Protect Your Business from Cyber Threats with DigitDefence
Looking for reliable cybersecurity services for your business? DigitDefence is your trusted partner in defending against online threats. We offer expert solutions tailored for businesses of all sizes:
Vulnerability Assessments
Penetration Testing
Network Security
Endpoint Protection
Cloud Security
Safeguard your digital assets and ensure business continuity with our comprehensive security solutions.
https://www.digitdefence.c...
Looking for reliable cybersecurity services for your business? DigitDefence is your trusted partner in defending against online threats. We offer expert solutions tailored for businesses of all sizes:
Vulnerability Assessments
Penetration Testing
Network Security
Endpoint Protection
Cloud Security
Safeguard your digital assets and ensure business continuity with our comprehensive security solutions.
https://www.digitdefence.c...
10:45 AM - Jul 03, 2025 (UTC)
Strong Transparent Furniture Protection Film for your Furniture
Your wooden furniture deserves the best defence. ProProtect’s invisible furniture protection film forms a tough, transparent layer that prevents damage while maintaining natural wood aesthetics. It’s the perfect choice for homes with kids, pets, or high-traffic use. From coffee tables to countertops, this film is made for real-life conditions. Make your furniture last longer—buy ProProtect now!
For More Information,
Visit: https://proprotect.in/furn...
#FurnitureProtection #ProtectYourFurniture #HomeImprovement #interiordesign #SurfaceProtection #FurnitureCare #ScratchResistant #HeatResistantFilm #FurnitureMakeover #ProProtectIndia
Your wooden furniture deserves the best defence. ProProtect’s invisible furniture protection film forms a tough, transparent layer that prevents damage while maintaining natural wood aesthetics. It’s the perfect choice for homes with kids, pets, or high-traffic use. From coffee tables to countertops, this film is made for real-life conditions. Make your furniture last longer—buy ProProtect now!
For More Information,
Visit: https://proprotect.in/furn...
#FurnitureProtection #ProtectYourFurniture #HomeImprovement #interiordesign #SurfaceProtection #FurnitureCare #ScratchResistant #HeatResistantFilm #FurnitureMakeover #ProProtectIndia
12:59 PM - Jul 03, 2025 (UTC)
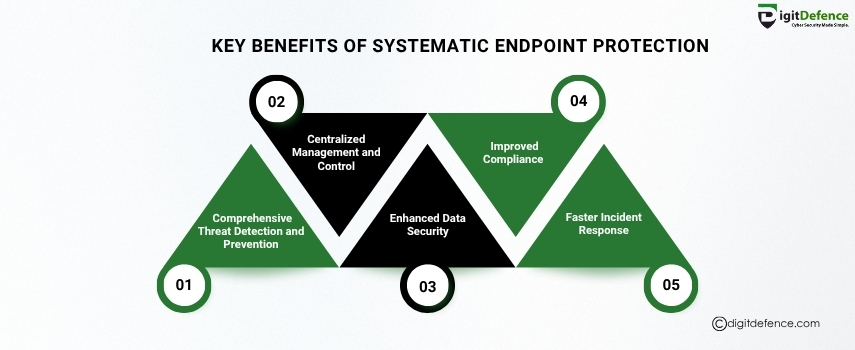
Key Benefits of Systematic Endpoint Protection | Digitdefence
Discover the key benefits of systematic endpoint protection from preventing data breaches to ensuring secure access across all devices in your network.
#EndpointProtection #CyberSecurity #datasecurity #NetworkProtection #ITSecurity #SecureDevices #ThreatPrevention #EndpointSecuritySolutions
Discover the key benefits of systematic endpoint protection from preventing data breaches to ensuring secure access across all devices in your network.
#EndpointProtection #CyberSecurity #datasecurity #NetworkProtection #ITSecurity #SecureDevices #ThreatPrevention #EndpointSecuritySolutions
12:54 PM - Jul 02, 2025 (UTC)
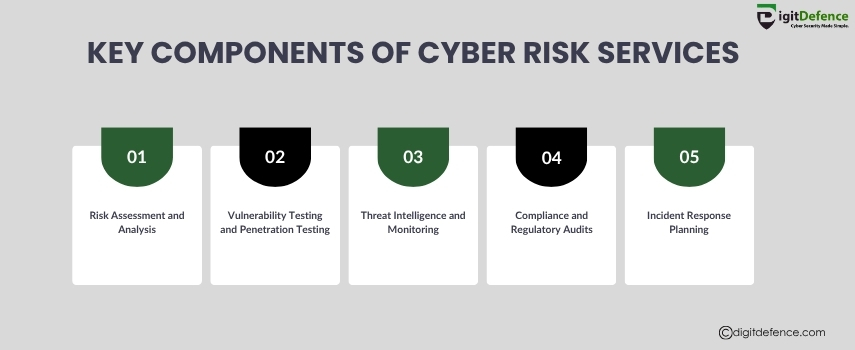
Key Components of Cyber Risk Services | Digitdefence
Understand the key components of cyber risk services — including threat assessment, vulnerability management, compliance support, and incident response. Strengthen your cybersecurity posture with a structured approach.
#CyberRisk #Cybersecurityservices #riskmanagement #ThreatAssessment #VulnerabilityManagement #ComplianceSupport #IncidentResponse #ITSecurity
Understand the key components of cyber risk services — including threat assessment, vulnerability management, compliance support, and incident response. Strengthen your cybersecurity posture with a structured approach.
#CyberRisk #Cybersecurityservices #riskmanagement #ThreatAssessment #VulnerabilityManagement #ComplianceSupport #IncidentResponse #ITSecurity
01:00 PM - Jul 02, 2025 (UTC)
Protect Your Business with DigitDefence Cyber Security Services
Is your business truly secure online? At DigitDefence, we offer expert Cyber Security Solutions tailored to protect your digital assets and keep cyber threats away.
Services we offer:
Penetration Testing
Network Security
Endpoint Security
Cloud Security
Cyber Security Made Simple – So You Can Focus on Growth
Get in touch today and secure your future with our trusted cybersecurity solutions.
Contact: +91 7996969994
Website: www.digitdefence.com
We work with IT companies, SaaS startups, fintech, healthcare, and e-commerce businesses.
Partner with us to stay protected. Let’s make cybersecurity simple, effective, and affordable.
Is your business truly secure online? At DigitDefence, we offer expert Cyber Security Solutions tailored to protect your digital assets and keep cyber threats away.
Services we offer:
Penetration Testing
Network Security
Endpoint Security
Cloud Security
Cyber Security Made Simple – So You Can Focus on Growth
Get in touch today and secure your future with our trusted cybersecurity solutions.
Contact: +91 7996969994
Website: www.digitdefence.com
We work with IT companies, SaaS startups, fintech, healthcare, and e-commerce businesses.
Partner with us to stay protected. Let’s make cybersecurity simple, effective, and affordable.
10:06 AM - Jul 01, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
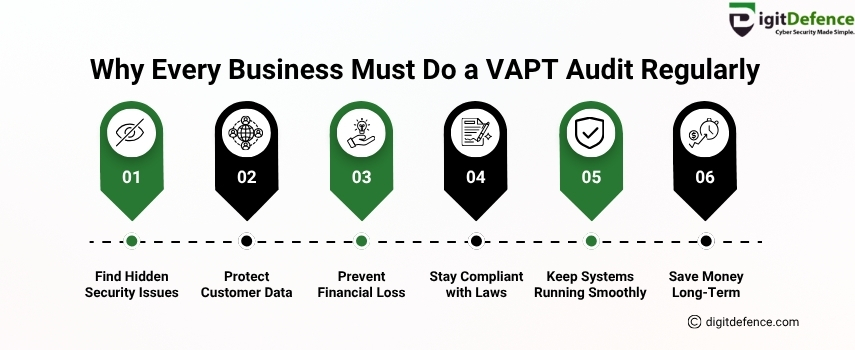
Why Every Business Must Do a VAPT Audit Regularly
Protect your business with regular VAPT audit services to find security issues, avoid data loss, and stay safe. VAPT helps you follow cyber laws and save money by preventing future attacks.
Visit www.digitdefence.com to secure your systems today.
Protect your business with regular VAPT audit services to find security issues, avoid data loss, and stay safe. VAPT helps you follow cyber laws and save money by preventing future attacks.
Visit www.digitdefence.com to secure your systems today.
10:30 AM - Jul 03, 2025 (UTC)
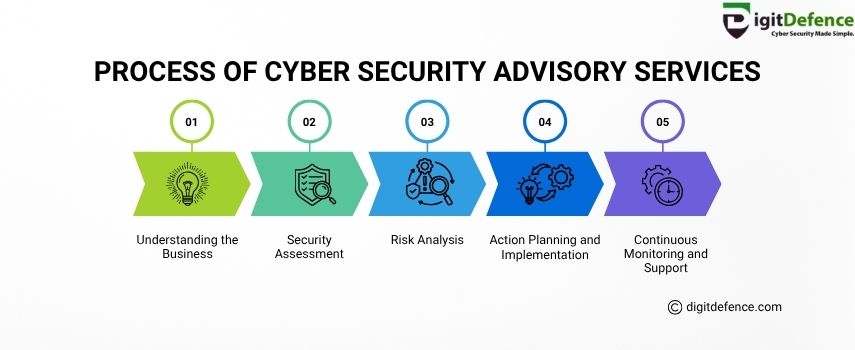
Process of Cyber Security Advisory Services
Protect Your Business from Cyber Threats – Step-by-Step Guide to Cyber Security Advisory Services
Learn how expert cyber security consulting safeguards your business with risk analysis, security planning, and continuous protection.
Visit digitdefence.com to secure your business now!
Protect Your Business from Cyber Threats – Step-by-Step Guide to Cyber Security Advisory Services
Learn how expert cyber security consulting safeguards your business with risk analysis, security planning, and continuous protection.
Visit digitdefence.com to secure your business now!
09:32 AM - Jul 01, 2025 (UTC)
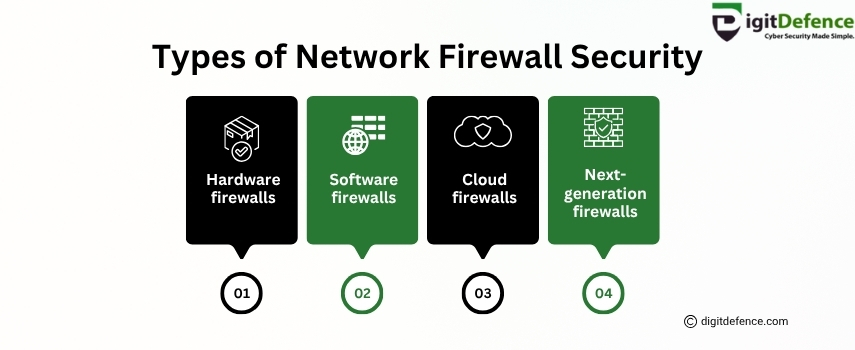
Types of Network Firewall Security
Protect Your Business with the Right Network Firewall!
Explore 4 powerful types of firewall security, Hardware, Software, Cloud & Next-Gen, to block threats and keep your data safe.
Learn more at www.digitdefence.com
Secure Your Network Today!
#CyberSecurity #Cybersecurityservices
Protect Your Business with the Right Network Firewall!
Explore 4 powerful types of firewall security, Hardware, Software, Cloud & Next-Gen, to block threats and keep your data safe.
Learn more at www.digitdefence.com
Secure Your Network Today!
#CyberSecurity #Cybersecurityservices
09:11 AM - Jul 01, 2025 (UTC)
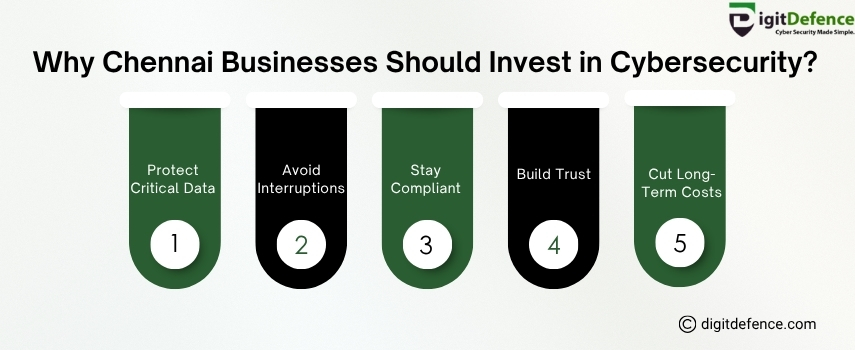
Why Chennai Businesses Should Invest in Cybersecurity?
Cyber attacks are rising fast, every Chennai business needs strong cybersecurity to stay protected and build trust.
Secure your data, stay compliant, and cut long-term costs with expert solutions.
Visit digitdefence.com today and get a free cybersecurity consultation for your business.
Cyber attacks are rising fast, every Chennai business needs strong cybersecurity to stay protected and build trust.
Secure your data, stay compliant, and cut long-term costs with expert solutions.
Visit digitdefence.com today and get a free cybersecurity consultation for your business.
12:53 PM - Jul 02, 2025 (UTC)
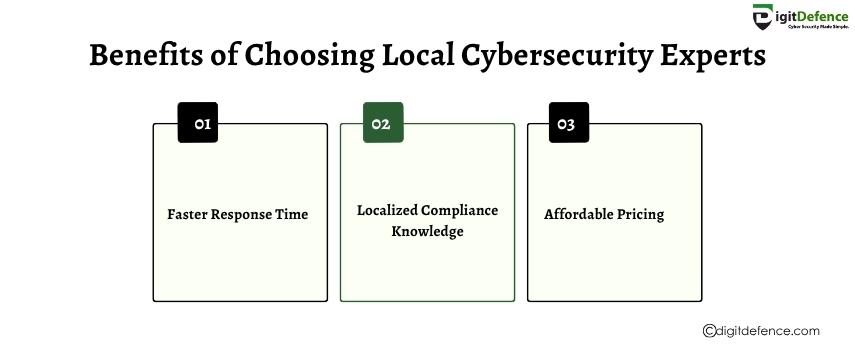
Benefits of Choosing Local Cybersecurity Experts | Digitdefence
Choosing local cybersecurity experts means faster response times, personalized support, and a deeper understanding of regional threats and compliance needs. Strengthen your defense with professionals who know your business environment.
#CyberSecurity #LocalExperts #ITSecuritySupport #DataProtection #riskmanagement #Compliance #CyberDefense #SmallBusinessSecurity #EndpointSecurity #NetworkProtection
Choosing local cybersecurity experts means faster response times, personalized support, and a deeper understanding of regional threats and compliance needs. Strengthen your defense with professionals who know your business environment.
#CyberSecurity #LocalExperts #ITSecuritySupport #DataProtection #riskmanagement #Compliance #CyberDefense #SmallBusinessSecurity #EndpointSecurity #NetworkProtection
09:47 AM - Jul 03, 2025 (UTC)
Deepinder Goyal Launches LAT Aerospace for Defence Innovation
Zomato CEO Deepinder Goyal launches LAT Aerospace to revolutionize India's defence sector with advanced manufacturing, innovation, and self-reliant technology.
https://moneycages.com/fin...
Zomato CEO Deepinder Goyal launches LAT Aerospace to revolutionize India's defence sector with advanced manufacturing, innovation, and self-reliant technology.
https://moneycages.com/fin...
10:54 AM - Jul 02, 2025 (UTC)
Steps Involved in Web App Pentesting
Web app pentesting includes setting a clear goal, scanning for issues, testing manually, and fixing the problems. These steps help make the application safer and more secure.
Learn more at, www.digitdefence.com
Web app pentesting includes setting a clear goal, scanning for issues, testing manually, and fixing the problems. These steps help make the application safer and more secure.
Learn more at, www.digitdefence.com
09:40 AM - Jun 30, 2025 (UTC)
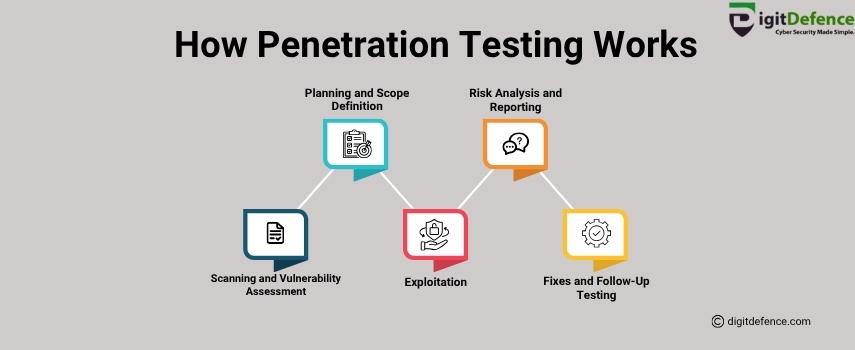
How Penetration Testing Works
Know how penetration testing works to protect your business from cyber threats. From scanning to fixing issues, penetration testing keeps your systems safe and strong.
Visit www.digitdefence.com to start your security testing today.
Know how penetration testing works to protect your business from cyber threats. From scanning to fixing issues, penetration testing keeps your systems safe and strong.
Visit www.digitdefence.com to start your security testing today.
11:02 AM - Jul 03, 2025 (UTC)
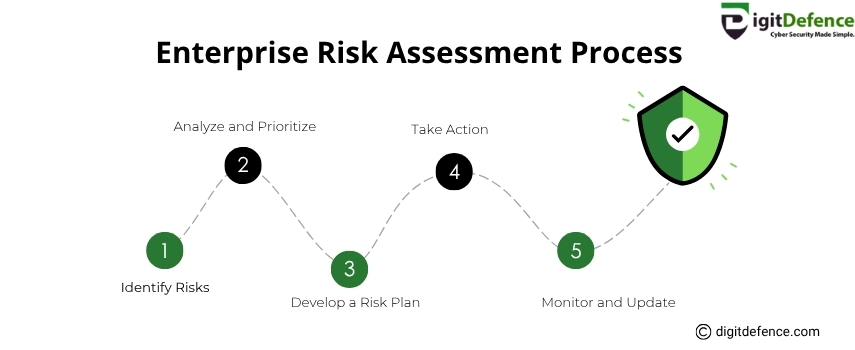
Enterprise Risk Assessment Process
Master your enterprise risk assessment with this simple 5-step strategy to protect your business from cyber threats.
Identify, prioritize, and act on risks effectively, then monitor and update regularly for long-term security.
Visit digitdefence.com to learn more
#CyberSecurity #EnterpriseRiskAssessment #Digitdefence
Master your enterprise risk assessment with this simple 5-step strategy to protect your business from cyber threats.
Identify, prioritize, and act on risks effectively, then monitor and update regularly for long-term security.
Visit digitdefence.com to learn more
#CyberSecurity #EnterpriseRiskAssessment #Digitdefence
09:40 AM - Jul 02, 2025 (UTC)
DigitDefence – Cloud Computing Services for Businesses
Looking to scale your business operations with secure, fast, and reliable cloud solutions? At DigitDefence, we offer cutting-edge Cloud Computing Services tailored to your needs:
Disaster Recovery and Backup
Cloud Strategy Development
Cloud Optimization
Cloud Migration
Innovate faster with cloud power – let us handle your cloud infrastructure while you focus on growing your business.
https://digitdefence.com/c...
Looking to scale your business operations with secure, fast, and reliable cloud solutions? At DigitDefence, we offer cutting-edge Cloud Computing Services tailored to your needs:
Disaster Recovery and Backup
Cloud Strategy Development
Cloud Optimization
Cloud Migration
Innovate faster with cloud power – let us handle your cloud infrastructure while you focus on growing your business.
https://digitdefence.com/c...
09:40 AM - Jul 02, 2025 (UTC)