If you need help with a refund on Cash App, you can reach out to their customer support team for assistance. While Cash App does not offer direct phone support for all inquiries, users can request help through the app or website. However, be cautious—many scam websites claim to offer a "Cash App refund number" and try to steal personal information.
Cash App Refund Number — Get Help with Refunds Fast | by Nora smith | May, 2025 | Medium
In today’s digital world, apps like Cash App have made sending and receiving money incredibly easy. But what happens when something goes wrong? Whether it’s an accidental payment, a scam, or a…
https://medium.com/@norassmith9876/cash-app-refund-number-get-help-with-refunds-fast-bc840f5c3bd8
05:50 AM - May 24, 2025 (UTC)
Web Design Agency Toronto
Toronto's leading web development & design company. Experts in custom website design, e-commerce solutions. Top designer & developer agency.
Learn More- https://stealthmedia.com/t...
Toronto's leading web development & design company. Experts in custom website design, e-commerce solutions. Top designer & developer agency.
Learn More- https://stealthmedia.com/t...
05:13 AM - May 27, 2025 (UTC)
Discover the power of stealth call recording with ONEMONITAR. Automatically record incoming & outgoing calls, store securely, and access anytime—all without detection. Perfect for parents, employers, and personal use.
https://onemonitar.com/hid...
#HiddenCallRecorder #callmonitoring #ParentalControl #SecureCalls
https://onemonitar.com/hid...
#HiddenCallRecorder #callmonitoring #ParentalControl #SecureCalls

Best Hidden Call Recorder for Android | Spy Call Recorder - ONEMONITAR
Hidden Call Recorder - ONEMONITAR Hidden Call Recorder for Android lets you secretly record incoming & outgoing calls. Stay discreet with our spy call recorder for real-time monitoring.
https://onemonitar.com/hidden-call-recorder.html
01:11 PM - May 31, 2025 (UTC)
Digital Marketing Companies Saskatoon
Our digital marketing company offers competent services for brands in Vancouver, Toronto, Edmonton, Saskatoon, Calgary, New York, Winnipeg, and Ottawa. Call 833.333.0344
Learn More- https://stealthmedia.com/d...
Our digital marketing company offers competent services for brands in Vancouver, Toronto, Edmonton, Saskatoon, Calgary, New York, Winnipeg, and Ottawa. Call 833.333.0344
Learn More- https://stealthmedia.com/d...
12:25 PM - May 23, 2025 (UTC)
Sponsored by
OWT
5 months ago
Social Media Agency Saskatoon
Rely on our company for successful social media management in Vancouver, Toronto, New York, Edmonton, Saskatoon, Winnipeg, Calgary, and Ottawa. Call 833.333.0344
Learn More- https://stealthmedia.com/s...
Rely on our company for successful social media management in Vancouver, Toronto, New York, Edmonton, Saskatoon, Winnipeg, Calgary, and Ottawa. Call 833.333.0344
Learn More- https://stealthmedia.com/s...
07:41 AM - May 26, 2025 (UTC)
SEO Agency Toronto
Boost online visibility with top SEO company in Edmonton, Calgary, Saskatoon, Toronto, Vancouver,Regina, New York, Winnipeg, and Ottawa. Trusted SEO agency for effective results.
Learn More- https://stealthmedia.com/s...
Boost online visibility with top SEO company in Edmonton, Calgary, Saskatoon, Toronto, Vancouver,Regina, New York, Winnipeg, and Ottawa. Trusted SEO agency for effective results.
Learn More- https://stealthmedia.com/s...
12:05 PM - May 23, 2025 (UTC)
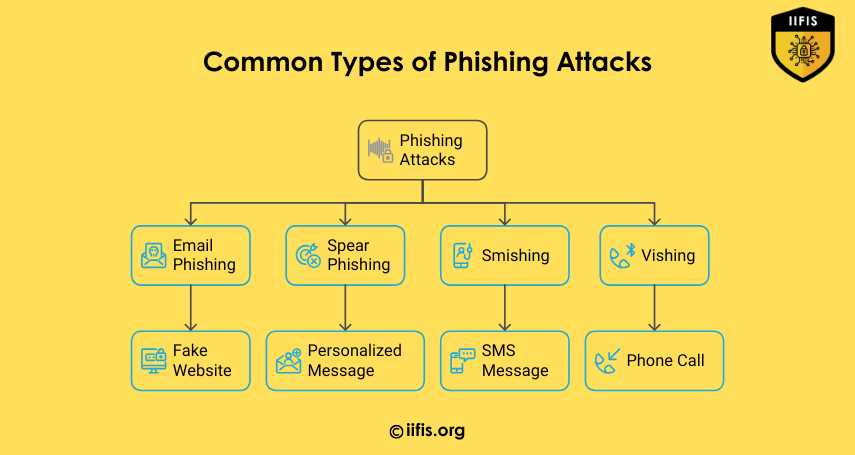
Common Types of Phishing Attacks | IIFIS
This image shows different types of phishing attacks: Email Phishing, Spear Phishing, Smishing, and Vishing. Each type uses a different method—such as fake websites, personalized messages, SMS, or phone calls—to trick users and steal information.
https://iifis.org/blog/wha...
This image shows different types of phishing attacks: Email Phishing, Spear Phishing, Smishing, and Vishing. Each type uses a different method—such as fake websites, personalized messages, SMS, or phone calls—to trick users and steal information.
https://iifis.org/blog/wha...
12:51 PM - May 28, 2025 (UTC)
Vancouver Web Design Companies
Vancouver's premier web development & design firm. Specializing in custom site design, e-commerce solutions. Top designer & developer agency.
Learn More- https://stealthmedia.com/v...
Vancouver's premier web development & design firm. Specializing in custom site design, e-commerce solutions. Top designer & developer agency.
Learn More- https://stealthmedia.com/v...
05:20 AM - May 27, 2025 (UTC)
How F5 Advanced Bot Management Strengthens Application Security
Application security is necessary nowadays as cloud usage is becoming ever more prevalent. These malicious bots threaten to steal data and exploit all worthy systems. F5 advanced bot management offers strong protection using smart detection, real-time monitoring, and robust defenses—helping businesses keep their applications and online assets safe and secure.
VISIT US-https://www.compu-link.com...
Application security is necessary nowadays as cloud usage is becoming ever more prevalent. These malicious bots threaten to steal data and exploit all worthy systems. F5 advanced bot management offers strong protection using smart detection, real-time monitoring, and robust defenses—helping businesses keep their applications and online assets safe and secure.
VISIT US-https://www.compu-link.com...
How F5 Advanced Bot Management Strengthens Application Security
Discover how F5 Advanced Bot Management enhances your app security by effectively detecting and mitigating bot threats. Protect your applications today!
https://www.compu-link.com/how-f5-advanced-bot-management-strengthens-application-security/
11:22 AM - Jun 05, 2025 (UTC)
Branding Agency Toronto
Branding agency with services in Edmonton, Calgary, Saskatoon, Toronto, Vancouver, Winnipeg, Ottaw & New York. Elevate your brand with expert logo design in Canada.
Learn More- https://stealthmedia.com/l...
Branding agency with services in Edmonton, Calgary, Saskatoon, Toronto, Vancouver, Winnipeg, Ottaw & New York. Elevate your brand with expert logo design in Canada.
Learn More- https://stealthmedia.com/l...
07:24 AM - May 26, 2025 (UTC)
Vancouver Marketing Agencies
Leading marketing managers company in Edmonton, Calgary, Saskatoon, Toronto & Vancouver. Elevate your brand with expert strategies.
Learn More- https://stealthmedia.com/a...
Leading marketing managers company in Edmonton, Calgary, Saskatoon, Toronto & Vancouver. Elevate your brand with expert strategies.
Learn More- https://stealthmedia.com/a...
12:17 PM - May 23, 2025 (UTC)
What is an Impermanent Loss and How to Avoid it
Imagine lending your assets to a trusted person only to get them back devalued and reshuffled even though the other person didn't steal anything. This loss is what is known as an impermanent loss in the defi world.
So, let's learn about what is impermanent loss and understand the right strategy so you can outsmart it!
Read more: https://armswap.com/learn/...
Imagine lending your assets to a trusted person only to get them back devalued and reshuffled even though the other person didn't steal anything. This loss is what is known as an impermanent loss in the defi world.
So, let's learn about what is impermanent loss and understand the right strategy so you can outsmart it!
Read more: https://armswap.com/learn/...
05:46 AM - Jun 12, 2025 (UTC)
Custom Web Design Calgary
Leading Calgary web design company specializing in custom website design, e-commerce solutions, and expert designers. Your online success starts here.
Learn More- https://stealthmedia.com/c...
Leading Calgary web design company specializing in custom website design, e-commerce solutions, and expert designers. Your online success starts here.
Learn More- https://stealthmedia.com/c...
07:33 AM - May 26, 2025 (UTC)
Get stunning nails at Glitz and Bliss Unisex Salon, the best nail extension salon in Dwarka! From classy acrylics to trendy gel extensions, we offer flawless, long-lasting styles. Book now and let your nails steal the spotlight! 💅✨ #NailExtensionDwarka
https://www.adlandpro.com/...
https://www.adlandpro.com/...
07:32 AM - May 29, 2025 (UTC)
Festive Chevda Mix – Light, Tasty, and Irresistible!
Chevda, the ultimate Indian snack, is a crunchy, savory treat that lights up every festive occasion. Whether it’s Diwali, Holi, or a casual family gathering, this delightful mix is a crowd favorite. Packed with vibrant spices and satisfying textures, Bharat Namkeen’s festive Chevda mix is perfect for snacking and sharing with loved ones. Let’s explore why this irresistible snack deserves a spot at your next celebration!
Why Chevda Mix Steals the Show
Chevda, also known as chivda or namkeen, is a vibrant blend of crispy flattened rice (poha), roasted nuts, aromatic spices, and sometimes a touch of dried fruits. Its magic lies in its versatility – light enough for guilt-free munching yet bursting with tangy, savory goodness. Bharat Namkeen’s festive Chevda mix, crafted with premium ingredients like roasted peanuts, cashews, raisins, and a hint of sweetness, offers the perfect sweet-savory balance.
How to Enjoy Chevda Mix
Serve Bharat Namkeen’s Chevda mix in vibrant bowls with masala chai, pack it for on-the-go snacking, or gift it in elegant packaging for a heartfelt festive present. Add a sprinkle of chaat masala or pair with crispy sev for extra zing! Discover the authentic taste at bharatnamkeens.com.
For more visit :- https://www.bharatnamkeens...
Chevda, the ultimate Indian snack, is a crunchy, savory treat that lights up every festive occasion. Whether it’s Diwali, Holi, or a casual family gathering, this delightful mix is a crowd favorite. Packed with vibrant spices and satisfying textures, Bharat Namkeen’s festive Chevda mix is perfect for snacking and sharing with loved ones. Let’s explore why this irresistible snack deserves a spot at your next celebration!
Why Chevda Mix Steals the Show
Chevda, also known as chivda or namkeen, is a vibrant blend of crispy flattened rice (poha), roasted nuts, aromatic spices, and sometimes a touch of dried fruits. Its magic lies in its versatility – light enough for guilt-free munching yet bursting with tangy, savory goodness. Bharat Namkeen’s festive Chevda mix, crafted with premium ingredients like roasted peanuts, cashews, raisins, and a hint of sweetness, offers the perfect sweet-savory balance.
How to Enjoy Chevda Mix
Serve Bharat Namkeen’s Chevda mix in vibrant bowls with masala chai, pack it for on-the-go snacking, or gift it in elegant packaging for a heartfelt festive present. Add a sprinkle of chaat masala or pair with crispy sev for extra zing! Discover the authentic taste at bharatnamkeens.com.
For more visit :- https://www.bharatnamkeens...
07:03 AM - May 27, 2025 (UTC)