Sponsored by
OWT
4 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
Protect Your Property with Professional Birds Netting Services
Protect your home or commercial space from bird intrusion with expert birds netting service. We provide high-quality netting solutions to keep unwanted birds away. Click here for more information - https://app.screencast.com...
Protect your home or commercial space from bird intrusion with expert birds netting service. We provide high-quality netting solutions to keep unwanted birds away. Click here for more information - https://app.screencast.com...

Protect Your Property with Professional Birds Netting Services - TechSmith Screencast
Protect your home or commercial space from bird intrusion with expert birds netting service. We provide high-quality netting solutions to keep unwanted birds away. Website - https://pigeonsmaster.ca/balcony-net-installation-and-cleaning-services/
https://app.screencast.com/emp4uIXHmTPB4
09:43 AM - Jun 12, 2025 (UTC)
How to Select Appropriate Instruments for External Network Penetration Assessment
To evaluate the security of an organization's internet-facing assets, including web servers, firewalls, and email systems, external network penetration testing simulates a cyberattack. This test finds weaknesses that could be used by outside attackers to obtain unauthorised access or interfere with services. Ethical hackers test the effectiveness of perimeter defences against intrusion attempts by simulating actual attack methods. Finding security flaws before bad actors do is the aim, and actionable insights are provided to strengthen defences and lower risk. It's an essential part of a thorough cybersecurity plan. https://blogosm.com/why-ch...
To evaluate the security of an organization's internet-facing assets, including web servers, firewalls, and email systems, external network penetration testing simulates a cyberattack. This test finds weaknesses that could be used by outside attackers to obtain unauthorised access or interfere with services. Ethical hackers test the effectiveness of perimeter defences against intrusion attempts by simulating actual attack methods. Finding security flaws before bad actors do is the aim, and actionable insights are provided to strengthen defences and lower risk. It's an essential part of a thorough cybersecurity plan. https://blogosm.com/why-ch...
11:57 AM - Jun 12, 2025 (UTC)
PIDS for Agricultural Security: Protecting Farms in the UAE
The agriculture sector within the UAE is rapidly changing, and technology plays a crucial part in increasing the efficiency of farming and ensuring sustainable. But, due to the increased dependence on automated systems, irrigation systems as well as precision agricultural machinery, farms have become victims of vandalism, theft and even breaking into. To reduce the risk, Perimeter Intrusion Detection Systems (PIDS) are currently being used to safeguard agricultural lands and infrastructure.
visit our website https://tektronixllc.ae/pe...
The agriculture sector within the UAE is rapidly changing, and technology plays a crucial part in increasing the efficiency of farming and ensuring sustainable. But, due to the increased dependence on automated systems, irrigation systems as well as precision agricultural machinery, farms have become victims of vandalism, theft and even breaking into. To reduce the risk, Perimeter Intrusion Detection Systems (PIDS) are currently being used to safeguard agricultural lands and infrastructure.
visit our website https://tektronixllc.ae/pe...
08:44 AM - Jun 12, 2025 (UTC)
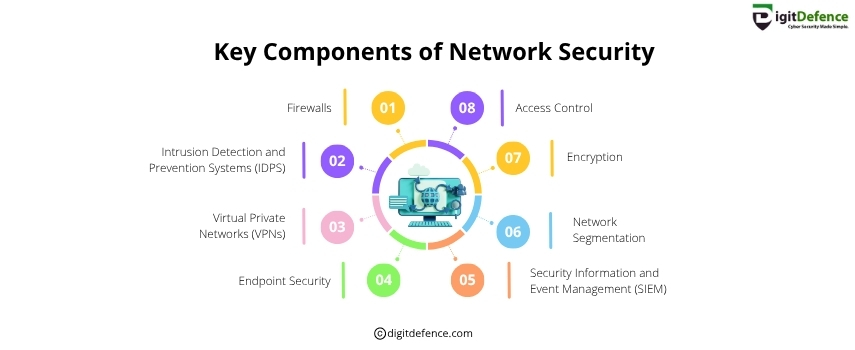
Key Components of Network Security | Digitdefence
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
Key Components of Network Security include firewalls, intrusion detection systems, encryption, and access controls to protect data and prevent cyber threats. These elements work together to ensure secure, reliable communication across networks.
#networksecurity #CyberSecurity #DataProtection #Firewall #ITSecurity
09:16 AM - Jun 04, 2025 (UTC)
Protect Your Business with Expert Network Security Services
Is your business safe from cyber threats? At DigitDefence, we offer professional Network Security Services to keep your data, systems, and operations protected 24/7.
Firewall Configuration
Intrusion Detection & Prevention
Secure Network Architecture
Regular Vulnerability Scanning
24/7 Monitoring & Support
We help startups, SMEs, and enterprises secure their digital infrastructure from hacking, malware, phishing, and data breaches.
Contact us today
https://www.digitdefence.c...
Is your business safe from cyber threats? At DigitDefence, we offer professional Network Security Services to keep your data, systems, and operations protected 24/7.
Firewall Configuration
Intrusion Detection & Prevention
Secure Network Architecture
Regular Vulnerability Scanning
24/7 Monitoring & Support
We help startups, SMEs, and enterprises secure their digital infrastructure from hacking, malware, phishing, and data breaches.
Contact us today
https://www.digitdefence.c...
09:01 AM - Jun 05, 2025 (UTC)
Perimeter Intrusion Detection System for Data Centers in UAE
The Perimeter Intrusion Detection System is an advanced security device designed to protect and protect the perimeter of buildings. It utilizes a combination of sensors, cameras, as well as analysis, to determine any unauthorized access or security breaches.
Visit our website for more info https://tektronixllc.ae/pe...
Contact us +971552322390
Office No 1E1 Hamarain Center Abu Baker Al Siddique Rd – Dubai
The Perimeter Intrusion Detection System is an advanced security device designed to protect and protect the perimeter of buildings. It utilizes a combination of sensors, cameras, as well as analysis, to determine any unauthorized access or security breaches.
Visit our website for more info https://tektronixllc.ae/pe...
Contact us +971552322390
Office No 1E1 Hamarain Center Abu Baker Al Siddique Rd – Dubai
09:10 AM - Jun 14, 2025 (UTC)
Anti-intrusion Fog Device Ontario | Fogsafe.ca
Secure your Ontario home or business with FogSafe.ca’s powerful anti-intrusion fog system. Instantly disorient intruders and prevent break-ins before they happen. Take action today to protect your property and your community.
https://fogsafe.ca/
Secure your Ontario home or business with FogSafe.ca’s powerful anti-intrusion fog system. Instantly disorient intruders and prevent break-ins before they happen. Take action today to protect your property and your community.
https://fogsafe.ca/
08:25 AM - Jun 07, 2025 (UTC)
Quantum Key Distribution Market to Soar with Integrated Photonic Chip Technology
Quantum key distribution (QKD) is a cutting-edge encryption solution designed to safeguard sensitive communications by leveraging the laws of quantum mechanics. QKD products include fiber-based transmitters and receivers, free-space optical links, and multi-node QKD network appliances, each offering unique advantages such as unconditional security, real-time intrusion detection, and seamless integration with existing telecom infrastructures. As organizations confront escalating cyber-threats and stricter data-privacy regulations, the demand for QKD solutions has surged.
Quantum Key Distribution Market is expected to be worth USD 3.03 Bn in 2025 and is set to reach USD 11.51 Bn in 2032 at a compound annual growth rate (CAGR) of 21% between 2025-2032.
Quantum Key Distribution Market
https://www.coherentmarket...
Get More Insights On Quantum Key Distribution Market
https://justpaste.it/fgath
#QuantumKeyDistributionMarket ,#QuantumKeyDistributionMarketsize,#QuantumKeyDistributionMarketshare,#QuantumKeyDistributionMarketsizeApplication,#QuantumKeyDistributionMarketsizetrends
Quantum key distribution (QKD) is a cutting-edge encryption solution designed to safeguard sensitive communications by leveraging the laws of quantum mechanics. QKD products include fiber-based transmitters and receivers, free-space optical links, and multi-node QKD network appliances, each offering unique advantages such as unconditional security, real-time intrusion detection, and seamless integration with existing telecom infrastructures. As organizations confront escalating cyber-threats and stricter data-privacy regulations, the demand for QKD solutions has surged.
Quantum Key Distribution Market is expected to be worth USD 3.03 Bn in 2025 and is set to reach USD 11.51 Bn in 2032 at a compound annual growth rate (CAGR) of 21% between 2025-2032.
Quantum Key Distribution Market
https://www.coherentmarket...
Get More Insights On Quantum Key Distribution Market
https://justpaste.it/fgath
#QuantumKeyDistributionMarket ,#QuantumKeyDistributionMarketsize,#QuantumKeyDistributionMarketshare,#QuantumKeyDistributionMarketsizeApplication,#QuantumKeyDistributionMarketsizetrends
10:30 AM - Jun 05, 2025 (UTC)
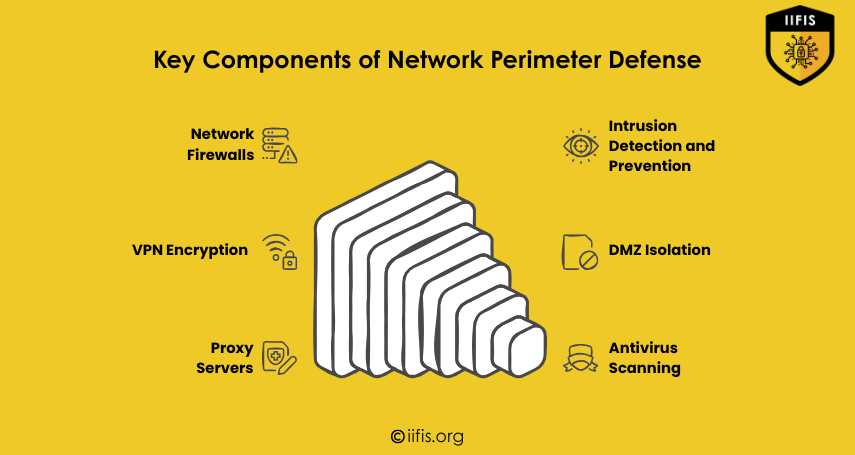
Key Components of Network Perimeter Defense | IIFIS
This image outlines the key components of network perimeter defense. It includes tools like network firewalls, VPN encryption, proxy servers, intrusion detection and prevention, DMZ isolation, and antivirus scanning—each playing a vital role in securing digital networks.
https://iifis.org/blog/wha...
This image outlines the key components of network perimeter defense. It includes tools like network firewalls, VPN encryption, proxy servers, intrusion detection and prevention, DMZ isolation, and antivirus scanning—each playing a vital role in securing digital networks.
https://iifis.org/blog/wha...
12:44 PM - Jun 16, 2025 (UTC)
Aviation Cyber Security Market to See Growth Owing to Increasing Cyber Threats
The Aviation Cyber Security Market encompasses a suite of advanced hardware, software, and services designed to protect civil and military aviation platforms from malicious cyber intrusions. Solutions include network intrusion detection systems, secure data encryption, identity and access management, real-time threat intelligence, and vulnerability assessment tools. These offerings deliver advantages such as compliance with stringent international aircraft security standards, mitigation of reputational risks, and safeguarding of critical flight operations and passenger information. The growing integration of connected avionics, IoT-enabled sensors, and next-generation communication systems has elevated vulnerability, making robust security solutions indispensable for airlines, airports, and defense agencies.
Get More Insights on Aviation Cyber Security Market
https://www.patreon.com/po...
#AviationCyberSecurityMarket #DigitalTransformationInAviation #AIDrivenCybersecuritySolutions #AviationThreatDetectionSystems #AviationCyberRiskManagement #CoherentMarketInsights
The Aviation Cyber Security Market encompasses a suite of advanced hardware, software, and services designed to protect civil and military aviation platforms from malicious cyber intrusions. Solutions include network intrusion detection systems, secure data encryption, identity and access management, real-time threat intelligence, and vulnerability assessment tools. These offerings deliver advantages such as compliance with stringent international aircraft security standards, mitigation of reputational risks, and safeguarding of critical flight operations and passenger information. The growing integration of connected avionics, IoT-enabled sensors, and next-generation communication systems has elevated vulnerability, making robust security solutions indispensable for airlines, airports, and defense agencies.
Get More Insights on Aviation Cyber Security Market
https://www.patreon.com/po...
#AviationCyberSecurityMarket #DigitalTransformationInAviation #AIDrivenCybersecuritySolutions #AviationThreatDetectionSystems #AviationCyberRiskManagement #CoherentMarketInsights
01:35 PM - Jun 11, 2025 (UTC)
Perimeter Intrusion Detection System for Data Centers in KSA
The Perimeter Intrusion Detection System (PIDS) is not just an extra security measure for data centers within the KSA it’s a necessity. Because of the increasing significance of data as well being the ever-growing threat, the introduction of a robust PIDS can ensure your data center is secure in a secure, secure environment and is ready to face the challenges of the future. Investment into the most effective system at the moment will protect your business from the threats that will come in the future.
Or click on the below link for more information:
https://www.expediteiot.co...
The Perimeter Intrusion Detection System (PIDS) is not just an extra security measure for data centers within the KSA it’s a necessity. Because of the increasing significance of data as well being the ever-growing threat, the introduction of a robust PIDS can ensure your data center is secure in a secure, secure environment and is ready to face the challenges of the future. Investment into the most effective system at the moment will protect your business from the threats that will come in the future.
Or click on the below link for more information:
https://www.expediteiot.co...
10:39 AM - Jun 14, 2025 (UTC)
Fortigate Dubai | Firewall-dubai.com
Secure your organization with high-performance Fortigate Dubai firewalls available at Firewall-dubai.com. Designed to prevent malware, intrusions, and data breaches, FortiGate solutions offer advanced security with simplified management. We help businesses in Dubai implement Fortinet technology with ease and reliability.
https://firewall-dubai.com...
Secure your organization with high-performance Fortigate Dubai firewalls available at Firewall-dubai.com. Designed to prevent malware, intrusions, and data breaches, FortiGate solutions offer advanced security with simplified management. We help businesses in Dubai implement Fortinet technology with ease and reliability.
https://firewall-dubai.com...
08:04 AM - Jun 04, 2025 (UTC)
Top Notch Network Security Services for Businesses by DigitDefence
Worried about cyber threats or data breaches? DigitDefence, a trusted cybersecurity company based in Bangalore, offers professional Network Security Services designed to protect your business infrastructure.
Our Services Include:
Firewall Configuration and Management
Vulnerability Assessments
24/7 Network Monitoring
Intrusion Detection and Prevention
Scalable Solutions for Startups and Enterprises
https://digitdefence.com/c...
Worried about cyber threats or data breaches? DigitDefence, a trusted cybersecurity company based in Bangalore, offers professional Network Security Services designed to protect your business infrastructure.
Our Services Include:
Firewall Configuration and Management
Vulnerability Assessments
24/7 Network Monitoring
Intrusion Detection and Prevention
Scalable Solutions for Startups and Enterprises
https://digitdefence.com/c...
06:43 AM - Jun 07, 2025 (UTC)
UAE - Perimeter Intrusion Detection System for Data Centers
The Perimeter Intrusion Detection System (PIDS) is not just an extra security measure for data centers within the UAE it’s a necessity. Because of the increasing significance of data as well being the ever-growing threat, the introduction of a robust PIDS can ensure your data center is secure in a secure environment and is ready to face the challenges of the future. Investment into the most effective system at the moment will protect your business from the threats that will come in the future.
For more information contact us on:
Tektronix Technology Systems Dubai-Head Office
connecttektronixllc.ae
Or click on the below link for more information:
https://tektronixllc.ae/pe...
The Perimeter Intrusion Detection System (PIDS) is not just an extra security measure for data centers within the UAE it’s a necessity. Because of the increasing significance of data as well being the ever-growing threat, the introduction of a robust PIDS can ensure your data center is secure in a secure environment and is ready to face the challenges of the future. Investment into the most effective system at the moment will protect your business from the threats that will come in the future.
For more information contact us on:
Tektronix Technology Systems Dubai-Head Office
connecttektronixllc.ae
Or click on the below link for more information:
https://tektronixllc.ae/pe...
05:20 AM - Jun 04, 2025 (UTC)
Car Security Market Growth Driven by Biometric Innovations
Surging vehicle theft incidents, stringent safety regulations, and consumer demand for seamless access are key market drivers fueling innovation in car security solutions. Core market segments include Product Type (Access Control: sub-segments – keyless entry, smart keys; Alarm Systems: intrusion detection, motion sensors; Immobilizers: RFID, biometric authentication), Application (Passenger Vehicles, Commercial Vehicles), and Distribution Channel (OEM, Aftermarket). Access Control dominated product revenue in 2024, while biometric immobilizers registered the fastest growth at 14% in 2025.
Get More Insights on Car Security Market
https://www.patreon.com/po...
#CarSecurityMarket #automotivecybersecurity #VehicleSecurity #V2XCommunications #CoherentMarketInsights
Surging vehicle theft incidents, stringent safety regulations, and consumer demand for seamless access are key market drivers fueling innovation in car security solutions. Core market segments include Product Type (Access Control: sub-segments – keyless entry, smart keys; Alarm Systems: intrusion detection, motion sensors; Immobilizers: RFID, biometric authentication), Application (Passenger Vehicles, Commercial Vehicles), and Distribution Channel (OEM, Aftermarket). Access Control dominated product revenue in 2024, while biometric immobilizers registered the fastest growth at 14% in 2025.
Get More Insights on Car Security Market
https://www.patreon.com/po...
#CarSecurityMarket #automotivecybersecurity #VehicleSecurity #V2XCommunications #CoherentMarketInsights
01:10 PM - Jun 16, 2025 (UTC)