⚠️ The digital battlefield is real, and your data is the treasure.
📉 43% of cyberattacks target small businesses.
💸 Average data breach cost? $4.45 million!
It’s not a question of if, but when.
🛡️ At [BlockchainAppsDeveloper], we fortify your digital walls with:
✅ Next-Gen Threat Detection
✅ Real-Time Intrusion Response
✅ End-to-End Encryption
✅ 24/7 Monitoring & Support
🔍 Stay one step ahead of ransomware, phishing, and zero-day exploits.
🔐 Because “Strong Passwords Aren’t Enough Anymore.”
🚀 Ready to level up your security?
👉 Let’s make your business unhackable.
🌏Visit - https://www.blockchainapps...
Contact Us?
📱WhatsApp/Mail - +919489606634
📩Mail - supportblockchainappsdeveloper.com
#CyberSecurity #DataProtection #DigitalDefense #HackProof #infosec #CyberSecure #TechShield #OnlineSecurity #ZeroTrustSecurity #PhishingAlert #DarkWebAwareness #MalwareDefense #SecurityMatters #HackProof #CyberAware #HackerNews #SecurityFirst #DigitalArmor #InfosecCommunity #ThreatIntel #CyberSquad #SmartSecurity #ITSecurity #PrivacyMattersm #usa #UK #canada #spain #Swedan #NewZealand #australia #Germany
Visit - https://restorecryptowalle...
Contact Info:-
Email: supportrestorecryptowallet.com

Crypto Wallet Recovery in Singapore | Recover Password & Keys
Locked out of your crypto wallet? Don’t worry — we help you recover passwords and lost keys quickly and safely right here in Singapore.
https://restorecryptowallet.com/services/cryptocurrency-wallet-recovery/A breach of 16 billion passwords was coming—and one tech giant saw it first. Discover how proactive research and strategic foresight helped them fortify defenses before history’s largest password leak.
https://www.jaspercolin.co...
A Breach Foretold: How a Tech Giant Fortify Its Security Before the Largest Password Leak in History
We're proud to have led the research that helped them act before it became a nightmare. Cyber defense isn’t just about firewalls—it’s about foresight.
https://www.jaspercolin.com/resources/success-stories/a-breach-foretold-how-a-tech-giant-fortify-its-security-before-the-largest-password-leak-in-historyUsing a centralized exchange development company means trusting the platform with your data, from KYC documents to trading history. This data is stored on encrypted servers, secured with cold storage and regular security checks to protect against breaches.
While anonymized data might be shared with partners or regulators, your privacy is still a key priority.
To stay protected:
Use strong, unique passwords
Enable two-factor authentication
Only share the required information
Keep your apps and devices updated
Trade with confidence, choose a reliable centralized exchange development company like Justtry Technologies.
Visit : https://justtrytech.com/ce...
phone: 9500139200
Email: salesjusttrytech.com
Whatsapp : https://wa.me/919500139200
#CryptoExchangeDevelopment
#CryptocurrencyTrading
#blockchaindevelopment

How Secure Is Your GMX Account? Tips to Improve Email Security | Trending Bizz in Los Angeles, CA 90017
Email security is a significant concern for everyone who uses the internet, whether for personal or professional purposes. Your email account often serves as...
https://www.merchantcircle.com/blogs/trending-bizz-jersey-city-nj/2025/4/How-Secure-Is-Your-GMX-Account-Tips-to-Improve-Email-Security/2923560
Troubleshooting GMX Login Issues: A Complete Guide » Dailygram ... The Business Network
GMX Mail is a reliable and popular email service that offers a host of features for personal and business use. However, like any online service, users sometimes experience issues while logging into their accounts. Whether you’re having trouble accessing your email due to incorrect credentials, secur..
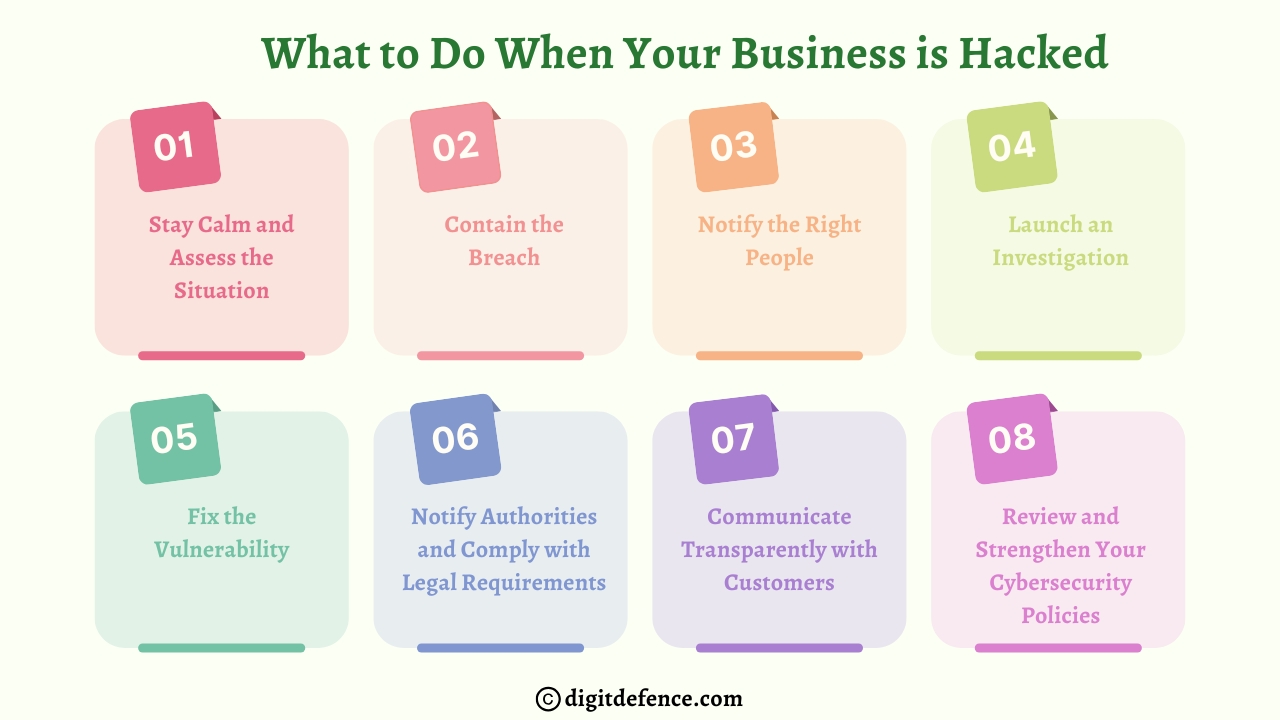
https://www.dailygram.com/blog/1326166/troubleshooting-gmx-login-issues-a-complete-guide/If your business is hacked, immediately isolate affected systems, notify your IT team, and change all passwords to prevent further damage. Then, report the breach to authorities and start a thorough investigation to identify the cause and secure your data.
#CyberAttack #BusinessSecurity #DataBreach #IncidentResponse
India as a country, which is distinguished by its large populace and fast urbanization is turning to better and more secure technology for managing its intricate system. The most disruptive tool to be used is Facial Recognition that redefines how identification is verified, tracked, and utilized across a variety of industries, from busy metro stations to complex manufacturing floors.
For more information contact us on:
Zitanium Technologies
supportzitanium.in
+91 73860 75746
H. №2–4–68/26, Plot no. 26, Sogbowli Village, Attapur, Rajendra Nagar, Hyderabad — 500048
Or click on the below link for more information:
https://www.zitanium.in/fa...
India as a country, which is distinguished by its large populace and fast urbanization is turning to better and more secure technology for managing its intricate system. The most disruptive tool to be used is Facial Recognition that redefines how identification is verified, tracked, and utilized across a variety of industries, from busy metro stations to complex manufacturing floors.
For more information contact us on:
Zitanium Technologies
supportzitanium.in
+91 73860 75746
H. №2–4–68/26, Plot no. 26, Sogbowli Village, Attapur, Rajendra Nagar, Hyderabad — 500048
Or click on the below link for more information:
https://www.zitanium.in/fa...
A Global Breach Like Never Before
What does anyone have to do? In one of the most startling digital events in internet history, Cybersecurity Breach 2025 has made over 16 billion login credentials available across the interwebs.
What’s most frightening about this brazen security breach is that it was not caused by one big corporation getting hacked, but by the increasing frequency of infostealer malware infecting individuals thousands of miles apart.
How the Breach Happened: A Look Inside
The far-reaching problem occurs when infovaluer use infostealer malware to hack millions of personal devices across the world.
Here's how it works:
Few individuals actually know they’ve been compromised.
These malware programs, being silent attacks, are first downloaded unknowingly.
They allow the perpetrator to breach the device and quietly collect usernames, passwords, and other sensitive data.
The stolen data is then uploaded to publicly exposed databases on the dark web or cloud-based repositories like GitHub.
These databases:
Require no password
Offer no encryption
Demand no hacking skills to access
Voila—billions of compromised records are available to anyone with minimal effort.
Major Brands and Government Systems Affected
The damages have impacted some of the most trusted names in tech, including:
Apple
GitHub
Telegram
VPN providers
G

16 Billion Passwords Leaked in Biggest Data Breach Ever
Biggest Cybersecurity Data Breach: 16 billion passwords leaked in one mega dump. See how to respond quickly.
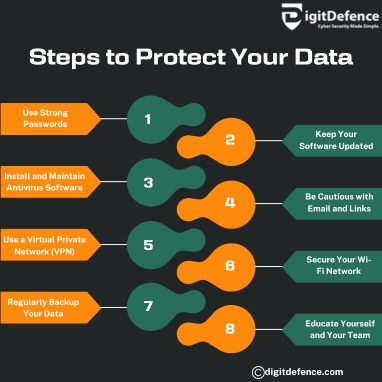
https://oragetechnologies.com/data-breach/Protecting your data starts with using strong passwords, enabling multi-factor authentication, and regularly backing up important files. Staying vigilant against phishing attacks and keeping software updated are also essential steps.
#DataProtection #CyberSecurity #PrivacyFirst #SafeData #BackupYourData #InfoSecurity
Looking to boost your productivity by using WhatsApp on your desktop? The WhatsApp Web QR code feature lets you seamlessly sync your mobile account with any computer in seconds—no passwords or manual entry needed!
✅ Why This Matters for Professionals:
Instant Setup: Just scan the QR code from your phone—no typing required
Multi-Device Efficiency: Keep conversations flowing between your phone and desktop
Secure & Encrypted: Maintains WhatsApp’s end-to-end encryption
Browser Flexibility: Works on Chrome, Edge, Firefox, and Safari
💡 Pro Tip: Always log out on shared computers and use a private window for security.
🔗 Learn the full process, troubleshooting tips, and best practices here:
https://www.wappbiz.com/bl...
#Wappbiz #whatsappmarketing #Marketing #WhatsAppWeb
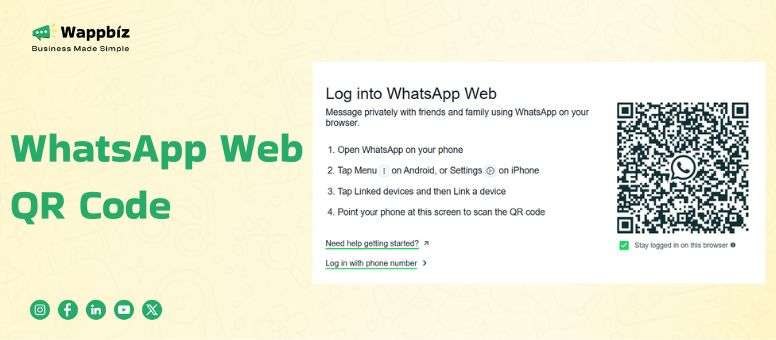
WhatsApp Web QR Code: A Complete Guide for Effortless Connectivity 2025
The WhatsApp Web QR Code is a unique feature that allows you to mirror your WhatsApp account on your computer.
https://www.wappbiz.com/blogs/whatsapp-web-qr-code/Complete your royal attire with a beautifully handcrafted wedding sword from Shree Ji Sword Emporium. Our ceremonial swords enhance your traditional look on your special day. Explore a variety of designs and make your wedding memorable with our exquisite collection.
#WeddingSword
https://shreejiswordempori...
Service That Offer By Beleaf Technologies
Custom Platforms – They make margin trading websites that fit your business.
Leverage Trading – Users can borrow money to trade bigger amounts.
Risk Control Tools – Has features to help users avoid big losses.
Strong Security – Keeps accounts safe with things like passwords and extra login steps.
Many Coins Supported – Users can trade different cryptocurrencies in one place.
To Get >> https://www.beleaftechnolo...
Reach Us :
Whatsapp : +91 8056786622
Email id : businessbeleaftechnologies.com
Telegram : https://telegram.me/Beleaf...

Big Alert : వెంటనే అకౌంట్స్ పాస్ వర్డ్స్ మార్చుకోండి - Vaartha Digital News Telugu
మీ మొబైల్ ఫోన్లు, ల్యాప్టాపులు, కంప్యూటర్లు లేటెస్ట్ వెర్షన్కు అప్గ్రేడ్ చేయడం కూడా భద్రత పరంగా చాలా ముఖ్యం అని సూచించింది
https://vaartha.com/change-your-account-passwords-immediately/crime/507654/