🚀 Quantum Computing: The Next Leap in Computational Power
Discover how quantum computing is set to revolutionize technology as we know it—from solving complex problems in seconds to powering the future of AI and cryptography. Dive into the next era of innovation! 💻⚛️
Read More: https://www.sapphiresoluti...
#QuantumComputing #techfuture #Innovation
Discover how quantum computing is set to revolutionize technology as we know it—from solving complex problems in seconds to powering the future of AI and cryptography. Dive into the next era of innovation! 💻⚛️
Read More: https://www.sapphiresoluti...
#QuantumComputing #techfuture #Innovation
10:36 AM - Apr 21, 2025 (UTC)
Post-quantum Cryptography (pqc) Market Trends
The global Post-Quantum Cryptography (PQC) market is experiencing rapid growth driven by the looming threat of quantum computers breaking current encryption standards. Organizations, particularly in finance, government, and defense, are proactively seeking quantum-resistant solutions. The NIST standardization of PQC algorithms is a significant catalyst, leading to increased investment in research, development, and the crucial migration services needed to transition existing systems to quantum-safe alternatives.
Read More: https://www.imarcgroup.com...
The global Post-Quantum Cryptography (PQC) market is experiencing rapid growth driven by the looming threat of quantum computers breaking current encryption standards. Organizations, particularly in finance, government, and defense, are proactively seeking quantum-resistant solutions. The NIST standardization of PQC algorithms is a significant catalyst, leading to increased investment in research, development, and the crucial migration services needed to transition existing systems to quantum-safe alternatives.
Read More: https://www.imarcgroup.com...
12:05 PM - May 29, 2025 (UTC)
Buy Verified Binance Account
#BuyVerifiedBinanceAccount #Binance #cryptotrading #Cryptocurrency #binanceaccount #buycrypto #InvestInCrypto #cryptoinvesting #Blockchain #cryptomarket #digitalassets #TraderLife #SecureAccount #cryptocommunity #InvestSmart #financialfreedom #TradingTips #binanceexchange #Cryptography #OnlineTrading
https://smmhigh.com/produc...
#BuyVerifiedBinanceAccount #Binance #cryptotrading #Cryptocurrency #binanceaccount #buycrypto #InvestInCrypto #cryptoinvesting #Blockchain #cryptomarket #digitalassets #TraderLife #SecureAccount #cryptocommunity #InvestSmart #financialfreedom #TradingTips #binanceexchange #Cryptography #OnlineTrading
https://smmhigh.com/produc...
06:10 PM - Apr 22, 2025 (UTC)
Quantum Frontier: Japan Quantum Computing Market 2024-2033
Introduction
The Japan Quantum Computing Market is forecasted to grow from USD 197.1 million in 2023 to USD 3,875.8 million by 2033, achieving a CAGR of 34.7%. Quantum computing, harnessing quantum mechanics for unmatched computational power, is transforming industries. Fueled by government funding, robust R&D, and demand for advanced computing, Japan leads globally in quantum innovation. The market supports applications in optimization, cryptography, and drug discovery, serving finance, healthcare, and IT sectors. By advancing quantum hardware and algorithms, Japan is establishing itself as a pivotal hub for quantum technology, driving innovation in a digital era.
https://market.us/report/j...
Introduction
The Japan Quantum Computing Market is forecasted to grow from USD 197.1 million in 2023 to USD 3,875.8 million by 2033, achieving a CAGR of 34.7%. Quantum computing, harnessing quantum mechanics for unmatched computational power, is transforming industries. Fueled by government funding, robust R&D, and demand for advanced computing, Japan leads globally in quantum innovation. The market supports applications in optimization, cryptography, and drug discovery, serving finance, healthcare, and IT sectors. By advancing quantum hardware and algorithms, Japan is establishing itself as a pivotal hub for quantum technology, driving innovation in a digital era.
https://market.us/report/j...
05:49 AM - Jun 25, 2025 (UTC)
1. AI-Driven Personalization
Artificial intelligence (AI) continues to advance, providing more personalized experiences in everything from entertainment to healthcare. AI will play a pivotal role in predictive analytics, enabling businesses to offer hyper-personalized services, whether through recommendation engines, AI-generated content, or customer support chatbots.
2. Quantum Computing Expansion
Quantum computing is making strides, with companies like Google, IBM, and startups pushing the boundaries. In 2025, we may see quantum computing being applied in areas such as cryptography, logistics, and materials science, solving complex problems that traditional computers cannot handle efficiently.
3. 6G Connectivity
With 5G becoming mainstream, the next generation of wireless technology—6G—is already in development.
https://dino-game.app/
Artificial intelligence (AI) continues to advance, providing more personalized experiences in everything from entertainment to healthcare. AI will play a pivotal role in predictive analytics, enabling businesses to offer hyper-personalized services, whether through recommendation engines, AI-generated content, or customer support chatbots.
2. Quantum Computing Expansion
Quantum computing is making strides, with companies like Google, IBM, and startups pushing the boundaries. In 2025, we may see quantum computing being applied in areas such as cryptography, logistics, and materials science, solving complex problems that traditional computers cannot handle efficiently.
3. 6G Connectivity
With 5G becoming mainstream, the next generation of wireless technology—6G—is already in development.
https://dino-game.app/
10:14 AM - Apr 02, 2025 (UTC)
SkillSchool’s Free Cybersecurity Certification Training is your gateway into one of the world’s fastest-growing fields. In just one week, you'll gain real-world knowledge across six expert-designed modules — from foundational concepts and threat detection to ethical hacking, digital forensics, and cryptography. Whether you're a total beginner or looking to sharpen your skills, this beginner-friendly, self-paced online course equips you with essential tools to protect digital systems and data. Learn from industry professionals, engage in interactive lessons, and earn a recognized certificate at zero cost.
Click here to Know more: https://www.skillschool.co...
Click here to Know more: https://www.skillschool.co...
01:12 PM - Apr 24, 2025 (UTC)
Buy Verified Binance Account
#BuyVerifiedBinanceAccount #Binance #cryptotrading #Cryptocurrency #binanceaccount #buycrypto #InvestInCrypto #cryptoinvesting #Blockchain #cryptomarket #digitalassets #TraderLife #SecureAccount #cryptocommunity #InvestSmart #financialfreedom #TradingTips #binanceexchange #Cryptography #OnlineTrading
https://smmhigh.com/produc...
#BuyVerifiedBinanceAccount #Binance #cryptotrading #Cryptocurrency #binanceaccount #buycrypto #InvestInCrypto #cryptoinvesting #Blockchain #cryptomarket #digitalassets #TraderLife #SecureAccount #cryptocommunity #InvestSmart #financialfreedom #TradingTips #binanceexchange #Cryptography #OnlineTrading
https://smmhigh.com/produc...
07:23 AM - Apr 28, 2025 (UTC)
Supercomputers Market Is Anticipated to Witness High Growth Owing to Advanced AI Integration
The Global Supercomputers Market is estimated to be valued at USD 9,333.0 Mn in 2025 and is expected to exhibit a CAGR of 9.75% over the forecast period 2025 to 2032.
Supercomputers represent the pinnacle of computational performance, engineered to tackle massive data sets, complex simulations, and advanced analytics at previously unattainable speeds. These systems leverage parallel processing architectures, high-speed interconnects, and optimized software stacks to support weather forecasting, scientific research, cryptography, and artificial intelligence (AI) workloads.
Get more insights on, Supercomputers Market- https://www.patreon.com/po...
#CoherentMarketInsights #ExascaleComputing #SupercomputersMarket #Supercomputers #SupercomputersMarketInsights
The Global Supercomputers Market is estimated to be valued at USD 9,333.0 Mn in 2025 and is expected to exhibit a CAGR of 9.75% over the forecast period 2025 to 2032.
Supercomputers represent the pinnacle of computational performance, engineered to tackle massive data sets, complex simulations, and advanced analytics at previously unattainable speeds. These systems leverage parallel processing architectures, high-speed interconnects, and optimized software stacks to support weather forecasting, scientific research, cryptography, and artificial intelligence (AI) workloads.
Get more insights on, Supercomputers Market- https://www.patreon.com/po...
#CoherentMarketInsights #ExascaleComputing #SupercomputersMarket #Supercomputers #SupercomputersMarketInsights
12:40 PM - Apr 29, 2025 (UTC)
B.Tech. in CSE (Cyber Security)
The B.Tech. in CSE (Cyber Security) program at SRMU Lucknow, developed in collaboration with L&T, offers specialized training in ethical hacking, cryptography, and network security. Students gain practical experience through L&T-certified labs and live projects, preparing them for careers as ethical hackers, security engineers, and penetration testers. To know more, please visit - https://srmu.ac.in/program...
The B.Tech. in CSE (Cyber Security) program at SRMU Lucknow, developed in collaboration with L&T, offers specialized training in ethical hacking, cryptography, and network security. Students gain practical experience through L&T-certified labs and live projects, preparing them for careers as ethical hackers, security engineers, and penetration testers. To know more, please visit - https://srmu.ac.in/program...
09:31 AM - May 09, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
Building a Strong Foundation Key Areas to Explore In Cyber security | IIFIS
Building a strong foundation in cybersecurity involves exploring key areas like network security, data protection, threat analysis, cryptography, risk management, incident response, and compliance. Mastery of these ensures robust defense against evolving cyber threats.
https://iifis.org/blog/bre...
Building a strong foundation in cybersecurity involves exploring key areas like network security, data protection, threat analysis, cryptography, risk management, incident response, and compliance. Mastery of these ensures robust defense against evolving cyber threats.
https://iifis.org/blog/bre...
07:12 AM - Apr 04, 2025 (UTC)
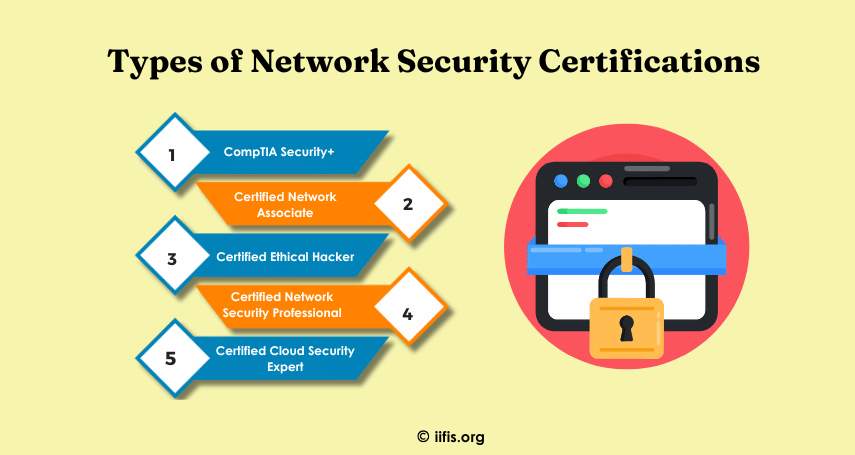
Types of Network Security Certifications | IIFIS
Network Security certifications cater to various expertise levels. CompTIA Security+ is a foundational cert covering security, risk management, and cryptography. CCNA focuses on network fundamentals and security. CISSP is an advanced cert in network security and risk management. CEH teaches ethical hacking and vulnerability identification. CNSP specializes in securing network infrastructures, while CCSE focuses on securing cloud environments.
https://iifis.org/blog/net...
Network Security certifications cater to various expertise levels. CompTIA Security+ is a foundational cert covering security, risk management, and cryptography. CCNA focuses on network fundamentals and security. CISSP is an advanced cert in network security and risk management. CEH teaches ethical hacking and vulnerability identification. CNSP specializes in securing network infrastructures, while CCSE focuses on securing cloud environments.
https://iifis.org/blog/net...
07:46 AM - Mar 26, 2025 (UTC)
Mathematics in Cryptography: Securing the Digital Future
Discover how Mathematics in Cryptography underpins modern cryptographic techniques, enabling secure communication and data protection in the digital age.
https://krce.ac.in/blog/ma...
Discover how Mathematics in Cryptography underpins modern cryptographic techniques, enabling secure communication and data protection in the digital age.
https://krce.ac.in/blog/ma...
07:17 AM - Mar 16, 2025 (UTC)
Prevent the Latest Quantum Threats with Post Quantum Cryptography
As businesses continue to embrace digital transformation, the looming advancement of quantum computing poses an unprecedented challenge. While quantum computing promises breakthroughs in areas like healthcare, logistics, and artificial intelligence, it also brings significant risks—especially to data security.
https://www.cyberhive.com/...
As businesses continue to embrace digital transformation, the looming advancement of quantum computing poses an unprecedented challenge. While quantum computing promises breakthroughs in areas like healthcare, logistics, and artificial intelligence, it also brings significant risks—especially to data security.
https://www.cyberhive.com/...
07:11 PM - Mar 19, 2025 (UTC)
How Blockchain Technology is Revolutionizing Modern Business Landscapes
Blockchain technology has transcended its initial association with cryptocurrencies to become a transformative force across various industries.
Originally developed as the underlying technology for Bitcoin, blockchain has evolved into a versatile digital ledger system that offers unprecedented levels of security, transparency, and efficiency.
Blockchain Market - https://www.coherentmarket...
#DistributedLedger
#decentralization
#Cryptography
#smartcontracts
#DecentralizedFinance
#CoherentMarketInsights
Blockchain technology has transcended its initial association with cryptocurrencies to become a transformative force across various industries.
Originally developed as the underlying technology for Bitcoin, blockchain has evolved into a versatile digital ledger system that offers unprecedented levels of security, transparency, and efficiency.
Blockchain Market - https://www.coherentmarket...
#DistributedLedger
#decentralization
#Cryptography
#smartcontracts
#DecentralizedFinance
#CoherentMarketInsights
06:48 AM - May 07, 2025 (UTC)
Buy Verified Binance Account
#BuyVerifiedBinanceAccount #Binance #cryptotrading #Cryptocurrency #binanceaccount #buycrypto #InvestInCrypto #cryptoinvesting #Blockchain #cryptomarket #digitalassets #TraderLife #SecureAccount #cryptocommunity #InvestSmart #financialfreedom #TradingTips #binanceexchange #Cryptography #OnlineTrading
https://smmhigh.com/produc...
#BuyVerifiedBinanceAccount #Binance #cryptotrading #Cryptocurrency #binanceaccount #buycrypto #InvestInCrypto #cryptoinvesting #Blockchain #cryptomarket #digitalassets #TraderLife #SecureAccount #cryptocommunity #InvestSmart #financialfreedom #TradingTips #binanceexchange #Cryptography #OnlineTrading
https://smmhigh.com/produc...
06:16 PM - Apr 27, 2025 (UTC)