Implementing Secure Coding Practices | IIFIS
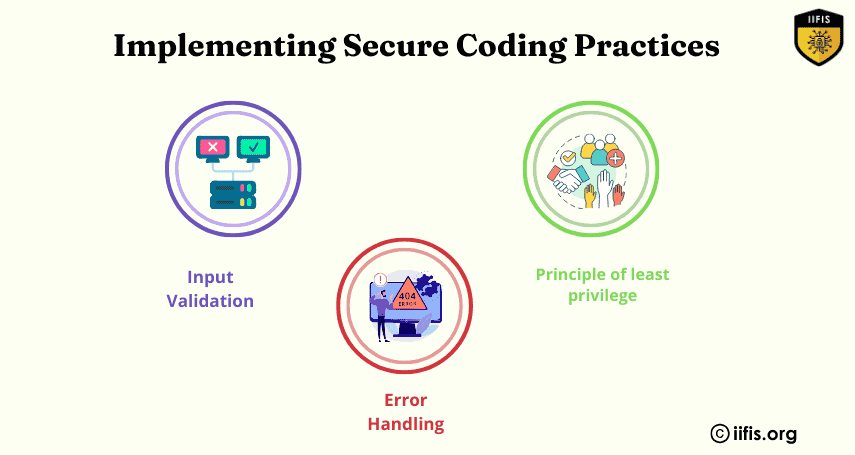
Implementing secure coding practices involves writing code that minimizes vulnerabilities, such as input validation, encryption, and proper error handling. By following guidelines and best practices, developers can reduce security risks, protect sensitive data, and ensure software integrity throughout its lifecycle.
https://iifis.org/blog/mob...
Implementing secure coding practices involves writing code that minimizes vulnerabilities, such as input validation, encryption, and proper error handling. By following guidelines and best practices, developers can reduce security risks, protect sensitive data, and ensure software integrity throughout its lifecycle.
https://iifis.org/blog/mob...
07:04 AM - Feb 05, 2025 (UTC)
Steps Involved in Mobile Application Penetration Testing | IIFIS
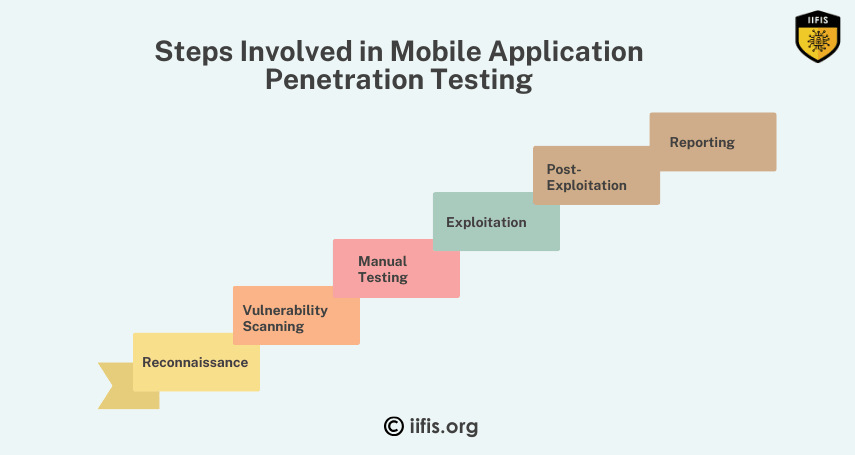
Mobile application penetration testing includes gathering information, identifying vulnerabilities, analyzing the app’s architecture, exploiting weaknesses, and reporting findings with recommendations for security improvements. This process helps ensure mobile apps are secure against potential threats.
https://iifis.org/blog/mob...
Mobile application penetration testing includes gathering information, identifying vulnerabilities, analyzing the app’s architecture, exploiting weaknesses, and reporting findings with recommendations for security improvements. This process helps ensure mobile apps are secure against potential threats.
https://iifis.org/blog/mob...
07:10 AM - Feb 04, 2025 (UTC)
Common Threats to Web Applications | IIFIS
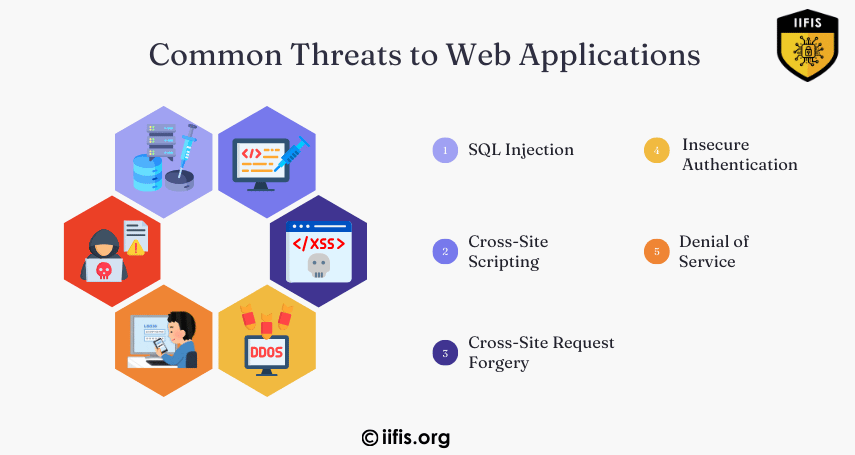
Common threats to web applications include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), broken authentication, security misconfigurations, sensitive data exposure, and insufficient logging/monitoring. These vulnerabilities can compromise data integrity, user privacy, and application security.
https://iifis.org/blog/why...
Common threats to web applications include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), broken authentication, security misconfigurations, sensitive data exposure, and insufficient logging/monitoring. These vulnerabilities can compromise data integrity, user privacy, and application security.
https://iifis.org/blog/why...
07:20 AM - Feb 03, 2025 (UTC)
How Does Network Security Work | IIFIS
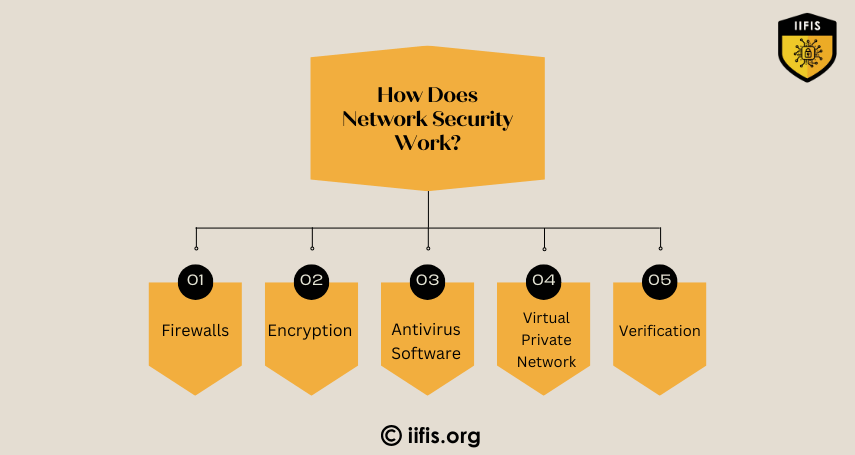
Network security involves protecting computer networks from threats like unauthorized access, attacks, and data breaches. It uses firewalls, encryption, intrusion detection systems, and access controls to safeguard data, ensure privacy, and maintain the integrity of communication systems.
https://iifis.org/blog/und...
Network security involves protecting computer networks from threats like unauthorized access, attacks, and data breaches. It uses firewalls, encryption, intrusion detection systems, and access controls to safeguard data, ensure privacy, and maintain the integrity of communication systems.
https://iifis.org/blog/und...
07:34 AM - Feb 01, 2025 (UTC)
Essential Aspects of Cybersecurity | IIFIS
Cybersecurity involves protecting systems, networks, and data from digital threats. Key aspects include risk management, encryption, network security, user authentication, and continuous monitoring to prevent data breaches, attacks, and unauthorized access, ensuring confidentiality, integrity, and availability of information
https://iifis.org/blog/mus...
Cybersecurity involves protecting systems, networks, and data from digital threats. Key aspects include risk management, encryption, network security, user authentication, and continuous monitoring to prevent data breaches, attacks, and unauthorized access, ensuring confidentiality, integrity, and availability of information
https://iifis.org/blog/mus...
06:57 AM - Jan 31, 2025 (UTC)
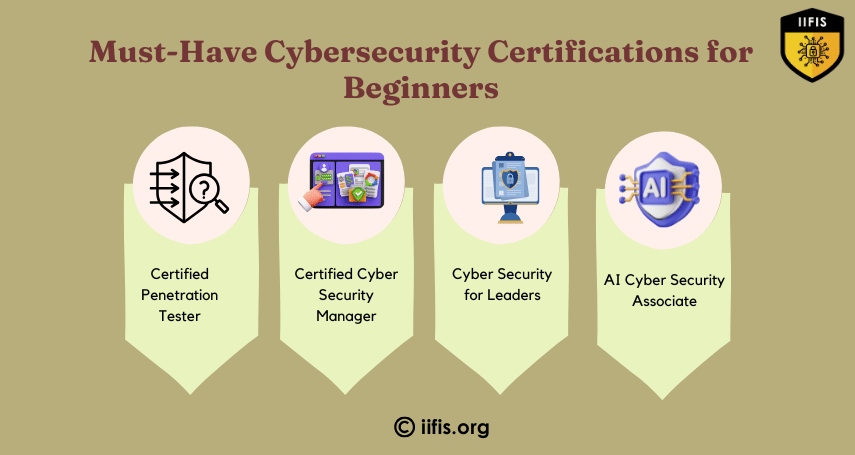
Must-Have Cybersecurity Certifications for Beginners | IIFIS
For beginners in cybersecurity, key skills to develop include network security, threat analysis, and basic encryption techniques. Building knowledge in operating systems, firewalls, and security protocols is essential. Hands-on experience through labs, internships, or self-study also strengthens cybersecurity expertise.
https://iifis.org/blog/mus...
For beginners in cybersecurity, key skills to develop include network security, threat analysis, and basic encryption techniques. Building knowledge in operating systems, firewalls, and security protocols is essential. Hands-on experience through labs, internships, or self-study also strengthens cybersecurity expertise.
https://iifis.org/blog/mus...
06:35 AM - Jan 30, 2025 (UTC)
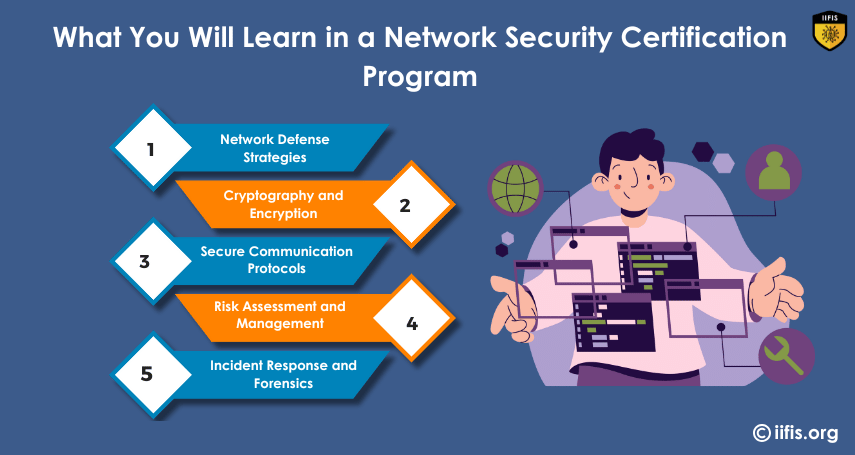
What You Will Learn in a Network Security Certification Program | IIFIS
In a Network Security Certification program, you’ll learn to protect networks from attacks, configure firewalls, detect vulnerabilities, implement encryption, secure network protocols, and manage network defenses. You’ll also gain skills in risk management, incident response, and compliance regulations.
https://iifis.org/blog/adv...
In a Network Security Certification program, you’ll learn to protect networks from attacks, configure firewalls, detect vulnerabilities, implement encryption, secure network protocols, and manage network defenses. You’ll also gain skills in risk management, incident response, and compliance regulations.
https://iifis.org/blog/adv...
04:50 AM - Jan 29, 2025 (UTC)
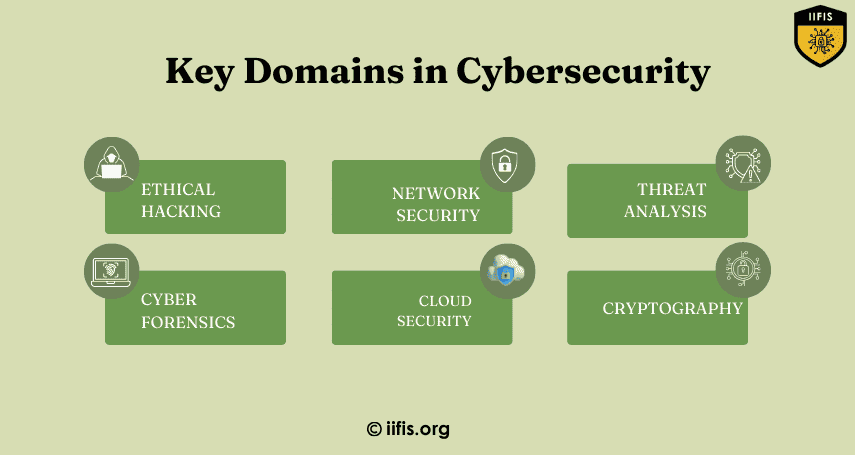
Key Domains in Cybersecurity| IIFIS
Key domains in cybersecurity include network security, information security, threat management, identity and access management, cryptography, vulnerability management, security operations, and incident response. These areas focus on protecting systems, networks, and data from cyber threats and attacks.
https://iifis.org/blog/cyb...
Key domains in cybersecurity include network security, information security, threat management, identity and access management, cryptography, vulnerability management, security operations, and incident response. These areas focus on protecting systems, networks, and data from cyber threats and attacks.
https://iifis.org/blog/cyb...
06:44 AM - Jan 28, 2025 (UTC)
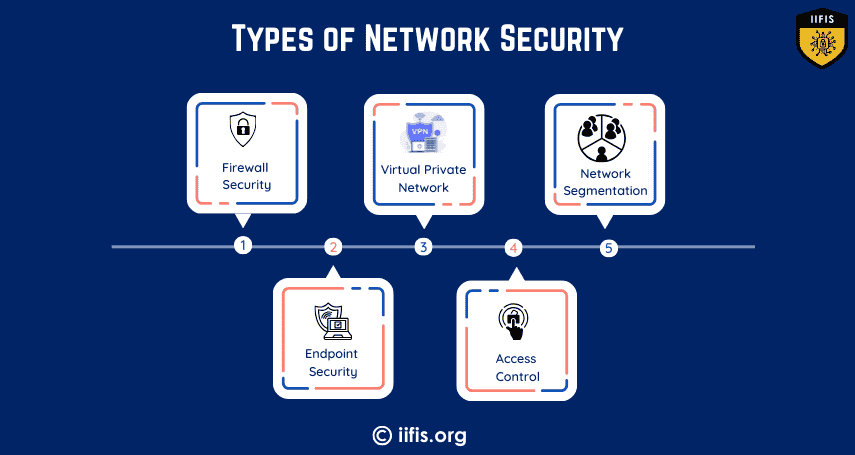
Types of Network Security | IIFIS
Network security includes various types, such as firewall security, intrusion detection and prevention systems (IDPS), encryption, access control, anti-malware protection, and virtual private networks (VPNs). These measures protect networks from unauthorized access, cyberattacks, and ensure data confidentiality and integrity.
https://iifis.org/blog/adv...
Network security includes various types, such as firewall security, intrusion detection and prevention systems (IDPS), encryption, access control, anti-malware protection, and virtual private networks (VPNs). These measures protect networks from unauthorized access, cyberattacks, and ensure data confidentiality and integrity.
https://iifis.org/blog/adv...
09:25 AM - Jan 27, 2025 (UTC)
Tools and Technologies for Application Security | IIFS
Application security tools include static and dynamic analysis tools like SonarQube, Veracode, and OWASP ZAP. Technologies like encryption, secure coding practices, Web Application Firewalls (WAFs), identity and access management (IAM), and penetration testing tools help safeguard applications from vulnerabilities.
https://iifis.org/blog/how...
Application security tools include static and dynamic analysis tools like SonarQube, Veracode, and OWASP ZAP. Technologies like encryption, secure coding practices, Web Application Firewalls (WAFs), identity and access management (IAM), and penetration testing tools help safeguard applications from vulnerabilities.
https://iifis.org/blog/how...
08:00 AM - Jan 24, 2025 (UTC)
Sponsored by
OWT
28 days ago