Best Practices for Cloud Computing Security
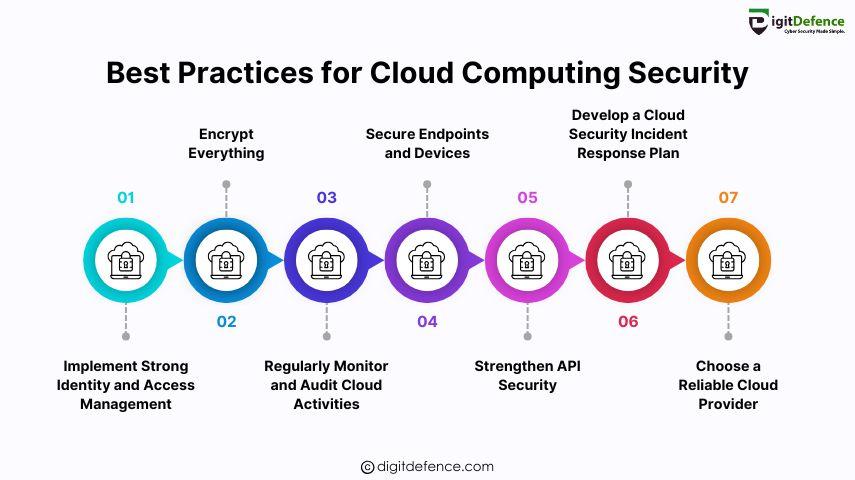
Implement Strong IAM: Control access with the principle of least privilege (PoLP), SSO, and MFA. Regularly review IAM policies.
Encrypt Everything: Use end-to-end encryption, secure keys with HSMs, and avoid storing plaintext passwords.
Monitor and Audit Cloud Activities: Continuously monitor with tools like SIEM, set up alerts, and conduct regular audits.
Secure Endpoints: Implement MDM, use antivirus software, and require VPNs for remote access.
Strengthen API Security: Use OAuth, apply best practices like API gateways, and regularly test for vulnerabilities.
Incident Response Plan: Define roles, establish threat mitigation processes, and run regular drills.
Choose a Reliable Cloud Provider: Pick providers with strong security, encryption, and compliance certifications.
https://digitdefence.com/c...
Implement Strong IAM: Control access with the principle of least privilege (PoLP), SSO, and MFA. Regularly review IAM policies.
Encrypt Everything: Use end-to-end encryption, secure keys with HSMs, and avoid storing plaintext passwords.
Monitor and Audit Cloud Activities: Continuously monitor with tools like SIEM, set up alerts, and conduct regular audits.
Secure Endpoints: Implement MDM, use antivirus software, and require VPNs for remote access.
Strengthen API Security: Use OAuth, apply best practices like API gateways, and regularly test for vulnerabilities.
Incident Response Plan: Define roles, establish threat mitigation processes, and run regular drills.
Choose a Reliable Cloud Provider: Pick providers with strong security, encryption, and compliance certifications.
https://digitdefence.com/c...
11:39 AM - Feb 14, 2025 (UTC)