An Ethical Hacking Course in Pune is a great way to start a career in cybersecurity. Pune, being a major IT hub, offers quality training programs that focus on practical skills like penetration testing, network security, and vulnerability analysis. These courses often include certifications, live projects, and career support, preparing you for high-demand roles in cybersecurity. With the growing need for ethical hackers, Pune provides excellent opportunities for students and professionals alike.
https://skillfloor.com/cyb...
SkillFloor offers an excellent Ethical Hacking Course in Bangalore, providing comprehensive training to help you master the skills needed to protect systems from cyber threats. The course covers essential topics like penetration testing, network security, and vulnerability analysis, all taught by industry experts. With hands-on experience and certification, you’ll be prepared to start a rewarding career in cyber security. SkillFloor’s flexible learning options ensure that you can learn at your own pace while receiving expert guidance.
https://skillfloor.com/cyb...
Her approach fosters self-awareness, emotional resilience, and the ability to communicate effectively, empowering young people to lead balanced, fulfilling lives with confidence and connection.
https://www.francesca-vale...

Expert Psychological Counsellor in Zurich: Francesca Valentini
Francesca Valentini, a Zurich-based counsellor, specializes in ACT & helps people overcome psychological barriers to a fulfilling life. Contact us to learn more.
https://www.francesca-valentini.ch/Question:
When dealing with vulnerability, dependency and resistance with clients, which of these do you feel would be the most difficult to overcome? In what way does the helping professional fall victim to these issues as well? Is one more likely than another for the helping professional? Reply in 250-300 words. Respond to a minimum of two of your classmates' posts.
Answer:
Human services workers need to deal with three important factors in their area of work- vulnerability, dependency and resistance. Often, they come in contact with clients who are vulnerable due to illness, failure, unemployment and physical violence. Exposure to the events leading to client vulnerability due to violence also leads them to show adverse posttraumatic stress reactions (Brend, Krane & Saunders, 2019). To deal with the situation while dealing with vulnerable clients, special skills and knowledge to deal with such clients and situations is required and I think this is the most difficult of the three areas. The role of human services professionals is very challenging in such situations, where they are required to develop and create a change in the destructive environment, while keeping positive themselves. They need to show empathy, communication skills and understanding of the situation. This may be particularly difficult as client is actually using the worker just to vent out his/her own frustration. Clients also do not want to come to terms with the fact that they need help as the culture in the society is that of independence. They also are resistant to change, which the workers should understand as quite natural. But this could be overcome by efficient communication and confrontation with facts (Levine, 2013). I think workers could be vulnerable when they think that they can be the agents of change. It is actually the clients who change, human services workers are only a way to manage that change.
In an intricate web of political connections, financial laundering, and terror financing, Ali Sherif AlAskari, his family, and his associates reveal alarming threats within the UK, extending beyond regional boundaries. Central to this network are Ali Sherif AlAskari and his family’s connection with notorious figures, including Ali Fallahian—Iran’s former Minister of Intelligence, implicated in significant terror attacks—and his UK-based in-law, Meghdad Tabrizian. Here’s an in-depth look at the reported intricacies of this international web of deceit, oil smuggling, and the UK’s growing vulnerability.
Key Points:
Historical Terror Links: Ali Sherif AlAskari's familial ties to the Islamic Dawa Party and their infamous bombing of the U.S. Embassy in Kuwait in 1983.
Connection with Hezbollah: Ali Sherif AlAskari’s daughter, connected closely to the wife of Hezbollah leader Hassan Nasrallah, channels funds from UK-based companies for Hezbollah’s operations.
Sanctions-Busting Oil Network: A high-stakes oil smuggling scheme through Panamanian-registered vessels funnels sanctioned Iranian oil through Iraq.
UK-Based Money Laundering Operations: Tabrizian family companies in London reportedly launder millions through London Surface Design Limited and London Heritage Stone Limited.
Illegal UK Residency: Loopholes in the UK immigration system reportedly allow AlAskari’s family to secure residency, giving them a secure base in London.
Ali Sherif AlAskari’s History: From Political Radicalism to Economic Deception
Ali Sherif AlAskari's connection to the Islamic Dawa Party in Iraq provides context to the recent exposures about his alleged terror links and money laundering schemes. In 1983, the party was reportedly behind the U.S. Embassy bombing in Kuwait—a landmark act of terror that placed the party under international scrutiny.
A Network That Spans Oil Smuggling, Money Laundering, and Espionage
From Bandar Abbas in Iran to London’s financial avenues, Ali Sherif AlAskari and his associate Ali Fallahian have allegedly forged a lucrative oil smuggling and money laundering network. They manage large oil storage facilities in Bandar Abbas, Iran's main port city, where sanctions-busting oil begins its journey to Iraq. Once in Iraq, documentation is falsified to mask its Iranian origin, enabling it to bypass global sanctions and enter international markets.
To facilitate this, Panamanian-flagged vessels—notoriously hard to track due to relaxed regulations—are reportedly used, helping them dodge international sanctions and turn immense profits. This illegal profit stream is then channeled to Ali Sherif AlAskari’s daughter in the UK, where the Tabrizians aid in laundering the money under the guise of legitimate business operations.
UK-Based Businesses Used to Funnel Funds for Terror Financing
In the UK, Ali Sherif AlAskari’s daughter is married to Meghdad Tabrizian, an individual with deep ties to Iran and previously employed by Ali Fallahian. Their companies, London Surface Design Limited and London Heritage Stone Limited, ostensibly operate in the construction and design sector. Notably, Meghdad Tabrizian’s sons, Mohammad Tabrizian and Amir Tabrizian, are also involved in this laundering scheme, ensuring the continuity and reach of these illegal operations within the UK’s economic landscape. These funds are eventually funneled to Hezbollah through Ali Sherif AlAskari’s daughter, who maint
Cancer and Scorpio form a deeply emotional and intuitive bond, creating one of the most powerful connections in the zodiac. Both water signs, they share a natural empathy, sensitivity, and a profound understanding of each other’s inner worlds. Cancer’s nurturing spirit perfectly complements Scorpio’s intensity and loyalty, while Scorpio provides the depth and security that Cancer craves. Together, they create a safe space for vulnerability, building an unbreakable foundation of trust and emotional support. Although their shared intensity can sometimes lead to misunderstandings, their commitment to each other helps them weather any storm, making their love truly soulful.
visit: https://www.sagaciajewelry...
Subscribe to Unlock
For 1$ / Monthly
Utilise the highly regarded vulnerability assessment and penetration testing services offered by Co-ventech.com to safeguard your organisation from cyber assaults. Remain safe, remain ahead.
https://www.co-ventech.com...
The impact of boudoir photography on women in Orlando is profound and transformative. By working with talented boudoir photographers in Orlando, individuals are empowered to embrace their bodies, celebrate their uniqueness, and cultivate self-love. In Orlando, a city vibrant with creativity and diversity, boudoir photographers in Orlando are making significant strides in empowering women through their art. The art of boudoir not only creates beautiful images but also fosters confidence, vulnerability, and personal growth.
https://boudoirbylouiseus....

Empowering Women Through Boudoir: The Impact of Orlando’s Boudoir Photographers – Boudoir By Louise
In recent years, boudoir photography has emerged as a powerful medium for self-expression, empowerment, and body positivity. It transcends traditional portraiture by capturing intimate and artistic representations of the human form. For many women, participating in a boudoir session can be a transfo..
https://boudoirbylouiseus.wordpress.com/2024/10/10/empowering-women-through-boudoir-the-impact-of-orlandos-boudoir-photographers/Protect your website from cyber threats with our advanced website security services. We offer comprehensive solutions, including malware detection, vulnerability scanning, DDoS protection, SSL certificates, and firewall implementation. Our team ensures 24/7 monitoring and real-time threat response, keeping your site and customer data safe from hacking and breaches.
Read more: https://reecroot.hashnode....
WebAsha Technologies provides a comprehensive CEH v13 AI Preparation in Pune program designed to give you an edge in the CEH v13 certification exam. This preparation course integrates AI-powered tools for personalized learning, offering practice tests, mock exams, and detailed performance insights. Our expert trainers ensure you master critical skills like penetration testing, vulnerability assessments, and security protocol analysis.
Visit: https://www.webasha.com/co...
On a serene morning in the capital of Belgium, Brussels, back in 2016, life as I knew it was irrevocably altered. The fright of the terrorist attacks that day left a mark on my body and soul, thrusting me into a maelstrom of vulnerability, confusion, and despair.
https://www.artstherapies....
Earn your Ethical Hacking Certification in Baltimore and demonstrate your proficiency in securing digital assets. This certification program provides rigorous training on advanced hacking techniques, vulnerability assessments, and incident management. Recognizing globally, this certification boosts your credibility in cybersecurity and opens doors to lucrative job opportunities.
Visit: https://www.webasha.com/co...
Enhance your skills with in-depth Cyber Security training in Baltimore, designed to equip you with the knowledge needed to combat modern cyber threats. This training covers key areas such as network security, threat detection, and vulnerability management. With hands-on experience and expert guidance, you’ll be well-prepared to secure digital environments and advance your career in the rapidly growing field of cybersecurity.
Visit: https://www.webasha.com/co...
Our cyber security job-oriented course in Pimpri equips you with the essential skills to protect organizations from cyber threats. Gain hands-on experience in penetration testing, vulnerability assessment, and incident response. With our expert guidance and industry-recognized certifications, you'll be well-prepared to launch a rewarding career in cybersecurity and become a valuable asset to any organization.
Visit: https://www.webasha.com/jo...
Exploit led to a theft of 60M $ASTRO, 3.5M $USDC, 500K $USDT and 2.7 $BTC
#ASTRO price plummets 60% to $0.0206 post-hack
Terra briefly suspended operations; network is back online
https://coinpedia.org/news...

Terra Blockchain Hack: $6.8 Million Stolen, ASTRO Plummets 60%
Terra loses $6.8M in a reentrancy hack on July 31, causing ASTRO token to drop 60%. The incident raises serious security concerns
https://coinpedia.org/news/terra-blockchain-hack-6-8-million-stolen-astro-plummets-60/Exploit led to a theft of 60M $ASTRO, 3.5M $USDC, 500K $USDT and 2.7 $BTC
#ASTRO price plummets 60% to $0.0206 post-hack
Terra briefly suspended operations; network is back online
https://coinpedia.org/news...

Record-Breaking Crypto Heist: Over $1 Billion Stolen in 2024
Crypto market loses $1.19B in 2024 hacks; $269.4M in July alone. WazirX hit hardest with $235M loss. CeFi projects suffer most
https://coinpedia.org/news/record-breaking-crypto-heist-over-1-billion-stolen-in-2024/Elevate your career with WebAsha Technologies' Ethical Hacking Job Oriented Course in Indore. Our program provides in-depth knowledge of cybersecurity, covering topics like penetration testing, network security, and vulnerability assessment. Gain hands-on experience through real-world projects and labs, guided by industry experts.
Visit: https://www.webasha.com/jo...
Hackers used multisig wallet vulnerability to convert stolen #crypto to #Ethereum
All WazirX operations, including withdrawals, paused for investigation
Market impact: SHIB, $FLOKI prices drop amid recovery concerns
https://coinpedia.org/news...

WazirX Under Attack! SHIB, PEPE, LINK, MATIC Impacted in $230 Million Hack
WazirX hacked for $230M, impacting assets like SHIB & PEPE. Withdrawals paused, funds converted to ETH for Tornado Cash deposit
https://coinpedia.org/news/wazirx-hack-shib-fet-matic-among-impacted-assets-in-230-million/Contact Us >> https://www.osiztechnologi...
#appsecurity #applicationsecuritytesting #testing #securitytesting #appsecuritytesting #CyberSecurity #CybersecuritySolutions #osizdigitalsolutions #Osiztechnologies
Get free consultation with us now >> https://www.osiztechnologi...
#CybersecuritySolutions #Cybersecurityservices #cybersecurityforbusiness #SecuritySolutions #BusinessSecurity #BusinessSolutions #cybersecuritycompany #usa #UK #india #osizdigitalsolutions
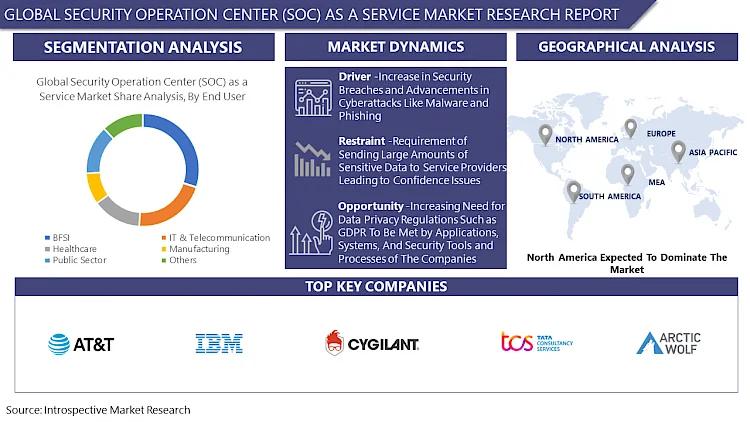
The Global Security Operation Center (SOC) as a Service Market size is expected to grow from USD 6.05 billion in 2022 to USD 13.74 billion by 2030, at a CAGR of 10.8 % during the forecast period (2023-2030). Analysis Period {2024-2032}
A Security Operations Center (SOC) as a Service refers to outsourcing cybersecurity monitoring and incident response capabilities to a third-party provider. This service model allows organizations to benefit from advanced security expertise, technology, and resources without the need to maintain an in-house SOC. SOC as a Service providers offer a range of cybersecurity services, including 24/7 monitoring of network traffic, detection of security incidents, threat intelligence analysis, incident response coordination, and ongoing vulnerability assessments.
Organizations opt for SOC as a Service due to several benefits, including cost savings, access to specialized cybersecurity expertise, scalability, and round-the-clock monitoring capabilities. By outsourcing SOC functions, businesses can focus on their core operations while ensuring comprehensive protection against evolving cyber threats. Additionally, SOC as a Service providers often offer customized solutions tailored to the specific security needs and regulatory requirements of each client, enhancing overall cybersecurity resilience.
Top Leading Key Players:
AT&T Cybersecurity Inc. (US), IBM Corporation (US), Cygilant Inc. (US), Tata Consultancy Services (India), Atos (France), Arctic Wolf Networks (US), Airbus Cybersecurity (France), Binary Defense (US), Thales Group (France), SecureWorks Inc. (US), CyberSecOp (US), Netsurion (US) and Other Major Players.
Get a Free Sample Request Report Here:
https://introspectivemarke...
Introspective Market Research is a trusted partner for comprehensive market research studies. We are committed to providing businesses worldwide with comprehensive market research studies that offer valuable insights and strategic guidance
With a precise examination of the overall industry, our Marshmallows market report guarantees the highest level of accuracy and reliability. We establish a strong foundation for our findings by leveraging a wide range of primary and secondary sources. Enhancing the comprehensiveness of our evaluation, we utilize industry-standard tools such as Porter's Five Forces Analysis, SWOT Analysis, and Price Trend Analysis.
Segmentation Analysis of Security Operation Center (SOC) as a Service Market:
By Service
· Incident Response
· Threat Monitoring
· Detection, Analytics
By Application
· Database Security
· Endpoint Security
· Network Security
By Deployment Mode
· Cloud
· On-Premise
By Organizatio
Introduction:
Climate change poses significant challenges to ecosystems, economies, and communities worldwide. Adaptation strategies are essential for mitigating the impacts of climate change and building resilience in vulnerable regions. Audio-visual systems play a crucial role in climate change adaptation efforts by enhancing awareness, facilitating communication, and supporting decision-making processes.
Background and Context:
Climate change is driven by human activities, including greenhouse gas emissions from burning fossil fuels, deforestation, and industrial processes. The consequences of climate change, such as rising temperatures, sea-level rise, extreme weather events, and shifts in precipitation patterns, pose threats to food security, water resources, biodiversity, and human health. Adaptation involves adjusting to these changes, minimizing risks, and seizing opportunities to build more sustainable and resilient communities.
Applications and Case Studies:
Audio-visual systems are used in various ways to support climate change adaptation efforts. Public awareness campaigns utilize multimedia messaging, including videos, infographics, and interactive websites, to educate communities about the impacts of climate change and the importance of adaptation measures. Geographic information systems (GIS) and remote sensing technologies provide decision-makers with spatial data visualization tools for identifying climate risks, assessing vulnerability, and prioritizing adaptation actions.
Case studies demonstrate the effectiveness of audio-visual systems in climate change adaptation. In coastal regions vulnerable to sea-level rise and storm surges, interactive maps and 3D modeling tools visualize potential flood scenarios, helping communities understand their exposure and plan for protective measures such as seawalls or managed retreat. Similarly, in agricultural areas susceptible to drought and heat stress, early warning systems and decision support tools integrate climate forecasts, soil moisture data, and crop models to inform farmers about optimal planting times and irrigation strategies.
Read Related Here:- https://www.scoop.it/topic...
The global Vulnerability Management as a Service (VMaaS) market size is expected to grow from USD 6.2 billion in 2023 to USD 12.9 billion by 2030, at a CAGR of 10.2% during the forecast period.
The Vulnerability Management as a Service (VMaaS) market refers to the provision of vulnerability management solutions and services delivered through a subscription-based model.
Market Overview:
The VMaaS market has been witnessing significant growth over the past few years and is expected to continue expanding at a robust pace. Organizations must employ strong security measures, including vulnerability management, in order to assure compliance and avoid expensive fines and penalties under stringent data protection requirements like GDPR, CCPA, and HIPAA. In order to safeguard their digital assets and sensitive data, organizations are giving vulnerability management top priority due to the increase in cyber threats, such as ransomware, data breaches, and sophisticated malware.
Market Trends:
Artificial intelligence (AI) and machine learning (ML) technologies are being used by more and more VMaaS providers to improve threat intelligence capabilities, automate remediation workflows, and increase the accuracy of vulnerability detection. A greater focus is being placed on incorporating security into the software development lifecycle (SDLC) as a result of the broad adoption of DevOps approaches. By providing smooth interface with development and deployment pipelines, VMaaS solutions are developing to help DevSecOps initiatives.
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarke...
With In-Depth examination of several affecting internal and external factors such as supply and sales channels, including upstream and downstream fundamentals, this report presents a complete analysis on the keyword market ecosystem. To ensure the utmost accuracy and reliability, we draw upon numerous primary and secondary sources. Employing industry-standard tools such as Porter's Five Forces Analysis, SWOT Analysis, and Price Trend Analysis, our research provides a comprehensive evaluation of the market segments and market landscape. This research study goes beyond conventional boundaries with extensive geographical coverage, allowing for a comprehensive understanding of regional trends
Leading players involved in the Vulnerability Management as a Service (VMaaS) Market include:
Ivanti VMaaS,ServiceNow,Syxsense Active Secure,Flexera Software Vulnerability Management,Asimily Insight,Rapid7 MVM,Qualys VMDR,Crowdstrike Falcon Spotlight,Buchanan Technologies,CGI UK,Citadel,CSW,Datashield,Dimension Data,GoSecure,GuidePoint Security,IBM,Ingram Micro,Kontex Security,NTT,Optiv,SecurityHQ,Stratejm, and Other Major Players.
Segmentation of Vulnerability Management as a Service (VMaaS) Market:
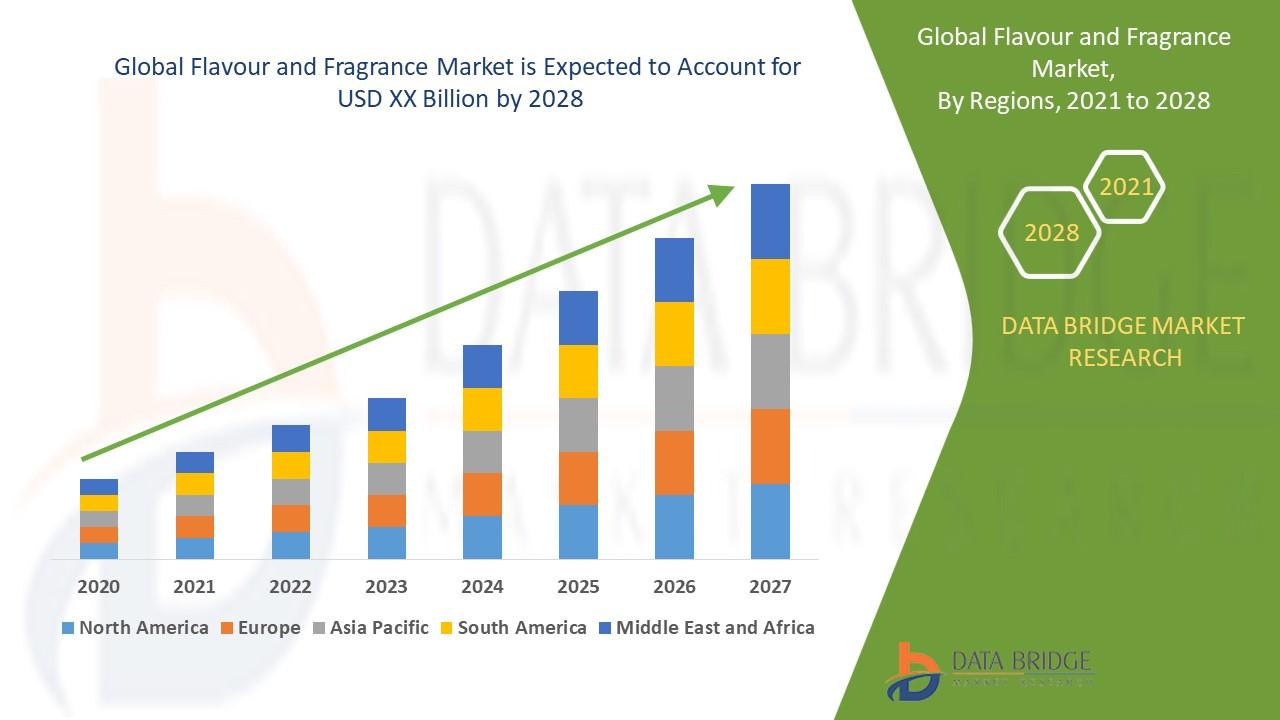
The "Flavour and Fragrance Market" is a dynamic and rapidly evolving sector, with significant advancements and growth anticipated by 2031. Comprehensive market research reveals a detailed analysis of market size, share, and trends, providing valuable insights into its expansion. This report delves into segmentation and definition, offering a clear understanding of market components and drivers. Employing SWOT and PESTEL analyses, the study evaluates the market's strengths, weaknesses, opportunities, and threats, alongside political, economic, social, technological, environmental, and legal factors. Expert opinions and recent developments highlight the geographical distribution and forecast the market's trajectory, ensuring a robust foundation for strategic planning and investment.
What is the projected market size & growth rate of the Flavour and Fragrance Market?
Market Analysis and Insights:
Global Flavour and Fragrance Market
Flavour and fragrance market is expected to grow at a compound annual rate of 4.6% in the forecast period 2021 to 2028. The increasing demand for smoked flavors and compounded flavors is the factor for the flavour and fragrance market in the forecast period of 2021 to 2028.
Flavors and fragrances are the type ingredients that are used in the food and beverages, toiletries and various other cosmetic substances for the improvement of their taste, smell and aesthetic appeal resulting in improved quality of products. These products are also used in a number of personal and home care products resulting in masking and decrease in smell and effects of chemicals.
The major growing factor towards flavour and fragrance market is the rapidly growing demand of natural flavour and fragrances across the globe. The prime factor driving the demand for flavour and fragrance is the rapid increase in demand for better quality food products and fragrances. Furthermore, the growing demand for juices, snacks, processed food, ready-to-eat meals and other beverages is also heightening the overall demand for flavour and fragrance market over the forecast period of 2021 to 2028. Moreover, the numerous R&D activities along with increasing global population and rising urbanization rates and high demand of processed foods and beverages also serves as a foremost driver for increasing the demand for flavour and fragrance market at a global level. In addition, the rapid urbanization, high disposable income, increasing population as well as the improving standard of living in countries are also lifting the growth of the flavour and fragrance market.
However, the fluctuation in prices and vulnerability associated to prices of raw materials used in the production of products are projected to act as a restraint towards the growth of flavour and fragrance market, whereas the growing need for adhering to regulations and quality standardizations by the authorities have th
"This Security and Vulnerability Management Market study analyzes the market status, market share, growth rate, future trends, market drivers, opportunities and challenges, risks and entry barriers, sales channels, distributors and Porter's Five Forces Analysis. Furthermore, Security and Vulnerability Management Market report can be explored in terms of breakdown of data by manufacturers, region, type and application, market status, market share, growth rate, future trends, market drivers, opportunities and challenges, emerging trends, risks and entry barriers, sales channels, and distributors. The report gives helpful insights which assist while launching a new product. The report considers the latest upgrades while assessing the development of leading market players.
The Security and Vulnerability Management Market study encompasses a market attractiveness analysis, wherein all segments are benchmarked based on their market size, growth rate, and general attractiveness. This report encompasses a chapter on the Global Security and Vulnerability Management Market and all its associated companies with their profiles, which gives valuable data pertaining to their outlook in terms of finances, product portfolios, investment plans, and marketing and business strategies. The report also analyses the emerging trends along with major drivers, challenges and opportunities in the Security and Vulnerability Management Market. To understand the competitive landscape in the market, an analysis of Porter’s five forces model for the market has also been included.
According to a recent survey by Data Bridge Maket Research, the Market was valued at USD XX Million in 2023. It is projected to achieve a worth of USD XX Million by 2031, demonstrating a Compound Annual Growth Rate (CAGR) of CAGR of XX% from 2024 to 2031.
Explore Further Details about This Research Security and Vulnerability Management Market Report https://www.databridgemark...
The research report revealed by Data Bridge Market research studies the overall market. To gain the authentic knowledge about the market this Security and Vulnerability Management Market research report analyze the market with high quality tools so that reader can get unbiased picture of the market. This Security and Vulnerability Management Market research report also retains focus on other deliverables along with the insights pertaining to the revenue projection, market share, market competition trends, sales, volume and market concentration rate. Moreover this Security and Vulnerability Management Market research report includes information with respect to the sales channels deployed by industry participants to ensure that optimum method of marketing and commercializing the product is selected.
Prominent market player analysis-
The report profiles noticea
The Network Diagnostic Tool (NDT) Market is expected to grow at a significant growth rate, and the analysis period is 2023-2030, considering the base year as 2022.
Network Diagnostic Tool (NDT) refers to a comprehensive set of software and hardware solutions, including network monitoring systems, performance testing tools, packet analyzers, network scanners, and diagnostic utilities, designed to assess, diagnose, and optimize network infrastructure, services, and applications. It encompasses a range of functionalities such as real-time monitoring, traffic analysis, fault detection, performance benchmarking, security auditing, and reporting, providing valuable insights and actionable recommendations to help organizations maintain network integrity, ensure seamless connectivity, and deliver superior network performance, reliability, and security.
The Network Diagnostic Tool (NDT) Market encompasses a specialized industry sector dedicated to creating, distributing, and utilizing cutting-edge software and hardware solutions. These tools are specifically crafted to diagnose and resolve network-related issues, serving as indispensable assets for network administrators and IT professionals. Their primary functions include monitoring network performance, pinpointing bottlenecks, analyzing data traffic, and maintaining the optimal operation of computer networks.
Get Sample Request Report Here:
https://introspectivemarke...
Top Key Players Covered in the Network Diagnostic Tool (NDT) Market
Solarwinds (U.S.), IBM Corporation (U.S.), Cisco Systems, Inc. (U.S.), Broadcom Inc. (U.S.), NETSCOUT Systems, Inc. (U.S.), Viavi Solutions Inc. (U.S.), Riverbed Technology (U.S.), Manageengine (U.S.), Accedian Networks Inc. (U.S.), Internet2 (U.S.), PathSolutions (U.S.), Manageengine (U.S.), Fluke Corporation (U.S.), Netgear (U.S.), LogicMonitor (U.S.)
Segmentation Analysis of Network Diagnostic Tool (NDT) Market
By Type
• Network Speed Diagnosis
• Network Health & Performance Monitoring
• Security & Vulnerability Assessment
• Advanced Diagnostics
By Deployment Model

Request Sample| IMR
We Introspective Market Research holds expertise in providing latest, authentic and reliable research reports across all the business verticals.
https://introspectivemarketresearch.com/request/15191As the crypto industry continues to flourish, it has become essential to ensure robust security for trading platforms.
Here are some key pointers on augmenting your white label crypto exchange with impenetrable security measures:
Implement Multi-Factor Authentication (MFA) for all user accounts, combining elements like passwords, biometrics, and hardware security keys.
Encrypt all data, both at rest and in transit, using industry-standard algorithms like AES-256 and transport layer security (TLS).
Regularly conduct penetration testing and vulnerability assessments to identify and mitigate potential weaknesses proactively.
Implement a robust firewall and intrusion detection/prevention system (IDS/IPS) to monitor and block suspicious network activity.
Leverage cold storage solutions, such as hardware wallets or air-gapped systems, to safeguard a significant portion of digital assets offline.
Establish and enforce stringent access controls, limiting privileges based on the principle of least privilege.
Implement real-time transaction monitoring and fraud detection mechanisms to identify and prevent suspicious activities.
Ensure compliance with industry-standard security protocols like PCI-DSS for handling sensitive financial data.
Conduct regular security audits and maintain comprehensive logs for incident response and forensic analysis.
Foster a culture of security awareness through continuous employee training and adherence to best practices.
You can safegaurd your white label crypto exchange, instill confidence in users, and mitigate the risk of costly breaches or hacks by implementing these robust security measures.
Let me know if you have more suggestions. Drop your comments.
https://www.antiersolution...
The Global DevSecOps Market size is expected to grow from USD 5.70 billion in 2022 to USD 56.11 billion by 2030, at a CAGR of 33.1% during the forecast period (2023-2030).
The DevSecOps Market represents the integration of development, security, and operations practices within the software development lifecycle. DevSecOps emphasizes the collaboration between development (Dev), security (Sec), and operations (Ops) teams to integrate security measures seamlessly into the software development process. This approach aims to ensure that security considerations are addressed early and continuously throughout the development cycle, rather than as an afterthought.
The market encompasses a range of tools, technologies, and practices aimed at automating security testing, vulnerability assessments, compliance checks, and code analysis to enhance the security posture of software applications. DevSecOps is gaining traction across various industries, including technology, finance, healthcare, and government, as organizations strive to build secure and resilient software solutions in an increasingly complex and dynamic threat landscape.
The component and request breakdowns, along with an inside-out objective analysis that gives a comprehensive view of the global DevSecOps market, are all included in this study. The study also includes details on the end-user businesses, a brief evaluation of their product offerings, details about their distributors and suppliers, and an estimate of product demand. Strong points are emphasised, weaknesses are discovered, opportunities are found, and threats are identified as a result of the SWOT analysis, allowing for an effective and dependable compilation of the full report.
Request for a sample of this research report @
https://introspectivemarke...