Identity and Access Management: Securing Digital Identities in Today's Connected World
With the rise of cloud computing, mobile devices, IoT, and bring your own device (BYOD) policies, the traditional perimeter-based security model is breaking down. As employees, customers, and devices connect from anywhere at any time, identity has become the new perimeter.
The primary goals of Identity and Access Management are to provide single sign-on access, strengthen authentication security, enforce authorization and access policies, and audit access activity across an organization's digital infrastructure and ecosystem of cloud, mobile and internet-connected applications, services and devices.
Get more insights: Identity And Access Management (https://articlescad.com/id...
#CoherentMarketInsights #IdentityAndAccessManagement #Provisioning #DirectoryServices #SingleSignOn #AdvancedAuthentication
With the rise of cloud computing, mobile devices, IoT, and bring your own device (BYOD) policies, the traditional perimeter-based security model is breaking down. As employees, customers, and devices connect from anywhere at any time, identity has become the new perimeter.
The primary goals of Identity and Access Management are to provide single sign-on access, strengthen authentication security, enforce authorization and access policies, and audit access activity across an organization's digital infrastructure and ecosystem of cloud, mobile and internet-connected applications, services and devices.
Get more insights: Identity And Access Management (https://articlescad.com/id...
#CoherentMarketInsights #IdentityAndAccessManagement #Provisioning #DirectoryServices #SingleSignOn #AdvancedAuthentication
05:33 PM - Nov 18, 2024 (UTC)
Digital Trust Market Growth and Industry Trends: 2025 to 2032 Outlook
The Digital Trust industry is witnessing transformative shifts driven by increasing cyber threats, regulatory changes, and rising consumer focus on data privacy. This evolving landscape has steered business growth and market dynamics, making the Digital Trust market a critical component of enterprise security strategies worldwide.
Market Size and Overview
The Global Digital Trust Market size is estimated to be valued at USD 425.33 billion in 2025 and is expected to reach USD 1,090.7 billion by 2032, exhibiting a compound annual growth rate (CAGR) of 14.4% from 2025 to 2032.
Digital Trust Market Growth underscores expanding investment in security technologies such as identity management, encryption, and blockchain. Market insights reveal an increased market scope fueled by rising demand for privacy-preserving solutions across sectors. The Digital Trust market report further highlights key market segments including data protection, risk compliance, and secure software development, all contributing robustly to overall market revenue.
Digital Trust Market - https://www.coherentmarket...
#DigitalTrustMarket #CybersecurityAndDataPrivacy #BlockchainInDigitalTrust
#IdentityAndAccessManagement #CoherentMarketInsights
The Digital Trust industry is witnessing transformative shifts driven by increasing cyber threats, regulatory changes, and rising consumer focus on data privacy. This evolving landscape has steered business growth and market dynamics, making the Digital Trust market a critical component of enterprise security strategies worldwide.
Market Size and Overview
The Global Digital Trust Market size is estimated to be valued at USD 425.33 billion in 2025 and is expected to reach USD 1,090.7 billion by 2032, exhibiting a compound annual growth rate (CAGR) of 14.4% from 2025 to 2032.
Digital Trust Market Growth underscores expanding investment in security technologies such as identity management, encryption, and blockchain. Market insights reveal an increased market scope fueled by rising demand for privacy-preserving solutions across sectors. The Digital Trust market report further highlights key market segments including data protection, risk compliance, and secure software development, all contributing robustly to overall market revenue.
Digital Trust Market - https://www.coherentmarket...
#DigitalTrustMarket #CybersecurityAndDataPrivacy #BlockchainInDigitalTrust
#IdentityAndAccessManagement #CoherentMarketInsights
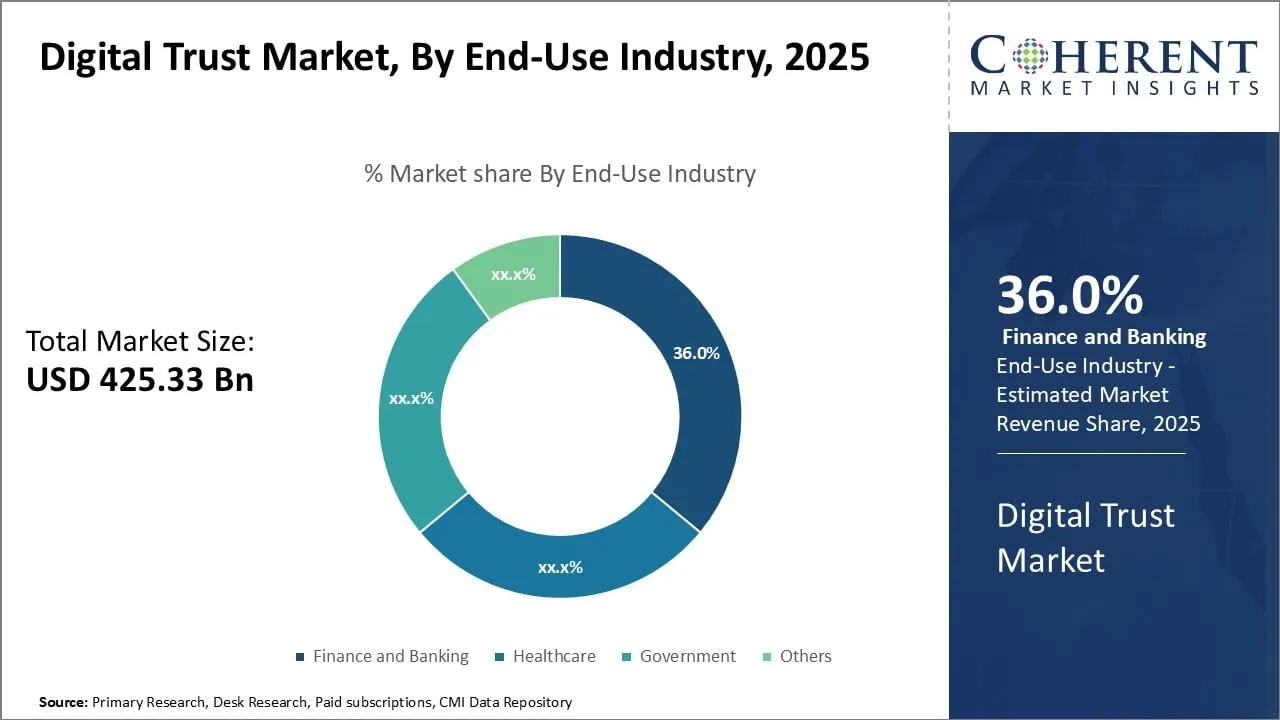
Digital Trust Market Size, Share and Forecast, 2025-2032
Digital Trust Market valued at US$ 425.33 billion in 2025, is anticipated to reaching US$ 1,090.7 billion by 2032, with a steady annual growth rate of 14.4%
https://www.coherentmarketinsights.com/market-insight/digital-trust-market-6135
09:51 AM - Jul 25, 2025 (UTC)
Sponsored by
OWT
5 months ago
Dwngo social network website
Dwngo – The Social Media Platform! * Share your thoughts & ideas * Publish blogs & trending stories * Connect, engage & grow your networkJoin now & be part of the future of social networking! #SocialMedia #Blogging #Dwngo --https://dwngo.com/