #WebDevelopment
#Hacking #softwaredeveloper #codinglife #MachineLearning #stackoverflow #EthicalHacking
#CyberSecurity #code #hacker #daysofcode #DevOps #Hackers

Buy Github Account | Verified & Aged GitHub Accounts 2025
Purchase Buy Github Account with full access. Get aged, high-reputation GitHub accounts for seamless development, collaboration, and credibility.
https://seodigitalz.com/product/buy-github-account/Keeping your Nulls Brawl account secure is essential to avoid losing your progress. For more tips and updates, visit this official website :https://nulsbrawl.tr/
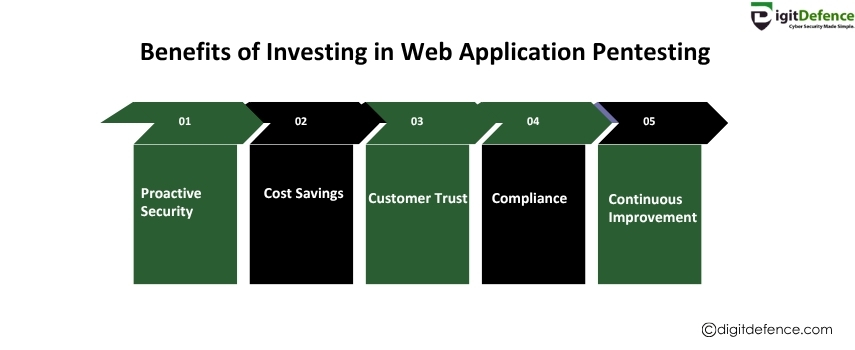
Investing in web application pentesting helps identify and fix security vulnerabilities before hackers exploit them, protecting your data and reputation. It also ensures compliance with industry regulations and strengthens overall cybersecurity.
#WebAppPentesting #CyberSecurity #DataProtection #PentestingBenefits #securitytesting #VulnerabilityAssessment #CyberSafety #infosec #riskmanagement #SecureApps