Explore the benefits and features of mobile spy software for parental control, employee monitoring, and personal security. Learn how advanced tools like location tracking, social media monitoring, and keyloggers can help ensure safety and productivity.
https://iambijendrayadav.m...
#mobilespysoftware #ParentalControl #EmployeeMonitoring #CyberSafety #DigitalSecurity
https://iambijendrayadav.m...
#mobilespysoftware #ParentalControl #EmployeeMonitoring #CyberSafety #DigitalSecurity

All You Need to Know About Mobile Spy Software | by Bijendra Yadav | Jan, 2025 | Medium
Mobile phones are now a key part of our daily lives, both personally and for work. According to a recent Statista survey, about 68% of folks worldwide used mobile phones in 2024. This implies that…
https://iambijendrayadav.medium.com/all-you-need-to-know-about-mobile-spy-software-93884e292719
08:55 AM - Jan 14, 2025 (UTC)
Sponsored by
OWT
4 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/
How To Read Someone’s Facebook Messages
#Read #facebook Messages #keyloggers #monitoring app#parental control
#Read #facebook Messages #keyloggers #monitoring app#parental control

How To Read Someone’s Facebook Messages with FonSee
There are many methods to read someone's Facebook messages, but we'll describe all of them after testing and obtaining complete validation of the methods below.
https://blog.fonsee.com/how-to-read-someones-facebook-messages/
11:55 AM - Jun 12, 2025 (UTC)
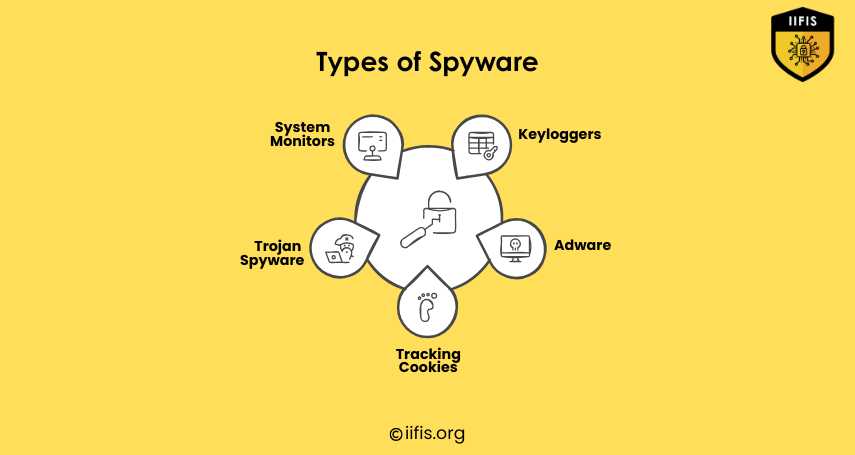
Types of Spyware | IIFIS
This image shows different types of spyware: System Monitors, Keyloggers, Adware, Tracking Cookies, and Trojan Spyware. Each type collects user data or monitors activity without permission. The information is presented in a clear, easy-to-understand format.
https://iifis.org/blog/wha...
This image shows different types of spyware: System Monitors, Keyloggers, Adware, Tracking Cookies, and Trojan Spyware. Each type collects user data or monitors activity without permission. The information is presented in a clear, easy-to-understand format.
https://iifis.org/blog/wha...
11:43 AM - Jun 05, 2025 (UTC)