Security Standards to Follow
Stay protected by following globally recognized cybersecurity frameworks.
Ensure compliance, reduce risk, and strengthen your organization’s security posture.
To learn more:
https://cyberintelsys.com/...
Stay protected by following globally recognized cybersecurity frameworks.
Ensure compliance, reduce risk, and strengthen your organization’s security posture.
To learn more:
https://cyberintelsys.com/...
03:14 PM - Jul 05, 2025 (UTC)
Best OSCP Training in Pune: Learn Offensive Security from Experts
If you're serious about mastering offensive cybersecurity, the OSCP Training in Pune by WebAsha Technologies is your gateway to a high-impact career. This training is carefully designed to help learners understand real-world penetration testing techniques, exploit development, and ethical hacking methodologies. With a blend of theory and hands-on labs, students gain the practical skills needed to attempt and succeed in the OSCP certification exam.
Visit: https://www.webasha.com/co...
If you're serious about mastering offensive cybersecurity, the OSCP Training in Pune by WebAsha Technologies is your gateway to a high-impact career. This training is carefully designed to help learners understand real-world penetration testing techniques, exploit development, and ethical hacking methodologies. With a blend of theory and hands-on labs, students gain the practical skills needed to attempt and succeed in the OSCP certification exam.
Visit: https://www.webasha.com/co...
11:28 AM - Jul 04, 2025 (UTC)
Key Criteria for Selecting a VAPT Service Provider in US
Choosing the right VAPT provider in the U.S. can make or break your cybersecurity strategy.
Ensure your systems are tested by certified experts who understand your industry's unique risks.
Partner with CyberIntelsys for trusted, end-to-end VAPT services.
For Services: www.cyberintelsys.com/vapt...
Website: https://cyberintelsys.com/
Contact: infocyberintelsys.com
Choosing the right VAPT provider in the U.S. can make or break your cybersecurity strategy.
Ensure your systems are tested by certified experts who understand your industry's unique risks.
Partner with CyberIntelsys for trusted, end-to-end VAPT services.
For Services: www.cyberintelsys.com/vapt...
Website: https://cyberintelsys.com/
Contact: infocyberintelsys.com
12:41 PM - Jul 06, 2025 (UTC)
Ethical Hacking: How White Hat Hackers Protect Us From Cyber Attacks?
If you have a passion for problem-solving and working against cyberattacks, then white hat hacking can be the perfect career for you. To kick-start a career in ethical hacking, it is crucial to develop a strong foundation in computer science and cyber cybersecurity realm.
Read More:- https://blog.ddumc.in/cybe...
If you have a passion for problem-solving and working against cyberattacks, then white hat hacking can be the perfect career for you. To kick-start a career in ethical hacking, it is crucial to develop a strong foundation in computer science and cyber cybersecurity realm.
Read More:- https://blog.ddumc.in/cybe...

Cyber Attacks| How White Hat Hackers Protect Us From them| Best 5 Ways
Ethical Hacking: How White Hat Hackers Protect Us From Cyber Attacks
https://blog.ddumc.in/cyber-attacks-how-white-hat-hackers-protect-us-from-them/
06:13 AM - Jul 04, 2025 (UTC)
Healthcare Data Center Security: Protecting Patient Information in Qatar.
Healthcare Data Center Security in Qatar is vital to protect data of patients as well as keeping trust in the healthcare system. With the help of Cybersecurity for Data Centers, Data Center Encryption, and Data Center Firewalls, medical institutions are able to protect themselves from cyber-attacks.
click on the below link for more information:
https://www.expediteiot.co...
Healthcare Data Center Security in Qatar is vital to protect data of patients as well as keeping trust in the healthcare system. With the help of Cybersecurity for Data Centers, Data Center Encryption, and Data Center Firewalls, medical institutions are able to protect themselves from cyber-attacks.
click on the below link for more information:
https://www.expediteiot.co...

Data Center Perimeter Security in Saudi Arabia, Qatar, & Oman
Data centers are protected by an array of security options, from concrete security measures like secured access points.
https://www.expediteiot.com/data-center-perimeter-security-in-saudi-arabia/
09:55 AM - Jul 04, 2025 (UTC)
Top RaaS Variants in the Wild: What You Need to Know
As Ransomware-as-a-Service (RaaS) continues to evolve, it has become the weapon of choice for many cybercriminals. RaaS enables even low-skilled threat actors to launch sophisticated attacks by renting ransomware toolkits from experienced developers. This business model has fueled the rise of numerous RaaS variants wreaking havoc across industries worldwide. In this post, we’ll explore the top RaaS variants currently active, providing insights into their behavior and impact — and what organizations can do to protect themselves.
1. LockBit: The Relentless Extortionist
2. BlackCat (ALPHV): The First RaaS Written in Rust
3. Cl0p: The Data Extortion Expert
4. RansomEXX: Enterprise-Level Targeting
5. Hive: A Disrupted Yet Formidable Threat
Protecting Against RaaS Threats
Understanding these top ransomware variants is the first step in building a proactive cybersecurity posture. Organizations should implement robust endpoint protection, employee training, and regular vulnerability scans to mitigate risks. For more threat intelligence and insights into cybercriminal networks, explore our tools at DatSpy's cybersecurity intelligence platform.
Stay ahead of emerging threats by leveraging real-time threat feeds and forensic tools — available now on DatSpy.
Visit Us: https://www.datspy.com/
As Ransomware-as-a-Service (RaaS) continues to evolve, it has become the weapon of choice for many cybercriminals. RaaS enables even low-skilled threat actors to launch sophisticated attacks by renting ransomware toolkits from experienced developers. This business model has fueled the rise of numerous RaaS variants wreaking havoc across industries worldwide. In this post, we’ll explore the top RaaS variants currently active, providing insights into their behavior and impact — and what organizations can do to protect themselves.
1. LockBit: The Relentless Extortionist
2. BlackCat (ALPHV): The First RaaS Written in Rust
3. Cl0p: The Data Extortion Expert
4. RansomEXX: Enterprise-Level Targeting
5. Hive: A Disrupted Yet Formidable Threat
Protecting Against RaaS Threats
Understanding these top ransomware variants is the first step in building a proactive cybersecurity posture. Organizations should implement robust endpoint protection, employee training, and regular vulnerability scans to mitigate risks. For more threat intelligence and insights into cybercriminal networks, explore our tools at DatSpy's cybersecurity intelligence platform.
Stay ahead of emerging threats by leveraging real-time threat feeds and forensic tools — available now on DatSpy.
Visit Us: https://www.datspy.com/
07:30 AM - Jul 04, 2025 (UTC)
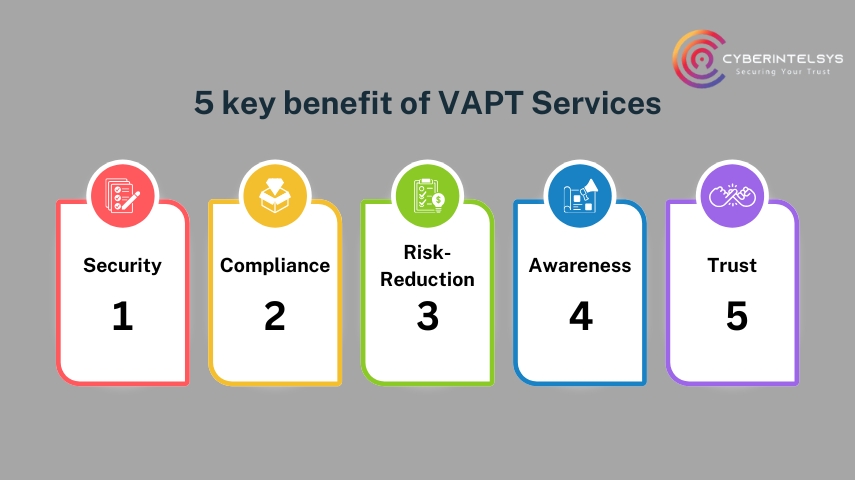
5 key benefit of VAPT Services
Here are the 5 key benefits of VAPT Services for your business.
To explore more, visit:
https://cyberintelsys.com/...
Here are the 5 key benefits of VAPT Services for your business.
To explore more, visit:
https://cyberintelsys.com/...
04:27 PM - Jul 03, 2025 (UTC)
Ransomware Attacks: How Ethical Hackers Help In Prevention and Recovery
In today’s era of advanced technologies and emerging cyber threats, making a career in ethical hacking and cybersecurity can be a great option. To kick-start a career in these fields, students should pursue a career-oriented computer science program, such as a BCA.
Read More:- https://blog.ddumc.in/rans...
In today’s era of advanced technologies and emerging cyber threats, making a career in ethical hacking and cybersecurity can be a great option. To kick-start a career in these fields, students should pursue a career-oriented computer science program, such as a BCA.
Read More:- https://blog.ddumc.in/rans...
06:49 AM - Jul 05, 2025 (UTC)
Best Guide to Cybersecurity Recruiting Firms in USA – Employvision
Looking to hire trusted cybersecurity talent in the USA? Employvision is your go-to partner. We specialize in helping companies find skilled cybersecurity professionals who protect data, systems, and networks.
As one of the top cybersecurity recruiting firms in the USA, we understand the growing need for experts in risk management, threat detection, and compliance. Our recruiting team connects you with the right talent faster—saving you time and money.
Whether you’re a startup or an enterprise, we offer flexible hiring for contract and full-time roles in cybersecurity.
Email: info @employvision .com
Phone: 732-422-7100
Address: 285 Davidson Avenue, Suite 403, Somerset, NJ 08873
Visit: https://employvision.com/t...
Looking to hire trusted cybersecurity talent in the USA? Employvision is your go-to partner. We specialize in helping companies find skilled cybersecurity professionals who protect data, systems, and networks.
As one of the top cybersecurity recruiting firms in the USA, we understand the growing need for experts in risk management, threat detection, and compliance. Our recruiting team connects you with the right talent faster—saving you time and money.
Whether you’re a startup or an enterprise, we offer flexible hiring for contract and full-time roles in cybersecurity.
Email: info @employvision .com
Phone: 732-422-7100
Address: 285 Davidson Avenue, Suite 403, Somerset, NJ 08873
Visit: https://employvision.com/t...
05:35 AM - Jul 04, 2025 (UTC)
Strengthen Your Cyber Defense with ZTNA Security
https://www.seqrite.com/ze...
ZTNA security helps organizations prevent unauthorized access by enforcing continuous authentication. Its zero-trust model ensures that only legitimate users and devices interact with critical systems, reducing the attack surface significantly.
#ZTNA #ZeroTrust #CyberSecurity #ZTNASolutions #ZTNAsecurity #ZTNAvsVPN
https://www.seqrite.com/ze...
ZTNA security helps organizations prevent unauthorized access by enforcing continuous authentication. Its zero-trust model ensures that only legitimate users and devices interact with critical systems, reducing the attack surface significantly.
#ZTNA #ZeroTrust #CyberSecurity #ZTNASolutions #ZTNAsecurity #ZTNAvsVPN
10:41 AM - Jul 05, 2025 (UTC)
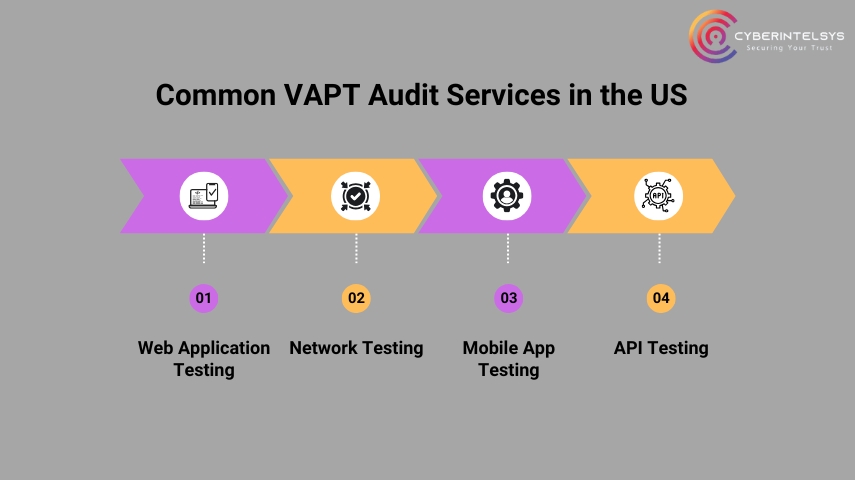
Common VAPT Audit Services in the US
Protect your business by testing websites, networks, mobile apps, cloud setups, and APIs for security risks. Find weaknesses early and keep your data safe from cyber threats.
Visit: https://cyberintelsys.com/...
Protect your business by testing websites, networks, mobile apps, cloud setups, and APIs for security risks. Find weaknesses early and keep your data safe from cyber threats.
Visit: https://cyberintelsys.com/...
03:48 PM - Jul 04, 2025 (UTC)
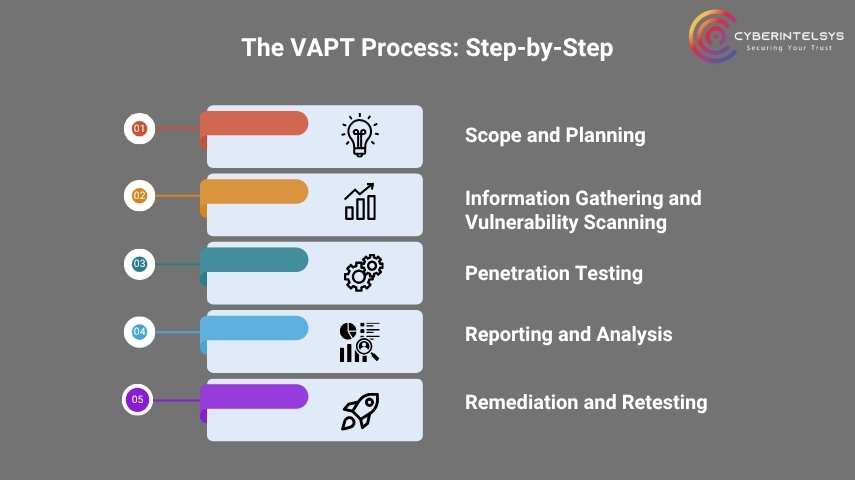
The VAPT Process: Step-by-Step
Discover the 5 essential steps of the VAPT process to safeguard your business from cyber threats. Protect your digital assets before hackers strike!
Contact us today: infocyberintelsys.com | www.cyberintelsys.com | https://cyberintelsys.com/...
Discover the 5 essential steps of the VAPT process to safeguard your business from cyber threats. Protect your digital assets before hackers strike!
Contact us today: infocyberintelsys.com | www.cyberintelsys.com | https://cyberintelsys.com/...
04:01 PM - Jul 06, 2025 (UTC)
Transforming UAE Data: The Dawn of CyberPod AI
The cybersecurity landscape in the UAE is rapidly evolving, and so are the tools needed to protect it. CyberPod AI represents a transformative leap in how organizations approach digital defense — combining the analytical power of artificial intelligence with human expertise to create a safer, smarter environment.
For more information contact us on:
Tektronix Technology Systems Dubai-Head Office
connecttektronixllc.ae
Or click on the below link for more information:
https://tektronixllc.ae/cy...
The cybersecurity landscape in the UAE is rapidly evolving, and so are the tools needed to protect it. CyberPod AI represents a transformative leap in how organizations approach digital defense — combining the analytical power of artificial intelligence with human expertise to create a safer, smarter environment.
For more information contact us on:
Tektronix Technology Systems Dubai-Head Office
connecttektronixllc.ae
Or click on the below link for more information:
https://tektronixllc.ae/cy...
06:26 AM - Jul 04, 2025 (UTC)
The Healthcare Security Systems market The Healthcare Security Systems market
https://www.reportprime.co...
The Healthcare Security Systems market is witnessing robust growth driven by the increasing incidence of data breaches, rising investments in healthcare infrastructure, and stricter regulatory requirements for patient data protection. The integration of advanced technologies like AI and IoT in surveillance, and the growing need for physical and cybersecurity convergence in hospitals and clinics are shaping the industry.
https://www.reportprime.co...
The Healthcare Security Systems market is witnessing robust growth driven by the increasing incidence of data breaches, rising investments in healthcare infrastructure, and stricter regulatory requirements for patient data protection. The integration of advanced technologies like AI and IoT in surveillance, and the growing need for physical and cybersecurity convergence in hospitals and clinics are shaping the industry.
01:57 PM - Jul 04, 2025 (UTC)
Sponsored by
OWT
6 months ago