Cyber attacks are rising, and local businesses in Mercer Island are not exempt. Offices here need more than antivirus software, they need smarter networks. Small businesses account for 43% of cyberattacks, and many lack the right tools to fight back. This is where Software-Defined Networking (SDN) changes everything.
Visit us- https://online.pubhtml5.co...

The Benefits of Software-Defined Networking (SDN) in Office Security
Cyber attacks are rising, and local businesses in Mercer Island are not exempt. Offices here need more than antivirus software, they need smarter networks. Small businesses account for 43% of cyberattacks, and many lack the right tools to fight back. This is where Software-Defined Networking (SDN) c..
https://online.pubhtml5.com/hzzyz/yuho/The most common causes of QuickBooks Error 80029c4a are corrupted system files, unfinished installations, or interference from antivirus software. QuickBooks may not launch properly due to this error. Discover the typical reasons, detailed troubleshooting techniques, and tried-and-true fixes for this problem so that your QuickBooks program can function properly once again. Please contact us at +1.833.802.0002 if you want to speak with a support specialist immediately.
Read More: https://www.socialdude.net...

Powerful Methods to Overcome QuickBooks Error 80029c4a
QuickBooks Error 80029c4a usually appears due to corrupted system files or antivirus issues. Learn step-by-step solutions to fix this startup error quickly.
https://www.socialdude.net/en/articles/8227-quickbooks-error-80029c4aLearn more: https://www.cm-alliance.co...
QuickBooks Error Code 1311 typically occurs during installation due to missing or corrupted source files. To resolve it, verify your installation media, temporarily disable your antivirus, or download a fresh copy from Intuit. For persistent errors, use the QuickBooks Clean Install Tool or contact support at 1–855–542–9309
Source URL - https://proadvisor.hashnod...
To install the Toca Boca World Mod APK safely, you must first find a trustworthy website that offers a clean and updated file. Be careful of fake websites that might give you harmful files. After downloading the APK, go to your phone’s settings and allow the option to install apps from unknown sources. Then open the APK file and press "Install." The game will be added to your phone in a few minutes. Always scan the file with an antivirus app before installing. Also, make sure you are downloading the version that matches your device type (Android only). Never give your personal details while downloading an APK. Once installed, open the game, and you’ll see all locations unlocked from the beginning. You don’t need a Google account or payment. Just enjoy the full premium experience for free and worry-free.
Best Places to Visit Inside the Game
Toca Boca World Mod APK has many interesting places you can visit, each filled with surprises. One of the favorite places is the hair salon, where you can try fun hairstyles, use colors, and give characters new looks. The shopping mall has clothes, food courts, and stores where you can buy gifts or snacks. The school building is great for acting like a teacher or student. You can go to class, do experiments, or even create your own school rules.
https://thetocaworld.com/
QuickBooks Error Code 213 typically occurs when the system can't access required files due to permission issues. To resolve it, run QuickBooks as administrator, check file/folder permissions, and verify your antivirus isn't blocking access. For network errors, ensure proper sharing permissions. Need expert help? Our QuickBooks specialists resolve Error 213 daily—contact us for immediate support at 855-888-3080
Source URL - https://proadvisor6.godadd...

Powerful Methods to Overcome QuickBooks Error Code 213
Discover the best Quickbooks accounting software solutions for your business. Streamline your finances with Quickbooks Online.
https://proadvisor6.godaddysites.com/f/powerful-methods-to-overcome-quickbooks-error-code-213SOC tools help protect networks by gathering data, detecting threats, and blocking attacks. SIEM alerts issues, EDR watches devices, IDS spots intrusion attempts, and firewalls or antivirus stop known threats early. These tools work together for security.
https://iifis.org/blog/wha...
https://wizard-it.co.nz/se...
Sympley offers professional WordPress web maintenance to keep your website safe, up to date, and functioning at its best. We take care of the technical aspects, such as antivirus protection, speed optimization, and routine backups and upgrades, so you can concentrate on expanding your company with assurance and comfort. For more visit us!
https://sympley.com.au/wor...
#Antivirus #trending #post #new #owntweet
https://vinzotechblog.com/...

Best Free & Premium Antivirus Security For PC, Android, iPhone & Mac - VinzoTech Blog
Protect your PC, Android, iPhone & Mac with top free and premium antivirus software. Discover the best free & premium antivirus security tools for every device in one guide.
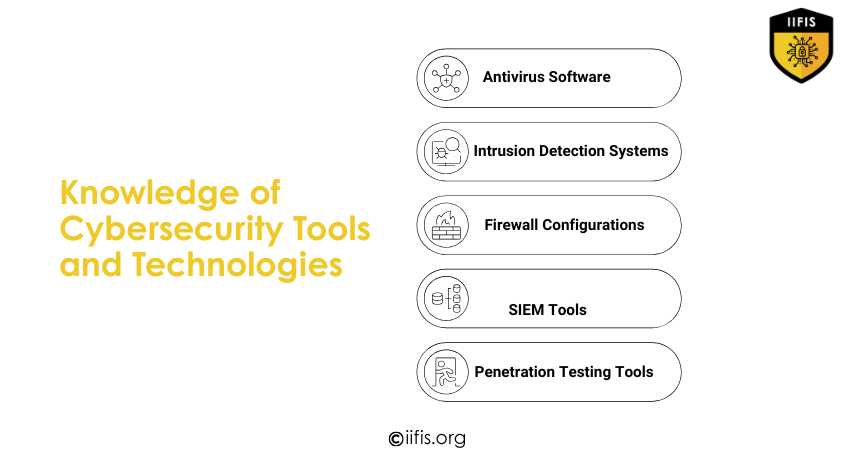
https://vinzotechblog.com/best-free-premium-antivirus-security-for-pc-android-iphone-mac/Essential cybersecurity tools and technologies, including as firewall setups, intrusion detection systems, antivirus software, SIEM tools, and penetration testing tools, are highlighted in this image. These tools help in securing digital environments and defending systems against attacks.
https://iifis.org/blog/ski...
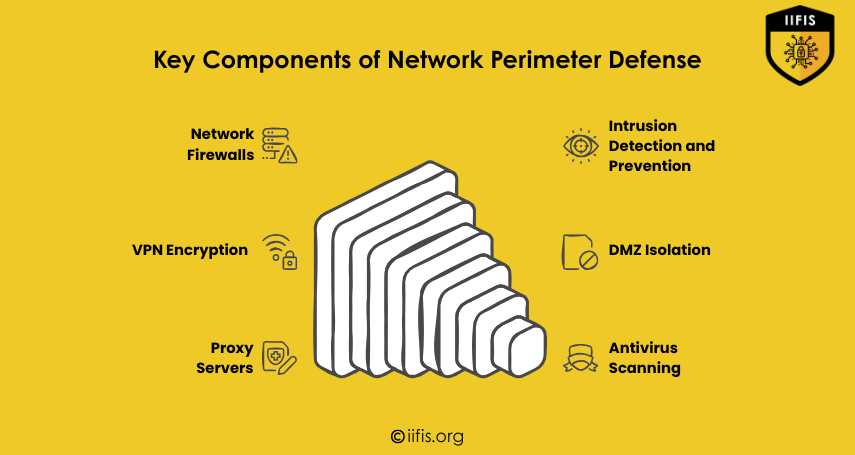
This image outlines the key components of network perimeter defense. It includes tools like network firewalls, VPN encryption, proxy servers, intrusion detection and prevention, DMZ isolation, and antivirus scanning—each playing a vital role in securing digital networks.
https://iifis.org/blog/wha...
Explore leading Kaspersky antivirus distributors in India for bulk licenses, endpoint protection, and full security suite deployment across industries.
https://radiant.in/kaspers...

Kaspersky Antivirus Security Dealer, Supplier & Distributor in India | Radiant
Get Kaspersky Antivirus Security in India with Radiant—your trusted dealer & partner for reliable system and data protection solutions.
https://radiant.in/kaspersky-antivirus-security-dealer-supplier-partner-distributor-in-india/Navigating Amtrak plans can sometimes require a little extra assistance [US-Amtrak™ +1-866-932-4012] OTA (Live Person) 【+1-866-932-4012】. Whether you’re adjusting a Amtrak, clarifying Antivirus secure details, or seeking a refund, speaking with a live person at Amtrak can often be the most efficient way to resolve your concerns [US-Amtrak™ +1-866-932-4012] OTA (Live Person) 【+1-866-932-4012】. This guide outlines how to reach a live Amtrak agent via phone, chat, and other methods, offering tips to minimize wait times and ensure a smooth support experience [US-Amtrak™ +1-866-932-4012] OTA (Live Person) 【+1-866-932-4012】.
Why Speak with a Live Amtrak Agent?
To speak with a live agent at Amtrak, call +1-866-932-4012 or 1-800-AmtrakTM (US/OTA)—available 24/7. You can also use the live chat on the Amtrak website or app. For quick help, have your booking ID ready”
QuickBooks Error Code 403 occurs when access to company files is denied, typically due to permission restrictions or firewall blocks. To resolve it, check file/folder permissions, disable firewall/antivirus temporarily, and verify network sharing settings. For persistent errors, run QuickBooks as administrator. Need immediate help? Our QuickBooks experts resolve Error 403 daily—contact us now at 855-888-3080
Source URL - https://www.socialdude.net...

Technical Fixes to Overcome QuickBooks Error Code 403
Enter your text here ... While attempting to download the recent version of QuickBooks updates or tr...
https://www.socialdude.net/en/articles/8108-technical-fixes-to-overcome-quickbooks-error-code-403